Web Application Analysis
Summary
Web Application Analysis is engaged in finding and vulnerabilities and if necessary to harden current security measures. The analysing process should be contemplated for every web application. It might reveal exploits that would cause devastating consequences. Unprotected websites and web applications are targeted by hackers and often lead to database leaks, theft of banking information and infringement of privacy. Many companies are not technically adept and therefore cannot evaluate the possible damage, hoping to save costs in the development phase by skipping the web application analysis. [1][2]
Web Application Security
Web application analysis is a branch in the IT security field that deals with web vulnerabilities and how to find them. Using it vulnerabilities that were overlooked in the development can be found and eliminated before they can be exploited.
Security Threats
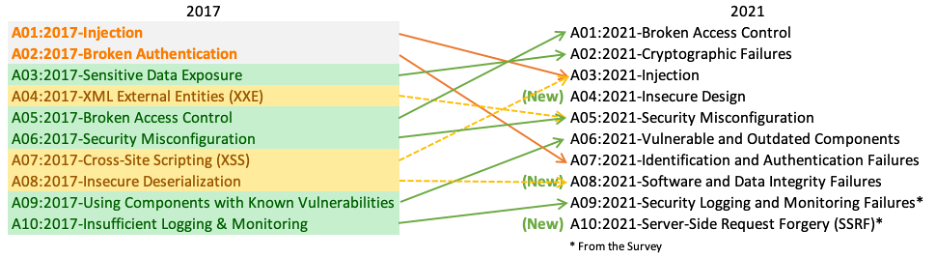
There is a magnitude of security threats that can occur in a website or web application. The Open Web Application Security Projekt (OWASP) publishes every four years the OWASP Top 10 report, including the ten most occurring security threats [3]. Here is a comparison between the year 2017 and the year 2021:
These vulnerabilities are easily avoidable but end up over and over on the Top 10 list. One common reason for them being this high listed is the lack of knowledge of the developer. Because knowledge and understanding of the possible threats are so important, there are many test and learning platforms specially made to train and improve best practice security policies.
Web Application Scanning Tool
It is possible to perform web application analysis by hand but it is slower and mistakes can more easily happen. Using software tools created for finding vulnerabilities the efficiency increases significantly. For this purpose were a bunch of tools developed. A few of those are:
- skipfish
- ZAP
- WpScan
- sqlmap
- commix
- ...
Many tools come pre-installed with Kali Linux. They are used for information gathering, exploitation and testing throughout the development of web applications. These tools run a set of tests to see how the application reacts and analyses those reactions. Depending on the kind of reaction the tools recieve they evaluate if an attack could be accomplished or not. The positive/false ratio is usually pretty low, which is an indication of how accurate they are. [5]
There are 3 ways to test web applications: static, dynamic or interactive.
Static Application Security Testing (SAST)
Static Application Security Testing is also called white-box testing. It is a testing method where the source code is available to the tester. Using code reviews and analysing tools mistakes can be corrected. This technique is usually only used internally because access to the code needs to be granted.
Dynamic Application Security Testing (DAST)
Dynamic Application Security Testing is the testing method that first comes to mind when talking about web application analysis. It can be done by anyone because it does not require access to the source code of the application. This technique is a black-box testing method, meaning the structure is hidden and information can only be assumed by sending requests and analysing the responses. The tools mentioned in this article are all DAST tools.
Interactive Application Security Testing (IAST)
Contrary to SAST and DAST, IAST analyses threats in real-time while the application is executed and work from inside of the web application. Usually, it gets combined with the other testing methods to simulate an attacker trying to break in.
Commix
Commix, which stands for [Comm]and [I]njection E[x]ploiter, is an open-source penetration testing tool. It is used to find and exploit command injection vulnerabilities in web applications. [6]
To install commix it needs to be cloned from its Github repository:
git clone https://github.com/commixproject/commix.git commix
In the downloaded folder is a file called commix.py that can be executed using:
python commix.py [command]
to see a list with possible commands enter:
python commix.py -h
It is possible to gather information about the structure of the attacked machine and to create a shell giving the attacker lots of control over the server running the application.
Skipfish
Skipfish is a tool that allows quick scanning of websites and web applications for vulnerabilities and threats. After finishing the scan it presents its results in an interactable sitemap and lists the findings according to their importance. [7]
It can only be used for information gathering and cannot be used to exploit vulnerabilities. Because it is written in C it runs very performant and handles many requests and responses without loading the CPU.
To install Skipfish use:
sudo apt-get install skipfish
After installing a list of the available commands can be listed using the command:
skipfish -h
WPScan
WPScan stands for WordPress Scanner. WordPress is a popular tool for creating websites. It is often used for blogs and private websites that are hosted by a single private person. It is estimated that over 43% of all websites on the Internet are powered by WordPress. This makes it a popular target for attackers, so popular that it even got its own tool. It scans web applications using a database with 24500+ registered WordPress vulnerabilities.
To install it you need to clone the git repository:
git clone https://github.com/wpscanteam/wpscan.git
It does not work on windows but there are virtual machines that can be downloaded instead.
When using Linux some dependencies need to be installed depending on the Linux version:
- Ubuntu 14.04+ command:
sudo apt-get install libcurl4-openssl-dev libxml2 libxml2-dev libxslt1-dev ruby-dev build-essential
- Prior to Ubunto 14.04 command:
sudo apt-get install libcurl4-openssl-dev libopenssl-ruby libxml2 libxml2-dev libxslt1-dev ruby-dev
- Debian command:
sudo apt-get install git ruby ruby-dev libcurl4-openssl-dev make
- Fedora command:
sudo yum install gcc ruby-devel libxml2 libxml2-devel libxslt libxslt-devel libcurl-devel patch
- ArchLinux:
pacman -Syu ruby
WPScan runs on Ruby which means it requires "gems". After installing it WPScan can be started.
For available commands use
ruby wpscan.rb -h
Testing Environments
Because testing for vulnerabilities on someone else website is illegal without the owner's consent it can be difficult to build up experience. To help overcome this problem testing environments were created. These environments are there to recreate real-world cases safely and legally. Eventually, docker is needed, this varies between the different testing environments.
A few well known intentional web applications are:
- Damn Vulnerable Web Application (DVWA)
- buggy Web Application (bWAPP)
- CommixProjext/commix testbed
- and others
They should never be hosted on the Internet because of their intentional flaws. They are meant to be tested on a virtual machine or locally to be safe.
After downloading they are ready to use. The included challenges are often organized into different categories and sorted with increasing difficulty.
Requirements
- Notebook or VM running a Linux distribution (ideally Kali Linux)
- Internet connection (There are downloadable Testbeds too, an Internet connection is not required after install)
References
- ↑ https://blog.stackpath.com/web-application/
- ↑ https://www.w4rri0r.com/hacking-tools-windows-os-x-linux-android-solaris-unixware/web-application-analysis.html
- ↑ https://owasp.org/
- ↑ https://owasp.org/www-project-top-ten/
- ↑ https://www.imperva.com/learn/application-security/application-security-testing/
- ↑ https://www.kali.org/tools/commix/
- ↑ https://code.google.com/archive/p/skipfish/