AirDrive Forensic Keylogger Cable
Summary
This keylogger is one with WiFi access and a minimized risk of detection. The USB keylogger module is hidden in a USB extension cable. Externally, the USB cable does not differ from conventional cables.
The AirDrive Forensic Keylogger Module which was built into the cable is an ultra-small USB keylogger module designed for installation in a USB keyboard. The small size makes it easy to install in any USB keyboard. This is available as standard and pro version. Exact information can be found here. A video with detailed installation instructions can be found here.
Characteristics
- Stores input from any USB keyboard
- 16MB internal flash memory
- Undetectable by security software
- Supports over 40 national keyboard layouts
- Compatible with barcode readers
- Works as a wireless Wi-Fi hotspot
- Connect from any computer, smartphone or tablet
- Data access via web browser
- Remote data retrieval without touching the device
- Supports WEP, WPA and WPA-2 network security
- Memory secured by hardware encryption
Description
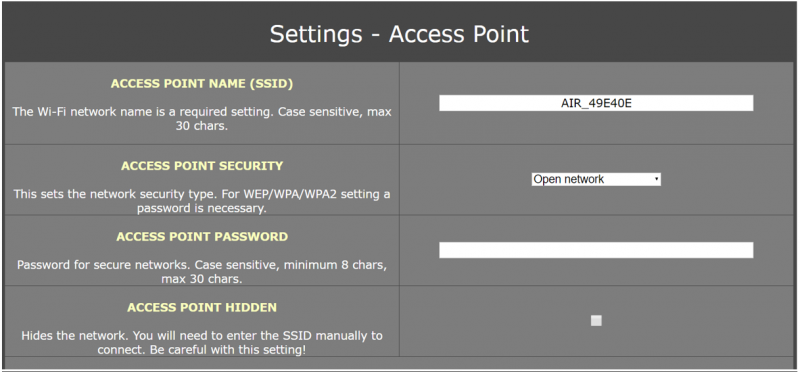
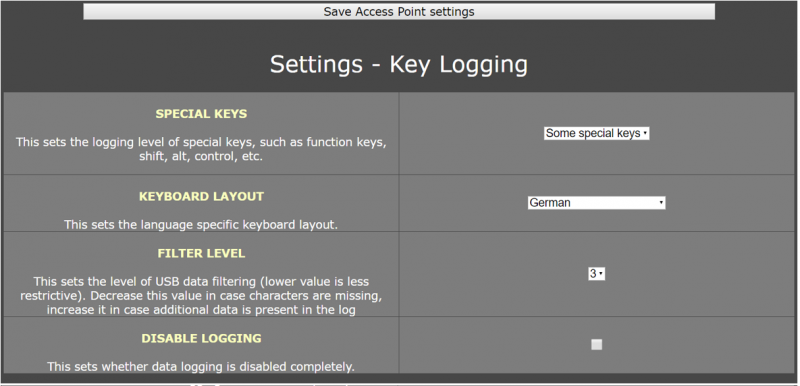
The AirDrive cable acts as a Wi-Fi hotspot. This means that the cable can establish a Wi-Fi connection with any Wi-Fi device (smartphone, tablet or laptop). The selected Wi-Fi device can then connect to the interface with the data protocol. There, there is the possibility to set configurations, such as the WLAN settings of the WLAN access point and the options for logging the keyboard strokes. Over 40 national keyboard layouts, including the world's most popular languages and keyboard layouts, are supported. Installation requires no additional software or drivers.
Hands-On
1. Connect the USB keylogger cable to the external keyboard and the target host. 2.
2. Connect your smartphone, tablet or computer to the Wi-Fi network "AIR_XXYYZZ", where "XXYYZZ" is the device ID of the USB cable. 3.
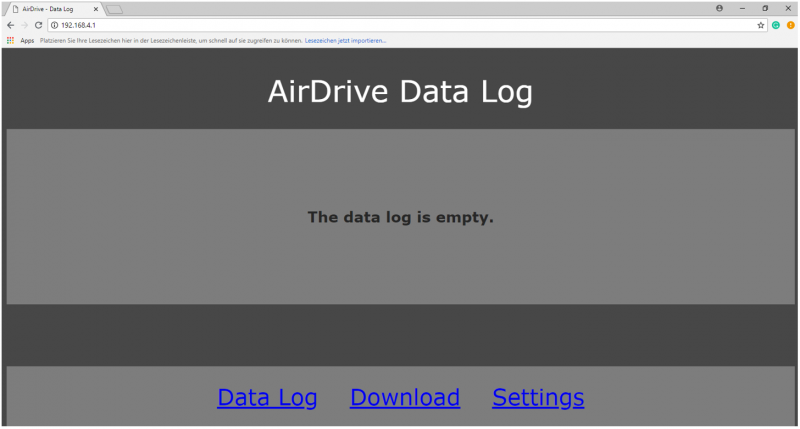
3. You can then use any web browser to access the interface under the IP "192.168.4.1".
4. Open the settings to configure the keylogger cable. Various configurations can be made there:
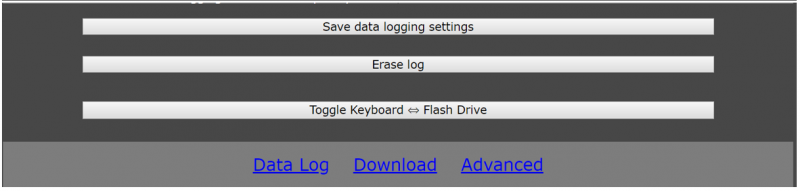
To apply the settings, click on "Save data logging settings" and/or on “Save Access Point settings”.
5. Since this is not a "Pro" device, there are no advanced settings available. Features like an internet connection via the access point, timestamps, reporting via email and data streaming can be set via this sub-menu.
6. However, we can download the "Data Log" under the "Download" button, which can be several pages long.
7. With a click on "Data Log" we can observe what is typed on the external keyboard.
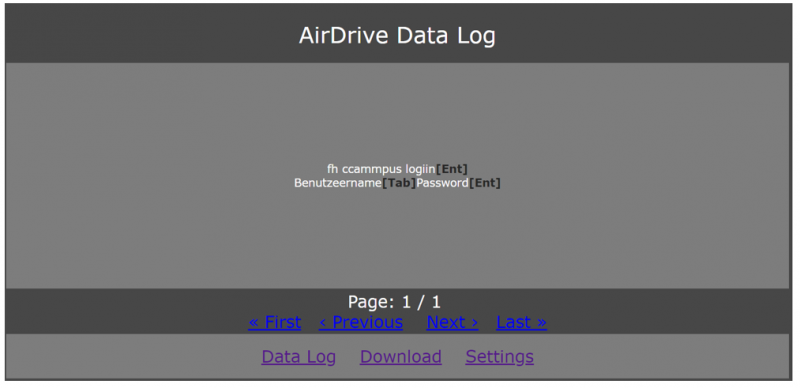
Example of a Data Log
In the following you can see a screenshot of a typical user logon process on the portal of the FH Campus Wien.
Important Legal Notice [1]
The usage of a keylogger is fully legal as long as a clear notice is displayed, informing the user of the monitored equipment about the presence of a keystroke logger. We encourage the use of this equipment only for the purpose of monitoring your own computer, especially for protecting children against online hazards. It is NOT LEGAL to use a keylogger for the purpose of intercepting third party data, especially passwords, banking data, confidential correspondence, etc. If in doubt, please seek legal advice before using a keystroke logger. A good starting point is the U.S. Department of Justice Letter on Keystroke Monitoring and Login Banners, according to which a clear notice should be displayed, warning that user keystrokes may be logged.