IOT Security: Pentesting on IP Cameras
Summary
This is a documentation on pentesting performed on TP-link Kasa Cam Smart Home Camera KC120, Ezviz CS-C1C and Abus PPIC32020.
Requirements
Operating System
- Kali Linux 2022.2
Hardware
- TP-link Kasa Cam Smart Home Camera KC120
- Encryption: 128-Bit-AES, WPA/WPA2-PSK
- Storage: Amazon Web Services (AWS) Cloud
- Ezviz CS-C1C
- Encryption: 64/128-bit WEP, WPA/WPA2, WPA-PSK/WPA2-PSK
- Storage: EZVIZ cloud and/or MicroSD
- Abus PPIC32020
- Encryption: AES 128bit, WPA/WPA2-PSK
- Storage: MicroSD
Apps
- Kasa Smartphone application (IOS or Android)
- Ezviz Smartphone application (IOS or Android)
- ABUS App2Cam Plus Smartphone application (IOS or Android)
Description
A penetration test can be divided into several stages:
- Pre-Engagement Interactions
Working with a client to absolutely outline and report evaluation objectives, scope, and policies of engagement. There are three ways to run the test. In our case, the tester is doing a black-box test, which means the tester doesn't know anything about the system to be tested, i.e. he/she has to act as a hacker. The pentester needs to create a contract with the client on when, how, and what to test. In addition, there should be a privilege explanation and a non-disclosure agreement between the pentester and the client.
- Gathering Information
Collecting and examing key data regarding the software and its infrastructure. We recommend creating an architectural sketch (deployment diagram). The camera software itself may not be threateningly modelable, but you need to identify the protocol for all the surrounding systems that the camera needs to communicate with. After that, you should identify who uses the protocol and who accesses them.
- Threat Modeling
Threat modeling is an established technique of figuring out and prioritizing ability threats to a system and figuring out the value that ability mitigations might have in decreasing or neutralizing one's threats. A threat is a set of situations that might purpose harm, which means a hypothetical action where the attacker exploits a vulnerability.
3 main types of threats in the IoT are taking control, stealing information, and disrupting service.
The OWASP Top 10 is a standard awareness document that represents a broad consensus about the most critical security risks to web applications.
This includes the following top 10 IOT vulnerabilities: weak passwords, insecure network services, insecure ecosystem interfaces, lack of secure update mechanism, use of insecure or outdated components, insufficient privacy protection, insecure data transfer and storage, lack of device management, insecure default settings and lack of physical hardening.
These elements should be considered: IoT device, cloud, mobile application, network interfaces, software, use of encryption, use of authentication, physical security, and USB ports.
Suppose you have an IP camera installed and you want to log in remotely to monitor your home situation. Such a simple implementation poses many risk factors and creates a huge attack surface in the environment. An attacker could remotely scan for a vulnerability in an IP camera, brute force, connect (if you have a backdoor or the same hard-coded SSH key), and exploit it.
- Vulnerability Analysis
Find current vulnerabilities and identify any potential security weaknesses that could allow an outside attacker to gain access to the environment.
- Exploitation
The pentester tries to establish a connection with the target and exploit the vulnerabilities found in the previous phase. Exploitation can be software, shellcode, certain commands, code injection, remote exploits without any prior access, and local exploits with prior access to the system.
- Post Exploitation
After successful exploitation, it's far crucial to report all steps and tools - so that you can demonstrate the impact and possible consequences of the vulnerabilities to the client.
- Reporting
Providing a complete report with deep evaluation and suggestions on the way to mitigate the found vulnerabilities. It consists of two parts: An executive summary and a technical report. The executive summary provides a background overview, test overview, risk profile, general findings, an overview of the tasks required to mitigate the problem, and short-term and long-term goals to improve security increase. It is important to document how easy it was to find this vulnerability and what the countermeasures are. The risk analysis is the most important part because the pentester needs to consider how high the risks of the detected vulnerabilities are and how these vulnerabilities could affect the company. These results are used to make company decisions that could have a significant impact on the company. The technical report details the intelligence collection and vulnerability testing results, and the client's internet footprint.
