Difference between revisions of "W3af - Web application attack and audit framework"
EPelanovic (talk | contribs) (Created page with "= Newest Kali Linux VM or MacOS Installation (2024) = == Summary == This document is a Step-by-Step Guide on how to install and use w3af (command line, no GUI). w3af is a fully comprehensive environment for web application testing and exploitation. It provides a solid platform for web vulnerability assessments and penetration testing. w3af is able to identify 200+ vulnerabilities, including Cross-Site Scripting (XSS), SQL injection and OS commanding. == Requiremen...") |
EPelanovic (talk | contribs) |
||
| Line 50: | Line 50: | ||
[[File:SolutionW3AF.png|900px]] | [[File:SolutionW3AF.png|900px]] | ||
Here are the commands again if a copy & paste is needed. The "--network host" parameter is important to be able to scan websites within the virtual machine which run locally, because w3af runs in a docker container. Be careful to change the path accordingly. | Here are the commands again if a copy & paste is needed. The "--network host" parameter is important to be able to scan websites within the virtual machine which run locally, because w3af runs in a docker container. Be careful to change the path accordingly. What is done here is a port forwarding from the docker container to localhost and then a SSH session is created to the container. | ||
$ docker run -d --network host -p 22:22 --name w3af andresriancho/w3af | $ docker run -d --network host -p 22:22 --name w3af andresriancho/w3af | ||
Latest revision as of 18:02, 16 January 2024
Newest Kali Linux VM or MacOS Installation (2024)
Summary
This document is a Step-by-Step Guide on how to install and use w3af (command line, no GUI). w3af is a fully comprehensive environment for web application testing and exploitation. It provides a solid platform for web vulnerability assessments and penetration testing. w3af is able to identify 200+ vulnerabilities, including Cross-Site Scripting (XSS), SQL injection and OS commanding.
Requirements
Make sure you have the following software ready before starting the installation:
- Git client: sudo apt-get install git
- Python
- Pip
- Docker (whatever version)
- Kali Linux (in my case as a VM in Windows 10) or MacOS
Description
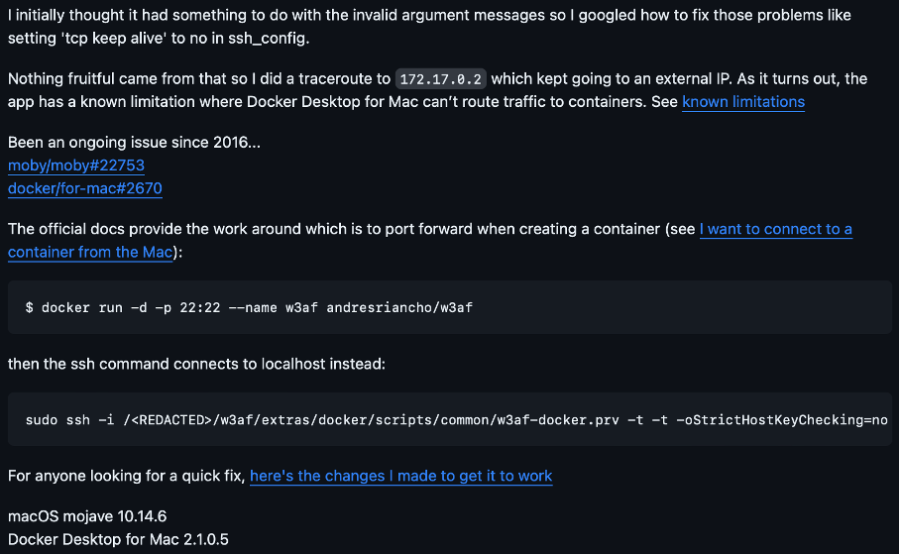
In my case the normal installation steps which were shown on "http://docs.w3af.org/en/latest/install.html" didn't worked out, because dependencies and packages are not available or do not work with newer operating systems, particularly for the GUI. Neither the w3af package was found like it was shown in the "Kali Linux Installation" section. Therefore the Docker Installation version was used with some modifications in order to start the w3af console.
Installation
Enter these commands in the shell
git clone https://github.com/andresriancho/w3af.git cd w3af/extras/docker/scripts/ sudo ./w3af_console_docker
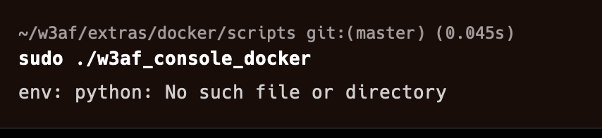
If you are using MacOS after executing the last command it is possible that you got the following error:
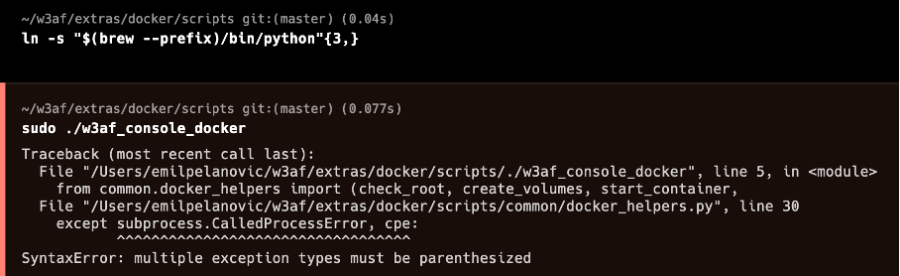
Type in the following command and try it again. In both MacOS Linux you will get the following error message which is because of Python.
Replace in the displayed file named "docker_helpers.py" the "," in the exception with an "as" on every place where it is. It should be used on two places. Execute the command again and you should get the following result:
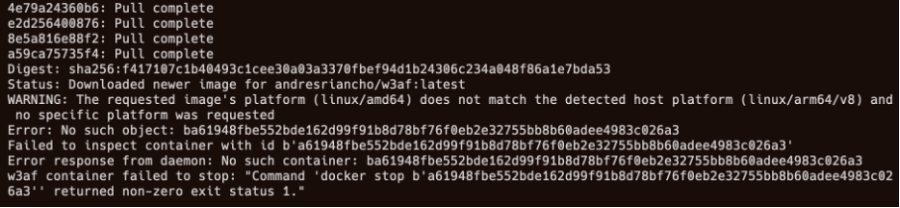
This problem was also described here:
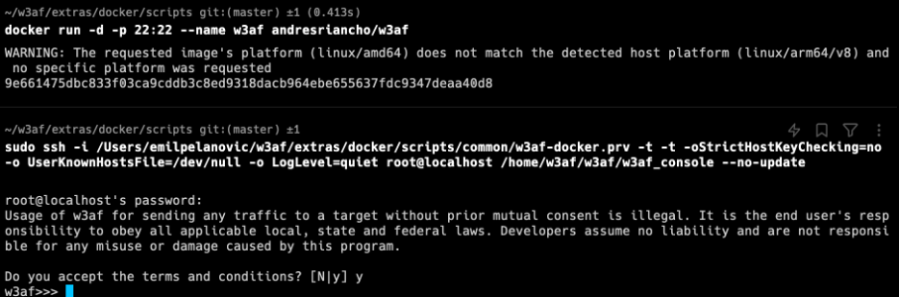
Running the following commands with following credentials should be the solution (username=root ; password=w3af):
Here are the commands again if a copy & paste is needed. The "--network host" parameter is important to be able to scan websites within the virtual machine which run locally, because w3af runs in a docker container. Be careful to change the path accordingly. What is done here is a port forwarding from the docker container to localhost and then a SSH session is created to the container.
