Port Scanning with Nmap
Summary
Nmap is a free and open source tool for network scanning, created by Gordon Lyon in 1997. The original article in the Phrack Magazine can still be found http://phrack.org/issues/51/11.html#article.
Description
Nmap is a so-called Port Scanner. The idea behind port scanners is to send out network packets to hosts. By analysing the responses information about the hosts can be gathered. This is the main idea behind port scanners. Gordon Lyon compared the process to sticking messages in every mailbox and waiting for the responses to trickle back. In order to test for different behaviours, different packets are sent. For controlling what kind of packets are sent, Nmap offers a wide variety of options.
Synopsis
nmap [Scan Type] [Options] [Target Specification]
The Nmap command has three sections. In the [Scan Type]-section the type of scan is defined. In the [Options]-sections various modifications can be done and in the [Target Specification]-section the targeted hosts are specified.
Scan Type
- -sS (TCP SYN scan)
- -sT (TCP connect scan)
- -sU (UDP scans)
- -sY (SCTP INIT scan)
- -sN; -sF; -sX (TCP NULL, FIN, and Xmas scans)
- -sA (TCP ACK scan)
- -sW (TCP Window scan)
- -sM (TCP Maimon scan)
- –scanflags <FLAGS> (Custom TCP scan)
- -sZ (SCTP COOKIE ECHO scan)
- -sI <zombie host>[:<probeport>] (idle scan)
- -sO (IP protocol scan)
- -b <FTP relay host> (FTP bounce scan)
Options
The Host discovery is a pre-scan to determine which host are active before starting with the actual scan. The following options control the host discovery.
- -sL (List Scan)
- -sn (No port scan)
- -Pn (No ping)
- -PS <port list> (TCP SYN Ping)
- -PA <port list> (TCP ACK Ping)
- -PU <port list> (UDP Ping)
- -PY <port list> (SCTP INIT Ping)
- -PE; -PP; -PM (ICMP Ping Types)
- -PO <protocol list> (IP Protocol Ping)
- –disable-arp-ping (No ARP or ND Ping)
- –traceroute (Trace path to host)
- -n (No DNS resolution)
- -R (DNS resolution for all targets)
- –resolve-all (Scan each resolved address
- –system-dns (Use system DNS resolver)
- –dns-servers <server1>[,<server2>[,...]] (Servers to use for reverse DNS queries)
The following options deal with the port scan
- -p <port ranges> (Only scan specified ports)
- –exclude-ports <port ranges>(Exclude the specified ports from scanning)
- -F (Fast, limited port scan)
- -r (Don’t randomize ports)
- –port-ratio <ratio><decimal number between 0 and 1>
- –top-ports <n>
The following options manage the service, version an OS detection:
- -sV (Version detection)
- –allports (Don’t exclude any ports from version detection)
- –version-intensity <intensity> (Set version scan intensity)
- –version-light (Enable light mode)
- –version-all (Try every single probe)
- –version-trace (Trace version scan activity)
- -O (Enable OS detection)
- –osscan-limit (Limit OS detection to promising targets)
- –osscan-guess; –fuzzy (Guess OS detection results)
- –max-os-tries (Set the maximum number of OS detection tries against a target)
In order to conceal the Nmap scan, the are a few options that deal with firewall and IDS evasion:
- -f (fragment packets); –mtu (using the specified MTU)
- -D <decoy1>[,<decoy2>][,ME][,...] (Cloak a scan with decoys)
- -S <IP_Address> (Spoof source address)
- -e <interface> (Use specified interface)
- –source-port<portnumber>;-g<portnumber>(Spoof source port number)
- –data <hex string> (Append custom binary data to sent packets)
- –data-string <string> (Append custom string to sent packets)
- –data-length <number> (Append random data to sent packets)
- –ip-options<S|R[route]|L[route]|T|U...>;–ip-options<hexstring> (Send packets with specified ip options)
- –ttl <value> (Set IP time-to-live field)
- –randomize-hosts (Randomize target host order)
- –spoof-mac <MAC address, prefix, or vendor name> (Spoof MAC address)
- –proxies <Comma-separated list of proxy URLs> (Relay TCP connections through a chain of proxies)
- –badsum (Send packets with bogus TCP/UDP checksums)
- –adler32 (Use deprecated Adler32 instead of CRC32C for SCTP checksums)
Target Specification
To describe which hosts should be scanned, Nmap offers multiple variants. The simplest being comma separated IP addresses. For IP ranges there is the CICR notation. For more complex ranges one can modify each octet of the IP address. Octet ranges are formed by a '-' and added together with a ','. One octet might look like this: 0-144,156,255 and as a whole IP address like this: 192.168.0-144,156,255.0-127. To reduce the size of Nmap commands, there is the option to store the hosts in a file and call Nmap with a reference to said file. This might be handy when the same hosts are scanned multiple times.
Installation
Nmap supports installation on many operating systems. The program can either be compiled from source code or installed via an executable installer. The full support can be found here [1].
Windows
For Windows versions including and above 7 there exists an executable installer that can be found on the official Nmap website. After downloading and executing the installer, nmap is ready to use.
Ubuntu
For Debian-based linux distributions Nmap can be installed with apt-get install nmap.
Examples
Scanner: Nmap (7.80) OS: Microsoft Windows 10 Pro (10.0.18363) Additionally: Wireshark (3.2.1)
nmap -sS -p 80,81 45.33.32.156
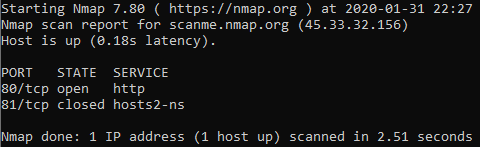
Using this command the host 45.33.32.156 has its ports 80 and 81 via TCP SYN scan scanned. Here TCP packets with a SYN flag are sent. A response with SYN/ACK flags would mean that some application wants to open a TCP connection and therefore the port is active, a response with a RST means that this port is not active. No response or an ICMP-Unreachable means that the port is filtered.
In this case the command produced the following output:
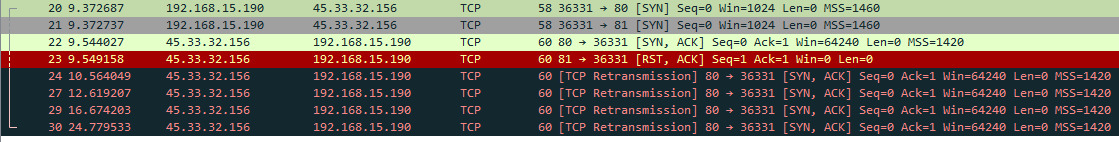
Additionally I captured the scan in Wireshark. Here you can see that two packets (packet 20 & 21) with the SYN flag are sent to the host. From port 80 we receive a SYN/ACK (packet 22) and from port 81 we receive a RST/ACK (packet 23). From this we can deduct that port 80 is active and port 81 is inactive. As Nmap never sent a TCP ACK back on port 80 to open the connection, the host retransmits the SYN/ACK multiple time (packets 24-30). This can be seen in the following image.
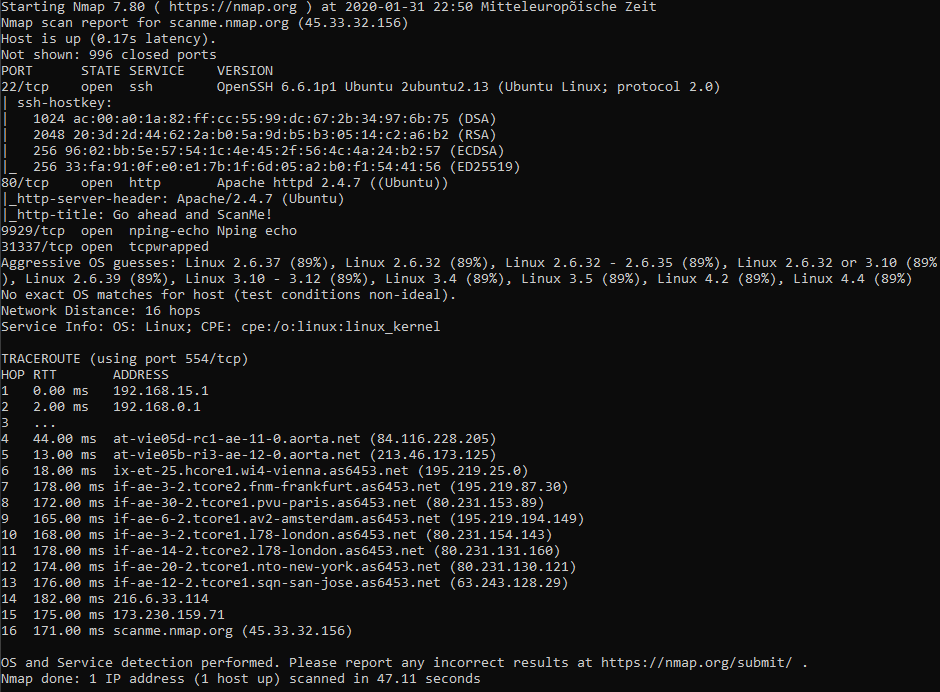
From now on we can use the -Pn option in the Nmap command to skip the host discovery, as we already know that the host is online. Additionally we know that port 80 is active. Now we might want to find out more about the host. Herefore we will use -sV to activate Version detection. The command might look like this: nmap -Pn -A 45.33.32.156 . This activates Service, Version, OS Detection and a few other things. An example output might look like this:
Additional to the open ports, Nmap found out to which service the open port belongs. Furthermore Nmap performed an OS detection. By sending packets with a special payload, Nmap can guess the hosts operating system. The performed traceroute might source some interesting information as well.
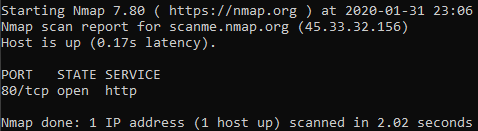
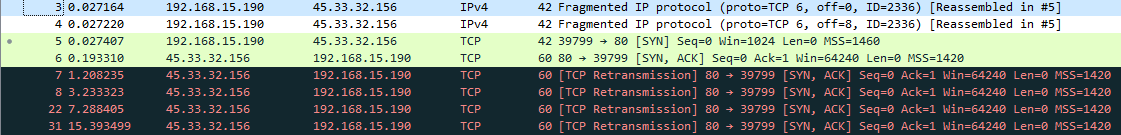
Some options that weren't needed in this case, but might be useful in other cases are the options for evading detection. As an example here the -f option for fragmenting is used. The command: nmap -Pn -p80 -f 45.33.32.156. Here only port 80 is scanned with fragmented packets. The Wireshark output looks as expected
In Wireshark on can see the in this case two packets (packets 3 & 4) with fragmented TCP. Wireshark automatically reassembled the TCP packet (packet 5).
When comparing the contained data in the two packets with the reassembled TCP packet, one can make out a clear similarity.