Difference between revisions of "Elliptic Curve Cryptography"
(Add references section; Remove Todo (cite extension)) |
|||
| (65 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
== Summary == | == Summary == | ||
This documentary gives a brief introduction into elliptic curve cryptography | This documentary gives a brief introduction into elliptic curve cryptography | ||
==Elliptic Curve Cryptography == | ==Elliptic Curve Cryptography (ECC) == | ||
Elliptic curve cryptography is a part of asymmetric cryptography, it is based on the mathematical hard problem to find a solution for the elliptic curve discrete logarithm. The calculations are performed on the algebraic structure of elliptic curves over finite fields, which means we compute points on a elliptic curve over finite field by applying the group operations double and add. | Elliptic curve cryptography is a part of asymmetric cryptography, it is based on the mathematical hard problem to find a solution for the elliptic curve discrete logarithm. The calculations are performed on the algebraic structure of elliptic curves over finite fields, which means we compute points on a elliptic curve over finite field by applying the group operations double and add. | ||
The scalar multiplication of a point on an elliptic curve over a finite field is equivalent to the exponentation of a number in a prime field, therefore the inversion is also called discrete logarithm. | The scalar multiplication of a point on an elliptic curve over a finite field is equivalent to the exponentation of a number in a prime field, therefore the inversion is also called discrete logarithm. | ||
First proposed application of elliptic curves in cryptography was random number generations, now ECC is widely used for key establishment and digital signature schemes. | |||
The main advantage of ECC is that it offers the same security level compared to RSA with shorter key lengths. Efficient implementations make ECC usable for constraint devices enabling security and privacy protection for emerging IoT systems. | |||
Example usage of ECC in IoT: | |||
{| class="wikitable" | |||
|ZigBee Smart Energy(1.x and 1.2)<ref name="zigbee"/> || sect163k1(1.x), sect283k1(1.2) | |||
|- | |||
|Vehicular Ad-Hoc Networks (IEEE1609.2) <ref name="vanet"/> || secp224r1,secp256r1 | |||
|- | |||
|NFC Forum Signature Record Type Definition(RTD) <ref name="nfc"/> || sec192r1, secp224r1, sect233k1, sect233r1 | |||
|} | |||
==Simple Weierstrass Elliptic Curve Presentation== | ==Simple Weierstrass Elliptic Curve Presentation== | ||
* Simple Weierstrass form curve equation: | * Simple Weierstrass form curve equation: | ||
<math>y^2 = x^3 + ax + b</math> | |||
<math> | The elliptic curve are all points in the <math>x,y</math> coordinates <math>P(x,y)</math> which fulfill the cubic curve equation, whereas <math>a</math> and <math>b</math> are called the characteristic of the curve. | ||
The elliptic curve are all points in the x,y coordinates which fulfill the cubic curve equation, whereas a and b are called the characteristic of the curve. | |||
The curve needs to be smooth, which means that it will not contain any singularities such as a cusp or a self intersection, | The curve needs to be smooth, which means that it will not contain any singularities such as a cusp or a self intersection, | ||
| Line 27: | Line 32: | ||
<math>4a^3 + 27b^2 \neq 0</math> | <math>4a^3 + 27b^2 \neq 0</math> | ||
Another characteristic we need to introduce is the point at infinity denoted by | Another characteristic we need to introduce is the point at infinity denoted by <math> \mathcal{O} </math> (also known as ideal point), which can be thought as identity element infinitly raised on the y axis. | ||
Therefore our points on the elliptic curve over R² all fulfill this equation | Therefore our points on the elliptic curve over R² all fulfill this equation | ||
<math>\{(x,y) | <math>\{(x,y) \in R^2 | y^2=x^3+ax+b, 4a^3+27b^2 \neq 0\} \cup \{\mathcal{O}\}</math>. A valid curve over rational numbers is shown in the next image. | ||
