Difference between revisions of "Bluetooth Sniffing with Ubertooth: A Step-by-step guide"
| Line 13: | Line 13: | ||
== BLE Fundamentals == | == BLE Fundamentals == | ||
This section will cover foundational aspects of BLE. | This section will cover foundational aspects of BLE [https://www.bluetooth.com/specifications/bluetooth-core-specification/]. | ||
Feel free to skip it, if you are already familiar with the technology. | Feel free to skip it, if you are already familiar with the technology. | ||
| Line 425: | Line 425: | ||
The utility ''gatttool'' can be used to manipulate characteristics attribute-values. | The utility ''gatttool'' can be used to manipulate characteristics attribute-values. | ||
In the following we change the temperature value of the thermostat. | In the following we change the temperature value of the thermostat. | ||
Connect to your device using the following command: | |||
<code>gatttool -b 78:A5:04:62:71:3D -I</code> | |||
This will give you a prompt. Type "connect" to innitiate pairing with the device: | |||
[78:A5:04:62:71:3D][LE]> connect | |||
Attempting to connect to 78:A5:04:62:71:3D | |||
Connection successful | |||
'''[78:A5:04:62:71:3D]'''[LE]> | |||
Now you can use a variety of commands to send read/write requests to your connected device: | |||
:* <code>characteristics</code> will list all characteristics and their respective handles available on the device | |||
:* <code>char-read-hnd 25</code> will read the characteristics value of handle 0x0025 | |||
:* <code>char-write-req 25 <nowiki><value></nowiki></code> will write ''value'' to handle 0x0025 | |||
Find out the handles you need to address by analyzing the captured BLE connection. | |||
| Line 436: | Line 454: | ||
== References == | == References == | ||
* https://www.bluetooth.com/specifications/bluetooth-core-specification/ | |||
* https://github.com/greatscottgadgets/ubertooth/wiki | * https://github.com/greatscottgadgets/ubertooth/wiki | ||
* https://github.com/mikeryan/crackle | * https://github.com/mikeryan/crackle | ||
Revision as of 21:46, 23 January 2020
Summary
This is a tutorial on how to sniff Bluetooth Low Energy (BLE) packets using the Ubertooth One, 2.4 GHz wireless development platform device. This guide will detail the setup process and outline every step to capture a BLE connection. Furthermore, it will provide methods of bluetooth hacking, i.e cracking the encryption of a BLE connection and overwriting characteristics of a device. This tutorial is created in regard to the seminar paper: File:Pentesting in IoT Bluetooth Sniffing.pdf
Requirements
- Linux-based Operating system: this test used Kali Linux 64-Bit v2019.4 native install
- BLE devices
- Tools: crackle, gatttool
BLE Fundamentals
This section will cover foundational aspects of BLE [1]. Feel free to skip it, if you are already familiar with the technology.
Communication Protocol
BLE was introduced in Bluetooth 4.0 is one of the most common technologies utilized by smart devices. The technology is explicitly designed for devices with resource and power constraints. BLE is effectively using lower data rate and less power than Bluetooth classic, thus significantly reducing battery consumption on smart devices.
Protocol Stack
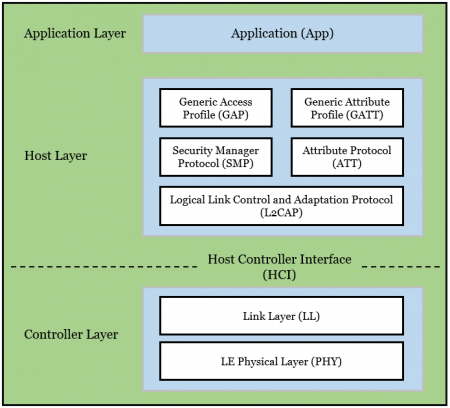
The figure shows the BLE stack and its three main layers: Application, Host, and Controller.
- Host Controller Interface (HCI)
- HCI enables the interaction between Host and Controller.
- LE Physical Layer (PHY)
- The Controller's PHY layer is responsible for signal modulation and demodulation. In addition to that it also calculates the hopping pattern for Frequency Hopping Spread-Spectrum.
- Link Layer (LL)
- LL manages several things, including the device's Bluetooth address, encryption and connection initiation.
- Logical Link Control and Adaptation Protocol (L2CAP)
- L2CAP encapsulate data from other layers into a proper BLE packet structure.
- Generic Access Profile (GAP)
- GAP controls a majority of the advertisements and also handles the role of the device in a specific connection.
- Attribute Protocol (ATT)
- ATT is the component which manages the data exchange and performs operations like read, write and error handling.
- Generic Attribute Profile (GATT)
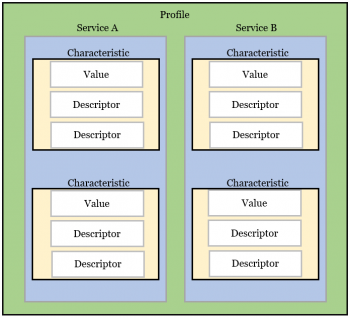
- GATT manages the data by categorizing it into Profiles, Services and Characteristics.
- If the concept is applied to the thermostat, the respective fields can be described as follows:
- BLE devices can have several profiles. A thermostat can have a "winter" and a "summer" profile for example.
- These profiles are comprised of services. An example for a service is temperature regulation.
- Furthermore, a service contain several characteristics which hold values, e.g. the temperature value.
- Such values are referenced through unique handles. This information is relevant to comprehend how gatttool works.
Bluetooth Address
The six byte Bluetooth Device Address (BD_ADDR) is comprised of three components.
| Part | Byte | Description |
|---|---|---|
| NAP | 2 | Non-significant Address Part - assigned by IEEE and therefore publicly available |
| UAP | 1 | Upper Address Part - also assigned by IEEE, publicly available |
| LAP | 3 | Lower Address Part - transmitted with every packet as part of the packet header |
Pairing Process
In the pairing process the devices agree upon everything related to security. The security measures are initiated by the Security Manager of the master. The slave may request the initiaton of pairing or the use of other security procedures. That means that the devices exchange their capabilities and consequently decide on a specific pairing method.
| Pairing Method | Description |
|---|---|
| Numeric Comparison | Both devices present the same Temporary Key (TK) on their respective displays. The user is asked to verify that the values match on both devices. This method is exclusive to LE Secure Connections. |
| Just Works | This mode is especially for devices which have no display or input mechanism, such as earphones or a computer mouse. The TK value is always set to zero. |
| Passkey Entry | With this mode the TK value is displayed on one device, and the user is prompted to enter the value into the other device. |
| Out of Band (OOB) | In this mode the key is exchanged through a different protocol than BLE, i.e. utilizing NFC or QR-codes |
The device's capabilities are exchanged through L2CAP values, which are not encrypted.
Following that, the devices agree upon a Temporary Key (TK).
The value of TK is an integer between 0 and 999999.
The user is asked to verify the generated TK using a display, for example when pairing a phone to a car.
The TK is ultimately used for generation of a Short Term Key (STK).
The STK itself is never transmitted between devices and is actually used to establish the Long Term Key (LTK).
The LTK is then used by the paired devices for subsequent connections.
Mike Ryan, the author of "Bluetooth: With Low Energy Comes Low Security" describes vulnerabilities of BLE security and exposes a critical security isse. The key exchange protocol is vulnerable to brute force attacks. It details that once a TK value is successfully found, the STK and LTK keys can also be otained by decrypting the corresponding keys. Ryan is also the creator of crackle, which we will use late to decrypt BLE connections.
Frequency Hopping Spread-Spectrum (FHSS)
Bluetooth can handle many devices at the same time by using a technique called Frequency Hopping Spread-Spectrum (FHSS). This technique enables transmitters to change the frequency mid-connection. Therefore, many devices can make use of the full radio spectrum. Consequently, it is highly unlikely for two devices to interfere with each other on the same frequency.
