WikiLeaks
Summary
This documentation is about WikiLeaks, media organization and Web site that functioned as a clearinghouse for unethical, illegal or otherwise privileged information. WikiLeaks was founded in 2006 by Australian computer programmer and activist Julian Assange.
Awards
WikiLeaks, its publisher and its journalists have won many awards, including:
- The Economist New Media Award (2008)
- The Amnesty New Media Award (2009)
- TIME Magazine Person of the Year, People's Choice (highest global vote) (2010)
- The Sam Adams Award for Integrity (2010)
- The National Union of Journalists Journalist of the Year (Hrafnsson) (2011)
- The Sydney Peace Foundation Gold Medal (2011)
- The Martha Gellhorn Prize for Journalism (2011)
- The Blanquerna Award for Best Communicator (2011)
- The Walkley Award for Most Outstanding Contribution to Journalism (2011)
- The Voltaire Award for Free Speech (2011)
- The International Piero Passetti Journalism Prize of the National Union of Italian Journalists (2011)
- The Jose Couso Press Freedom Award (2011)
- The Privacy International Hero of Privacy (2012)
- The Global Exchange Human Rights People's Choice Award (2013)
- The Yoko Ono Lennon Courage Award for the Arts (2013)
- The Brazillian Press Association Human Rights Award (2013)
- The Kazakstan Union of Journalists Top Prize (2014)
As well as nominations for the UN Mandela Prize (2015) and nominations in six consecutive years for the Nobel Peace Prize (2010-2015)
About
“WikiLeaks is a giant library of the world's most persecuted documents. We give asylum to these documents, we analyze them, we promote them and we obtain more.” - Julian Assange, Der Spiegel Interview
The founder - Julian Assange
Assange gained his first programming experience on a Commodore 64 computer, and in 1987 he also acquired an Internet hub. He began his hacking activities under the pseudonym “Mendax” (Latin: noble liar). He and two other hackers formed a group called “International Subversives.” This activity led to the Australian Federal Police in 1991 In 1992, Julian Assange was found guilty of 24 counts of illegal hacking and the court ordered him to pay A 2,100 dollar and put him on probation. In 1995, Assange wrote his first free software, called Strobe.
During his hacker activities he became acquainted with his later wife. They moved together in 1989 and had a son. They divorced in 1991. In 1999, after a one-year legal dispute, Assange and her mother, Christine, reached joint custody of the child’s mother.
He has been involved with WikiLeaks since 2006. He claims to have made a living on the internet and is therefore able to work for WikiLeaks without pay. During his work on WikiLeaks, he was arrested, interrogated, censored and sued several times, all to no avail.
History
WikiLeaks is an international nonprofit organization. It publishes leaked government and other documents on the Internet that exposes an unethical, illegal case or process, while keeping its sources anonymous. The system that enables file uploads is implemented via the Tor anonymization network. The website was launched in 2006, operated by The Sunshine Press. WikiLeaks claims that its founders were professionals from Chinese dissidents, journalists, mathematicians and start-ups who came to the organization from the United States, Europe, Taiwan, Australia and South Africa. Sweden was originally the site of the founding, and the public face was Australian exhacker Julian Assange.
According to the staff, the database of the site contained 1.2 million documents a year after its launch. The most echoed leaks were the nearly 92,000 military and similar secret documents related to the war in Afghanistan, the “Collateral Murder” video, the nearly 400,000 secret military reports released during the Iraq war, and 250,000 various messages sent by U.S. diplomats. Following the leak of diplomatic messages, the U.S. government launched a drive hunt against WikiLeaks, over and above Visa, Mastercard and PayPal refused to pass on donations to them.
Chronology
2006
The domain wikileaks.org is registered. The founders of Wikileaks, including Julian Assange, have made it their business to anonymously publish previously secret documents.
2007
Wikileaks is publishing documents for the first time and getting a bit of attention. Among other things, the founders put internal manuals from the US prison camp Guantanamo online. They prove the psychological torture methods used by the military. This year Julian Assange met his biggest supporter and partner, Daniel Domscheit-Berg.
2010
- Wikileaks lands its first big coup: video footage of a US military helicopter attacking civilians in 2007, including two reporters. The skepticism towards Wikileaks is still high.
- US soldier Chelsea Manning is arrested in Iraq. She is alleged to have leaked documents, including the video of the US attack on civilians in 2007, to Wikileaks.
- In cooperation with the British "The Guardian", the US American "New York Times" and the German "Spiegel", Wikileaks is going public with war documents: the "Afghan War Diaries" determine the news.
- Daniel Domscheit-Berg, German spokesman for Wikileaks, leaves the project in a dispute with Assange.
