Difference between revisions of "User:AReicher"
| Line 26: | Line 26: | ||
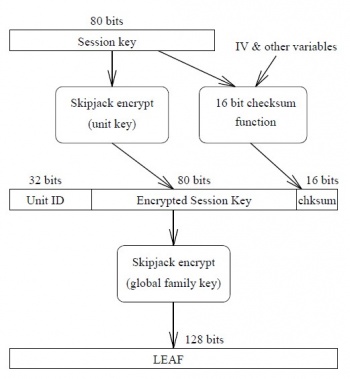
The session-key itself is encrypted with the device serial number (also known as unit-id), before it is put into the LEAF. (As mentioned before, the unit-id is also held in escrow in a Federal DB). | The session-key itself is encrypted with the device serial number (also known as unit-id), before it is put into the LEAF. (As mentioned before, the unit-id is also held in escrow in a Federal DB). | ||
In order to make the device keys secure from hidden tampering, a checksum is in the LEAF. | In order to make the device keys secure from hidden tampering, a checksum is in the LEAF. | ||
If a | If a LEAF does not pass integrity checks, using the safe mode is not possible. | ||
Revision as of 13:06, 20 December 2020
Clipper chip
Summary
This document shows an overview about the Clipper Chip programm, that was started by the U.S. Governtment in the early 90´s.
Description
The Clipper Chip is a small Chipset, that was developed by the NSA (National Security Agency) and advertised by the U.S. Government, in the early 90´s. The idea was, that the Chipset would be integrated in Communication devices like telephones or personal computers and to securely encrypt their Communication, while leaving a backdoor for the U.S. Government.
Origin
According to official U.S. Government Documents, the origins of the Clipper Chip programm, can be traced to the "Computer Security act of 1987". This Act was meant to ammend legislation of the Year 1949, to create security standards for non-military computer systems. in 1993 The U.S. Government introduced an initiative, that should provide security for communication of non-classified data with a special Chipset, called the Clipper Chip. The goal was to at first equip the DoJ (Department of Justice) with phones containing the Clipper Chip and then extend its use to the US high-tech industry.
Functionality
The Clipper Chip,uses a special encryption system based on the EES (Escrowed Encryption Standard). It uses the Skipjack-algorithm for encryption of te data and a key-escrow System, as a backdoor for decryption for autorised 3rd parties. Every device manufactured, with a Clipper Chip gets a unique number at the time of manufacturing (unit-id), that is kept, in escrow, in 2 Databases of the U.S. Government.
The encryption process
When a Clipper Chip secured device, communicates in safe (encrypted) mode, a LEAF (Law Enforcement Access Field) is exchanged.
Contained within the LEAF is a copy of the unique session-key, with whom control of the enceyption is possible. The session-key itself is encrypted with the device serial number (also known as unit-id), before it is put into the LEAF. (As mentioned before, the unit-id is also held in escrow in a Federal DB). In order to make the device keys secure from hidden tampering, a checksum is in the LEAF. If a LEAF does not pass integrity checks, using the safe mode is not possible.