BLE uses a slightly different FHSS scheme than Bluetooth classic, because BLE consists of 40 different channels, 3 advertisement and 37 data channels.
| Center Frequency | Data Channel Index |
Advertisement Channel Index |
|---|---|---|
| 2402 MHz | 37 | |
| 2404 MHz | 0 | |
| ... | ... | |
| 2424 MHz | 10 | |
| 2426 MHz | 38 | |
| 2428 MHz | 11 | |
| ... | ... | |
| 2478 MHz | 36 | |
| 2480 MHz | 39 |
Once a connection is established, it hops along the 37 data channels using the following formula:
Next channel ≡ channel + hop increment (mod 37)
The time in between hops is specified as the hop interval.
It is important to mention that Bluetooth 5 introduced a new channel selection algorithm. Hopping sequences follow a pseudo random sequence now.
Capturing BLE packets
Step 1 - Prerequisites
Ubertooth One offers a well-documented GitHub-repository [2]. Follwowing its instructions, the device's tools require several components. To fulfill the demands, one has to install:
sudo apt-get install cmake libusb-1.0-0-dev make gcc g++ libbluetooth-dev pkg-config libpcap-dev python-numpy python-qt4
In contrast to the guide, the python-pyside component needs to be installed separately using the pip-installer:
pip install pyside2
In order to for Ubertooth tools to decode Bluetooth packets the Bluetooth baseband library (libbtbb) needs to be downloaded and installed:
wget https://github.com/greatscottgadgets/libbtbb/archive/2018-12-R1.tar.gz -O libbtbb-2018-12-R1.tar.gz tar -xf libbtbb-2018-12-R1.tar.gz cd libbtbb-2018-12-R1 mkdir build cd build cmake .. make sudo make install sudo ldconfig
Following that, the Ubertooth tools can be downloaded from the GitHub repository. They include host code, which enables sniffing Bluetooth packets. Additionally, they provide means to configure the Ubertooth device, including a simplified method for a firmware update.
wget https://github.com/greatscottgadgets/ubertooth/releases/download/2018-12-R1/ubertooth-2018-12-R1.tar.xz tar xf ubertooth-2018-12-R1.tar.xz cd ubertooth-2018-12-R1/host mkdir build cd build cmake .. make sudo make install sudo ldconfig
The Wireshark Bluetooth Baseband (BTBB) and Basic Rate/Enhanced Data Rate (BR/EDR) plugins facilitate the analysis of Bluetooth baseband traffic that has been captured within the Wireshark GUI.
The plugins need to be installed both separately from the libbtbb library. For the BTBB plugin the following commands have been used:
sudo apt-get install wireshark wireshark-dev libwireshark-dev cmake cd libbtbb-2018-12-R1/wireshark/plugins/btbb mkdir build cd build cmake -DCMAKE_INSTALL_LIBDIR=/usr/lib/x86_64-linux-gnu/wireshark/libwireshark3/plugins .. make sudo make install
It is important to state that the MAKE_INSTALL_LIBDIR directory can vary depending on the OS used and the wireshark installation. However, it should be the directory of existing Wireshark plugins. The procedure needs to be repeated for the BR/EDR plugin.
