Difference between revisions of "Wireshark: Traffic analysis of a smart alarm system"
Jostrowski (talk | contribs) |
Jostrowski (talk | contribs) m (typo) |
||
| Line 190: | Line 190: | ||
== References == | == References == | ||
;I found | ; I found an interesting presentation very similar to my findings: | ||
:https://site.ieee.org/neworleans/files/2016/12/12052016-Presentation-IoT-security-website-copy.pdf | : https://site.ieee.org/neworleans/files/2016/12/12052016-Presentation-IoT-security-website-copy.pdf | ||
[[Category:Documentation]] | [[Category:Documentation]] | ||
Revision as of 10:15, 30 January 2020
Summary
This is a traffic analysis of the Technaxx WiFi smart alarm system starter kit TX-84 using Wireshark.
Requirements
- Router running tcpdump (see: OpenWRT: Installation)
- Technaxx WiFi smart alarm system starter kit TX-84 with connected Smartphone app
- Wireshark
Analysis
This analysis looks at the network traffic of the smart alarm system and later in step "Smartphone communication" at the traffic between the Alarm system and Smartphone App.
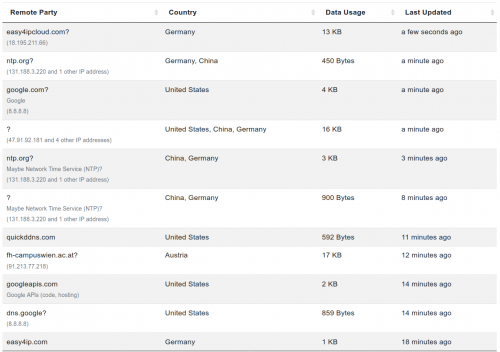
With the help of the Princeton IoT Inspector we are able to get a brief overview of the communications between the device and the outside world.
What is not covered by the Princeton IoT-Inspector is the internal traffic. We will later find out that is quite interesting.
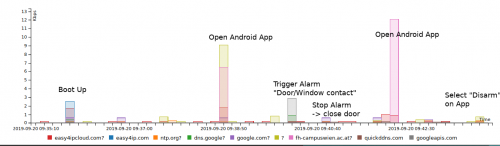
Boot up
There are two main communications to the outside world: 1. Heartbeat and 2. HTTP Traffic
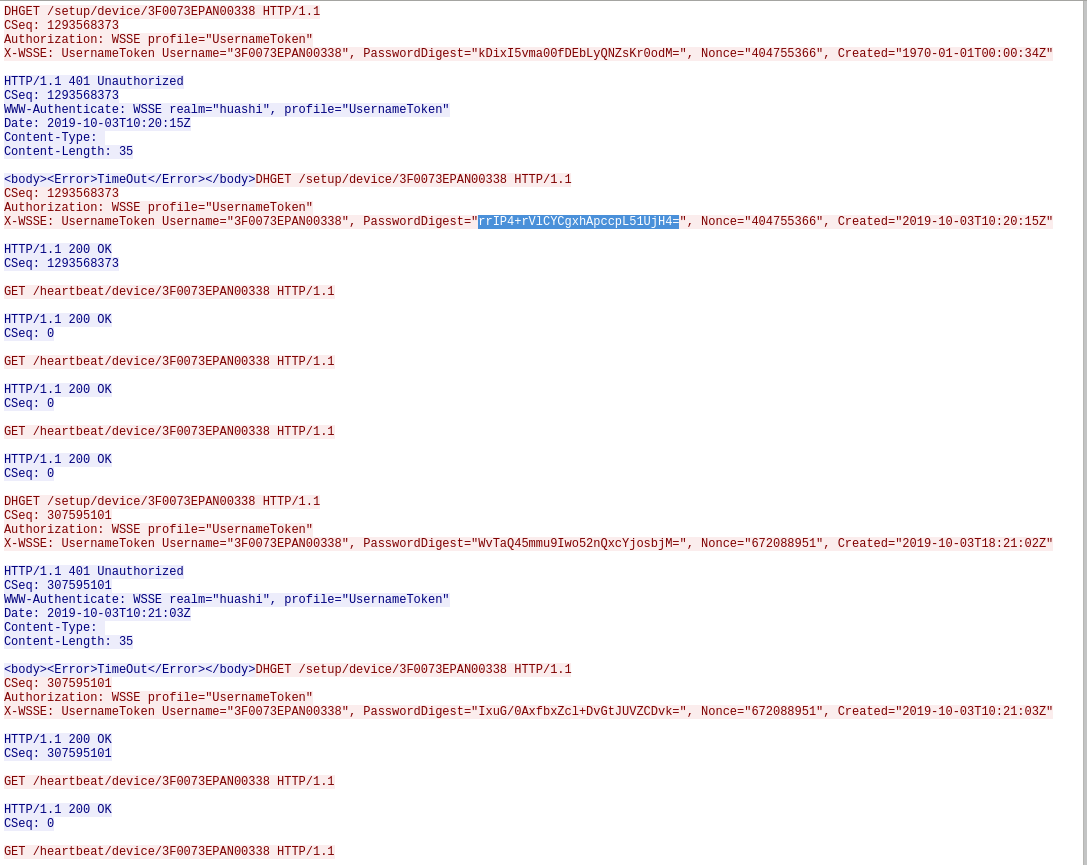
UDP Heartbeat / "Hello" to Chinese server 18.195.211.66
While the device is turned on it will send a notification to a Chinese server that it is turned on and active.
The password looks like a base64 string -> decode it: hex representation: aeb20fe3ead5942602831840a5c7292f9d548c7e (=bit length: 140 ... probably sha-1 or sha-128)
TODO: check out nonce attack
https://en.wikipedia.org/wiki/Digest_access_authentication
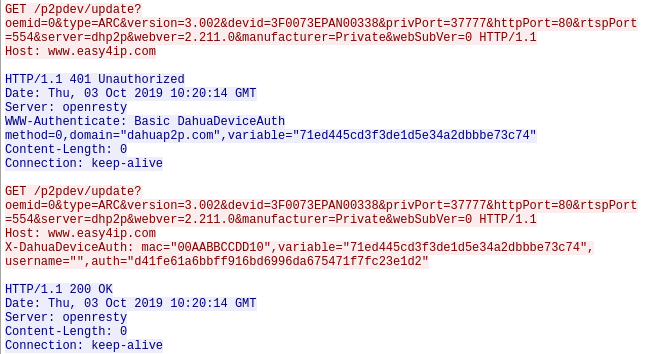
HTTP Traffic
Internal UDP communication between Smartphone App and alarm system
With the smartphone App My Secure Pro you can monitor the current status and configuration of the smart alarm system. The Smartphone and the alarm system are connected through WLAN and talk to each other quite frequently. The communication is based on UDP and I suspect they talk a custom protocol called PTCP which sometimes contains JSON strings. These JSON strings contain information about the interface of the alarm system and you are also able to invoke function calls, like "turn off alarm" or "arming the device".
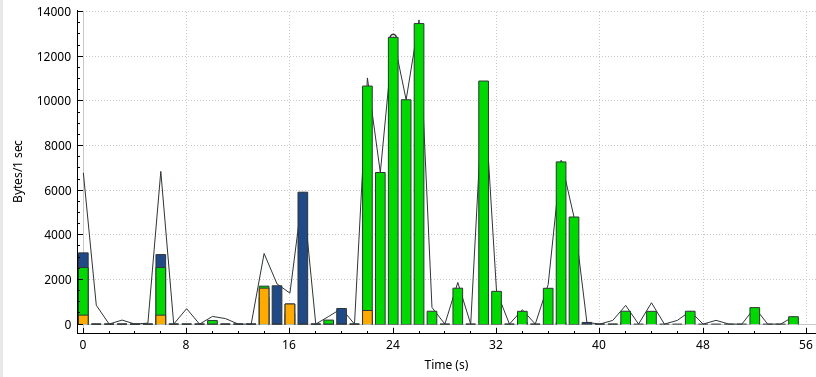
This type of internal UDP connection is quite a big portion as we can see: (using Wireshark IO-Graph)
Green: UDP
Blue: TCP
Orange: DNS
Phone:
50 54 43 50 00 00 05 89 00 00 0b 29 00 00 fb 50 PTCP.... ...)...P
56 14 5f c4 00 37 41 ec 10 00 00 e1 ff b3 b1 85 V._..7A. ........
00 00 00 00 f6 00 00 00 c1 00 00 00 2b 70 02 00 ........ ....+p..
00 00 00 00 c1 00 00 00 00 00 00 00 00 17 26 02 ........ ......&.
00 00 00 00 7b 20 22 69 64 22 20 3a 20 31 35 39 ....{ "i d" : 159
37 38 37 2c 20 22 6d 65 74 68 6f 64 22 20 3a 20 787, "me thod" :
22 61 6c 61 72 6d 2e 73 65 74 41 72 6d 4d 6f 64 "alarm.s etArmMod
65 22 2c 20 22 6f 62 6a 65 63 74 22 20 3a 20 31 e", "obj ect" : 1
38 36 30 36 37 32 38 2c 20 22 70 61 72 61 6d 73 8606728, "params
22 20 3a 20 7b 20 22 6d 6f 64 65 22 20 3a 20 22 " : { "m ode" : "
41 72 6d 69 6e 67 22 2c 20 22 70 72 6f 66 69 6c Arming", "profil
65 22 20 3a 20 22 41 74 48 6f 6d 65 22 2c 20 22 e" : "At Home", "
70 77 64 22 20 3a 20 22 34 30 41 46 36 44 46 31 pwd" : " 40AF6DF1
46 34 42 46 35 46 30 33 30 41 30 30 42 32 30 33 F4BF5F03 0A00B203
41 44 46 42 42 30 34 31 22 20 7d 2c 20 22 73 65 ADFBB041 " }, "se
73 73 69 6f 6e 22 20 3a 20 33 36 30 35 30 36 38 ssion" : 3605068
38 20 7d 0a 00 8 }..
Alarm:
50 54 43 50 00 00 0b 29 00 00 06 76 00 00 f9 8d PTCP...) ...v....
00 37 47 d2 56 14 5f c4 10 00 00 80 ff b3 b1 85 .7G.V._. ........
00 00 00 00 f6 00 00 68 60 00 00 00 2b 70 02 00 .......h `...+p..
00 00 00 00 60 00 00 00 00 00 00 00 00 17 26 02 ....`... ......&.
00 00 00 00 7b 22 69 64 22 3a 31 35 39 37 38 37 ....{"id ":159787
2c 22 70 61 72 61 6d 73 22 3a 7b 22 64 65 74 61 ,"params ":{"deta
69 6c 22 3a 7b 22 49 44 22 3a 30 2c 22 54 72 69 il":{"ID ":0,"Tri
67 67 65 72 4d 6f 64 65 22 3a 22 4e 65 74 22 7d ggerMode ":"Net"}
7d 2c 22 72 65 73 75 6c 74 22 3a 74 72 75 65 2c },"resul t":true,
22 73 65 73 73 69 6f 6e 22 3a 33 36 30 35 30 36 "session ":360506
38 38 7d 0a 88}.
Phone:
50 54 43 50 00 00 06 76 00 00 0b b5 00 00 fa c4 PTCP...v ........
56 14 65 aa 00 37 47 d2 V.e..7G.
50 54 43 50 00 00 06 76 00 00 0b b5 00 00 fa c4 PTCP...v ........