[[File:Ecc.png]] | [[File:Ecc.png|400px|center]] | ||
In cryptography elliptic curves over finite fields are used. The number of rational points <math>\#E</math> of an elliptic curve over a finite field <math>K</math> e.g. the prime field <math>GF(p)</math> can be computed with the Schoof-Elkies-Alkin algorithm, which is implemented in the PARI/GP library. The Hasse theorem gives an estimation of the number of points in the intervall: | |||
<div align="center"> | |||
<math>p+1-2\sqrt{p} \leq \#E \leq p+1+2\sqrt{p}</math> | |||
</div> | |||
The next figure shows a elliptic cuve <math>E:y^2=x^3-2x+2</math> over a finite field, the prime field GF(199). On each y-axis are two points, the point and its inverse point, mapped into the positive space of the prime field. | |||
[[File:Curveover199.png|400px|center]] | |||
===Group | ===Group Operations on Elliptic Curves=== | ||
According to the group law all points support following operations: | According to the group law all points support following operations: | ||
* Point | * '''Point Addition''': <math>P+Q=R</math> | ||
* Point | * Case <math>Q=P</math> -> '''Point Doubling''': <math>2P=R</math> | ||
* Case <math>Q=-P</math> -> '''Inversion of a Point''': <math>P + (-P)=\mathcal{O}</math> | |||
==== Point Addition ==== | |||
Given the elliptic curve <math>E:y^2=x^3+ax+b</math> and the points <math>P=(x_1,y_1)</math> and <math>Q=(x_2,y_2)</math>, we can calculate the coordinates of the point <math>R(x_3,y_3)</math> by adding this two points <math>R=P+Q</math> as follows.<ref name="HMV" /> | |||
<div class="toccolours mw-collapsible mw-collapsed " style="width:800px; overflow:auto;"> | <div class="toccolours mw-collapsible mw-collapsed " style="width:800px; overflow:auto;"> | ||
<div style="font-weight:bold;line-height:1.6;">Geometric derivation of the | <div style="font-weight:bold;line-height:1.6;">Geometric derivation of the Point Addition by the Tangent Chord Law</div> | ||
<div class="mw-collapsible-content"> | <div class="mw-collapsible-content"> | ||
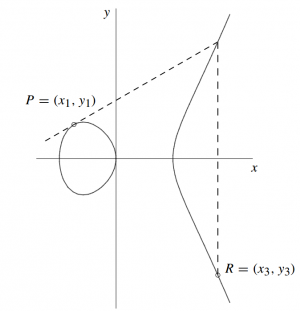
[[File:Ecc_addition.png]] | [[File:Ecc_addition.png|300px|center]] | ||
In the geometric derivation a line/chord is drawn through <math>P</math> and <math>Q</math>, the result point R is the symmtric inversion on the <math>y</math> axis of the point at the 3rd intersection on the elliptic curve. | |||
1. Calculation of the equation of the chord | |||
* We know the equation from the line | |||
<math>y=kx+d \qquad \text{concizing of} \qquad k=\frac{\Delta y}{\Delta x}</math> | |||
1. Calculation of | * Therefore | ||
* We know the equation from the line | |||
<math>y=kx+d \qquad \text{ | |||
* | |||
<math>k=\frac{y_2-y_1}{x_2-x_1}</math> and we can find the intersection with the y-axis and achieve d | <math>k=\frac{y_2-y_1}{x_2-x_1}</math> and we can find the intersection with the y-axis and achieve d | ||
<math> d=y_1-kx_1=\frac{y_1\cdot x_2-y_1 \cdot x_1-y_2 \cdot x_1 +y_1 \cdot x_1}{x_2-x_1}=\frac{y_1 \cdot x_2-y_2 \cdot x_1}{x_2-x_1}</math>. | <math> d=y_1-kx_1=\frac{y_1\cdot x_2-y_1 \cdot x_1-y_2 \cdot x_1 +y_1 \cdot x_1}{x_2-x_1}=\frac{y_1 \cdot x_2-y_2 \cdot x_1}{x_2-x_1}</math>. | ||
2. Calculation of <math>y_3</math> | |||
<math>y_3</math> we can find by insertion in the line equation: | |||
<math>y_3=(-1)\bigg( \frac{y_2-y_1}{x_2-x_1}\cdot x_3 + y_1 - \frac{y_2-y_1}{x_2-x_1}\cdot x_1 \bigg)=\bigg(\frac{y_2-y_1}{x_2-x_1}\bigg)(x_1-x_3)-y_1</math> | <math>y_3=(-1)\bigg( \frac{y_2-y_1}{x_2-x_1}\cdot x_3 + y_1 - \frac{y_2-y_1}{x_2-x_1}\cdot x_1 \bigg)=\bigg(\frac{y_2-y_1}{x_2-x_1}\bigg)(x_1-x_3)-y_1</math> | ||
2. Calculation of <math>x_3</math> | 2. Calculation of <math>x_3</math> | ||
* | * In the intersection point of the chord with the tangent, the <math>y</math> coordinate satisfies both equations, therefore we can extract <math>y</math> from both equations and get a new equation. | ||
<math>\begin{aligned} | <math>\begin{aligned} | ||