cd libbtbb-2018-12-R1/wireshark/plugins/btbredr mkdir build cd build cmake -DCMAKE_INSTALL_LIBDIR=/usr/lib/x86_64-linux-gnu/wireshark/libwireshark3/plugins .. make sudo make install
Step 2 - Verification & Firmware Update
After installing the prerequisits, the Ubertooth One device was plugged in through a USB port. It is of utmost importance to operate the Ubertooth One with the antenna attached to it. Otherwise, there is a risk of damaging the device. After inserting the device, verify that the system detects it:
lsusb
This will display information about USB buses in the system and the devices connected to them:
Bus 002 Device 001: ID 1d6b:0003 Linux Foundation 3.0 root hub Bus 001 Device 005: ID 04f2:b595 Chicony Electronics Co., Camera Bus 001 Device 004: ID 138a:003f Validity Sensors, Inc. VFS495 Bus 001 Device 003: ID 8087:0a2b Intel Corp. Bus 001 Device 002: ID 1ea7:0064 SHARKOON Technologies 2.4G Mouse Bus 001 Device 014: ID 1d50:6002 OpenMoko, Inc. Ubertooth One Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
Upon first operation of the Ubertooth One it is necessary to update its firmware. The tools, which were downloaded before, facilitate a simplified way to achieve this task. Change the directory to the firmware directory of Ubertooth and execute the following command:
ubertooth-dfu -d bluetooth_rxtx.dfu -r
If the update is successful, this output will be produced:
Switching to DFU mode... Checking firmware signature ........................................ ........................................ ........................................ Detached
To verify the firmware-version enter the following command:
ubertooth-util -v
Step 3 - Ubertooth Spectrum Analyzer
It is recommended to validate the functionality of the Ubertooth device via the spectrum analyzer, which is a tool to analyze the 2.4GHz band. Specifically, it provides a Graphical User Interface (GUI) tool named ubertooth-specan-ui, which visually monitors the frequencies. This command will start the spectrum analyzer:
ubertooth-specan-ui
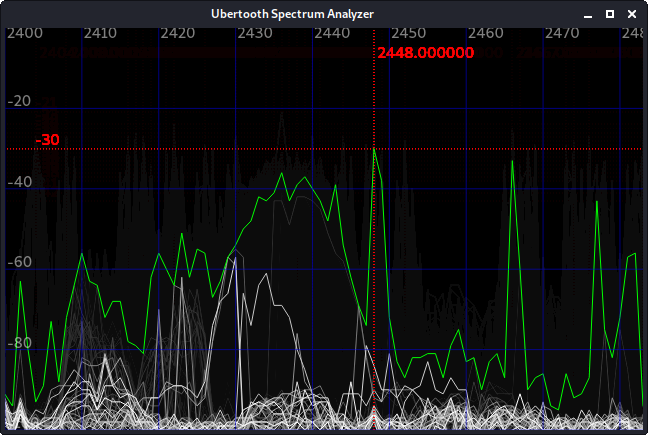
Once successful, you can see the analyzer work its task through a powerful GUI:
In this case the figure shows several 802.11b networks in different channels, represented by green amplitudes.
The white amplitudes depict beacons that are visible during scanning. The red lines adjust to different centers of frequency channels in the 2.4GHz radio band.
Step 4 - Intercepting Lower Address Part (LAP) Packets
The BD_ADDR makes the allocation of sniffed Bluetooth packets possible. The Ubertooth One can start the LAP scan with this command:
ubertooth-rx
A continuous output will follow on the console:
systime=1578428685 ch=26 LAP=3a5138 err=1 clkn=8355 clk_offset=5199 s=-80 n=-55 snr=-25 systime=1578428688 ch=26 LAP=3a5138 err=1 clkn=18479 clk_offset=5628 s=-81 n=-55 snr=-26 systime=1578428692 ch=43 LAP=3a5138 err=2 clkn=28967 clk_offset=6029 s=-80 n=-55 snr=-25 systime=1578428692 ch=47 LAP=3a5138 err=2 clkn=30327 clk_offset=6069 s=-81 n=-55 snr=-26 systime=1578428694 ch=52 LAP=3a5138 err=1 clkn=36948 clk_offset=87 s=-79 n=-55 snr=-24 systime=1578428696 ch=53 LAP=3a5138 err=0 clkn=42360 clk_offset=302 s=-77 n=-55 snr=-22
In the output ch represents the channel used by the device referenced in the LAP value. The channel hopping is clearly comprehensible. Clkn indicates the master`s clock, while s references the signal strength and n states the value of noise. Following that the snr value represents the signal-to-noise ratio. This mode is especially helpful for undiscoverable devices, because it can calculate a BD_ADDR through the LAP in combination with the other parameters.
