WiFI Pineapple Mark VII: Cracking WPA/WPA2-PSK with a dictionary/brut force attack
Summary
This Documentation will give you a guide how to retrieve a WPA2-PSK password with the Wi-Fi Pineapple Mark VII combined with the Linux Tool aircrack-ng. The Wi-Fi Pineapple Mark VII will be used to deauthenticate the clients of the victim's Wi-Fi. Simultaneously, the Wi-Fi Pineapple Mark VII will capture the 4-way handshake between client and access point and saves it as a PCAP or Hashcat file. This guide will use Linux to demonstrate how to use aircrack-ng.
Requirements
Remember: The hacking tools and knowledge that we share here should not be used on a target without prior mutual consent. It is the end user's responsibility to obey all applicable local, state and federal laws. We assume no liability and are not responsible for any misuse or damage caused by this site
Mandatory
GNU/Linux
- Install aircrack-ng suite:
sudo apt install aircrack-ng
To complete these steps, you must have followed WiFI Pineapple Mark VII: Initial Setup before.
Optional
Hashcat
- Clone GIT repository:
git clone https://github.com/hashcat/hashcat.git - Build:
cd ./hashcat && make && make install - Link:
sudo ln -s ./hashcat /usr/local/bin/hashcat
Description
Step 1 (Deauthenticate Client & Capture Handshake)
This step will describe you how to capture the handshake by deauthenticating the clients from its access point
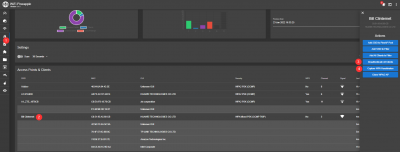
- Log in to Wi-Fi Pineapple Web GUI and open the tab Reacon
- As seen in figure "WiFI Pineapple GUI", scan your environment for the victim's Wi-Fi (1).
- Choose the victim's Wi-Fi and select "Capture WPA Handshake"(4)
- Start deauthentication attack (3)
- When a handshake has been captured, it can be then downloaded
Step 2 (Dictionary Attack)
The purpose of this step is to actually crack the WPA/WPA2 pre-shared key. To accomplish this, you need a dictionary of words as input. Basically, aircrack-ng takes each word and tests to see if this is, in fact, the pre-shared key.
Open a console session in Linux and enter:
aircrack-ng -w rockyou.txt -b 00:14:6C:7E:40:80 *.cap
Where:
-w rockyou.txt[1] is the name of the dictionary file. Remember to specify the full path if the file is not located in the same directory. Notice: any word list can be use for this attack. If the password you are looking for does not appear in the list, then the attack has failed.
.cap is the file containing the captured packets of the handshake.
Here is typical output when there are no handshakes found:
Opening psk-04.cap
Read 1827 packets.
No valid WPA handshakes found.
When this happens, you either have to redo step 3 (deauthenticating the wireless client) or wait longer if you are using the passive approach. When using the passive approach, you have to wait until a wireless client authenticates to the AP.
Here is typical output when handshakes are found:
Opening psk-04.cap
Read 1827 packets.
# BSSID ESSID Encryption
1 00:14:6C:7E:40:80 teddy WPA (1 handshake)
Choosing first network as target.
Now, at this point, aircrack-ng will start attempting to crack the pre-shared key. Depending on the speed of your CPU and the size of the dictionary, this could take a long time, even days.
Here is what successfully cracking the pre-shared key looks like:
Aircrack-ng 0.8
[00:00:00] 2 keys tested (37.20 k/s)
KEY FOUND! [ 12345678 ]
Master Key : CD 69 0D 11 8E AC AA C5 C5 EC BB 59 85 7D 49 3E
B8 A6 13 C5 4A 72 82 38 ED C3 7E 2C 59 5E AB FD
Transcient Key : 06 F8 BB F3 B1 55 AE EE 1F 66 AE 51 1F F8 12 98
CE 8A 9D A0 FC ED A6 DE 70 84 BA 90 83 7E CD 40
FF 1D 41 E1 65 17 93 0E 64 32 BF 25 50 D5 4A 5E
2B 20 90 8C EA 32 15 A6 26 62 93 27 66 66 E0 71
EAPOL HMAC : 4E 27 D9 5B 00 91 53 57 88 9C 66 C8 B1 29 D1 CB
Step 3 (Brut Force Attack)
In this method, we will be using both crunch and aircrack-ng inside Kali Linux to brute-force WPA2 passwords. But before we proceed, let me briefly introduce you to our tools:
crunch - is a wordlist generator from a character set.
aircrack-ng - a 802.11 WEP / WPA-PSK key cracker.
I assume you already have aircrack-ng installed on your system, and you already have a captured handshake ready for offline cracking. If not, I will post another article soon on how to use aircrack-ng to capture WPA2 handshakes.
For now let's get started and open a terminal!
If you don't have crunch, yet you can install it by typing:
sudo apt-get install crunch
It usually takes crunch a long time to create a wordlist and consumes a lot of disk space too if you choose to save the wordlist to your hard drive. Therefore, this technique can only be useful if somehow you already have an idea of what the password pattern is. The default Wi-Fi passwords of modem/routers provided by ISP's for example can be a target.
Let's say that after your research, you figured out that the default Wi-Fi password is an 8-digit number that always starts with the number 7. From that information, we can now create a wordlist using crunch and deliver the output directly to aircrack-ng without writing the file to the hard drive.
This can be done using pipes:
crunch 8 8 0123456789 -s 70000000 | aircrack-ng -w - -b AA:BB:CC:DD:00:11 /path/to/handshake.cap
The first command above (the one before the pipe) means that we'll create a wordlist using crunch with a minimum of 8 characters and a maximum of 8 characters (since we know that the password always use 8 digits) using only numbers 0 to 9. The "-s" also tells crunch to start the list from 70000000.
We can then use pipes to make the standard output (stdout) of the first command to be the standard input (stdin) of the second command. Thus, whatever output crunch generates will be used by aircrack-ng as the wordlist.
In the second command, the "-w -" tells aircrack-ng to use the wordlist from stdin (that's what the dash means). The "-b" is used to specify the bssid of the targer router (AA:BB:CC:DD:00:11) and the last parameter (/path/to/handshake.cap) is the absolute path to the captured WPA2 handshake. You can also use a relative path depending on your current working directory.
Now, the cracking process may take a while depending on your processor speed, but I believe it is possible to crack that password pattern within a few seconds to a couple of hours.
In my next articles I will show you how you can create rules with crunch even with complicated patterns such as passwords with common words inside.
Used Hardware
Courses
- Campus Cyber Security Team WiFi Hacking 28.01.2022