Hak5 LAN Turtle
Summary
The Lan turtle is an tool for Penetration testers and Systems Admins disguised as an simple USB Ethernet adapter.
Use Cases
The use cases may differ between the user groups.
Penetration users can use it for:
- Network scanning with nmap
- DNS spoofing clients
- Monitoring Browser Connections
Sysadmin may us it to:
- Access the LAN from an remote location with an VPN tunnel
- Send periodical status reports via email or https
Description
Setting up the LAN Turtle
- Start by plugging the turtle into a by you controlled computer.
- Your computer will get an 172.16.84.x address as soon as the startup sequence of the turtle finished
- Connect to it with
ssh root@172.16.84.1and enter the passwordsh3lls - The simplistic graphical shell interface will prompt you to change the password but the old one is also allowed.
- Then the LAN turtle can be configured and modules can be installed in the interface.
- If you end the interface you will be greeted with an normal Linux shell but you can open it again with the
turtlecommand
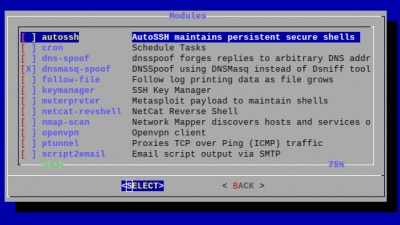
Using the Turtle modules
The LAN Turtle comes packed with pre-installed tool. Furthermore it is possible to program your own or download them from the internet and configure them with the module manager as well.
Auto ssh
Auto ssh opens an secure shell and keep it alive as long as u want. Before the usage can start you need to generate RSA keypairs via the key manager module. After configuring the auto ssh module you will be able to access the LAN Turtle form the public server at port 2222.
Cron
With the cron module you can access and modify the cron tab even simpler than usual. The Cron Tab allows you to schedule time driven shell commands.
Meterpreter
This module deploys an persistent shell to the Metasploit Framework of an other Machine.
OpenVPN
With the OpenVPN module you will be able to create an OpenVPN gateway device which allows you to send the captured data to your operating Network.
SSHFS
SSHFS mounts the filesystem of an remote device via ssh.
namp-scan
This module uses nmap for discovering running devices and their port of the current LAN network.
urlsnarf
URL Snarf allows you to capture which websites were accessed by the plugged in computer. URL Snarf only works with http webpages which are hard to find today.
Creating an Network discovery device with the LAN Turtle
For example project we use the following modules:
- Cron Job
- sshfs
- nmap-scan
Step 1: Configure sshfs
- Access the sshfs module via the module manager
- Go to the configure tab and insert
- Host: IP address of the remote server
- Port:
22 - User: the username
- Path: This can be left blank if you want to use the users home directory
- Start ssfs and enable it for start up
Step 2: nmap-scan
- Access the nmap-scan module via the module manager
- Go to the configure tab and insert
- target:
192.168.0.1-255(This may differ for our network) - logflie:
/sshfs/ - use the desired attack profile
- save the configuration with execute
- target:
Step 3: cron job
- add in the con config
*/15 * * * * start nmap-scan
This line start an nmap-scan every 15 minutes.