Unsecure Webservices: bWAPP vs. JuiceShop
Introduction
The number of users of online services has increased significantly in the last years. Nowadays web applications represent a fundamental part in information technologies. Therefore the danger of attacks on the internet is growing and make so-called penetration tests necessary. A penetration test comprises a series of activities which record and identify security gaps. In the attached seminar paper, two intentionally insecure web services are compared with each other. The focus of the practical part includes the testing of the world's most frequently used SQL-injection Attack. In this case, attackers take advantage of specific weaknesses in order to gain access to confidential information. A variation of this SQL injection attack is described.
Most software errors are the result of inappropriate input validation. This leads to an attack targeting confidential information more frequently. SQL injection attacks are very popular because they are executed using simple scripts. Identifying SQL-injection vulnerabilities is often not that easy. A lot of software errors in web applications are the result of invalid entries. Even though the majority of security gaps on the web are performed directly and from a strategic distance, many web designers are surprisingly not security conscious. Testing vulnerabilities for web applications is one way to deal with such problems. Tools like bWAPP and OWASP Juice Shop offer users a fun way to uncover these vulnerabilities.
Web Security Test-Application
Penetrating Testing
Penetrating testing is a targeted, permitted attempt to penetrate an IT system. The main objective is to detect and eliminate vulnerabilities in order to improve IT security. Vulnerabilities should be identified before they arise. Methods such as SQL injection, XML External Entities (XEE) and Cross-Site scripting (XSS) are very popular by hackers. For web applications, the Open Web Application Security Project (OWASP) offers materials for pentests.
SQL Injection Vulnerability
With the growing popularity of the World Wide Web, there was an increasing use for advanced technology and dynamic websites.
SQL injection vulnerability is one of the greatest dangers to confidentiality and integrity in Web applications and thus has been included in the OWASP Top 10 list of the most common vulnerabilities since its introduction. For example, attackers can insert malware into an SQL statement through an SQL injection vulnerability. The practical part of this thesis deals with the SQL injection attack. Attackers gain the ability to perform a series of actions if an SQL injection is applied to a vulnerable page. By exploiting this vulnerability, database contents can be added, edited, deleted or read.
bWAPP
The term bWAPP stands for buggy Web Applications. bWAPP belongs to the ITSEC-Games-Project and describes a deliberately extremely faulty web application. It was designed with the goal of ensuring IT security. Furthermore, it has a gaming character and should serve as a funny training enviroment.
OWASP Juice Shop
At first glance, the OWASP Juice Shop looks like an inconspicuous online shop for fruit juices. The Juice Shop was designed in 2014 and is a so-called 'online juice shop' for safety training. Two years after its foundation, Juice Shop was submitted and accepted as an OWASP tool project. This step made the Juice Shop accessible to a large community of users within a short period of time.
Comparison and architecture of bWAPP and OWASP Juice Shop
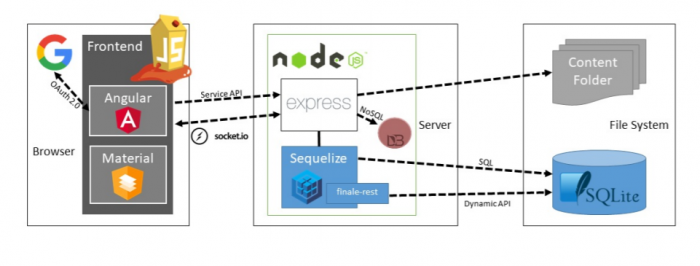
OWASP Juice Shop is a pure web application, which is implemented in JavaScript and TypeScript. In the frontend, Angular Framework is used to create a Single Page Application. The layout of the user interface is the implementation of Google's material design using Angular Material Components. In order to achieve responsiveness, the Angular Flex layout is used. All symbols which were used are from the Font Awesome library. Javascript is also used as a programming language in the backend. An Express Application is hosted on a Node.js server and provides the client-side code to the browser. The client is also provided with the required backend functionality via a RESTful API. SQLite was selected as the database. Sequelize and Finale-Rest are used as abstraction levels from the database. A MarsDB is part of the OWASP Juice Shops as additional data storage. It is a JavaScript derivative of the popular MongoDB NoSQL database and compatible with most query and change operations. Push notifications that appear when a challenge is successfully hacked are implemented via a WebSocket Protocol. The application also offers users a comfortable way of registration via OAuth 2.0. This give users the possibility to sign in using their Google accounts.
bWAPP is an open source PHP application that uses a MySQL database. It can be hosted on Linux or Windows with Apache or IIS and MySQL. To install bWAPP there is a possibility to use a local webserver like WAMP or XAMPP. Another possibility is the download of bee-box, a bWAPP preinstalled virtual machine.