- Resolution & Re-Testing
The client follows the recommendations and after completing patching the vulnerabilities a re-test is run.
Set-up
You need to set up the camera together with your phone app and allow it to connect with the identical WiFi that your smartphone uses. To find out the IP Address of the camera you need to install scanning tools, that can gain access to devices in your subnet. We recommend that you create a virtual machine and after that, you need to install Kali Linux on your VM. With this operating system, many tools are already pre-installed and ready to use.
Scanning Tools
Nmap
Nmap Scans will give you important information about the target system.
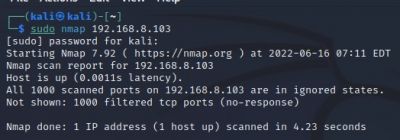
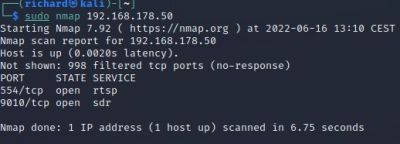
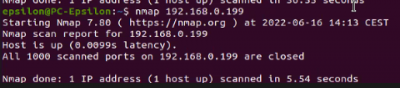
Target specification:
$sudo nmap <target IP> Scan a single IP
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
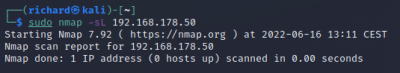
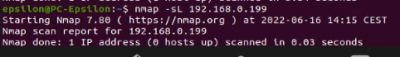
DNS query on a specific host:
$sudo namp -sL <target IP>
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
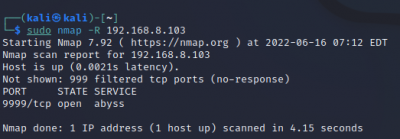
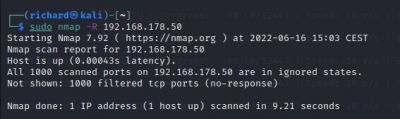
Force reverse DNS resolution:
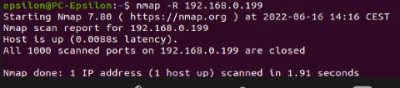
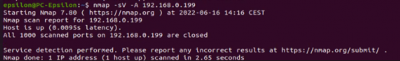
$sudo nmap -R <target IP>
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
Perform an aggressive scan and service version detection:
