GSM IMSI-Catcher
Summary
This article explains how to build an GSM IMSI-Catcher with the SDR called HackRF One.
Requirements
- Operating system: Ubuntu 20.04 LTS (Focal Fossa)!
- Packages: git, Wireshark
- SDR HackRF One
Description
Installation of the necessary tools
(Do not use any other OS than Ubuntu 20.04 LTS (Focal Fossa)!!!)
Enter these commands in the shell
git clone https://github.com/Oros42/IMSI-catcher.git cd IMSI-catcher
sudo apt install python3-numpy python3-scipy python3-scapy
sudo apt-get install -y \ cmake \ autoconf \ libtool \ pkg-config \ build-essential \ python-docutils \ libcppunit-dev \ swig \ doxygen \ liblog4cpp5-dev \ gnuradio-dev \ gr-osmosdr \ libosmocore-dev \ liborc-0.4-dev \ swig
git clone -b maint-3.8 https://github.com/velichkov/gr-gsm.git
cd gr-gsm mkdir build cd build cmake .. make -j 4 sudo make install sudo ldconfig echo 'export PYTHONPATH=/usr/local/lib/python3/dist-packages/:$PYTHONPATH' >> ~/.bashrc
IMSI-catching in action
Now that all necessary tools are installed, first thing to do is connect the HackRF One to the Computer, in case you are using a VM ensure that you mounted your USB device to the VM.
It is recommended do start each tool in separate terminals!
First start
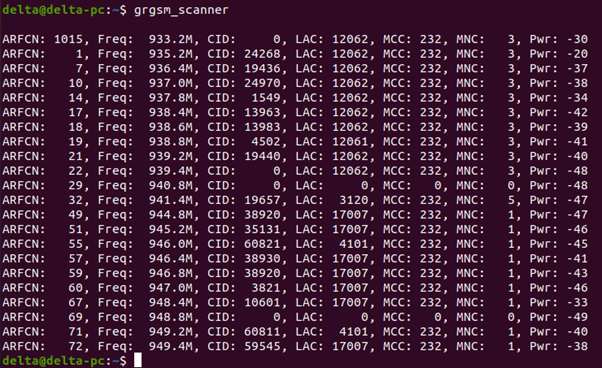
grgsm_scanner
grgsm_scanner is used to perform a GSM frequency channel scan to identify active frequencies in a given area. This should now list the active frequencies that can be received at the current location.
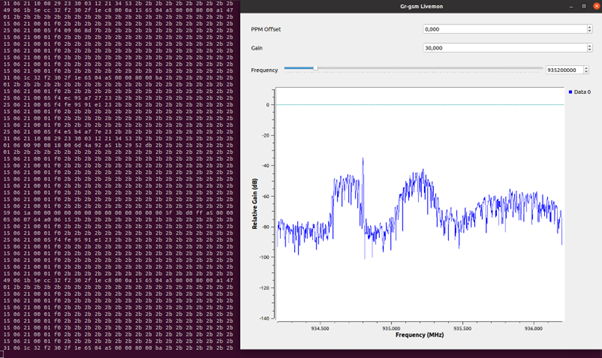
Then start grgsm_livemon with one of the frequencies that has just been discovered in the previous step.
grgsm_livemon -f <Frequency scanned with grgsm_scanner>
grgsm_livemon is used for capturing and analyzing GSM signals in a specific frequency band using a software-defined radio (SDR) in this case the HackRF One. This should now open a GUI displaying the scanner and the terminal should show incoming Hex values received by the SDR.
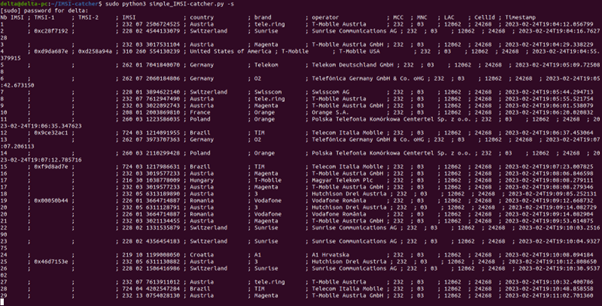
Next up is the simple_IMSI-catcher.py this is a handy script which takes the incoming radio stream from grgsm_livemon and decodes and extracts the most important information.
sudo python3 simple_IMSI-catcher.py -s
It list all the information in a nicely formatted table. This could take a minute until something is displayed. If there are issues with the scrip not displaying anything simple restart
a) the script
b) livemon
c) both
or pick an other frequency.