To download virtualbox, use the following link:
On the following page there is a step-by-step instructions for installing virtualbox:
Step-by-Step guideline: how to install virtualbox
To install beebox you can use the following link:
Practical demonstration Step-by-Step guideline
For the practical demonstrations SQL injection is chosen. This hacking method will be tested on both insecure web applications to get a clear comparison. SQL-Injection is one of the most common methods on the top 10 list of OWASP and therefore it is considered as a very serious threat.
bWAPP Challenge
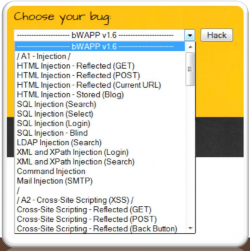
STEP 1: Select a challenge
The challenge is selected first. Afterwards, the user is redirected to the next web page to be able to execute the challenge.
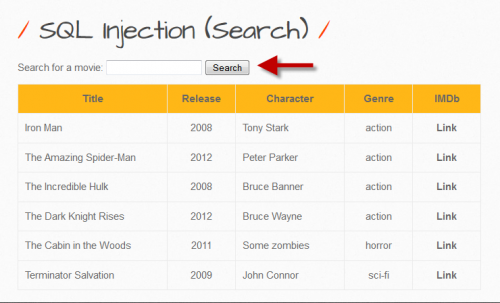
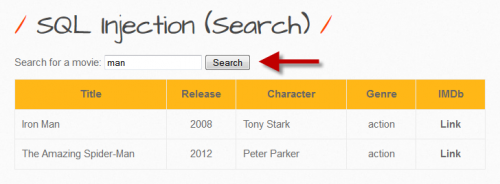
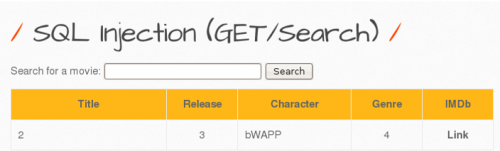
In order to be able to select a challenge, there is a registration requirement. However, users have the possibility to register with any data they wish. Afterwards, an SQL injection task can be selected from various 'bugs'. For the selected (GET/SEARCH) SQL-Injection, information about available movies is displayed in a table when entering a movie title. Here you can search for one or more movies. As a result of the search, the movie details are displayed. If the input button is clicked without entering a search term, all movies are displayed. The set goal is to get a user password.
STEP 2: Try out some SQL-Statements
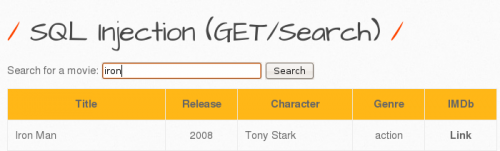
If you enter a search term such as 'iron', for example, all data will be displayed as can bee seen in the picture below. In this challenge, bWAPP is asking us to search the database for our favorite movie which contains the word 'iron' and the search field gives the result 'iron man'. In this case there is a high probability that this query contains some columns. The select-command is something like "Select column1, column2, column3, column4 from table where movie LIKE '%". $userinput."%'"
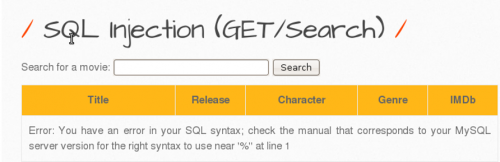
If the form is vulnerable, introducing a single 1 should throw a SQL error because "Select column1, column2, column3, column4 from table where movie LIKE "'" is not a valid query. As a result, you can see that the URL parameter 1' is definitely vulnerable to an SQL injection:
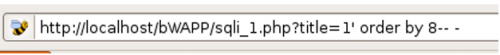
After recognizing a syntax error the URL is edited; action=search is deleted and replaced by order by 1 -- -.
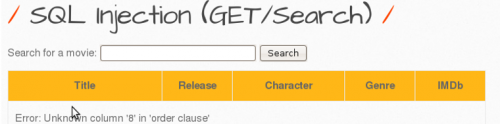
The output shows that the URL parameters are definitely vulnerable to SQL injections.
STEP 3: Trying to find out the number of columns
To find the answer we can use an 'ORDER BY' clause inside our query : ' order by 6 -- - The query sent to the database will look like : "Select column1, column2, column3, column4, column5, column6, from table where movie LIKE '%' order by 6 -- -%' . If the columns exists, the result will be ordered by the 6th column. Otherwise a SQL error will be thrown.
We can try the numbers until a so-called out of table message is displayed. This is done by increasing a number by 1 until an error message appears. As no error is thrown we know the query contains at least 7 columns. So we can try with 8 columns. By entering the 8th column there is an error message. Now we know the query contains 7 columns.