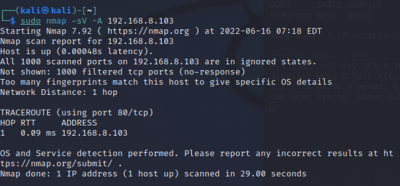
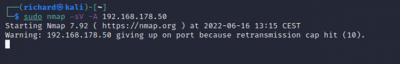
$sudo nmap -sV -A <target IP>
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
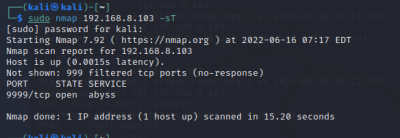
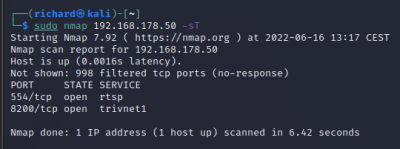
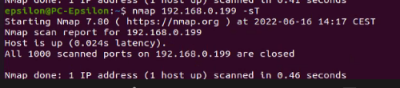
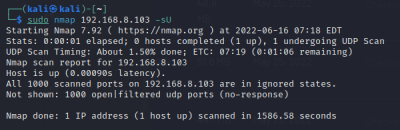
Scan TCP/UDP ports:
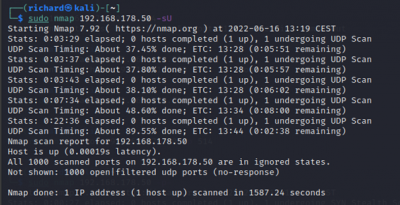
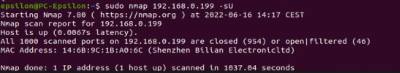
$sudo nmap <target IP> -sT TCP connect port scan (Default without root privilege) $sudo nmap <target IP> -sU UDP port scan
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
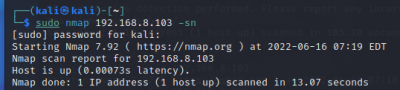
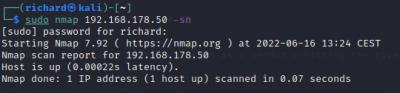
Host discovery and port scan:
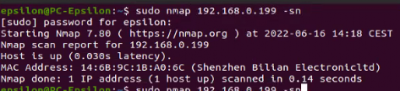
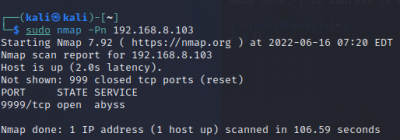
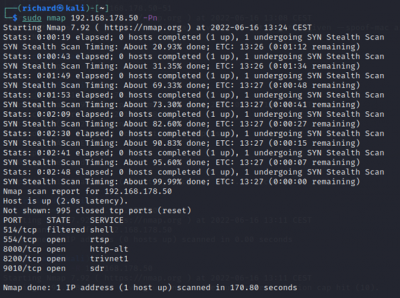
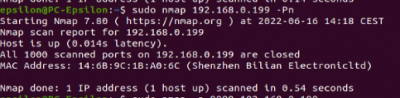
$sudo nmap <target IP> -sn Disable port scanning. Host discovery only $sudo nmap <target IP> -Pn Disable host discovery. Port scan only (If the host is down)
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
Port Specification:
$sudo nmap <target IP> -p- Scan all ports
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
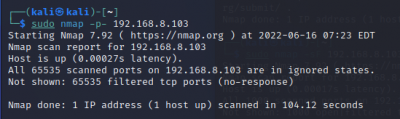 |
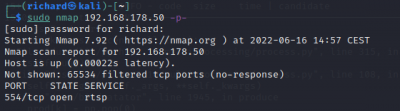 |
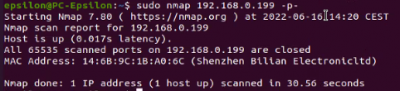
|
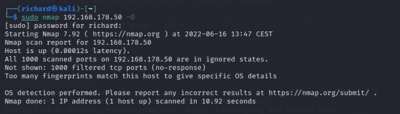
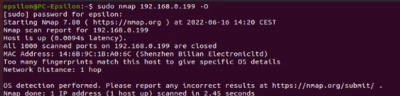
OS Detection:
