Botnets
Summary
This article has assembled the necessary information on the botnet. What the botnet is and how it works, its components, architecture, life cycle and deployment of a bot are explained briefly and concisely.
Definition of Botnets
Botnet is a concept created by combining the terms network and robot. Like a robot, bots are programmed by the bot master for an automated task. [1] A botnet is defined as a compromised network that infects other devices on the same network by running malware.[2] Botnets are used in cyber crime. For example, it is used to send spam, launch DoS attacks, steal personal information such as bank credentials or email account. It is widely known that about 80% of emails and such messages are spam and sent via botnets. [3] A large percentage of botnets are also used to interrupt services in order to drive other players down (e.g. foreign states). Malicious botnets are a real threat to individuals using Internet infrastructures and to the entire Internet world in general. [4]
Components of Botnets
A botnet has three main components: several bots, a Command and Control (C&C) server, and a bot master. Bots are software used in many games, Internet services. What we are talking about here are malicious worms programmed by a bot master. These worms spread through the Internet. They settle into the system using security vulnerabilities in user devices. All user devices that have malicious bots in their system are also considered as bots. It is also called a zombie. A bot master is someone who codes bots and infects computers over the internet. The infected computers are an army of zombies under his command. They manage bots via a control and command structure. ”A command and control architecture is a structure that issues commands to a botnet and receives reports back from the co-opted computers”. [5] It directives sending and receiving commands for the other nodes. We will focus on this theme in more detail on botnet’s architecture.
Life Cycle of a Bot
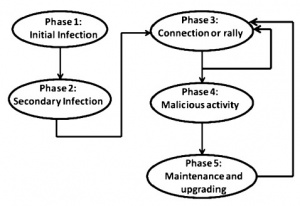
To better understand how a botnet is created, deployed and developed, it is important to understand the bot life cycle. We can divide the life cycle of a botnet into 5 phases. "These are Initial Infection, Secondary Infection, Connection Phase, Malicious Activity and Upgrading and Maintenance phase. Bot master follows this cycle to create, infect and control the bots." [6]. Figure 1 shows the life cycle of a bot. [3]
Initial Infection
Attackers make numerous bots and spread them to victims who once infected will spread bots automatically. [7] They search for vulnerable hosts and infect them using various exploitation techniques like sending spam emails, phishing, creating back doors etc.[6]
Secondary Infection
A script known as shell code are executed by the infected hosts, in this phase. FTP, HTTP, or P2P protocol or from the specific location, the shell code fetches the image of the actual binary bot. [8]After installation malware script infects machines become which than becomes real active bots.
[6]
Connection
The connection phase is the most important part of the botnet life cycle. In this phase, a command and control server is established to control the bots, namely the zombie army, and the bots connect to the server via the command and control channel. The bot master sends a request and waits for a response from the bots. If the response comes, it means the connection has been established.
Malicious Activity
A botnet start actually working in this phase.Command and control server and channel enables the bot master to remotely control the motion huge number of bots to conduct numerous illicit activities including, data robbery, performing DDoS (Distributed Denial-of-service) assaults, spreading malware, spamming, phishing, identification robbery, manipulating video games and many others. [8]
Upgrading and Maintaining
This phase is necessary to control all network and is also a vulnerable phase to save the command and control (C&C) server from detection by changing its location after some period of time. In this phase, bot master maintains an overall working of active bots and infect new host machines to increase the number of bots in botnet.[6]
Architecture Types of Botnets
Certain network architectures that we know are also used to set up a botnet. The oldest form of architecture, client-server architecture, also known as central architecture, comes first. It is followed by peer-to-peer, that is, decentralized architecture. Finally, a hybrid architecture, which is created by combining both architectures, can be used.