$ docker run -d --network host -p 22:22 --name w3af andresriancho/w3af
$ sudo ssh -i /<REDACTED>/w3af/extras/docker/scripts/common/w3af-docker.prv -t -t -oStrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null -o LogLevel=quiet root@localhost /home/w3af/w3af/w3af_console --no-update
Then the w3af console should finally run.
Scanning
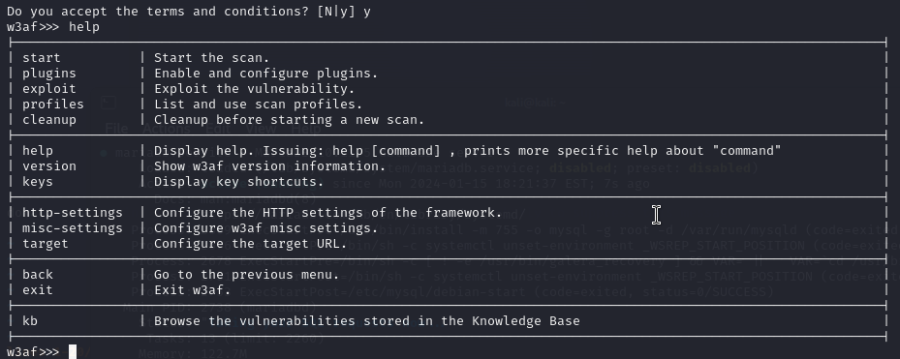
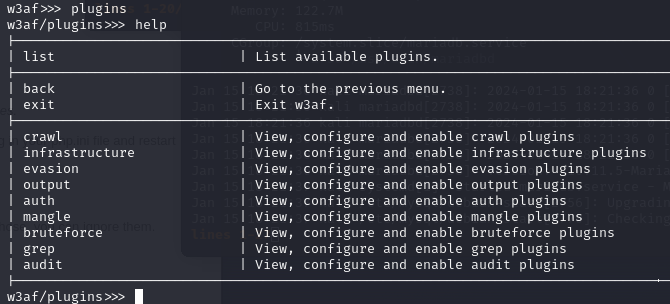
To make you familiar with the tool you can first type in "help" to see what commands are available:
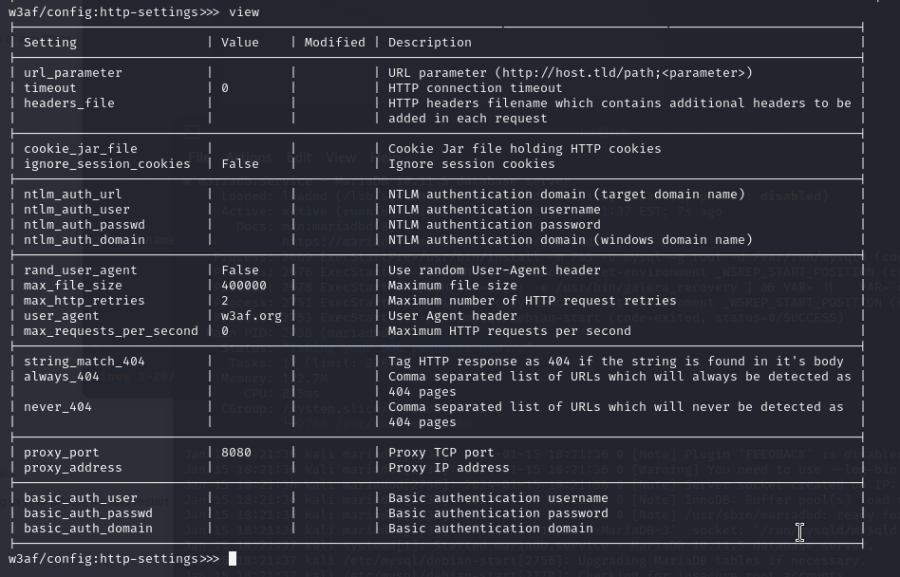
If you want to do some authenticated scans you have to play around with "http-settings like in the following two screenshots:
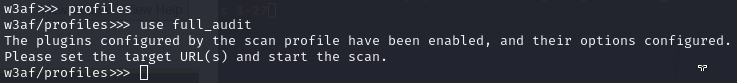