$sudo nmap <target IP> -O Remote OS detection using TCP/IP
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
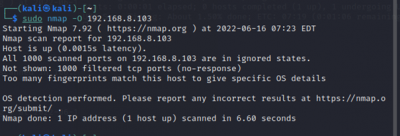 |
 |
|
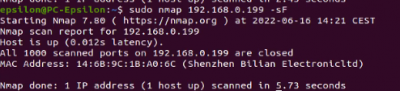
FIN-scan:
$sudo nmap <target IP> -sF Scanner sends FIN segments
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
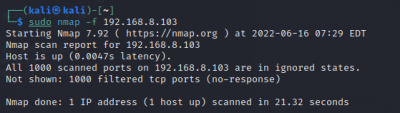
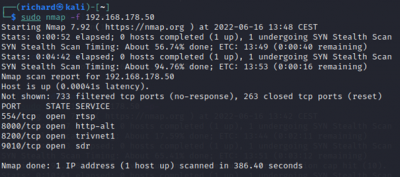
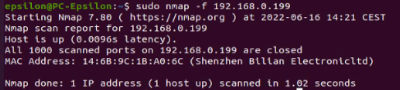
Firewall Evasion Technique:
$sudo nmap -f <target IP> augment packets
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
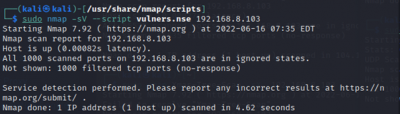
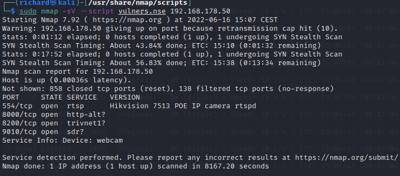
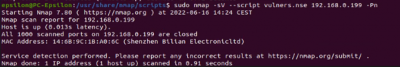
Use a set of scripts from the /usr/share/nmap/scripts/ directory:
$sudo nmap -sV --script $SCRIPT <target IP>
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
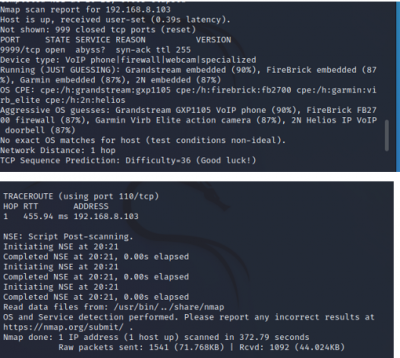
Aggressive Scan:
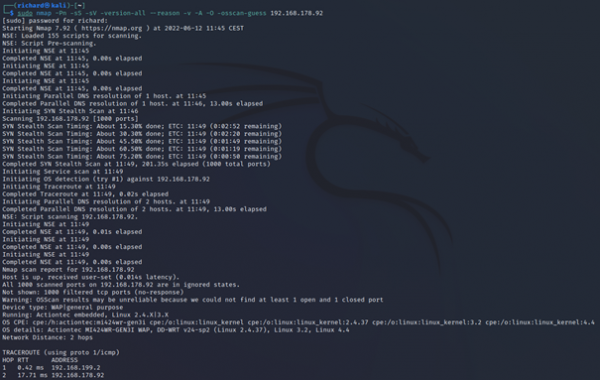
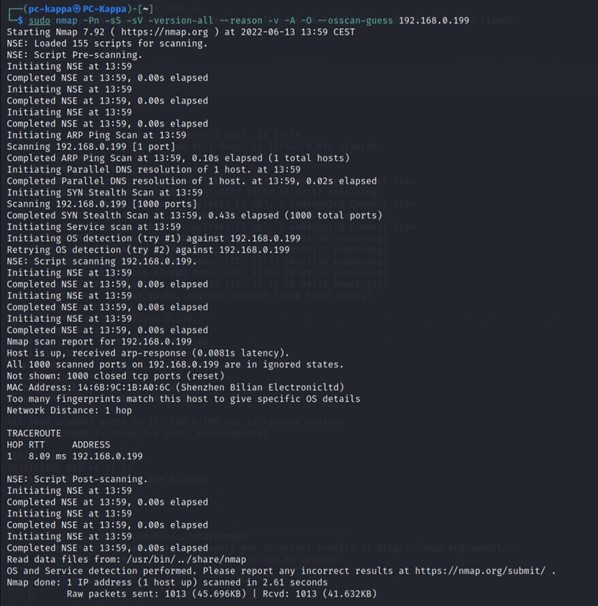
$sudo nmap -Pn -sS -sV -version-all --reason -v -A -O --osscan-guess <target IP>
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
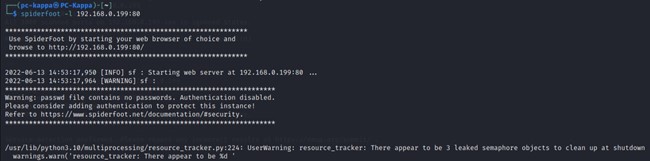
Spiderfoot
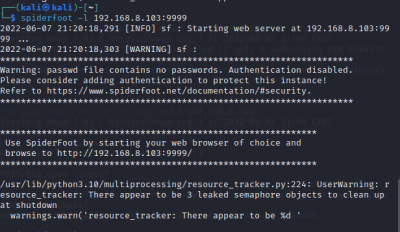
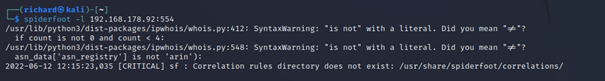
Spiderfoot uses various modules to collect information and it can collect information about the target host through the scanning options available in the Spiderfoot Framework.
