PandwaRF
Description
PandwaRF is a family of pocket-sized, portable RF analysis tools operating the sub-1 GHz range produced by the Comthings, a French startup focused on the PandwaRF analysis tool and custom RF penetration testing tools for professionals and law enforcement agencies. [1] analysis and re-transmission of RF via an Android device or a Linux PC.
It can be connected to an Android smartphone using BLE or USB, and to Linux using USB. It is based on the well-known RfCat and Yard Stick One tools with the Texas Instruments CC1111 RF transceiver [2], but with a lot of new features, making PandwaRF the perfect portable RF analysis tool. Practically, it removes the ‘standard SDR Grind’ of capturing, demodulating, analyzing, modifying and replaying by hand – replacing it with a simple but powerful interface.
The PandwaRF system consists of two elements: the hardware device and the software controller, either an Android device or a PC. The hardware is a very capable device, tailored for beginners and advanced users alike. Beyond the functionality provided by the Android interface, the PandwaRF can be easily controlled and customized. No need to risk bricking your device or writing in C, the PandwaRF can be controlled by JavaScript, directly on the smartphone. The Rogue Pro was designed for advanced users like pentesters or security professionals and it is specialized on brute forcing wireless devices in order to test their security.
General Overview
PandwaRF is a Radio Frequency hacking tool used to:[3]
Receive
Transmit
Analyze
Technical Overview
PandwaRF is composed of 2 elements:
PandwaRF HW dongle
The PandwaRF Rogue Pro dongle contains[4]:
Possible applications
Hardware Antennas
In its antenna pack version, PandwaRF is shipped with 3 miniature SMA antennas (315/433/868-915 MHz).
Using the proper antenna is critical to have good RF performance. Antennas are labelled with the first digit of their frequency band:
Warning
PandwaRF is a test equipment for RF systems. It has not been tested for compliance with the regulations governing the transmission of radio signals. You are responsible for using your PandwaRF legally. The intentional jamming of RF signals is ILLEGAL. PandwaRF should only be used for testing the robustness of your own devices.
Mobile App
PandwaRF offers a smartphone app to provide many tools for analysing RF signals:
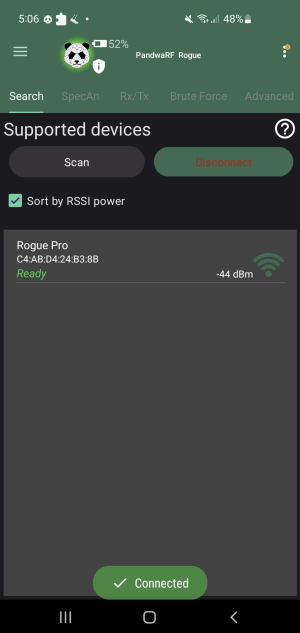
Pairing
In order to use the PandwaRF, the device has to be connected to the mobile device via Bluetooth.
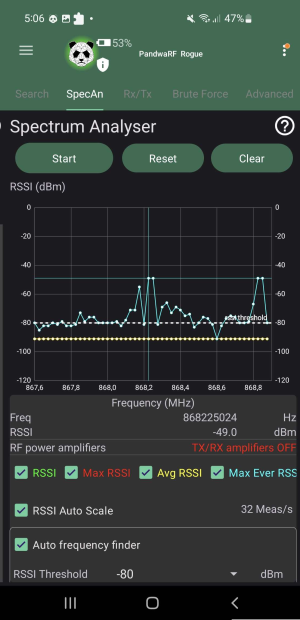
Spectrum Analyser
The spectrum analyser helps measuring the frequency at which a device's signal is exactly operating at. It is also possible to discern the modulation, distortion, noise and bandwidth.