Alternatively, if the devices are discoverable, you can use the BLE scan of hcitools:
sudo hcitool lescan
Among eventual other devices you should see the BLE devices you are testing, in this case the thermostat and the fitness tracker:
D5:AA:D0:41:A3:60 Mi Smart Band 4 78:A5:04:62:71:3D TepHeatB [...]
Step 5 - The Ubertooth-BTLE Tool
One of the most powerful tools the Ubertooth One provides is the Bluetooth Low Energy sniffing mode. Among other things, it can sniff and follow connections and even interfere with them. In the "follow" mode, Ubertooth listens on one of the three advertising channels. Once a BLE connection is established (on the advertising channel the device has been listenting to), Ubertooth will follow the hops along the data channels capturing the transmissions between the devices. Per default, Ubertooth can be used to follow any connection it observes randomly. Naturally, the device can be restricted to observe a specific device by providing the BD_ADDR of the device in question. The general syntax of the corresponding command for "follow" mode looks like:
ubertooth-btle -f <BD_ADDR>
Simply replace the BD_ADDR with the address you found out earlier:
ubertooth-btle -f 78:A5:04:62:71:3D
This will produce a continuous output in the console.
Furthermore, it is possible to redirect the output into a file or a pipe. To achieve this, the syntax requires this generic command:
ubertooth-btle -f <BD_ADDR> -c <file or pipe>
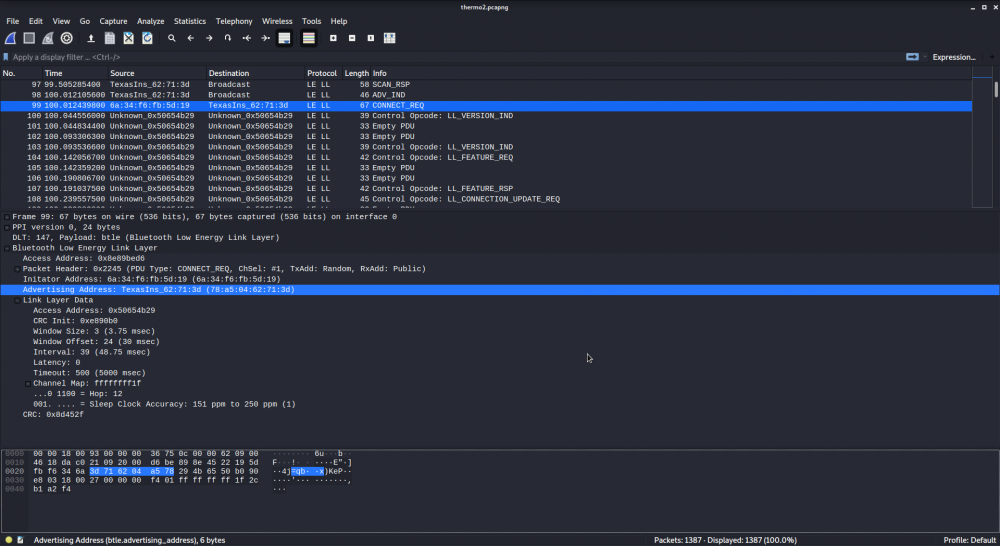
Step 6 - Wireshark Analysis
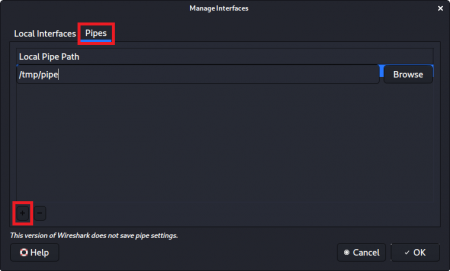
It is also possible to analyze the captured BLE packets in Wireshark. For this purpose create a pipe via:
mkfifo /tmp/pipe
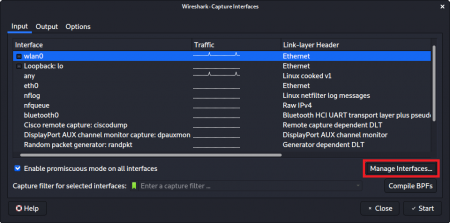
Following that, a new interface needs to be added to Wireshark in order to use the just created pipe.