$spiderfoot -l <target IP>:<target Port>
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
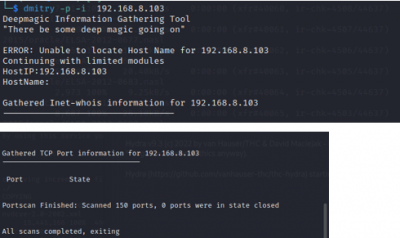
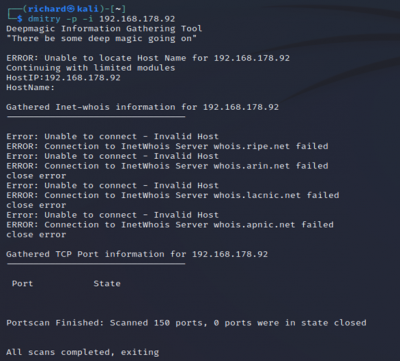
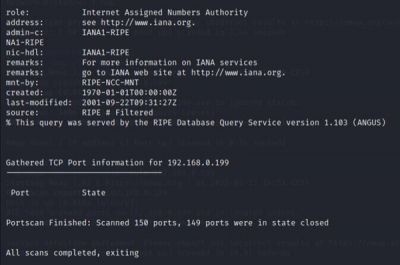
Dmitry
Dmitry Tool can be used to search subdomains of the target, find open ports of the target system, perform TCP scan, find operating system information, web server details, web host details, hosting service details, registered domain, name, address, the contact information of the person who registered it, find email addresses that are associated with the domain of the target.
$dimitry -p -l <target IP>
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
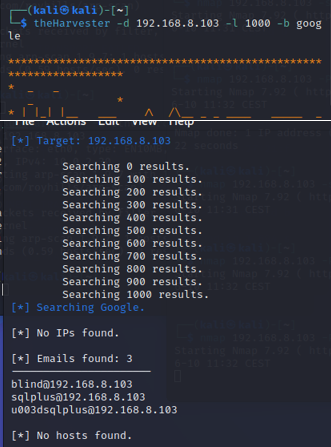
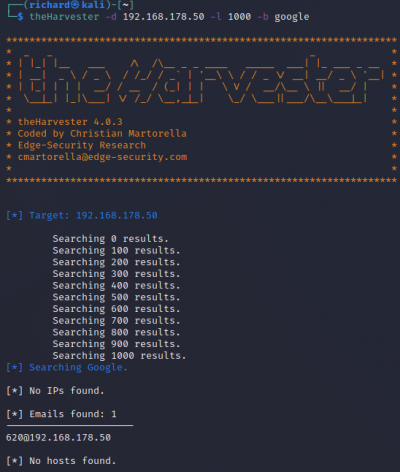
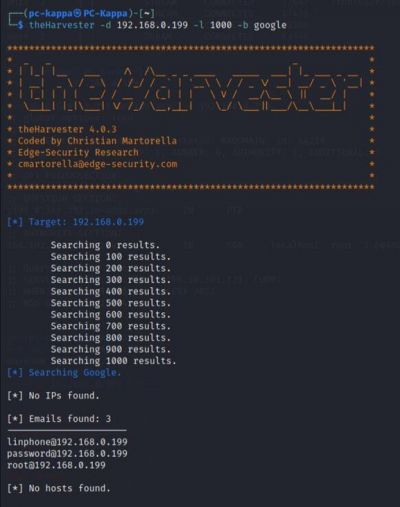
The Harvester
With the Harvester, you can gather information like emails, subdomains, hosts, employee names, open ports, and banners from different public sources like search engines, PGP key servers, and SHODAN computer database.