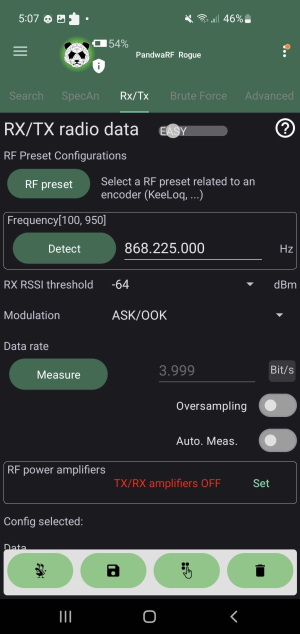
Rx/Tx Data Transmission
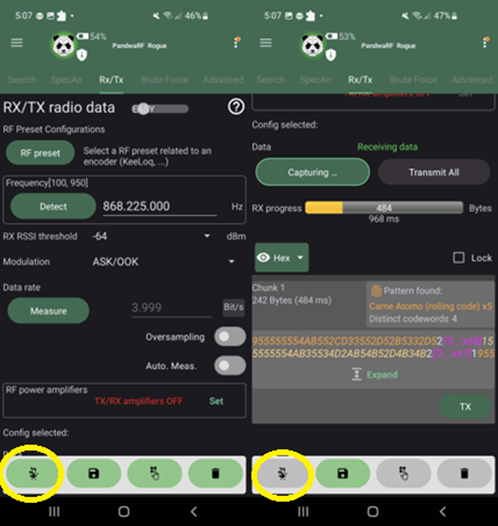
This tab is for capturing or transmitting the data of the device to be intercepted. It has two different modes: a beginner-friendly easy mode and hard mode designed for radio experts in order to fine-tune the eavesdropping. The easy mode needs three inputs: Device frequency operation, modulation type, and lastly the data rate.
The operating frequency can be either manually or automatically filled in by the results of the spectrum analyser. The next parameter is the modulation type and it is usually in the device's technical manual. Last but not least, the data rate can be filled in manually or have the rate measured by sending an RF signal.
Once set, the user can start the capture of the transmission and eavesdrop on the message. After having received data it will show in the mobile app as a hex or binary stream.
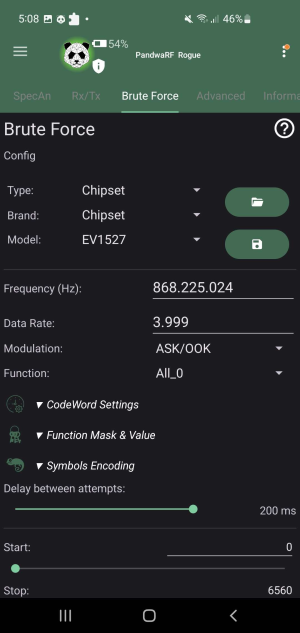
Brute Force
Another tool the app provides is the brute forcing code words on RF devices. With this feature the user can send multiple RF codes to the receiver after having configured the baselines for the code word. In order to start brute-forcing the code word and set-up the analysis tool, the user must gain insight on missing information first such as the RF parameters, codeword settings, etc [6].
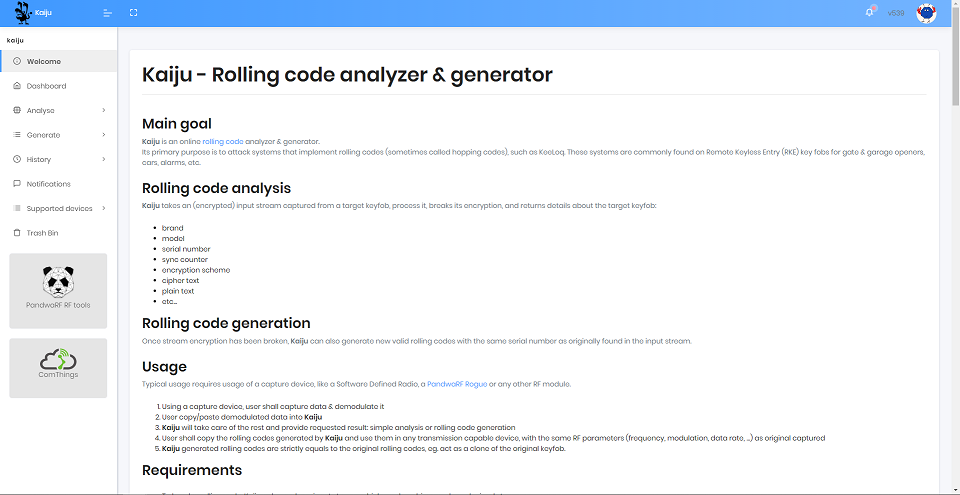
Kaiju
Kaiju is an online rolling code analyser and generator. It uses the captured payload of the RF signal, processes it, tries to break its encryption on a remote server by ComThings and returns several information including metadata about the victim such as [7]:
Rolling Code
One of the commonly used techniques when trying to securely gain access on vehicles or garage door openers is a rolling code implementation. This is also known as hopping code. It is an authentication scheme in order for the user to be able to remotely open up their car as an example. Therefore, no physical key is needed for systems using this technique but rather remote keys in the form of remote controls e.g. car key fobs.
In general, this protocol operates on generating a code and having it validated by the receiving device. The transmitter and receiver using this protocol must, however, be synchronised first. The generation of this code happens on the sender side and must be unique. The uniqueness can be guaranteed by having the sender device hold an internal counter and increment it on every code generation. Every time the user presses the button on their transmission device, it will create a new code. That remote has a unique identifier (UID), which the receiver knows since the first step is to synchronise both devices. The message can be validated by the receiving end as it contains the UID of the remote control. Once accepted, the receiver marks the newly generated code to its list and increments its own counter [8].
A good visualization can be found at https://harryli0088.github.io/rolling-code/
License required
However, to enable the rolling code generation against devices such as garage door openers, a Kaiju license has to be bought from the PandwaRF shop. Once bought, it has to be bound to a Kaiju account and the MAC address of a PandwaRF device. This association cannot be changed unless a request ticket is made to the support e-mail of the PandwaRF team [9].
Example: Rolling Code Attack
The following section presents an attempt to hack a garage door opener - the Chamberlain ML700EV Comfort [10] - with the help of the PandwaRF Rogue Pro. This device consists of a motor, several metal rails for the garage door and two remote controls to operate it. The motor acts as a receiver. The minimal required set-up for the opener to work is to plug in the motor and the remote control can send RF signals to open and close the gate by pressing a button.
Step 1: Setup RF Parameters
In the first step it is important to know what RF parameters the device operates in. The RF parameters needed to capture in PandwaRF are the following:
For the RF connectivity on the PandwaRF, it can connect two different antennas to its board. One is in the area of 433 MHz while the other operates on around 868 MHz. To find out the operating frequency of the device, there are multiple ways to figure it out. The simplest way to find out the frequency is to look at the vendor's shopping page and the product's technical details. Browsing the manual provided by the packaging is an alternative. Lastly, if the device has an Federal Communications Commission (FCC) ID [11], it is possible to search for the necessary data online. The operating frequency has been found inside the manual and it can operate on both the 433 MHz and the 868 MHz bands. For this example the antenna with the 868 MHz has been screwed in the PandwaRF. In order to start hacking, the data needs to be recorded and sent to Kaiju. The capturing of the data can be started in the Rx/Tx tab and have the capture displayed as either a binary or a hex data stream. Before we can start eavesdropping, the two remaining RF parameters (modulation and data rate) have to be found out. The data rate can be simply measured from the current tab whilst the modulation has to be figured out via trial and error.
Step 2: Capturing the Data
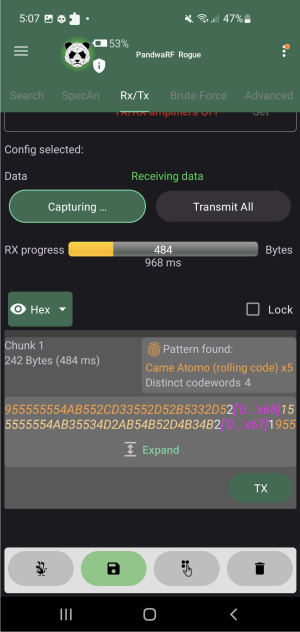
The eavesdrop can now start by initiating the capture in the app and then sending an RF signal from the remote control.