To be able to start a scan you can configure plugins. Switch to plugins (type in "plugins") and then enter "help" to see what opportunities you have:
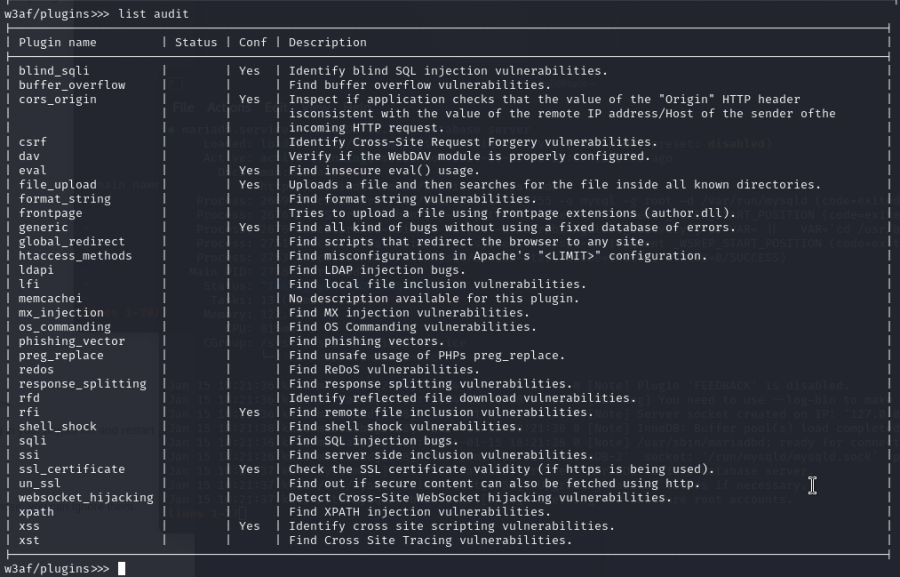
To view for example the "audit" plugin in more detail, enter "list audit":
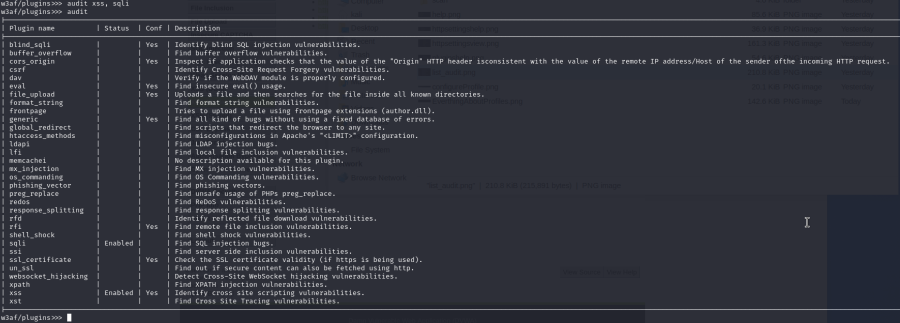
To enable some plugins of your choice in audit type in the appropriate plugin name:
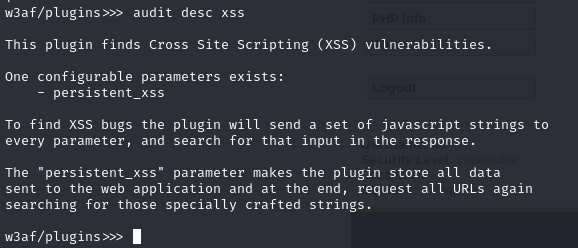
You can also view the details of the plugin itself:
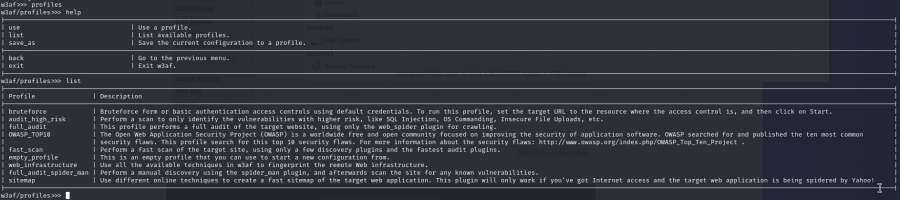
There are also prefabricated profiles which can be chosen like it can be seen in the following:
To choose a profile enter like in the screenshot below:
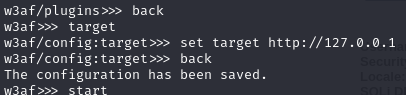
At the end, specify a target and start the scan:
Results
The results are printed out at the console. They can be copied to a textfile to maybe be searchable.