$theHarvester -d <target IP> -l 1000 -b google
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
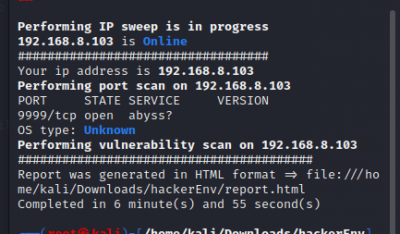
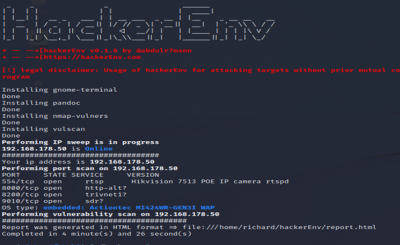
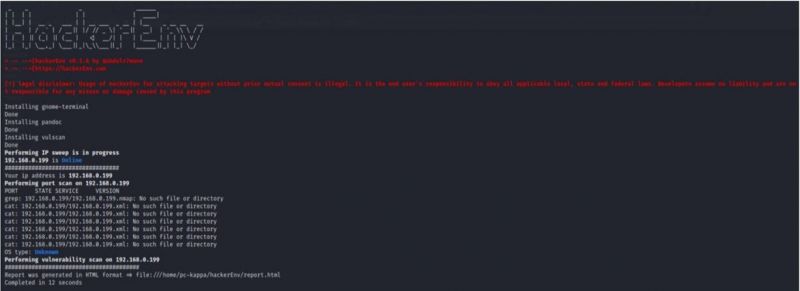
HackerEnv
HackerEnv is an automated tool developed in the Bash language that quickly performs port scans, scans target IP addresses for vulnerabilities, and retrieves exploits to form the Searchsploit utility.
$git clone https://github.com/abdulr7mann/hackerEnv.git $cd hackerEnv $chmod +x hackerEnv $bash hackerEnv -t <target IP>
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
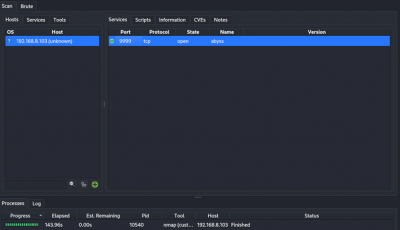
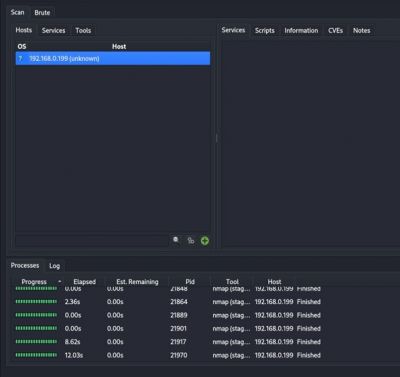
Legion
Legion works with a GUI which can perform automatic recon and scanning with NMAP, whataweb, nikto, Vulners, Hydra, SMBenum, dirbuster, sslyzer, webslayer, and more (with almost 100 auto-scheduled scripts). It is already installed on Kali Linux 2022.2.
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
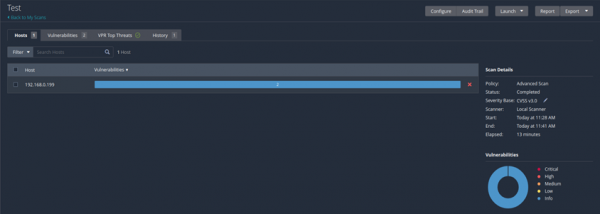
Nessus
Nessus is a special software, so-called vulnerability scanner, that inspects systems for security gaps and vulnerabilities. It can be used to identify local and remote vulnerabilities, to audit configuration and compliance, verify default credentials, and scan web applications.
$sudo dpkg -i <Nessus deb file> $/bin/systemctl start nessusd.service go to https://kali:8834/ to configure the scanner
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
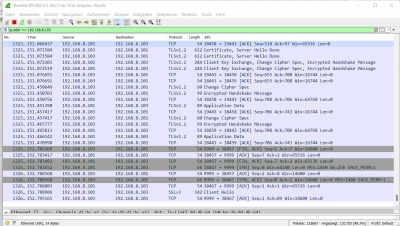
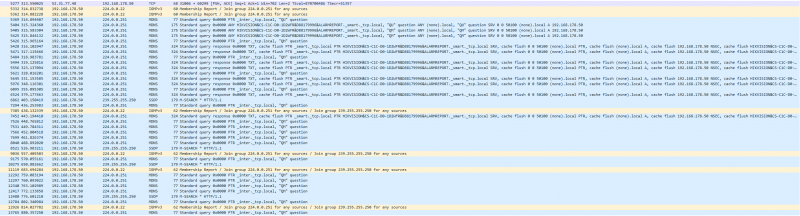
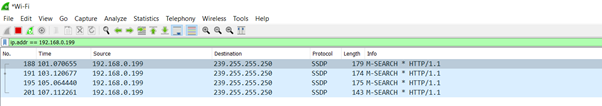
Wireshark
Wireshark is a protocol analyzer. It is an essential tool for safety experts or gadget administrators. It is used to investigate the shape of various community protocols and has the ability to illustrate applications.
