Elliptic Curve Cryptography
Summary
This documentary gives a brief introduction into elliptic curve cryptography
Elliptic Curve Cryptography
Elliptic curve cryptography is a part of asymmetric cryptography, it is based on the mathematical hard problem to find a solution for the elliptic curve discrete logarithm. The calculations are performed on the algebraic structure of elliptic curves over finite fields, which means we compute points on a elliptic curve over finite field by applying the group operations double and add. The scalar multiplication of a point on an elliptic curve over a finite field is equivalent to the exponentation of a number in a prime field, therefore the inversion is also called discrete logarithm.
First proposed application of elliptic curves in cryptography was random number generations, now ECC is widely used for key establishment and digital signature schemes.
Simple Weierstrass Elliptic Curve Presentation
- Simple Weierstrass form curve equation:
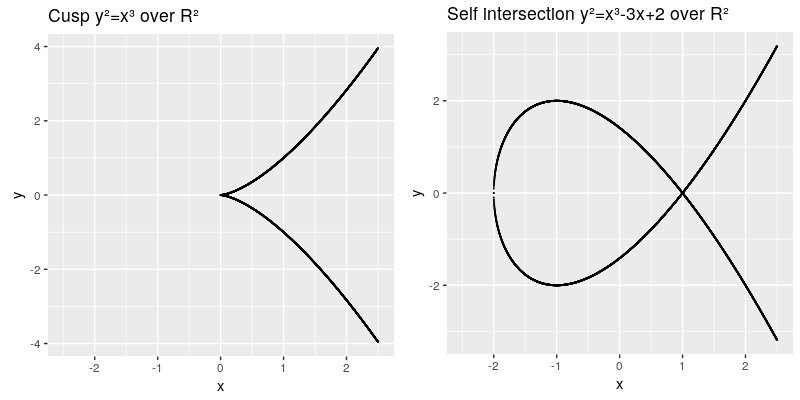
The elliptic curve are all points in the coordinates which fulfill the cubic curve equation, whereas a and b are called the characteristic of the curve. The curve needs to be smooth, which means that it will not contain any singularities such as a cusp or a self intersection,
This can be also described by the term:
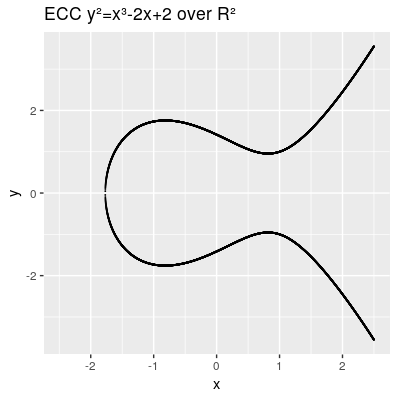
Another characteristic we need to introduce is the point at infinity denoted by (also known as ideal point), which can be thought as identity element infinitly raised on the y axis. Therefore our points on the elliptic curve over R² all fulfill this equation . A valid curve is shown in the next image.
Group Operations on Elliptic Curves
According to the group law all points support following operations:
- Point Addition:
- Case: -> Point Doubling :
- Case: -> Inversion of a Point:
TODO:Need to install link target extension: https://www.mediawiki.org/wiki/Extension:LinkTarget
Point Addition
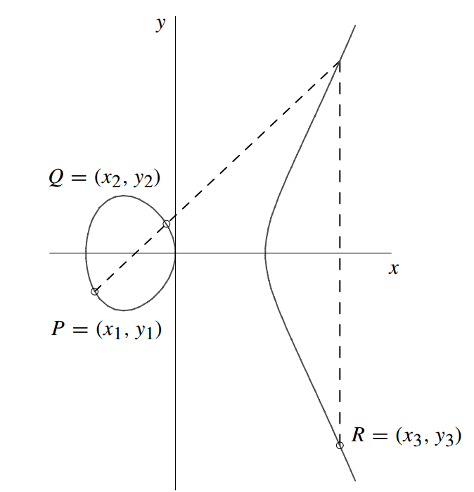
Given the elliptic curve and the points and , we can caculate the coordinates of the point as follows.[1]
1. Calculation of
- We know the equation from the line
- Therfore
and we can find the intersection with the y-axis and achieve d .