- Assange has been arrested in Sweden on charges of sexual assault and rape. He is wanted by Interpol, later arrested and released on bail. He is then under house arrest.
- The domain wikileaks.org is temporarily unavailable. Companies like Amazon, Paypal, Visa or Mastercard stop working with Wikileaks due to political pressure.
- In the meantime, the Wikileaks pages are "mirrored", so the content is stored as a copy on numerous servers around the world. However, no more documents can be uploaded.
2011
- "Der Freitag" reports a data leak at Wikileaks - for months all unprocessed US dispatches were freely accessible on the Internet, with all of the original senders. A British journalist's book contained the password to decrypt the file. In response, Wikileaks publishes all US cables on September 2nd, unprocessed.
- Wikileaks publishes the so-called SpyFiles and cooperates with the NDR for the first time.
2012
- Millions of emails from the US company Stratfor can be found in "The Global Intelligence Files" on Wikileaks. Partners, including the NDR, are given a preview of the data.
- After the British Supreme Court allowed Assange to be extradited to Sweden, the Wikileaks founder fled to the Ecuadorian embassy in London before being arrested. He applies for political asylum.
2016
- Whistleblower Chelsea Manning has been sentenced to 35 years in prison, among other things, for espionage.
- Wikileaks publishes emails from the account of John Podesta, campaign manager for Democratic presidential candidate Hillary Clinton. Representatives of the Clinton campaign accuse Wikileaks of promoting Russia's President Vladimir Putin. Ecuador then restricts Julian Assange's internet access for a while.
- Internal documents from the NSA committee of inquiry appear on Wikileaks.
2017
- US President Barack Obama pardons Chelsea Manning in one of his final acts.
2018
- It is revealed that the US is planning to bring charges against Julian Assange of treason. The proceedings in Sweden are now suspended.
2019
- Wikileaks publishes over 30000 documents from SAMHERJI and 2 other leaks came out this year
- Chelsea Manning is arrested again for refusing to testify in the Julian Assange trial.
- Julian Assange is arrested in London. Ecuador had previously withdrawn his diplomatic asylum and is allowing British police officers to enter the embassy. Scotland Yard confirms that the US has requested extradition against Assange.
2021
- WikiLeaks publishes "The Intolerance Network" over 17,000 documents from internationally active right wing campaigning organisations HazteOir and CitizenGO.
- "Julian Assange faces a 175 year prison sentence in the United States for publishing documents, including those which exposed wilful, or otherwise reckless, sabotage of climate action during prior climate change summits." - Wikileaks site
Famous Leaks
- US Military Equipment in Afghanistan - The full equipment register of every US Army managed unit in Afghanistan from psychological operations ("PsyOps") and interrogation units to Kabul headquarters. [[US Military Equipment in Afghanistan]]
- Collateral Murder - A classified US military video depicting the indiscriminate slaying of over a dozen people in the Iraqi suburb of New Baghdad — including two Reuters news staff. [[Collateral Murder]]
- Hillary Clinton Email Archive - A searchable archive for over 30 thousand emails & email attachments sent to and from Hillary Clinton's private email server while she was Secretary of State. [[Hillary Clinton Email Archive]]
- Sony Files - 30,287 documents from Sony Pictures Entertainment (SPE) and 173,132 emails to and from more than 2,200 SPE email addresses. [[Sony Files]]
- CIA espionage orders for the 2012 French presidential election - All major French political parties were targeted for infiltration by the CIA's human and electronic spies in the seven months leading up to France's 2012 presidential election. [[CIA France Elections]]
VAULT 7 - CIA Hacking Tools
Vault 7: CIA Hacking Tools Revealed
It is a series of leaks on the U.S. Central Intelligence Agency. Code-named "Vault 7" by WikiLeaks, it is the largest ever publication of confidential documents on the agency. It was leaked on March 7th 2017 and contains a couple million lines of code and about 8761 documents and files. Vault 7 consists of trojans, viruses and malware that infest Iphones, Android devices, Windows devices and Samsung TVs.[[CIA Hacking Tools]]
Zero Day Exploits
Furthermore Vault 7 contains so called "Zero Day" exploits. These are Attacks on completely unknown weaknesses of different devices. This is even more important, because devices like Iphones and Android phones can also be targeted. Zero day exploits have an obvious problem. If the manufacturer of the device does not know about the weakness, it cannot fix it, which can lead to it losing in the global market.
Who leaked Vault 7?
There are 2 people that are under suspicion when it comes to Vault 7. The founder Julian Assange and an ex-CIA programmer with the name Joshua Schulte. Joshua Schulte has apparently leaked the documents and files that are contained in Vault 7 and because of that is under arrest since 2022.
