Difference between revisions of "Hak5 LAN Turtle"
Jump to navigation
Jump to search
| Line 19: | Line 19: | ||
=== Setting up the LAN Turtle === | === Setting up the LAN Turtle === | ||
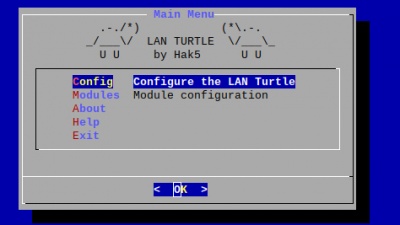
[[File:LANTurtleConfig.jpg|thumb|right|400px||LAN Turtle config shell interface]] | |||
# Start by plugging the turtle into a controlled computer. | # Start by plugging the turtle into a controlled computer. | ||
# Your computer will get an 172.16.84.x address as soon as the startup sequence of the turtle finished | # Your computer will get an 172.16.84.x address as soon as the startup sequence of the turtle finished | ||
| Line 26: | Line 26: | ||
# Then the LAN turtle can be configured and modules can be installed in the interface. | # Then the LAN turtle can be configured and modules can be installed in the interface. | ||
# If you end the interface you will be greeted with an normal Linux shell but you can open it again with the <code>turtle command</code> | # If you end the interface you will be greeted with an normal Linux shell but you can open it again with the <code>turtle command</code> | ||
=== Step 2 === | === Step 2 === | ||
Revision as of 15:24, 2 June 2020
Summary
The Lan turtle is an tool for Penetration testers and Systems Admins disguised as an simple USB Ethernet adapter.
Use Cases
The use cases may differ between the user groups.
Penetration users can use it for:
- Network scanner with nmap
- DNS spoofing clients
- Monitoring Browser Connections
Sysadmin my us it for:
- Access the LAN from an remote location with an VPN tunnel
- sending status reports via email or https periodically
Description
Setting up the LAN Turtle
- Start by plugging the turtle into a controlled computer.
- Your computer will get an 172.16.84.x address as soon as the startup sequence of the turtle finished
- Connect to it with
ssh root@172.16.84.1and enter the passwordsh3lls - The simplistic graphical shell interface will prompt you to change the password but the old one is also allowed.
- Then the LAN turtle can be configured and modules can be installed in the interface.
- If you end the interface you will be greeted with an normal Linux shell but you can open it again with the
turtle command
Step 2
Used Hardware
Device to be used with this documentation Maybe another device to be used with this documentation
Courses
- A course where this documentation was used (2017, 2018)
- Another one (2018)