Difference between revisions of "Web Application Analysis"
| Line 7: | Line 7: | ||
* Notebook or VM running a Linux distribution (ideally Kali Linux) | * Notebook or VM running a Linux distribution (ideally Kali Linux) | ||
* Internet connection (There are downloadable Testbeds too, an Internet connection is not required after install) | * Internet connection (There are downloadable Testbeds too, an Internet connection is not required after install) | ||
== Web Application Security == | |||
'''Web Application Security'' describes a branch in the information security | |||
=== Securitry Threats === | |||
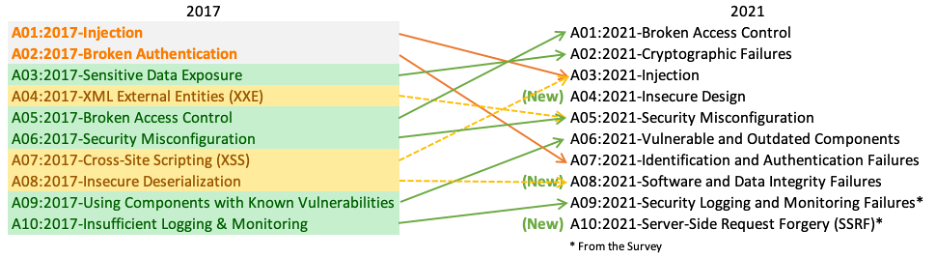
There is a magnitude of security threats that can occur in a website or web application. The Open Web Application Security Projekt (OWASP) publishes every four years the OWASP Top 10 report, including the ten most occurring security threats. Here is a comparison between the year 2017 and the year 2021: | |||
[[File:OwaspTop10.png]] | |||
These vulnerabilities are easily avoidable but end up over and over on the Top 10 list. One common reason for them being this high listed is the lack of knowledge of the developer. Because knowledge and understanding of the possible threats are so important, there are many test and learning platforms specially made to train and improve best practice security policies. | |||
== Web Application Scanning Tool == | == Web Application Scanning Tool == | ||
| Line 21: | Line 32: | ||
Many tools come pre-installed with Kali Linux. They are used for information gathering, exploitation and testing throughout the development of web applications. | Many tools come pre-installed with Kali Linux. They are used for information gathering, exploitation and testing throughout the development of web applications. | ||
== Courses == | == Courses == | ||
Revision as of 17:06, 18 December 2021
Summary
Web Application Analysis is engaged in finding and vulnerabilities and if necessary to harden current security measures. The analysing process should be contemplated for every web application. It might reveal exploits that would cause devastating consequences. Unprotected websites and web applications are targeted by hackers and often lead to database leaks, theft of banking information and infringement of privacy. Many companies are not technically adept and therefore cannot evaluate the possible damage, hoping to save costs in the development phase by skipping the web application analysis.
Requirements
- Notebook or VM running a Linux distribution (ideally Kali Linux)
- Internet connection (There are downloadable Testbeds too, an Internet connection is not required after install)
Web Application Security
'Web Application Security describes a branch in the information security
Securitry Threats
There is a magnitude of security threats that can occur in a website or web application. The Open Web Application Security Projekt (OWASP) publishes every four years the OWASP Top 10 report, including the ten most occurring security threats. Here is a comparison between the year 2017 and the year 2021:
These vulnerabilities are easily avoidable but end up over and over on the Top 10 list. One common reason for them being this high listed is the lack of knowledge of the developer. Because knowledge and understanding of the possible threats are so important, there are many test and learning platforms specially made to train and improve best practice security policies.
Web Application Scanning Tool
It is possible to perform web application analysis by hand but it is slower and mistakes can more easily happen. Using software tools created for finding vulnerabilities the efficiency increases significantly. For this purpose were a bunch of tools developed. A few of those are:
- skipfish
- ZAP
- WpScan
- sqlmap
- commix
- ...
Many tools come pre-installed with Kali Linux. They are used for information gathering, exploitation and testing throughout the development of web applications.
Courses
- A course where this documentation was used (2017, 2018)
- Another one (2018)