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
 |
 |
|
Exploitation Tools
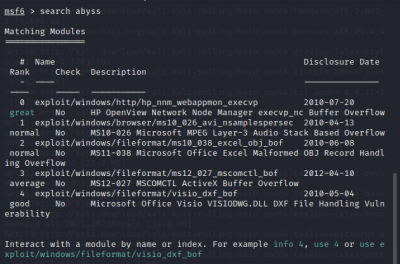
Metasploit
Test your camera for security gaps with the help of the framework provided by Metasploit.
You can use the various exploits collected by the framework to perform various security and penetration tests on your distributed target system.
The attack method (exploit) and the executed code (payload) are separated.
Exploits need to be specially tuned for various security gaps in software and hardware.
This code is used when the attack method is successful and can break into or compromise the system.
msf6 > search <open port protocol> Search for exploits of open ports
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C |
|---|---|
 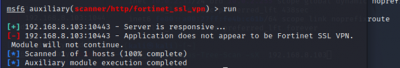 |

|
Searchsploit
The SearchSploit utility is a local copy of the Exploit Database and it searches this database to find exploits for various software and services found during the penetration testing phase. You can also use this utility to inspect an exploit and make a copy that you can modify for use on a particular host.
$searchsploit <open port protocol> Search for exploits of open ports
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C |
|---|---|
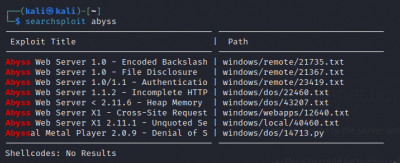 |
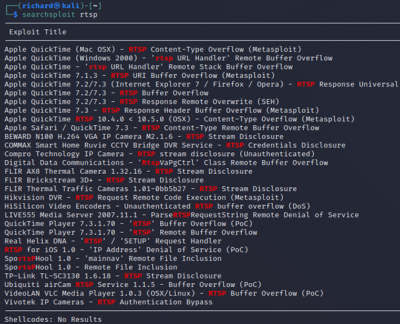
|
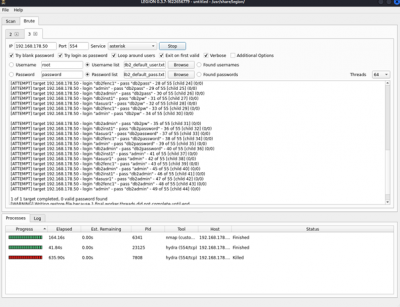
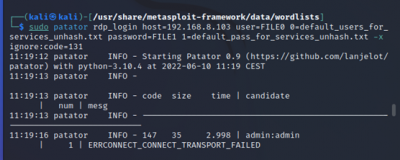
Hydra and Patator
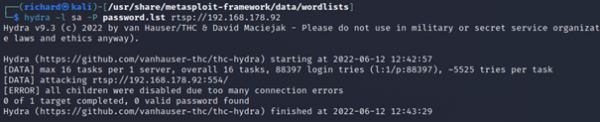
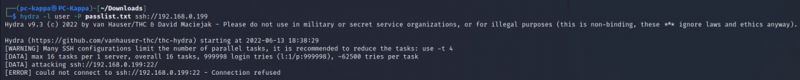
Hydra and Patator are login crackers that support numerous attack protocols. These tools make it possible for researchers and security consultants to show how easy it would be to gain unauthorized access to a system remotely. They are used to brute-force usernames and passwords to different services such as ftp, ssh, telnet, MS-SQL, etc.
You can access the wordlist in a directory by using the below command.
