Difference between revisions of "VirtualBox: How to Setup your Malware Analysis"
| Line 29: | Line 29: | ||
=== Installing VirtualBox === | === Installing VirtualBox === | ||
[[File:vbox.PNG| | [[File:vbox.PNG|1000px|center|thumb|VirtualBox Setup and Home Screen]] | ||
The first step is to install VirtualBox. During the setup, we have to prevent it from installing the network drivers as they provide a weak point malware likes to scan for. After, finish the setup with the remaining configurations on default. | The first step is to install VirtualBox. During the setup, we have to prevent it from installing the network drivers as they provide a weak point malware likes to scan for. After, finish the setup with the remaining configurations on default. | ||
Revision as of 20:01, 5 December 2019
Summary
This documentation will provide you with a step-by-step guide to creating a virtual machine over VirtualBox. Though, we will not create a generic VM! This VM will provide you with a completely non-detectable environment for Malware Analysis.
As advanced malware nowadays is able to detect its environment (e.g. scanning for RAM, CPU cores, disk space, registry keys and even drivers) they are now able to stop their execution if they detect a virtualized environment. Therefore it is critical to setup your malware analysis VM correctly.
In order to render your VM undetectable we have chosen two state-of-the-art tools on Github. One only supports Windows as its host OS and the other is relying on dependencies only available on Ubuntu. Though we will use Windows 7 on both as the host VM as it is the most popular for malware attacks.
Requirements
- Host Operating System: Ubuntu 16/18.04 or Windows 7/10
- Guest Operating System: Windows 7 Home Premium 64-Bit
- Software: VirtualBox 6.0.14
- Tools for VM-hardening: VBoxHardenedLoader (for Windows) and antivmdetection (for Ubuntu)
- Tool to check hardened VM: Pafish
- Tool to simulate network: FakeNet
Sandboxing on Windows
Before we start, make sure you have downloaded the following:
- Windows.iso
- VirtualBox
- VBoxHardenedLoader
- Pafish (recommended)
- FakeNet (recommended)
Regarding Pafish and FakeNet we recommend you to download them beforehand and make your own windows.iso that includes both. This will enable you to just drag and drop both from the virtual Windows installation CD on your VM, without the need to have a functioning Internet connection and download them.
Installing VirtualBox
The first step is to install VirtualBox. During the setup, we have to prevent it from installing the network drivers as they provide a weak point malware likes to scan for. After, finish the setup with the remaining configurations on default.
Basic VM setup
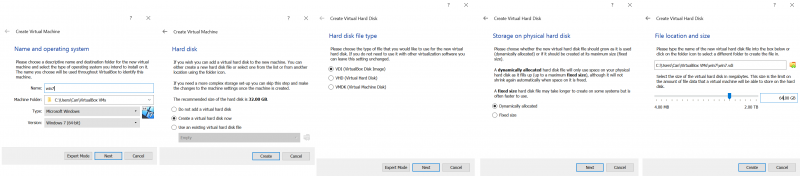
Having installed VirtualBox you should see the home screen with button to create a new virtual machine and settings.
As seen in the screenshots above (goes from left to right) we have assigned our VM the name 'win7' and chose the default path to save it. Next, we again chose the default options (VDI, because we will only use this disk with VirtualBox). The critical configuration here is the allocated disk and RAM size. Most advanced malware and our checking tool (Pafish) scans if your disk has less than 60GB and 2GB of RAM. So we advise you to set the disk to at least 64GB (recommended is +80GB) and RAM at least 2GB.
Advanced VM setup
Starting VBoxHardenedLoader
Make sure to read
- War and Peace
- Lord of the Rings
- The Baroque Cycle
Sandboxing on Ubuntu
Used Hardware
Device to be used with this documentation Maybe another device to be used with this documentation
Courses
- A course where this documentation was used (2017, 2018)
- Another one (2018)