(k \cdot x+d)^2 &=x^3+a \cdot x+b\\ | (k \cdot x+d)^2 &=x^3+a \cdot x+b\\ | ||
| Line 70: | Line 82: | ||
x^3-x^2k^2+x(a-2k \cdot d)+b-d^2 &=0 | x^3-x^2k^2+x(a-2k \cdot d)+b-d^2 &=0 | ||
\end{aligned}</math> | \end{aligned}</math> | ||
* | * This is a equation of 3rd degree therefore we have 3 cross points, which can be searched by | ||
<math>\begin{aligned} | <math>\begin{aligned} | ||
(x-x_1)\cdot(x-x_2)\cdot(x-x_3)&=0\\ | (x-x_1)\cdot(x-x_2)\cdot(x-x_3)&=0\\ | ||
| Line 88: | Line 100: | ||
</div> | </div> | ||
=== Algebraic group of points === | <math>x_3=\bigg(\frac{y_2-y_1}{x_2-x_1}\bigg)^2- x_1 -x_2 \ \text{ and } \ y_3=\bigg(\frac{y_2-y_1}{x_2-x_1}\bigg)(x_1-x_3)-y_1 \text{ over } E</math> | ||
This operation is also called the Point Addition in affine coordinates and the computational costs are 1 x inversion, 2 x multiplications and 1 x squaring. | |||
Interactive tool to visualize [https://cdn.rawgit.com/andreacorbellini/ecc/920b29a/interactive/reals-add.html point addition]. | |||
==== Point Doubling ==== | |||
Given the elliptic curve <math>E:y^2=x^3+ax+b</math> and the special case <math>P=Q</math> with the point <math>P=(x_1,y_1)</math>. The result point <math>R(x_3,y_3)</math> is achieved by doubling the point <math>R=2P</math> as follows.<ref name="HMV" /> | |||
<div class="toccolours mw-collapsible mw-collapsed " style="width:800px; overflow:auto;"> | |||
<div style="font-weight:bold;line-height:1.6;">Geometric derivation of the Point Doubling by the Tangent Chord Law</div> | |||
<div class="mw-collapsible-content"> | |||
For the doubling a tangent is drawn at point <math>P</math>. At the intersection with the elliptic curve again the inversion on the <math>y</math> is taken to achieve the result point <math>R</math>. | |||
[[File:Double.png|300px|center]] | |||
1. The tangent in point <math>P</math> has the equation of <math>y=kx+d</math>. The slope of the tangent <math>k</math> is calculated by the differential function of <math>E</math> by <math>\delta x</math> and <math>\delta y</math>. | |||
<math>k=\frac{E \delta x}{E \delta y}=\frac{(y^2=x^3+ax+b) \delta x}{(y^2=x^3+ax+b) \delta y}=\frac{3x_1^2+a}{2y_1}</math> | |||
and then the intersection of the tangent with the y-axis is calculated by inserting the point coordinates <math>P(x_1,y_1)</math> in the equation of the tangent <math>y=kx+d</math>. | |||
<math>d=y_1-k \cdot x_1=y_1-\frac{3x_1^2+a}{2y_1}\cdot x_1</math> | |||
2. The y-coordinate of the point of the second intersection with the elliptic curve <math>y_3</math> can be calculated by inserting the point coordinates in the equation of the tangent and multiply by <math>(-1)</math> to get the inverse point on the y axis. | |||
<math>y_3=(-1)(kx_3+d)= (-1)\bigg(\frac{3x_1^2+a}{2y_1} \cdot x_3 + y_1-\frac{3x_1^2+a}{2y_1}\cdot x_1 \bigg)=\bigg(\frac{3 x_1^2+a}{2 y_1}\bigg)(x_1-x_3)-y_1 </math> | |||
3. <math>y_3</math> is achieved by inserting | |||
<math>\begin{aligned} | |||
(k \cdot x+d)^2 &=x^3+a \cdot x+b\\ | |||
k^2x^2+2k \cdot x\cdot d+d^2&=x^3+a \cdot x +b\\ | |||
x^3-x^2k^2+x(a-2k \cdot d)+b-d^2 &=0 | |||
\end{aligned}</math> | |||
* The crossing points can be searched by | |||
<math>\begin{aligned} | |||
(x-x_1)^2\cdot(x-x_3)&=0\\ | |||
(x^2-2 x \cdot x_1 +x_1^2) \cdot(x-x_3)&=0\\ | |||
x^3-2 x^2 \cdot x_1+x\cdot x_1^2 - x^2 \cdot x_3 + 2x \cdot x_1x_3 -x_1^2x_3 &=0\\ | |||
x^3 - x^2 (2 x_1+x_3) + x(x^2+(x_1x_3)^2)+x_1^2x_3 &=0 | |||
\end{aligned}</math> | |||
* Now we can conclude from the second term | |||
<math>\begin{aligned} | |||
x^3-x^2 \underline {k^2}+x(a-2k \cdot d)+b-d^2 &=0\\ | |||
x^3 - x^2 \underline {(2 x_1+x_3)} + x(x_1^2 -2x_1x_3)+x_1^2 x_3 &=0\\ | |||
k^2 &= 2x_1+x_3 | |||
\end{aligned}</math> | |||
* and achieve a solution for <math>x_3</math> by: | |||
<math>x_3=k^2-2x_1 =\bigg(\frac{3x_1^2+a}{2y_1}\bigg)^2 -2 x_1=\bigg(\frac{3 x_1^2+a}{2 y_1}\bigg)^2-2 \cdot x_1</math> | |||
</div> | |||
</div> | |||
</div> | |||
</div> | |||
<math>y_3=\bigg(\frac{3 x_1^2+a}{2 y_1}\bigg)(x_1-x_3)-y_1\ \text{ and } \ x_3=\bigg(\frac{3 x_1^2+a}{2 y_1}\bigg)^2-2 \cdot x_1 \ \text{ over } E</math> | |||
This operation is also called the Point Doubling in affine coordinates and the computational costs are 1 x inversion, 2 x multiplications and 2 x squarings. | |||
==== Example of elliptic point operations over an elliptic curve over a finite field ==== | |||
Given a curve E | |||
<math> E:y^2=x^3+3x+5 \text{ over } \mathbb{Z}_{17}</math> we examine the basic operations on the elliptic curve: | |||
* '''Validation of the elliptic curve''': This is done to determine if the elliptic curve is smooth by calculating the discriminant. | |||
<math> \Delta = -16(4a^3+27b^2)= -12528 \equiv 1 (\mod 17)</math> therefore <math>\Delta \neq 0 </math> holds and this curve can be used for EC operations. | |||
* '''Examining the number of points''': Choosing one random point of the curve P(6,1) as generator G all points on the curve can be calculated with the equations given above over a the prime field 17. This means first the point gets doubled and a modulo 17 operation is applied. Then continuously all other points are calculated by adding the point P to the result each time applying the modulo 17 . | |||
{|class="wikitable" | |||
| (6,1) || (4,8) || (15,5) || (9,9) || (11,14) || (2,6)|| (1,14) || (12,1) | |||
|- | |||
|(16,16) || (10,10) || (5,14) || (5,3) || (10,7) || (16,1) || (12,16) ||(1,3) | |||
|- | |||
| (2,11) || (11,3) || (9,8) || (15,12)|| (4,9) || (6,16) || <math>\mathcal{O}</math> | |||
|} | |||
All by point P(6,1) generated 23 points satisfy the equation of the elliptic curve. Notice that each x value has two y values. | |||
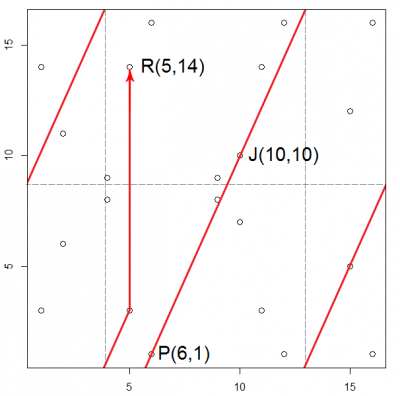
* '''Point Addition''':<math>P(6,1)+J(10,10) = ?</math> | |||
The points P(6,1) and J(10,10) are added with calculations in the finite field using the modular operation each time. | |||
<math> \begin{aligned} | |||
m &= \bigg(\frac{y_2-y_1}{x_2-x_1}\bigg) \mod 17 =(10-1) \cdot (10-6)^{-1} \mod 17 \\ | |||
&= 9 \cdot 4^{-1} \mod 17 = 9 \cdot 13 \mod 17 \\ | |||
&= 117 \mod 17 = 15 \\ | |||
\end{aligned} | |||
</math> | |||
<math>x_3=m^2- x_1 -x_2 \mod 17= 15^2-6-10 \mod 17=4-6-10 \mod 17= -12 \mod 17= 5</math> | |||
<math>y_3=m(x_1-x_3)-y_1= 15 (6-5)-1 \mod 17=14</math> | |||
'''Solution:''' <math>P(6,1)+J(10,10) = R(5,14)</math> | |||
The addition of point P and J to get the result point R is visualized in the next figure. | |||
[[File:exadd1.png|400px|center]] | |||
=== Algebraic group properties of the points === | |||
The points further comply associative and commutative algebraic group laws and the handling of the neutral element: | The points further comply associative and commutative algebraic group laws and the handling of the neutral element: | ||
* | * Closure: <math>P+Q=R \quad \forall \quad P,Q,R \in E</math> | ||
* | * Associative law: <math>P+\mathcal{O}=\mathcal{O}+P \quad \forall \quad P \in E</math> | ||
* | * Identity element and inverse that: <math>P+(-P) = \mathcal{O} \quad \forall \quad P \in E</math> | ||
* | * Cummutative law: <math>P+(Q+R)=(P+Q)+R \quad \forall \quad P,Q,R \in E</math> | ||
The inverse point of a point P(x,y) is | The inverse point of a point P(x,y) is therefore P(x,-y). | ||
== Scalar Multiplication == | == Scalar Multiplication == | ||
Is the mainly used operation on elliptic curves in cryptography, it adds <math>n</math> times the point <math>P</math> of the elliptic curve over a finite field e.g. prime field <math>GF(p)</math>. | |||
<div align="center"> | |||
<math>nP= \underbrace{P+P+P+P+...+P}_\text{n times} \ text{over} E</math> | |||
</div> | |||
=== Double and Add algorithm === | === Double and Add algorithm === | ||
| Line 105: | Line 214: | ||
== Standardization of elliptic curves == | == Standardization of elliptic curves == | ||
The domain parameters for ECC schemes are described in the form <math>E(q,a,b,G,n,h)</math>. | |||
{| | |||
!colspan="2"|Parameter description | |||
|- | |||
| <math>q</math> | |||
| defines the field size, either a prime <math>p</math> or <math>2^{m}</math> where m is prime | |||