The RF parameters are as follows:
Step 3: Send to Kaiju
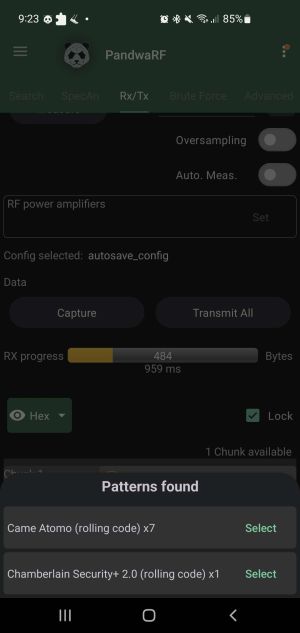
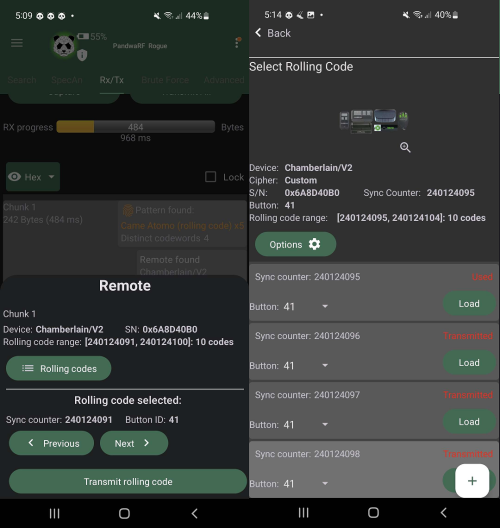
After a successful interception, the payload has already been evaluated and it is shown that the captured signal has a pattern that resembles a rolling code implementation. To have Kaiju correctly break through the encryption it is required to change the found Pattern to the Chamberlain Security+ 2.0 (rolling code).
The button on the bottom left will send the selected payload to Kaiju and will automatically generate 10 new rolling codes to use.
Step 4: Use Rolling Codes
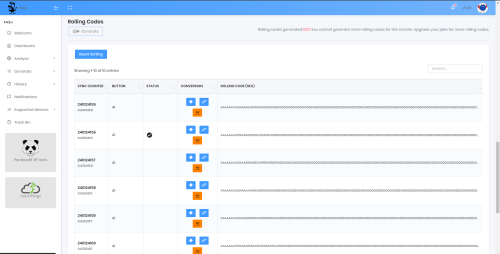
The payload is sent to the Kaiju servers and they process the data and try to break the encryption. The process behind how it attempt to break it is not stated on the Kaiju website. It cracks the input stream and returns a positive result. The signal has been figured out. Kaiju will automatically generate ten new rolling codes for each payload that was sent to it to be analysed. It is now possible to send these codes from the mobile app to the PandwaRF. The analysis tool will act as an impostor remote control and trigger an action from the actuator.
Evaluation on the Kaiju Website
Example: Simple Replay Attack on a Smart Plug
This section demonstrates a Simple Replay Attack on a smart plug with fixed codes, emphasizing the detection of "6 known codes" for brute force testing.
Step 1: Setup RF Parameters
The smart plug operates on the 433 MHz frequency band, which is commonly used for simple RF devices. Using the Spectrum Analyzer, the frequency and parameters were identified:
The 433 MHz antenna was connected to the PandwaRF for signal interception.
Step 2: Capturing the Data
The signal from the smart plug's remote control was captured using the Rx/Tx mode. The data was displayed in binary and hexadecimal formats.
6 Fixed Codes Detected:
The PandwaRF app successfully identified 6 fixed codes matching the signal's pattern. These codes are used in fixed-code systems, making them vulnerable to replay attacks.
Step 3: Replay the Signal
The captured fixed code was replayed using the Tx mode in the PandwaRF app. The smart plug responded to the replayed signal, successfully switching on and off.
Outcome: The smart plug was turned on and off using the replayed signal.
Step 4: Evaluation of Vulnerability
The replay attack highlights the weaknesses in systems using fixed codes:
Solution: Implementing Rolling Codes or encryption would prevent such replay attacks.
Conclusion
The PandwaRF Rogue Pro successfully demonstrated two types of attacks:
These experiments emphasize the need for stronger security measures in RF-based systems, such as rolling codes, AES encryption, or frequency hopping techniques.
Hardware
References
- ↑ Tania. Home: https://www.comthings.com/
- ↑ Texas Instruments. instruments guide, https://www.ti.com/product/CC1110-CC1111 , 2013.
- ↑ https://www.comthings.com/
- ↑ https://pandwarf.com/pandwarf-rogue-pro/
- ↑ https://github.com/ComThings/PandwaRF/wiki
- ↑ https://github.com/ComThings/PandwaRF/wiki
- ↑ https://rolling.pandwarf.com
- ↑ https://ieeexplore.ieee.org/document/9851991
- ↑ https://pandwarf.com/product/kaiju-gate-openers-pack-pro-license/
- ↑ https://wiki.elvis.science/index.php?title=Chamberlain_Garage_Motor_ML700EV
- ↑ https://www.fcc.gov/oet/ea/fccid