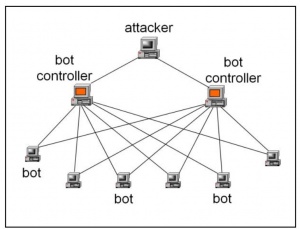
Centralized (Client-Server) Architecture
The old approach used by botnet for their Command and control (C&C) architecture was the centralized mechanism (hierarchical). In this approach, the bot-master (attacker) distributes the command over the botnet via various bot-controllers in order to hide attacker’s real identity. The uses of multiple bot-controllers prevent security professionals from shutting down C&C channel shown in Figure 2[9]. In Figure, the bot-controller retrieves the command from the bot-master and then bot-controller distributes these commands further to all the bots in the botnet. [9]
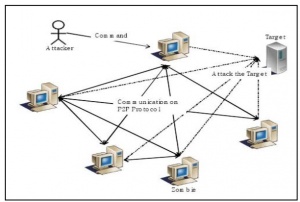
Decentralized (P2P) Architecture
There is no centrally managed server in the P2P botnet structure. All bots on the network are interconnected and work as both client and C&C server. Because the advantages over traditional centralized botnets, P2P botnets are more robust and difficult for security community to defend as the next generation of botnets in the future. [10] The client bots are attacked by the C&C servers. Once a client is attacked, all the other clients that communicate with the infected client gets attacked. The infected bots communicate with other bots and send the malicious codes to them in the event of P2P communications shown in Figure 3.[9]
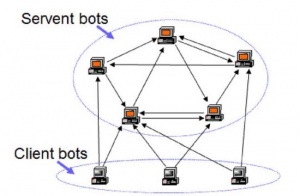
Hybrid Architecture
A hybrid C&C system is designed to exploit the benefits of both centralized and P2P models. There are two types of bots in this structure: the servant bot and the client bot. Client bots contain non-routable dynamic IP-addresses. Servant bots, on the other hand, contain static routable IP-addresses and act as both a server and a client. Hybrid C&C systems can also be located behind firewalls without a global connection to the Internet shown in Figure 4 [3]
Additionally, there exist other examples that are more specialized in nature. Proxy botnets use compromised computers to relay commands, making it difficult to trace the source and offering enhanced anonymity. IoT botnets exploit less secure Internet of Things devices like smart cameras and routers for tasks like DDoS attacks, cryptocurrency mining, or malware distribution.[11] Social botnets involve fake social media accounts for spreading disinformation or manipulating public opinion, often driven by political or commercial motives.[12] Lastly, spam botnets focus on sending vast amounts of spam emails for revenue generation or distributing malicious content, utilizing compromised computers for this purpose.[13]
Different botnet types are chosen based on the botmaster's goals and skills, each with specific functions and traits. Cybersecurity professionals and law enforcement actively strive to combat these botnets to safeguard people and organizations. Recognizing the variety of botnets is crucial for mitigating their effects in the digital world.
Propagation
To expand the botnet, infected machines spread bots to other machines in their network. The bot that exploits the vulnerabilities accesses the system and turns the machine into a new bot. In this way, the spread of the network is ensured. We can consider network propagation in two parts: active propagation and passive propagation.
In active propagation, a bot scans the hosts in the network to exploit their vulnerabilities to access the system and installs the bot binary that enables command and control communication. Some bots act like a worm. They copy themselves and propagate automatically to inject as many devices as possible. The worm may not necessarily include the main bot binary, however, it prepares ground for future bot binary installation [14]
Passive propagation is not directly, so it need a user activity. We describe some passive propagation mechanisms that are used widely: Drive-by Download, Infected Media, Social Engineering. [14]
Drive-by Download: A virus can infect user agents through some unsafe websites. Once the user visits this web page, on background malware is quickly downloaded to the visitor's machine.
Infected media: Using infected media like a USB is a powerful passive propagation method to infect a private network that no directly connect to the internet.
Social Engineering: Another method of passive propagation is social engineering that actually is underestimated. It covers all the methods that convince the user to download the bot binary
[14] to the machine.
It happens when the users downloads a file voluntarily. For example, if some visitors who want to watch a movie on an illegal movie site tells the visitors to click on the link below and download the file to watch the movie, if the user does this, it means users is probably downloading a malware to machine with their own hand. At the end of this, their own machine will also turn into a bot. The users will click on the referral link from a trusted but hacked account and reach a fake youtube site. When the users watches the video here, they actually downloads a malware to their computer. The result takes its place in the zombie army again.
Detection techniques
Anomaly-based detection
Anomaly-based botnet detection is about detecting different network irregularities, such as high network latency, unusually high traffic, traffic on unusual ports or unusual system behavior. Such irregularitites are so-called anomalies. Detection based on anomalies can be divided into two subcategories: Host-based and Network-based techniques.
