File:Wireshark tether app device decovery.png
Original file (3,072 × 2,106 pixels, file size: 1.21 MB, MIME type: image/png)
Summary
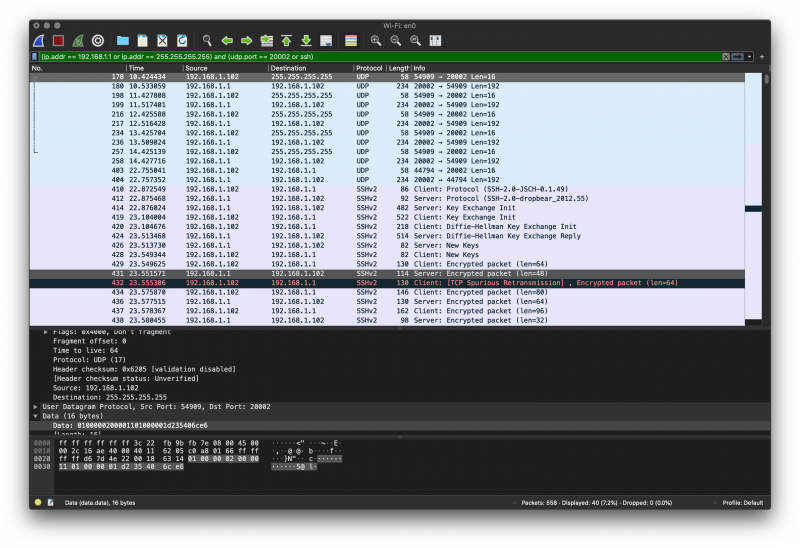
Before establishing an SSH session, the Tether app sends an multicast discovery UDP packet to 255.255.255.255 on port 20002. This message gets send 4 times. After that, the Tether app send another unicast message to responding devices on port 20002. The syntax of the payload is mostly unclear, an change after a restart. Anyway a device will still respond to any payload captured at any time. I assume that this discovery process is used to get device capatibilities and to finally initialize a secure channel via SSH. How the SSH tunnel gets initiated is also unkown at this state of research.
File history
Click on a date/time to view the file as it appeared at that time.
| Date/Time | Thumbnail | Dimensions | User | Comment | |
|---|---|---|---|---|---|
| current | 20:13, 1 July 2020 |  | 3,072 × 2,106 (1.21 MB) | JPDoe (talk | contribs) | Before establishing an SSH session, the Tether app sends an multicast discovery UDP packet to <code>255.255.255.255</code> on port <code>20002</code>. This message gets send 4 times. After that, the Tether app send another unicast message to responding... |
You cannot overwrite this file.
File usage
The following page uses this file: