Penetration Testing Tools in Kali Linux
Summary
The security of information and network systems has been gaining relevance for businesses and organizations as well as for public and private facilities. With the increased electronic storage of information on company networks, security must be improved and guaranteed by each organization to protect sensitive data and company secrets. A very effective method to verify the security of a system is to use Penetration Testing, which is also called Pen Testing or ethical hacking. A Pen Test helps to analyze a system to check and verify its security. The main objective is to find the system's vulnerabilities and weaknesses. There are plenty of tools and platforms for Penetration Testing, one specific platform being Kali Linux, which has its own integrated tools for testing, as well as additional tools that can be installed to it.
This tutorial is based on the seminar paper File:Penetration Testing Tools - Kali Linux.pdf and serves as an introduction of the Kali Linux platform.
Requirements
- Host Operating system: Windows 10 Home 64-Bit
- Guest Operating System: VMware® Workstation 14 Pro (Version 14.1.1)
- Server for Penetration Tests: Kali Linux for VMware 64.Bit
- Vulnerable Server for Demonstration Purposes: Metasploitable 2
Penetration Testing
Penetration Testing is a practice to find weaknesses of a system by precisely analyzing all components of a system for vulnerabilities. It simulates an attack on the system using testing tools and software. The main goal is to demonstrate how long it would take an attacker to get access to a system network and helps to determine the dangers of an unauthorized attack on a system. Therefore, countermeasures can be taken beforehand, and data confidentiality and integrity of a system can be ensured.
Framework
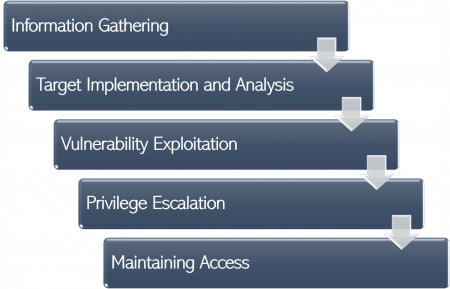
In order to successfully perform a Penetration Test, the formalization and strict compliance of a framework are essential. There are various versions and interpretations of such frameworks for Penetration Tests. However, apart from slight differences, the main steps of these frameworks remain the same, whereas the success of each step is crucial for the outcome of the next one. The following framework represents one version of a Penetration Testing framework, with a more detailed description being given in the attached seminar paper:
- 1. Information Gathering (Reconnaissance)
- The first step of the framework defines the collection of information about a target system and its environment, such as the internal structure, IP addresses, and used ports.
- 2. Target Implementation and Analysis
- At this step, the target system is scanned for vulnerabilities based on the information gathered in the first step of the framework. Also, the outcomes of the scan are properly documented.
- 3. Vulnerability Exploitation
- In the third step, the vulnerabilities of the target system that were found after the system scan in the second step are exploited to identify their level of security and to see how much information can be acquired from the target system network.
- 4. Privilege Escalation
- In order to finish an assignment, a Pen Tester might need to gain additional, unauthorized access to the target system. Thus, the tester might escalate privileges including password cracking and obtaining login credentials.
- 5. Maintaining Access
- Lastly, a Pen Tester must conceal any proof of the conducted penetration and establish backdoors to maintain access to the target system.
Setup of the Test Environment
For demonstration purposes of Penetration Testing, Kali Linux and the Metasploitable 2 server are used. This section includes a brief description of each server and shows a proper installation and configuration of the test environment.
Kali Linux
Kali Linux is a Linux distribution platform based on Debian Linux and is used for Penetration Testing and analysis of a target system. It is the successor to the platform BackTrack and was developed by Offensive Security in 2013. The Kali Linux platform includes over 600 tools for ethical hacking, therefore being one of the most used platforms for Penetration Tests. These tools are grouped in 13 categories, which range from tools for gathering information, password cracking, stress testing a network, and exploiting vulnerabilities. The following table shows some of the most well-known tools that are provided on the Kali Linux platform.
| Tool | Description |
|---|---|
| Nmap | Network scanner for network analysis |
| Burpsuite | Tool for testing the security of web applications |
| SQLMap | Software to identify and exploit the vulnerabilities of databases |
| John the Ripper | Password cracking tool |
| Aircrack-ng | Suite of tools to analyze and exploit weaknesses of WiFi networks |
| THC-Hydra | Tool for password cracking via brute force |
| Bettercap | Tool used for performing Man-in-the-Middle attacks by manipulating the network manipulation |
| Wireshark | Tool for capturing and analyzing packets |
Download, Installation and Configuration:
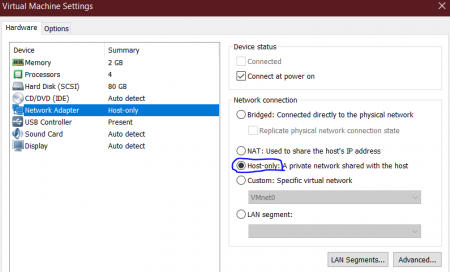
Download the Kali Linux image for VMware from the homepage and unzip the downloaded directory. Load the file
Kali-Linux-2019.4-vmware-amd64.vmx to VMWare and change the network adapter settings to allow network
connections only to and from the host machine. Therefore, go to the image on the VMware, select
Edit virtual machine settings → Network Adapter while the machine is still powered off, and change the settings from
NAT to Host-only. Then, confirm with OK and start the Kali Linux machine.
Afterward, log in with the following credentials, that are included in the file vmware.log:
Username: root Password: toor
Open the terminal on Kali Linux and input the following commands to update and synchronize the system:
apt-get update apt-get upgrade
Metasploitable 2
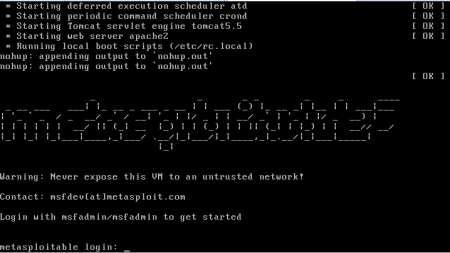
To legally perform Penetration Testing and to illustrate proper methods and results, a vulnerable server is needed as a target server on the virtual machine. For this purpose, the Metasploitable 2 server is used. Metasploitable 2 is an intentionally vulnerable version of an Ubuntu Linux machine and was developed by Rapid7. It was designed for testing purposes and is compatible with several environments.
Download, Installation and Configuration:
Metasploitable 2 is available on the Rapid7 website, which also provides documentation for configuring and operating on Metasploitable 2. Select one of the two provided servers to download the needed Metasploitable 2 directory. Then, unzip the directory and open the Metasploitable.vmx file with VMWare. Log in to the server with the following credentials:
Username: msfadmin Password: msfadmin