|- | |||
| <math>a</math> | |||
| first parameter of the curve equation | |||
|- | |||
| <math>b</math> | |||
| second parameter of the curve equation | |||
|- | |||
| <math>G</math> | |||
| generating point consisting of both point coordinates <math>(x_G,y_G)</math> | |||
|- | |||
| <math>n</math> | |||
| order of the point <math> G </math> | |||
|- | |||
| <math>h</math> | |||
| cofactor which is equal to the order of the curve divided by <math>n</math> | |||
|} | |||
The generation of safe elliptic curves is an effort, hence it is recommended to use standardized known curves. First curves have been standardized in the ANSI X9.62 standard by the American National Standards Institute(ANSI) in 1999 <ref name="ANSI-X9.62" />, these have been extended or replaced by ANSI X9.63 in 2001<ref name="ANSI-X9.63" /> and ANSI FRP256V1 in 2011. The National Institute of Standard and Technology (NIST) defined their own curves in the NIST FIPS 186-2 in 2000<ref name="NIST 186-2"/>. In the same year the Certicom published the widely-used Certicom SEC2 curves <ref name="SEC2-v1" /> which have been continously updated in version 2 <ref name="SEC2-v2" />. In 2005 NIST published the NSA Suite B<ref name="NIST Suite B"/> and the Federal Office for Information Security in Germany proposed their own randomly generated curves in the same year<ref name="Brainpool"/>. | |||
== Curve25519== | == Curve25519== | ||
Curve25519 is a highly optimized curve proposed by Daniel J. Bernstein (djb) in 2005. | Curve25519 is a highly optimized curve proposed by Daniel J. Bernstein (djb) in 2005 <ref name="curve25519" />. | ||
The curve equation is | The curve equation is | ||
<math>y^2=x^3+486662x^2+x< | |||
<math>y^2=x^3+486662x^2+x</math> over a prime field <math>2^{255}-19</math> | |||
=== Edward curves=== | === Edward curves=== | ||
== Applications Example Elliptic | [[File:Edwardscurve.png|300px|center]] | ||
== Applications of Elliptic Curve Cryptography == | |||
=== Example: Elliptic Curve Diffie Hellman Key Exchange (ECDH) === | |||
Is a key establishment protocol that allows two parties which know the common domain parameter of a curve <math>E(p,a,b,G,n,h) </math> to calculate a common shared secret over an insecure channel. Assuming Alice and Bob like to establish a common shard secret for communication, both need to generate a keypair. A keypair consists of a private/secret key <math>d_i</math> and a public key <math>Q_i</math> . For the private key <math>d_i</math> a integer less than <math>n</math> is randomly selected, then both need to calculate their public key with <math>Q_i=d_i \cdot G</math>, so that Alice has a pair of <math>(d_A,Q_A)</math>. She sends her public key <math>Q_A</math> to Bob and he sends back his public key <math>Q_B</math>. Now both are able to calculate the shared secret, Alice computes <math>K_{AB}=Q_B\cdot d_A</math> and Bob <math>K_{BA}=Q_A \cdot d_B</math>. This works because <math>K_{AB}=Q_B \cdot d_A=(d_B \cdot G) \cdot d_A=(d_A \cdot G) \cdot d_B=K_{BA}</math>. | |||
== Online resources== | |||
* https://safecurves.cr.yp.to/ | |||
* https://andrea.corbellini.name/2015/05/17/elliptic-curve-cryptography-a-gentle-introduction/ | |||
* https://www.allaboutcircuits.com/technical-articles/elliptic-curve-cryptography-in-embedded-systems/ | |||
==References== | |||
<references> | |||
<ref name="HMV">Hankerson, D., A. Menezes and S. Vanstome: Guide to Elliptic Curve Cryptographie. Springer Verlag New York, Inc., 1. Auflage, 2004.</ref> | |||
<ref name="SEC2-v1">Certicom Research. "SEC 2: Recommended Elliptic Curve Domain Parameters, Version 1.0." September 20, 2000. Local copy of http://www.secg.org/SEC2-Ver-1.0.pdf, which keeps moving</ref> | |||
<ref name="SEC2-v2">Certicom Research. "SEC 2: Recommended Elliptic Curve Domain Parameters, Version 2.0." January 27, 2010. Local copy of [http://www.secg.org/sec2-v2.pdf], which keeps moving.</ref> | |||
<ref name="Brainpool">ECC Brainpool. "ECC Brainpool standard curves and curve generation." October 2005. https://tools.ietf.org/html/rfc5639</ref> | |||
<ref name="ANSI-X9.62">Accredited Standards Committee X9. "American National Standard X9.62-1999, Public key cryptography for the financial services industry: the elliptic curve digital signature algorithm (ECDSA)." 1999.</ref> | |||
<ref name="ANSI-X9.63">Accredited Standards Committee X9. "American National Standard X9.63-2001, Public key cryptography for the financial services industry: key agreement and key transport using elliptic curve cryptography." 1999.</ref> | |||
<ref name="NIST 186-2">National Institute for Standards and Technology. "Digital signature standard." Federal Information Processing Standards Publication 186-2. 2000. [http://csrc.nist.gov/publications/fips/archive/fips186-2/fips186-2.pdf]</ref> | |||
<ref name="NIST Suite B">Committee on National Security Systems. "National information assurance policy on the use of public standards for the secure sharing of information among national security systems." 1 October 2012.</ref> | |||
= | <ref name="zigbee">https://zigbeealliance.org/wp-content/uploads/2019/11/docs-07-5356-19-0zse-zigbee-smart-energy-profile-specification.pdf</ref> | ||
< | <ref name="vanet">hhttps://www.researchgate.net/publication/216022102_Analysis_of_ECDSA_authentication_processing_in_VANETs</ref> | ||
<ref name="nfc">https://nfc-forum.org/wp-content/uploads/2013/12/Elliptic-Curve-Certificates-and-Signatures-for-NFC-Signature-Records-RIM.pdf</ref> | |||
<ref name="curve25519">Daniel Bernstein, Curve25519:new Diffie-Hellman speed records, Springer Berlin Heidelberg, 2006. https://cr.yp.to/ecdh/curve25519-20060209.pdf, [accessed 30.04.2020]</ref> | |||
</references> | |||
[[Category:Basic]] | [[Category:Basic]] | ||
Latest revision as of 09:33, 30 April 2020
Summary
This documentary gives a brief introduction into elliptic curve cryptography
Elliptic Curve Cryptography (ECC)
Elliptic curve cryptography is a part of asymmetric cryptography, it is based on the mathematical hard problem to find a solution for the elliptic curve discrete logarithm. The calculations are performed on the algebraic structure of elliptic curves over finite fields, which means we compute points on a elliptic curve over finite field by applying the group operations double and add. The scalar multiplication of a point on an elliptic curve over a finite field is equivalent to the exponentation of a number in a prime field, therefore the inversion is also called discrete logarithm. First proposed application of elliptic curves in cryptography was random number generations, now ECC is widely used for key establishment and digital signature schemes. The main advantage of ECC is that it offers the same security level compared to RSA with shorter key lengths. Efficient implementations make ECC usable for constraint devices enabling security and privacy protection for emerging IoT systems.
Example usage of ECC in IoT:
| ZigBee Smart Energy(1.x and 1.2)[1] | sect163k1(1.x), sect283k1(1.2) |
| Vehicular Ad-Hoc Networks (IEEE1609.2) [2] | secp224r1,secp256r1 |
| NFC Forum Signature Record Type Definition(RTD) [3] | sec192r1, secp224r1, sect233k1, sect233r1 |
Simple Weierstrass Elliptic Curve Presentation
- Simple Weierstrass form curve equation:
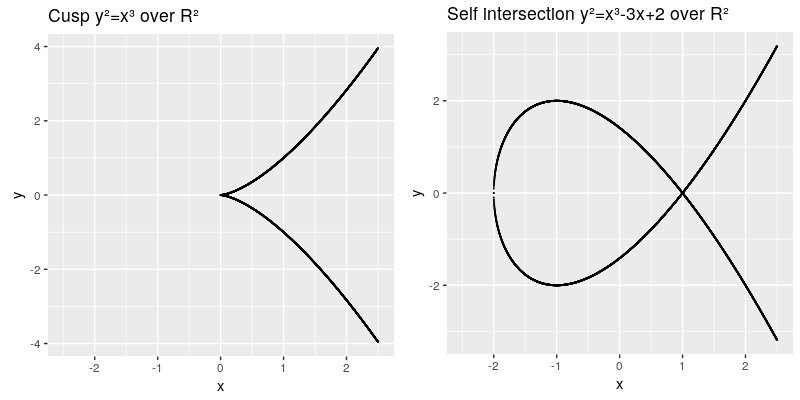
The elliptic curve are all points in the coordinates which fulfill the cubic curve equation, whereas and are called the characteristic of the curve. The curve needs to be smooth, which means that it will not contain any singularities such as a cusp or a self intersection,
This can be also described by the term:
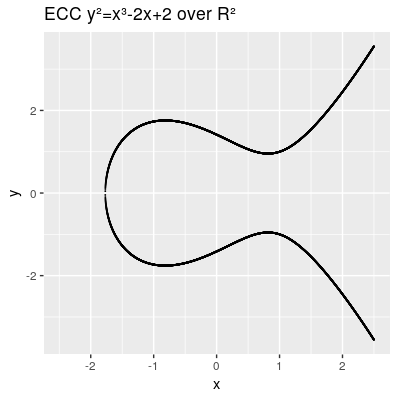
Another characteristic we need to introduce is the point at infinity denoted by (also known as ideal point), which can be thought as identity element infinitly raised on the y axis. Therefore our points on the elliptic curve over R² all fulfill this equation . A valid curve over rational numbers is shown in the next image.