Host-based techniques
The strategy for host-based botnet detection is to analyze the host machine itself. The analysis is based on examining various parameters and predetermined commands that bots receive from their C&C server.
BotSwat is a scanner developed to identify a host as a bot. The scanner monitors the so-called "execution status" of the Win32 library and observes runtime system calls, which are created by a processor. The problem with the BotSwat technique is malicious code can be hidden by code injection in harmless processes. Thus, the bots remain unnoticed.
Another detection technique is based on the analysis of multiple log files. Since bots act much faster than humans, the time needed for a complete request & response cycle can be used to determine whether the request came from a human or a bot. This technique can be used for IRC as well as for non-IRC botnets. A tool called BotTracer has been developed for this method.
BotTracer divides the life cycle of a bot into three phases (Startup, Preparation, Attack). In the startup phase, the bot is successfully im- planted in the target system. Afterwards, in the Preparation phase, the bot connects to the C&C server and waits for its commands. Finally, the botmaster sends its commands to the bots (Attack Phase). BotTracer tries to recognize the three phases and to find out where the connection with the bot is going. After that the traffic is compared with already known properties of C&C channels. The fundamental disadvantage of this technique is that it is not possible to detect the existence of virtual machines
Network-based techniques
In the network-based detection technique, attempts are made to detect botnets by examining the network traffic. The network-based techniques are divided into two subcategories, Active Monitoring and Passive Monitoring.
Active Monitoring
Active monitoring is based on the possibility of injecting test packets into the network. This produces extra traffic, but the response time of the network can be measured. The current best strategy for Active Monitoring is BotProb. BotProbe takes advantage of the fact that bots usually send commands according to certain predefined patterns. BotProb injects its packets into the network to find these patterns. This deterministic approach can effectively prove the existence of bots.
Passive Monitoring
Passive monitoring inspects the traffic while the network is in use. The traffic is analyzed by various anomaly detection techniques (distance-based techniques, support vector machines, neural networks, cluster analysis, and learned rules). Unlike active monitoring, no additional traffic is generated.
BotSniffer is a framework used for passive monitoring. The idea is that bots within the same botnet are very likely to have similarities in their activities. If bots are detected then the corresponding hosts are clustered together. An alarm is then triggered with a warning that the hosts in the cluster may be infected. For the detection of the bots, log files are used. Here, the log files store the incoming and outgoing traffic with the start time for the execution time of the started processes. Several correlation analysis algorithms are used for the analysis.
Honeynet-based detection
The term honeynet describes a network of real network components that intentionally uses components with vulnerabilities. This allows attackers to be distracted from the actual network. The honeynet is divided into two subcategories:
- Honeypot
- Honey-Wall
Honeypot
The honeypot is a mechanism for detecting unauthorized access to a system. As the bots infect the network, the honeypot collects information, such as the bot characteristics and the intent of the Botmaster.
There are three types of honeypots:
Low-interaction honeypots have only a limited number of services. Furthermore, the honeypot's interaction is severely limited. Often they communicate here only with dummy messages. This type of honeypot is usually only used to collect statistical information. The configuration and maintenance of this honeypot is very simple. However, an attacker can quickly detect that his target network is a honeypot.
Medium-interaction honeypots are very similar to low-interaction honeypots. They also have limited services, but with a greater level of interactions. The purpose of this type of honeypot is to get an attacker to continue his attack with the ability to send his payload.
High-interaction honeypots are the most advanced honeypots. They have an interactive operating system with which the attacker can interact. This complexity makes the installation and maintenance of the system the most demanding, but it also allows the most information to be collected. By imitating a complete system, appropriate preventive measures are needed in case the attacker compromises the system to use it for his attacks.
Honey-Wall
A honey-wall is used to protect honeypots from attacks. It acts as a gateway for the honeypots and collects all traffic from the honeynet system. Through the honey-wall, the network acquires the functions of Data Capture, Data Control and Data Analysis.
- Data Capture states that all actions within the network should be captured without the attacker being aware of it.
- Data Control aims to protect the Internet from compromising Honeynet systems. All data that enters or leaves the network is stopped.
- Data Analysis supports the analysis of the collected data.