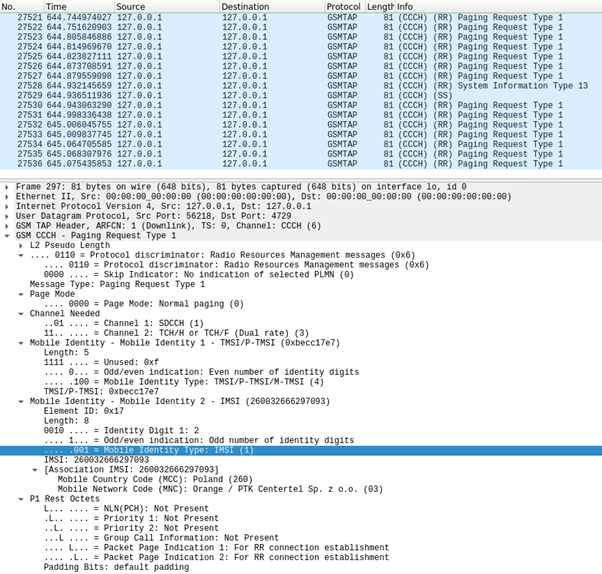
There is one extra step that can be done to display extra information, for that enter:
sudo wireshark -k -Y '!icmp && gsmtap' -i lo
This command captures GSM TAP protocol packets on the loopback interface using Wireshark, excluding ICMP packets. The GSMTAP protocol is a format used for capturing GSM protocol messages over the air interface. It is a simple protocol that encapsulates GSM protocol messages inside a UDP packet.
Now it should list all gsmtap protocol packets in real time giving more information about the transmission over the connected SDR.
Glossary
ARFCN: The Absolute Radio Frequency Channel Number, which is used to identify the specific frequency used by a particular channel. This number is assigned by the network operator and is used to differentiate between different channels.
Freq: The center frequency used by the channel, measured in megahertz (MHz).
CID: The Cell IDentifier, which is a unique identifier for the specific cell (or base station) that is providing service on this channel. A value of 0 indicates that the CID is not available or not applicable.
LAC: Location Area Code, is the unique number given to each location area within the network. The served area of a cellular radio access network is usually divided into location areas, consisting of one or several radio cells. The LAC is used as a unique reference for the location of a mobile subscriber. This code is necessary to address the subscriber in the case of an incoming call.
MCC: Mobile Country Code, a unique identifier identifying the home country of a Mobile network operator. It is a three-digit identification of the country. The MCC is especially relevant for determining the country of inbound roamers.
MNC: The Mobile Network Code, which is a two- or three-digit code used to identify the specific network operator within the country identified by the MCC.
Pwr: The signal strength or power level of the channel, measured in decibels relative to one milliwatt (dBm). The less negative a value indicates the stronger the signal.
IMSI: An IMSI (International Mobile Subscriber Identity) is a unique identification number assigned to a mobile device's SIM card, and it does not contain any information about the user's personal identity, such as name or address. However, mobile network operators use IMSI numbers to associate a mobile device with a subscriber's account, which can contain personal information such as the subscriber's name, billing address, and payment details. It is used to identify and authenticate the user on the mobile network.
TMSI: TMSI stands for Temporary Mobile Subscriber Identity. It is a temporary identifier assigned to a mobile device by a cellular network. The TMSI is used as a substitute for the IMSI (International Mobile Subscriber Identity) in order to protect the privacy of the user. When a mobile device first connects to a cellular network, it sends its IMSI to the network, which assigns a TMSI to the device. The TMSI is then used instead of the IMSI for subsequent communications between the device and the network. This helps to prevent eavesdropping and other security threats by making it more difficult to track a specific device. The TMSI is updated periodically by the network, and can also be updated by the device if it detects that its TMSI has been compromised.
Used Hardware
HackRF One Software Defined Radio (SDR)
References
https://github.com/velichkov/gr-gsm.git https://github.com/Oros42/IMSI-catcher