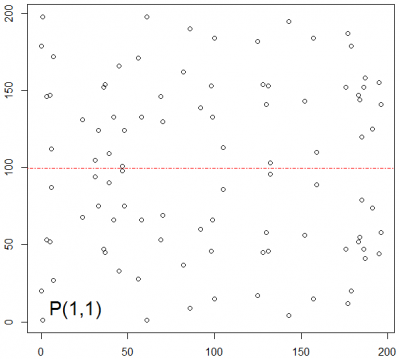
In cryptography elliptic curves over finite fields are used. The number of rational points of an elliptic curve over a finite field e.g. the prime field can be computed with the Schoof-Elkies-Alkin algorithm, which is implemented in the PARI/GP library. The Hasse theorem gives an estimation of the number of points in the intervall:
The next figure shows a elliptic cuve over a finite field, the prime field GF(199). On each y-axis are two points, the point and its inverse point, mapped into the positive space of the prime field.
Group Operations on Elliptic Curves
According to the group law all points support following operations:
- Point Addition:
- Case -> Point Doubling:
- Case -> Inversion of a Point:
Point Addition
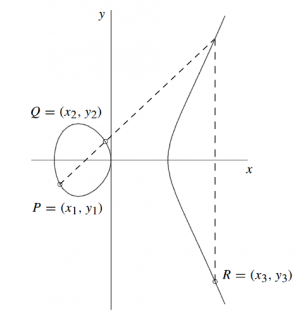
Given the elliptic curve and the points and , we can calculate the coordinates of the point by adding this two points as follows.[4]
In the geometric derivation a line/chord is drawn through and , the result point R is the symmtric inversion on the axis of the point at the 3rd intersection on the elliptic curve. 1. Calculation of the equation of the chord
- We know the equation from the line
- Therefore
and we can find the intersection with the y-axis and achieve d .
2. Calculation of we can find by insertion in the line equation:
2. Calculation of
- In the intersection point of the chord with the tangent, the coordinate satisfies both equations, therefore we can extract from both equations and get a new equation.
- This is a equation of 3rd degree therefore we have 3 cross points, which can be searched by
- Now we can conclude from the second term
- and achieve a solution for by:
This operation is also called the Point Addition in affine coordinates and the computational costs are 1 x inversion, 2 x multiplications and 1 x squaring. Interactive tool to visualize point addition.
Point Doubling
Given the elliptic curve and the special case with the point . The result point is achieved by doubling the point as follows.[4]
For the doubling a tangent is drawn at point . At the intersection with the elliptic curve again the inversion on the is taken to achieve the result point .
1. The tangent in point has the equation of . The slope of the tangent is calculated by the differential function of by and .
and then the intersection of the tangent with the y-axis is calculated by inserting the point coordinates in the equation of the tangent .
2. The y-coordinate of the point of the second intersection with the elliptic curve can be calculated by inserting the point coordinates in the equation of the tangent and multiply by to get the inverse point on the y axis.
3. is achieved by inserting
- The crossing points can be searched by
- Now we can conclude from the second term
- and achieve a solution for by:
This operation is also called the Point Doubling in affine coordinates and the computational costs are 1 x inversion, 2 x multiplications and 2 x squarings.
Example of elliptic point operations over an elliptic curve over a finite field
Given a curve E we examine the basic operations on the elliptic curve:
- Validation of the elliptic curve: This is done to determine if the elliptic curve is smooth by calculating the discriminant.
therefore holds and this curve can be used for EC operations.
- Examining the number of points: Choosing one random point of the curve P(6,1) as generator G all points on the curve can be calculated with the equations given above over a the prime field 17. This means first the point gets doubled and a modulo 17 operation is applied. Then continuously all other points are calculated by adding the point P to the result each time applying the modulo 17 .
| (6,1) | (4,8) | (15,5) | (9,9) | (11,14) | (2,6) | (1,14) | (12,1) |
| (16,16) | (10,10) | (5,14) | (5,3) | (10,7) | (16,1) | (12,16) | (1,3) |
| (2,11) | (11,3) | (9,8) | (15,12) | (4,9) | (6,16) |
All by point P(6,1) generated 23 points satisfy the equation of the elliptic curve. Notice that each x value has two y values.