$cd /usr/share/wordlists
$hydra <Target_IP> ssh -l <username> -P <password_file> -s 22 -vV to brute-force SSH username and password $hydra -L <username_file> -P <password_file> ftp://<Target_IP> to brute-force FTP username and password $hydra -l <username> -p <password> telnet://<Target_IP> to brute-force Telnet username and password
| TP-link Kasa Cam Smart Home Camera KC120 | Ezviz CS-C1C | Abus PPIC32020 |
|---|---|---|
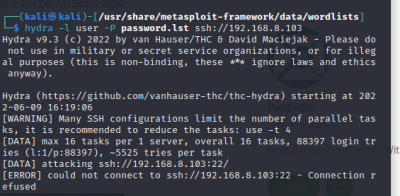 |
 |
|
$patator rdp_login host=<target IP> user=FILE0 0=<username_file> password=FILE1 1=<password_file> -x ignore:code=131
| TP-link Kasa Cam Smart Home Camera KC120 |
|---|
|
Report
All three cameras have motion and audio detection capabilities, and the app will notify you when motion is detected. Live video is also possible. TP-Link saves the data for user registration and communication with external cloud services from Amazon Web Services, Inc. (410 Terry Avenue North, Seattle WA 98109, United States; "AWS"), and Evziz uses its own Evziz Cloud. Unlike Abus and Evziz, you cannot store data on a MicroSD card on the kasa cam. All bits of the video are protected by industry-standard 128-bit AES encryption using SSL / TLS. EZVIZ Cloud provides a dual encryption solution that covers both server-side and client-side encryption, so data transmission between the device and the cloud is encrypted end-to-end. It also advises users to make sure that the data is stored on the physical device in encrypted form. This reduces the risks associated with unauthorized access of data to physical devices. All cameras use the WiFi connection protocol which supports WEP and WPA / WPA2 encryption.
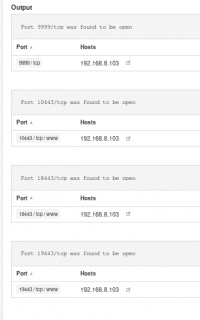
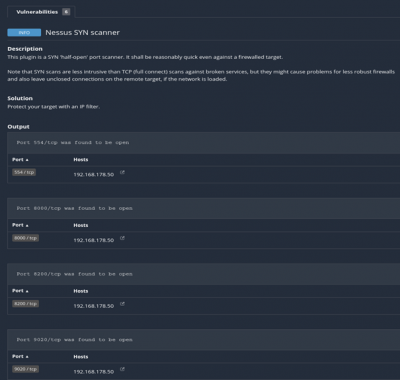
The scan tools has detected four open ports on TP-Link's with the service abyss and cirrossp. The Evziz camera had four open ports running RTSP, http-alt, trivnet1, and sdr services.
The Abus camera had no open ports, only the MAC address was displayed.
TP-Link uses TCP as traceroute, Evziz uses ICMP and Abus uses broadcast.
The final Nmap scan on Kasa Cam showed that the device type is a webcam. Nmap is guessing that the Garmin Embedded is running on the camera. The OS CPE is cpe:/h:/garmin:virb_elite and it has to be a Garmin Virb Elite action camera. Using Evziz Cam, Nmap thinks that the operating system Linux is probably running on the camera.
The exploit tools did not detect abyss and cirrossp exploits. The RTSP protocol on the Evziz camera had several exploits, but none of them has led to remote access. The login crackers could not infer login data. Based on these results, we would advise our client not to take new security measures.
Used Hardware
References
- https://wiki.owasp.org/index.php/Main_Page
- https://tools.kali.org/tools-listing
- https://nmap.org/
- https://www.spiderfoot.net/
- https://www.kali.org/tools/dmitry/
- https://github.com/laramies/theHarvester
- https://github.com/abdulr7mann/hackerEnv
- https://govanguard.com/legion/
- https://www.tenable.com/downloads/nessus?loginAttempted=true
- https://www.kali.org/tools/wireshark/
- https://www.metasploit.com/
- https://www.speedguide.net/ports.php
- https://www.exploit-db.com/
- https://github.com/vanhauser-thc/thc-hydra
- https://github.com/lanjelot/patator