For this, the custom pipe /tmp/mypipe was added to the list of interfaces.
Now repeat the command from Step 5, but now with a redirected ouput to the pipe:
ubertooth-btle -f 78:A5:04:62:71:3D -c /tmp/pipe
Select the custom interface you have just created in Wireshark to be able to analyze packtets with enhanced visibility and additional information.
Exploiting BLE
After capturing the data it is possible to use additional third party tools in combination with Ubertooth to obtain critical information. In the following this is outlined through the utilization of the tools crackle and gatttool.
Crackle
Crackle is a tool that attempts to decrypt BLE Encryption. Crackle is the right tool if you have captured a connection based on BLE Legacy Pairing. It can not decrypt LE Secure Connections based transmissions. Note that even if you are using Kali Linux the pre-installed version of crackle may be out of date without any possibility to update it through the respective repositories. It is recommended that you use the master branch from crackle GitHub-repository [3].
git clone https://github.com/mikeryan/crackle.git cd crackle make
Now you can use the latest version of the tool by executing this command:
./crackle -i <your_file.pcap>
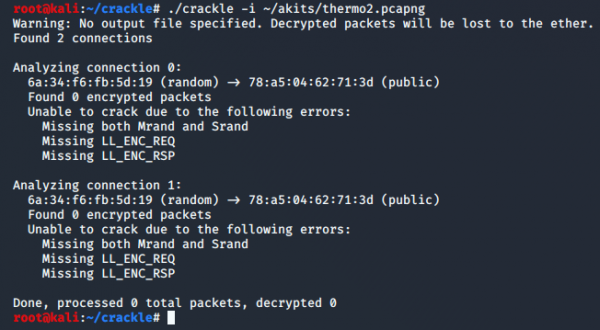
In this test, the captured connection revealed that the thermostat used no encryption and the fitness tracker used LE Secure Connections.
In this regard, crackle was unsuccessful in both instances.
When applied to the thermostat connection the output looked like this:
This is due to the fact that the thermostat connection has no encryption. Naturally, there is nothing to break. Note that you can receive a similar result if the connection uses some form of encryption but ubertooth fails to capture the respective packets. Ubertooth cannot track 100% of the transmissions.
In the case of the fitness tracker the output clearly states that the device is running LE Secure Connections.
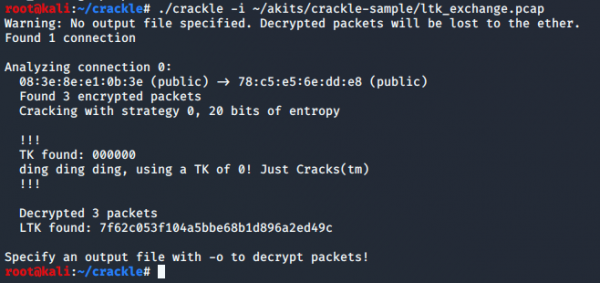
To show that crackle can indeed decrypt keys of Legacy Pairing connections we run the tool on the sample data provided here.
Gatttool
The utility gatttool can be used to manipulate characteristics attribute-values. In the following we change the temperature value of the thermostat.
Connect to your device using the following command:
gatttool -b 78:A5:04:62:71:3D -I
This will give you a prompt. Type "connect" to innitiate pairing with the device:
[78:A5:04:62:71:3D][LE]> connect Attempting to connect to 78:A5:04:62:71:3D Connection successful [78:A5:04:62:71:3D][LE]>
Now you can use a variety of commands to send read/write requests to your connected device:
characteristicswill list all characteristics and their respective handles available on the devicechar-read-hnd 25will read the characteristics value of handle 0x0025char-write-req 25 <value>will write value to handle 0x0025
Find out the handles you need to address by analyzing the captured BLE connection.
Used Hardware
- Ubertooth One, 2.4 GHz wireless development platform
- Room Thermostat Bluetooth
- Mi band 4 fitness tracker