PDF Forensic with MPeePDF
Summary
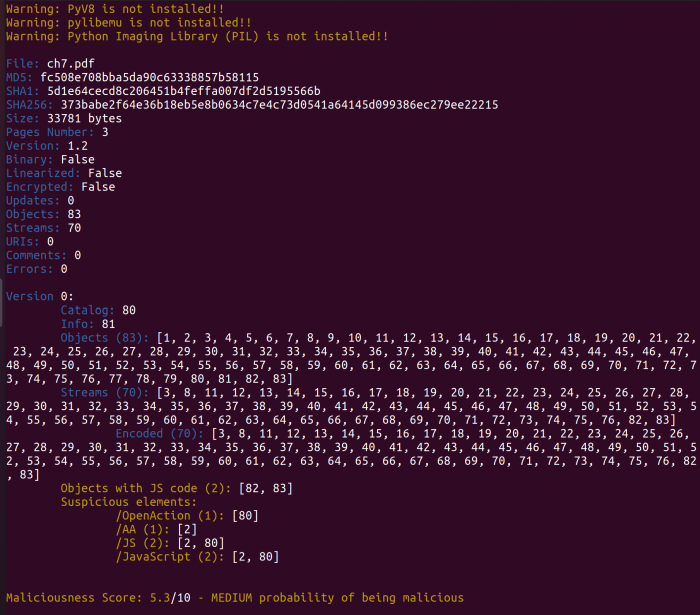
This documentations goal is to illustrate the use of the tool MPeePDF which can be used to do PDF forensic work. The goal of PDF forensic is to analyse documents and determine if a malicious activity is conducted.
Requirements
- Operating system: Ubuntu 20.04
- Packages: git, python2
In order to complete these steps, you must have followed python2 install guide before.
Description
Step 1
Enter these commands in the shell to start an analysis of a document.
python2 mpeepdf.py [your.pdf]
This will scan the document and output general information about the document and their contents. You can also go into the console to execute further commands. Just add the -i parameter.
python2 mpeepdf.py -i [your.pdf]
Step 2
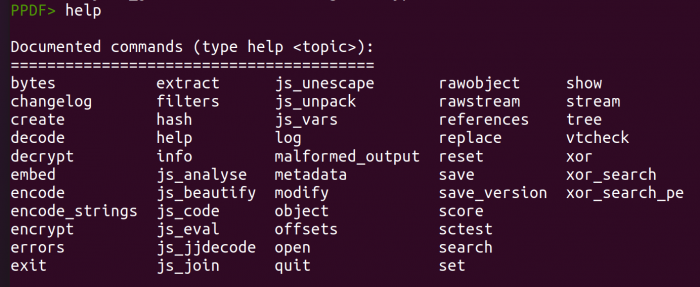
While inside the console, you can look up more things like metadata, specific information about streams and objects and much more. To see all available command type in help into the console.
Step 3
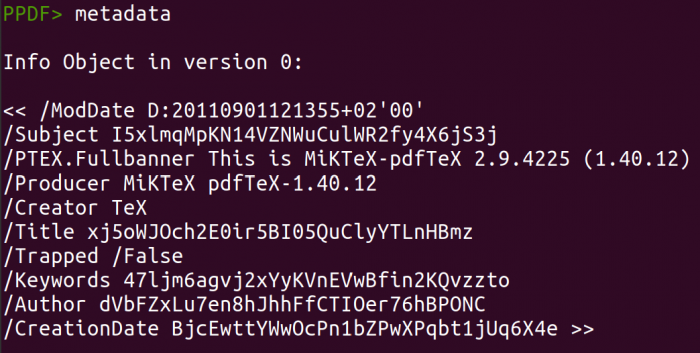
Inside the console are many options to analyse your document. You can start by looking at the metadata of the file by typing in:
metadata
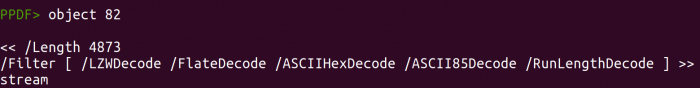
If you want to look at specific objects or stream type in:
object [1] stream [1]
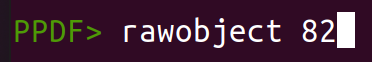
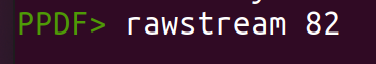
The raw data of the respective object/stream can also be seen with:
rawobject [1] rawstream [1]
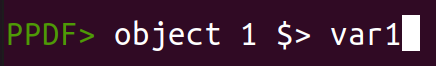
You can also store a object or stream in an variable with following command:
object [1] $> var1
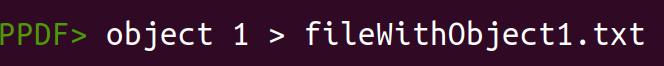
An export to a file is also possible with:
object [1] > object1.txt