Exploitation
If for example an sql injection vulnerability was found by the tool, the following can be chosen out of the exploits:
Deprecated Ubuntu 12.04 Installation (GUI version)
For everyone who wants to use the tool with Ubuntu 12.04 the following needs to be done:
Requirements
- Linux-based System - preferably Ubuntu 12.04 LTS
- Python2
Description
Installation
Enter these commands in the shell
sudo apt-get install git sudo apt install python2.7 git clone git@github.com:andresriancho/w3af.git cd w3af/ ./w3af_gui ./tmp/w3af_dependency_install.sh
In short, what happens here:
- We use git to download w3af’s source code
- Then we switch into a directory which contains some scripts
- Execution of w3af_console_docker script
Edit (Jan. 2023): Currently there might be new errors starting w3af_gui, therefore you might have to downgrade specific dependencies/packets or use an older OS (i.e. Ubuntu 12.04).
Scanning
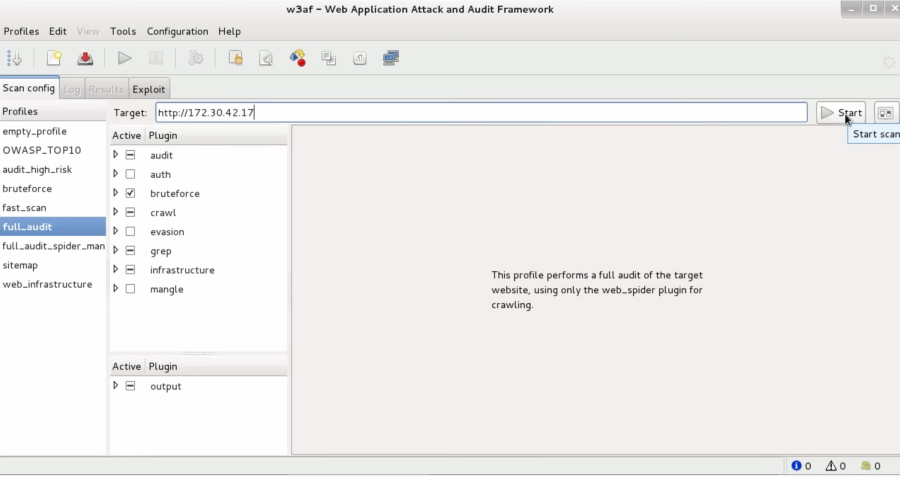
This is how the GUI looks like:
On the left hand side, you can find different profiles, that have different plugins to select and configure. Under the plugin section, there are different plugin groups:
- audit
- bruteforce
- crawl
- infrastructure
- evasion
- grep
- mangle
- output
After selecting a plugin, in the window on the right is a description regarding the plugin and its configurations. To configure the plugin, just select it, and modify the options that appears in the right window. You need to save the configuration to use it.
To finish the configuration for the scan, you need to insert a target URL in the upper text entry.