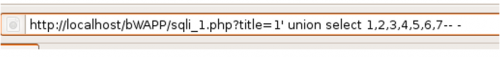
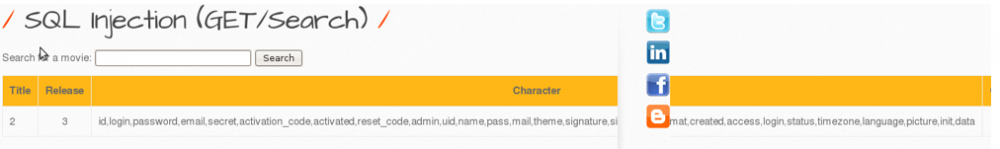
The attempt to display confidential information begins with an SQL Union statement. With this statement it is possible to merge database tables. First, it must be ensured that the same number of columns is used as in the original SQL statement. Then it is possible to perform some malicious queries.
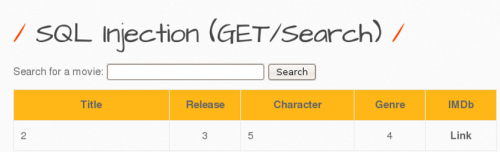
The result shows that column 5 corresponds to one character.
STEP 4: Get the password
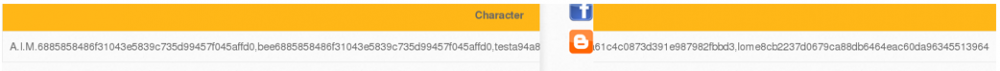
Again, the URL is changed to access the desired password. Now it is possible to play with the field order and visualize the current database character:
The result ejects the character bWAPP. Now it is only a few steps to the hashed password.
In the following step the contents of the columns-output is 'User'. Now we have all we need to retrieve all users secrets. The column names login, password, email and secret looks interesting.
The goal is to get the password. Therefore the URL is changed so the login and password of the user are displayed. The result gives some interesting values. The database is exploited by retrieving confidential data. The value of the password is stored in a hash state and cannot yet be retrieved. There is one last query to get the hashed password from bwapp.
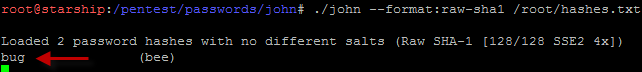
STEP 5: Cracking the hashed password with John the Ripper
To crack the hashed password, the next step is to use a password cracker software such as John the Ripper. John the Ripper is a popular open source password cracking software. A number of password crackers are combined in one package. Password hash types are detected automatically the password's output in clear text.
OWASP Juice Shop Challenge
At OWASP Juice Shop there is a separate website where the Challenges are listed. You have to search for the possibility of executing these Challenges. If a Challenge was successful, a notification will appear on the screen.
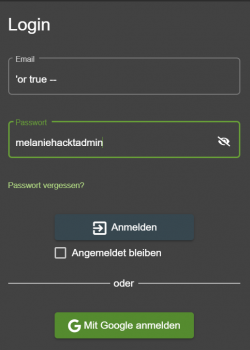
STEP 1: Try to login as Admin with simple SQL-statements
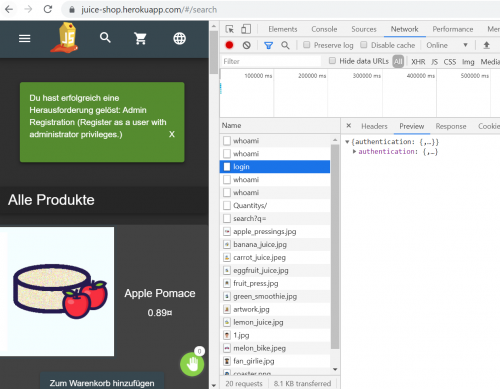
The following command is used to attempt to log in as Admin: 'or true - -. Within a short period of time it was possible to log in as Admin using this SQL command and a randomly chosen password. True as an SQL command means that this result is always true. The double hyphen after it means that all characters after true are comments. In this case the Login worked uncomplicated and fast.
Successful login: Register as a user with administrator priviliges. If a challenge is successfully solved, this will be shown on the screen.
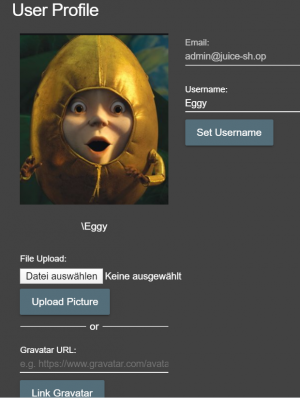
STEP 2: Change user data
After the successful login it is possible to change user data like account name and a picture. It is also possible to make further changes and, for example, fill the shopping cart.
Conclusion
Tools like bWAPP and OWASP Juice Shop are very helpful and interesting for anyone interested in trying out various hacking tasks with different levels of difficulty in a playful manner. With the unstoppable development of technology and today's abundance of information it becomes more important to be well informed about the dangers that come with the World Wide Web. An SQL injection example (GET / Search) shows that passwords of any user can be cracked in a short time. The two insecure web services bWAPP and OWASP Juice Shop were introduced and compared in terms of installation, architecture and application. Due to the different levels of difficulty in the challenges and additional challenges on special events, users are able to further develop their skills. Further information on this article can be found in my paper: seminar paper
References
Open Web Application Security Project (OWASP)