Honey-wall simplifies the collection and analysis of data and also helps to control what data enters and leaves the network. However, a firewall is needed to verify the authenticity of the user.
Conclusion
With the exponential spread of internet technologies and the involvement of more and more smart tools in our lives, our need for cyber security is increasing. In this study, botnet, which is one of the cyber-attack crimes, has been mentioned and the information that the reader needs to protect themselves from malicious bots has been given in an understandable way.
Courses
- Ausgewählte Kapitel der IT-Security SE (2021, 2022)
References
- ↑ Himanshi Dhayal and Jitender Kumar. Botnet and P2P botnet detection strategies: A review. In 2018 International Conference on Communication and Signal Processing (ICCSP), pages 1077–1082, 2018.
- ↑ M. Thangapandiyan and P. M. Rubesh Anand. An efficient botnet detection system for p2p botnet. In 2016 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), pages 1217–1221, 2016.
- ↑ 3.0 3.1 3.2 3.3 3.4 Nazrul Hoque, Dhruba K. Bhattacharyya, and Jugal K. Kalita. Botnet in ddos attacks: Trends and challenges. IEEE Communications Surveys Tutorials, 17(4):2242–2270, 2015.
- ↑ Gernot Vormayr, Tanja Zseby, and Joachim Fabini. Botnet communication patterns. IEEE Communications Surveys Tutorials, 19(4):2768–2796, 2017.
- ↑ Pedram Amini, Muhammad Amin Araghizadeh, and Reza Azmi. A survey on botnet: Classification, detection and defense. In 2015 International Electronics Symposium (IES), pages 233–238, 2015.
- ↑ 6.0 6.1 6.2 6.3 Navdeep Kaur and Maninder Singh. Botnet and botnet detection techniques in cyber realm. In 2016 International Conference on Inventive Computation Technologies (ICICT), volume 3, pages 1–7, 2016.
- ↑ Wei Wan and Jun Li. Investigation of state division in botnet detection model. In 16th International Conference on Advanced Communication Technology, pages 265–268, 2014.
- ↑ 8.0 8.1 Syeda Farjana Shetu, Mohd. Saifuzzaman, Nazmun Nessa Moon, and Fer- naz Narin Nur. A survey of botnet in cyber security. In 2019 2nd In- ternational Conference on Intelligent Communication and Computational Techniques (ICCT), pages 174–177, 2019.
- ↑ 9.0 9.1 9.2 9.3 9.4 N.S. Raghava, Divya Sahgal, and Seema Chandna. Classification of bot- net detection based on botnet architechture. In 2012 International Confer- ence on Communication Systems and Network Technologies, pages 569–572, 2012.
- ↑ Wei Zhang, Yue-Ji Wang, and Xiao-Lei Wang. A survey of defense against p2p botnets. In 2014 IEEE 12th International Conference on Dependable, Autonomic and Secure Computing, pages 97–102, 2014
- ↑ T. Trajanovski and N. Zhang, "An Automated and Comprehensive Framework for IoT Botnet Detection and Analysis (IoT-BDA)," in IEEE Access, vol. 9, pp. 124360-124383, 2021, doi: 10.1109/ACCESS.2021.3110188.
- ↑ J. Zhang, R. Zhang, Y. Zhang and G. Yan, "The Rise of Social Botnets: Attacks and Countermeasures," in IEEE Transactions on Dependable and Secure Computing, vol. 15, no. 6, pp. 1068-1082, 1 Nov.-Dec. 2018, doi: 10.1109/TDSC.2016.2641441.
- ↑ M. A. R. Putra, T. Ahmad, R. M. Ijtihadie and D. P. Hostiadi, "Detecting Botnet Spam Activity by Analyzing Network Traffic Using Two-Stack Decision Tree Algorithms," 2023 International Conference of Computer Science and Information Technology (ICOSNIKOM), Binjia, Indonesia, 2023, pp. 1-6, doi: 10.1109/ICoSNIKOM60230.2023.10364480.
- ↑ 14.0 14.1 14.2 Sheharbano Khattak, Naurin Rasheed Ramay, Kamran Riaz Khan, Affan A. Syed, and Syed Ali Khayam. A taxonomy of botnet behavior, detection, and defense. IEEE Communications Surveys Tutorials, 16(2):898–924, 2014.