- Point Addition:
The points P(6,1) and J(10,10) are added with calculations in the finite field using the modular operation each time.
Solution: The addition of point P and J to get the result point R is visualized in the next figure.
Algebraic group properties of the points
The points further comply associative and commutative algebraic group laws and the handling of the neutral element:
- Closure:
- Associative law:
- Identity element and inverse that:
- Cummutative law:
The inverse point of a point P(x,y) is therefore P(x,-y).
Scalar Multiplication
Is the mainly used operation on elliptic curves in cryptography, it adds times the point of the elliptic curve over a finite field e.g. prime field .
Double and Add algorithm
Calculation in projective coordinates
Side Channel Attacks
Montgomery ladder
Standardization of elliptic curves
The domain parameters for ECC schemes are described in the form .
| Parameter description | |
|---|---|
| defines the field size, either a prime or where m is prime | |
| first parameter of the curve equation | |
| second parameter of the curve equation | |
| generating point consisting of both point coordinates | |
| order of the point | |
| cofactor which is equal to the order of the curve divided by | |
The generation of safe elliptic curves is an effort, hence it is recommended to use standardized known curves. First curves have been standardized in the ANSI X9.62 standard by the American National Standards Institute(ANSI) in 1999 [5], these have been extended or replaced by ANSI X9.63 in 2001[6] and ANSI FRP256V1 in 2011. The National Institute of Standard and Technology (NIST) defined their own curves in the NIST FIPS 186-2 in 2000[7]. In the same year the Certicom published the widely-used Certicom SEC2 curves [8] which have been continously updated in version 2 [9]. In 2005 NIST published the NSA Suite B[10] and the Federal Office for Information Security in Germany proposed their own randomly generated curves in the same year[11].
Curve25519
Curve25519 is a highly optimized curve proposed by Daniel J. Bernstein (djb) in 2005 [12]. The curve equation is
over a prime field
Edward curves
Applications of Elliptic Curve Cryptography
Example: Elliptic Curve Diffie Hellman Key Exchange (ECDH)
Is a key establishment protocol that allows two parties which know the common domain parameter of a curve to calculate a common shared secret over an insecure channel. Assuming Alice and Bob like to establish a common shard secret for communication, both need to generate a keypair. A keypair consists of a private/secret key and a public key . For the private key a integer less than is randomly selected, then both need to calculate their public key with , so that Alice has a pair of . She sends her public key to Bob and he sends back his public key . Now both are able to calculate the shared secret, Alice computes and Bob . This works because .
Online resources
- https://safecurves.cr.yp.to/
- https://andrea.corbellini.name/2015/05/17/elliptic-curve-cryptography-a-gentle-introduction/
- https://www.allaboutcircuits.com/technical-articles/elliptic-curve-cryptography-in-embedded-systems/
References
- ↑ https://zigbeealliance.org/wp-content/uploads/2019/11/docs-07-5356-19-0zse-zigbee-smart-energy-profile-specification.pdf
- ↑ hhttps://www.researchgate.net/publication/216022102_Analysis_of_ECDSA_authentication_processing_in_VANETs
- ↑ https://nfc-forum.org/wp-content/uploads/2013/12/Elliptic-Curve-Certificates-and-Signatures-for-NFC-Signature-Records-RIM.pdf
- ↑ 4.0 4.1 Hankerson, D., A. Menezes and S. Vanstome: Guide to Elliptic Curve Cryptographie. Springer Verlag New York, Inc., 1. Auflage, 2004.
- ↑ Accredited Standards Committee X9. "American National Standard X9.62-1999, Public key cryptography for the financial services industry: the elliptic curve digital signature algorithm (ECDSA)." 1999.
- ↑ Accredited Standards Committee X9. "American National Standard X9.63-2001, Public key cryptography for the financial services industry: key agreement and key transport using elliptic curve cryptography." 1999.
- ↑ National Institute for Standards and Technology. "Digital signature standard." Federal Information Processing Standards Publication 186-2. 2000. [1]
- ↑ Certicom Research. "SEC 2: Recommended Elliptic Curve Domain Parameters, Version 1.0." September 20, 2000. Local copy of http://www.secg.org/SEC2-Ver-1.0.pdf, which keeps moving
- ↑ Certicom Research. "SEC 2: Recommended Elliptic Curve Domain Parameters, Version 2.0." January 27, 2010. Local copy of [2], which keeps moving.
- ↑ Committee on National Security Systems. "National information assurance policy on the use of public standards for the secure sharing of information among national security systems." 1 October 2012.
- ↑ ECC Brainpool. "ECC Brainpool standard curves and curve generation." October 2005. https://tools.ietf.org/html/rfc5639
- ↑ Daniel Bernstein, Curve25519:new Diffie-Hellman speed records, Springer Berlin Heidelberg, 2006. https://cr.yp.to/ecdh/curve25519-20060209.pdf, [accessed 30.04.2020]