After selecting the profile, the plugins and typed in the URL, you can start the scan with clicking on start.
After starting the scan, the Log Pane will be opened, where in the upper part you have the logging text & below that messages you can see what the system is currently doing. Also on the right bottom side, there are three indicators showing the quantity of information items found, vulnerabilities found, & the shell, which were successfully exploited.
Results
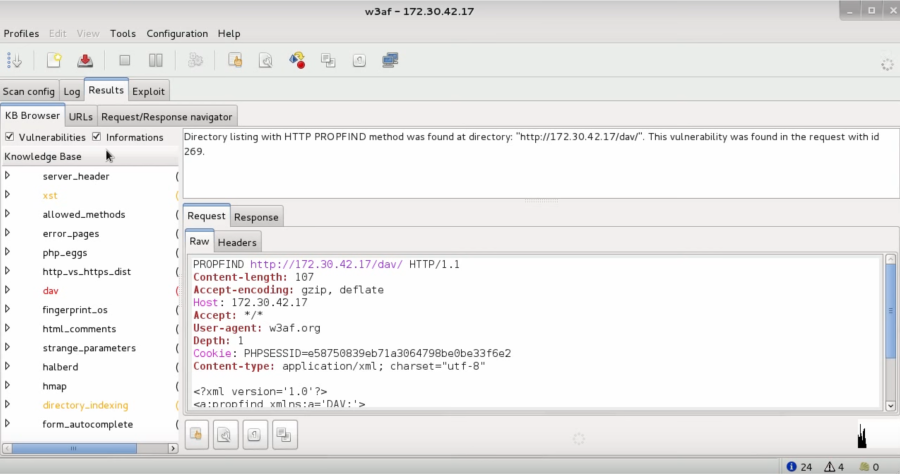
During the scan or after finishing the scan, you can look in the results tab:
On the left side, it shows you the vulnerabilities and informations. When selecting one of the items, and that item corresponds to a HTTP request originated by the scanning, you can see it on the right side with its information. The colours indicate the severity of the vulnerability and have the following meaning:
- black for information,
- orange for low severity
- red for medium/high severity.
Exploitation
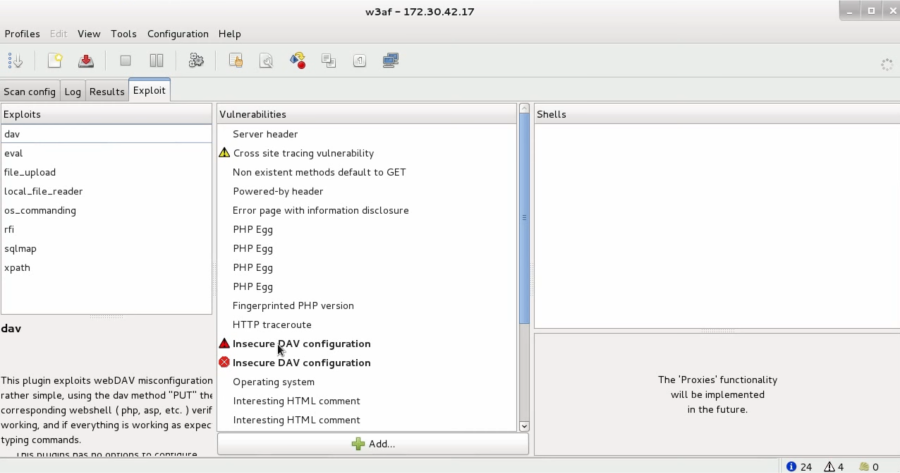
We can also use exploits in w3af:
In order to exploit a vulnerability, you need to drag the exploit to the vulnerability you want to exploit and drop it there. This drag-and-drop process is all you need to activate a particular vulnerability.
Apart from the w3af core functionality, that is to scan for vulnerabilities and exploit them, there are other tools that can be used, to find them follow the guide (Tools section) under the References section.