Vault 7 Tools
All VAULT7 Tools can be found on the WikiLeaks website. Here is a list of their names and a small description from the WikiLeaks site:
- Project Dark Matter - contains documentation for several CIA projects that infect Apple Mac Computer firmware
- Marble Framework - 676 source code files for the CIA's secret anti-forensic Marble Framework
- Grasshopper Framework - a platform used to build customized malware payloads for Microsoft Windows operating systems
- HIVE (There is a leak from 2017 called VAULT8: Hive which is a source code repository related to the CIA Project Hive)
- Weeping Angel - the User Guide for CIA's "Weeping Angel" tool - an implant designed for Samsung F Series Smart Televisions
- Scribbles - the documentation and source code for CIA's "Scribbles" project, a document-watermarking preprocessing system
- Archimedes - a tool used by the CIA to attack a computer inside a Local Area Network
- After Midnight and Assassin - "AfterMidnight" and "Assassin", two CIA malware frameworks for the Microsoft Windows platform
- Athena - remote beacon and loader capabilities on target computers running Microsoft Windows
- Pandemic - a persistent implant for Microsoft Windows machines that share files in a local network
- Cherry Blossom - a means of monitoring the Internet activity of and performing software exploits on Targets of interest
- Brutal Kangaroo - targets closed networks by air gap jumping using thumbdrives
- Elsa - a geo-location malware for WiFi-enabled devices
- Outlaw Country - argets computers running the Linux operating system
- BothanSpy - designed to intercept and exfiltrate SSH credentials
- Highrise - an Android application designed to provide a redirector function for SMS
- UCL/Raytheon - documents from the CIA contractor Raytheon Blackbird Technologies for the "UMBRAGE Component Library" project
- Imperial - documents from the Imperial project of the CIA
- Dumbo - enabling a way to suspend processes utilizing webcams and corrupt any video recordings
- CouchPotato - the User Guide for the CoachPotato project of the CIA, a remote tool for collection against RTSP/H.264 video streams
- ExpressLane - documents from the cyber operations the CIA conducts against liaison services - which includes NSA, DHS and FBI.
- Angelfire - a persistent framework used to infect Microsoft Windows systems
- Protego - four secret documents from the Protego project of the CIA, along with 37 related manuals
Sonic Screwdriver
Sonic Screwdriver is an exploit contained in the project "Dark Matter". It was leaked on the 23rd, March 2017. With this attack the CIA is able to execute code from a connected device while a Mac device is booting. Usually this would need a firmware password, but this gets bypassed. For this exploit you need a Thunderbolt-to-Ethernet Adapter, an external USB-Drive or a CD/DVD-Drive and a Mac computer released between 2011 and 2012.
- Setup - The first step is to flash the adapter. This is done by booting an ISO file that is saved on a peripheral device and plugging it in combination with the thunderbolt-to-ethernet adapter into a Mac device. This will boot a FreeDos Operating System. There the command "B57UDIAG.exe -ppe x:\ss.rom" needs to be executed and the adapter is flashed. This adapter will look for a specific file path to execute from a USB or CD/DVD-Drive. This file path is "/EFI/BOOT/BOOTX64.efi". This filepath needs to be configured onto the before mentioned USB or CD/DVD-Drive.
- Execution - Now the thundebolt-to-ethernet adapter and the USB or the CD/DVD-Drive need to be connected to the target Mac device before it boots up. After the requirements are met, the adapter will automatically execute the BOOT64.efi file while the Mac computer boots up.
Weeping Angel
This attack was leaked on the 21th, april 2017 and is based on the "Extending Tool", that was developed together with the British Secret Service. This targets Samsung F Series Smart TVs. With this attack the built in microphone of the TV can be exploited to listen to conversations in real time or to record conversation and extract them per USB or Wi-Fi Hotspot. Futhermore it can put the TV into a fake off mode, to be even more hidden.
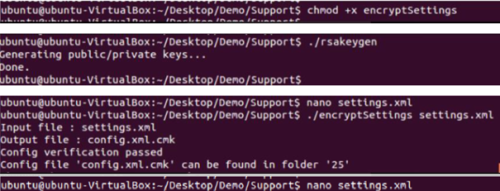
- Setup - First the Extending tool needs to be installed on a system. This tool consists of 2 folders: "Support" and "TV". The Support folder contains an unencrypted "Settings" file and tools for encryption, like an RSA key generator. The "TV" folder contains another folder named Update. The before mentioned tools need to be made executable first, with the commands "chmod +x encryptSettings" and "chmod +x rsakeygen". Now the RSA key generator needs to be executed with "./rsakeygen", which creates a key pair. This is used to encrypt the recorded conversations. With "nano settings.xml" configurations can be made for this attack. The important thing here is to set the public key so it can encrypt the recorded conversations. Lastly the encryptSettings tool needs to be executed with "./encryptSettings" and the output is a file named "config.xml.cmk". This file needs to be placed into the files.zip which is located in the previously mentioned "Update" folder.