56 14 65 b4 00 37 47 d2 10 00 00 8b ff b3 b1 85 V.e..7G. ........
00 00 00 00 f6 00 00 00 6b 00 00 00 2b 72 02 00 ........ k...+r..
00 00 00 00 6b 00 00 00 00 00 00 00 00 17 26 02 ....k... ......&.
00 00 00 00 7b 20 22 69 64 22 20 3a 20 31 36 30 ....{ "i d" : 160
32 39 39 2c 20 22 6d 65 74 68 6f 64 22 20 3a 20 299, "me thod" :
22 61 6c 61 72 6d 2e 64 65 73 74 72 6f 79 22 2c "alarm.d estroy",
20 22 6f 62 6a 65 63 74 22 20 3a 20 31 38 36 30 "object " : 1860
36 37 32 38 2c 20 22 70 61 72 61 6d 73 22 20 3a 6728, "p arams" :
20 6e 75 6c 6c 2c 20 22 73 65 73 73 69 6f 6e 22 null, " session"
20 3a 20 33 36 30 35 30 36 38 38 20 7d 0a 00 : 36050 688 }..
Alarm:
50 54 43 50 00 00 0b b5 00 00 07 0d 00 00 ff 68 PTCP.... .......h
00 37 47 f0 56 14 65 b4 .7G.V.e.
Phone:
50 54 43 50 00 00 07 0d 00 00 0b b5 00 00 fa c4 PTCP.... ........
56 14 65 be 00 37 47 d2 10 00 00 20 ff b3 b1 85 V.e..7G. ... ....
00 00 00 00 a4 00 00 00 00 00 00 00 1a 00 00 00 ........ ........
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ........ ........
00 00 00 00
Calling the method: alarm.listMethod gives us following interface:
{
"id":157739,
"params":{
"method":[
"alarm.factory.instance",
"alarm.destroy",
"alarm.getInSlots",
"alarm.getOutSlots",
"alarm.getInState",
"alarm.getOutState",
"alarm.getExAlarmCaps",
"alarm.listMethod",
"alarm.startAlarmBell",
"alarm.stopAlarmBell",
"alarm.getChannelsState",
"alarm.getAlarmCaps",
"alarm.setArmMode",
"alarm.getArmMode",
"alarm.setBypassMode",
"alarm.getBypassMode",
"alarm.getActivateDefenceArea",
"alarm.addressBinding",
"alarm.getAllInSlots",
"alarm.getAllOutSlots",
"alarm.getAlarmInChannels",
"alarm.setSilentAlarm",
"alarm.setSoundAlarm"
]
},
"result":true,
"session":36050688
}
or configManager.listMethod
{
"id":161579,
"params":{
"method":[
"configManager.factory.instance",
"configManager.destroy",
"configManager.getConfig",
"configManager.setConfig",
"configManager.saveFile",
"configManager.deleteConfig",
"configManager.getDefault",
"configManager.setDefault",
"configManager.getMemberNames",
"configManager.restore",
"configManager.attach",
"configManager.detach",
"configManager.restoreExcept",
"configManager.copyConfig",
"configManager.getConfigEx",
"configManager.setConfigEx",
"configManager.exportPackConfig",
"configManager.importPackConfig",
"configManager.setChannelConfig",
"configManager.getVideoAnalyseConfig",
"configManager.setVideoAnalyseConfig",
"configManager.getFailureDetail",
"configManager.deleteFile",
"configManager.setTemporaryConfig",
"configManager.restoreTemporaryConfig",
"configManager.listMethod"
]
},
"result":true,
"session":36050688
}
Used Hardware
- Router: Zyxel Armor Z2 AC 2600 MU-MIMO dualband wireless router
- Technaxx WiFi smart alarm system starter kit TX-84
References
- I found an interesting presentation very similar to my findings
- https://site.ieee.org/neworleans/files/2016/12/12052016-Presentation-IoT-security-website-copy.pdf