KNOB Attack
Summary
The attack was found 2019 by Daniele Antonioli, Nils Ole Tippenhauer and Kasper B. Rasmussen. Bluetooth specification has an encryption key negotiation protocol to negotiate encryption keys. Attackers can manipulate this protocol to force encryption keys with 1 Byte of entropy without protecting the integrity of the negotiation process. This enables brute forcing the encryption keys in real time.
Key negotiation protocol
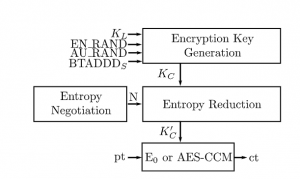
The goal of this protocol is to compute a session key starting from a long term shared secret At the top is Encryption Key Generation Function that takes as input the longterm secret a bunch of nonces and Bluetooth address of Slave and is computing Kc a key with 16 Bytes of entropy this key is not used as session key it is processed by an entropy reduction function that is used to modify the entropy to N bytes and this N number is computed from an entropy negotiation phase that is performed by alice and bob. This session key is used to encrypt and decrypt the packets using E0 stream cipher in case using legacy security mode or AES-CCM if both devices supporting Bluetooth secure connections.
Stages of Attack
KNOB Attack has 4 Main stages
- First stage: Alice and Bob (Victims) are pairing using the strongest security mechanisms Secure Simple pairing. They are establishing a long term secret and the attacker is not there.
- Second Phase: Alice and Bob wants to establish a new encrypted session and Charlie(Attacker) is in Bluetooth range with the victim.
- Phase 3: Charlie is able to manipulate the entropy negotiation phase of Bluetooth and let the two victim negotiate an encryption key with one byte of entropy.
- Phase 4: Charlie is able to eavesdropping ciphertext and using the ciphertext to bruteforce the encryption key and the brute force is in real time because If you use an encryption key with 1 Byte of entropy then you have to brute force one key out of 256 possibilities.
Requirements
- Clone Github https://github.com/francozappa/knob
- Rooted Nexus 5 running the internalblue/android_bluetooth_stack/nexus5_android6_0_1/bluetooth.default.so custom Android Bluetooth stack
- Computer running Linux operating system
- Wireshark
Internalblue is a framework which can patch the firmware from the operating system. This attack is simulating an attacker using Internalblue, because the setup is easier, has a higher reliability, and it is cheaper than over the air.
Perform Attack
- Connect Nexus 5 via USB to the computer
- Configure and install modified internalblue v0.1
- Edit internalblue/internalblue/core.py and set NEXUS5_MODE to which mode you want to perform
- Set NEXUS5_MODE = MASTER_MITM then the Nexus 5 is the master device or NEXUS5_MODE = SLAVE_MITM to set Nexus 5 to the slave device
- In terminal, switch into the internalblue directory, and run sudo python2 setup.py install
- Open a terminal and run internalblue (Internalblue is inserted in PATH Variable)
- In the internalblue menu start LMP monitoring with monitor lmp start
- A Wireshark window should pop up
- Pair target with Nexus 5
- When Nexus 5 is as the master configured (NEXUS5_MODE = MASTER_MITM) then you have to start the connection from the Nexus 5 to the target device.
- When the Nexus 5 is as the slave configured (NEXUS5_MODE = SLAVE_MITM) then you have to start the connection from the victim to the Nexus 5.
- In Wireshark you can see that the devices have negotiated an encryption key with 1 byte of entropy.
Countermeasures
- Force minimum and maximum amount of entropy that cannot be easily brute forced.
- Encryption keys with a fixed number of entropy.