- Execution - Now the whole Update folder needs to be saved into a USB device and connected to the TV. In the Smart Hub of the TV you can use the "More Apps" function to find the application "Update" and download it.
Highrise 2.0
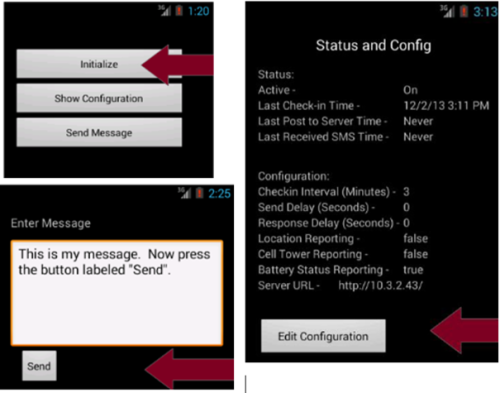
This attack was lead on the 13th, July 2017 and targets android devices. It is an application that is able to be installed on android devices with the version Android 4.0 to 4.3. Highrise 2.0 enables the attacker to redirect SMS messages, by creating an SMS Proxy that separates the device and the original receiver. This proxy can receive the outgoing messages of the device and redirect them to another user on the internet. Furthermore this application enabled the attacker to send messages to the receiver on the internet. To keep this attack hidden it hides itself on the android device with the name "TideCheck".
- Setup - This application can be downloaded from the internet, but the website is not available anymore. There was an older version of this exploit named "Highrise 1.4". If this was installed on the device before, it needs to be terminated. This is done by going into the settings and locating "TideCheck". Now the buttons "Force Stop", "Clear Data", and "Uninstall" need to be pressed in that exact order to uninstall the application. Now that all the requirements are met, Highrise 2.0 can be opened. Firstly it will prompt the attacker with password, which is "inshallah". Now 3 functions are displayed on the screen: "Initialize", "Show Configuration" and "Send Message". Initialize obviusly executes the the attack, which leads to the application being able to run in the background, whenever the android device is active. But before starting it the configurations need to be made. This is done by pressing the show configuration button. There are multiple options, but the 2 most important are the "Checkin Interval" and the "Server URL". For the Checkin Interval it is recommended to use 2-5 minutes and for the Server URL you need to set the receiver you want to redirect the SMS message to. The last function is the "send Message" button, which enables the attacker to send messages to the configured Server URL, for troubleshooting.
Security
- Sonic Screwdriver Prevention - Apple released a software update, that shuts down this attack on the 23rd, January 2017. With this update Mac devices no longer load optional ROMs while booting up. As the thunderbolt-to-ethernet adapter counts as an optional ROM it is not able to execute its filepath anymore, which leads to the attack being unable to be executed.
- Weeping Angel Prevention - The Extending tool has some limitations which are also specified in the documentation. First of all the voice recognition feature of the TV needs to be disabled for this exploit to work. So by simply enabling it it can cause troble for this attack. Furthermore it would be benefical for the user to turn of the internet connection to the TV, when it is not necessary.
- Highrise 2.0 Prevention - This exploit needs to be manually installed on the anroid device and cannot be remotely installed. Knowing this the user can simply uninstall the application, if it is found on the android device by using the method mentioned in the previous chapter "Highrise 2.0". Now the attacker would need to gain physical access to the device again.
References
- WikiLeaks Logo: https://de.wikipedia.org/wiki/WikiLeaks
- https://wikileaks.org/What-is-WikiLeaks.html
- https://wikileaks.org/-News-.html
- https://wikileaks.org/-Leaks-.html
- https://www.britannica.com/topic/WikiLeaks
- https://www.ndr.de/fernsehen/sendungen/zapp/medienpolitik/Wikileaks-eine-Chronologie,wikileaks300.html
- https://support.apple.com/de-at/guide/security/secc80b0cd0c/web
- https://wikileaks.org/vault7/document/SonicScrewdriver_1p0/
- https://wikileaks.org/vault7/document/HighRise-2_0-Users_Guide/
- https://wikileaks.org/vault7/document/EXTENDING_User_Guide/
- https://coed.com/2017/03/08/weeping-angel-cia-hack-protection-guide-how-to-prevent-protect-samsung-tv-info/
- https://www.nytimes.com/2022/07/13/nyregion/cia-engineer-joshua-schulte-theft-convicted.html
- https://wikileaks.org/ciav7p1/