- we can find by insertion in the line equation:
2. Calculation of
- Now we insert the values of the line equation into the elliptic curve equation:
- The cross points can be searched by
- Now we can conclude from the second term
- and achieve a solution for by:
This is also called the calculations in affine coordinates and the computational costs are 1 x inversion, 2 x multiplications and 1 x quadration. Interactive tool to visualize point addition online at https://cdn.rawgit.com/andreacorbellini/ecc/920b29a/interactive/reals-add.html. The Point Addition over an elliptic curve over a finite field (e.g. prime field) is shown in the next image.
Algebraic group of points
The points further comply associative and commutative algebraic group laws and the handling of the neutral element:
- Closure:
- Associative law:
- Identity element and inverse that:
- Cummutative law:
The inverse point of a point P(x,y) is therefore P(x,-y).
Scalar Multiplication
Is main used operation in cryptography, it adds n times the point P of the elliptic curve over a prime field.
Double and Add algorithm
Calculation in projective coordinates
Side Channel Attacks
Montgomery ladder
Standardization of elliptic curves
The domain parameters for ECC schemes are described in the form .
| Parameter description | |
|---|---|
| defines the field size, either a prime or where m is prime | |
| first parameter of the curve equation | |
| second parameter of the curve equation | |
| generating point consisting of both point coordinates | |
| order of the point | |
| cofactor which is equalto the order of the curve divided by | |
The generation of safe elliptic curves is an effort, hence it is recommended to use standardized known curves. First curves have been standardized in the ANSI X9.62 standard by the American National Standards Institute(ANSI) in 1999 [2], these have been extended or replaced by ANSI X9.63 in 2001[3] and ANSI FRP256V1 in 2011. The National Institute of Standard and Technology (NIST) defined their own curves in the NIST FIPS 186-2 in 2000[4]. In the same year the Certicom published the widely-used Certicom SEC2 curves [5] which have been continously updated in version 2 [6]. In 2005 NIST published the NSA Suite B[7] and the Federal Office for Information Security in Germany proposed their own randomly generated curves in the same year[8].
Curve25519
Curve25519 is a highly optimized curve proposed by Daniel J. Bernstein (djb) in 2005. The curve equation is over a prime field
Edward curves
Applications of Elliptic Curve Cryptography
Example Elliptic Curve Diffie Hellman Key Exchange (ECDH)
Is a key establishment protocol that allows two parties which know the parameter of a curve to calculate a common shared secret over an insecure channel.
Online resources
https://safecurves.cr.yp.to/ https://andrea.corbellini.name/2015/05/17/elliptic-curve-cryptography-a-gentle-introduction/
References
- ↑ Hankerson, D., A. Menezes and S. Vanstome: Guide to Elliptic Curve Cryptographie. Springer Verlag New York, Inc., 1. Auflage, 2004.
- ↑ Accredited Standards Committee X9. "American National Standard X9.62-1999, Public key cryptography for the financial services industry: the elliptic curve digital signature algorithm (ECDSA)." 1999.
- ↑ Accredited Standards Committee X9. "American National Standard X9.63-2001, Public key cryptography for the financial services industry: key agreement and key transport using elliptic curve cryptography." 1999.
- ↑ National Institute for Standards and Technology. "Digital signature standard." Federal Information Processing Standards Publication 186-2. 2000. [1]
- ↑ Certicom Research. "SEC 2: Recommended Elliptic Curve Domain Parameters, Version 1.0." September 20, 2000. Local copy of http://www.secg.org/SEC2-Ver-1.0.pdf, which keeps moving
- ↑ Certicom Research. "SEC 2: Recommended Elliptic Curve Domain Parameters, Version 2.0." January 27, 2010. Local copy of [2], which keeps moving.
- ↑ Committee on National Security Systems. "National information assurance policy on the use of public standards for the secure sharing of information among national security systems." 1 October 2012.
- ↑ ECC Brainpool. "ECC Brainpool standard curves and curve generation." October 2005. https://tools.ietf.org/html/rfc5639