Practical CSRF example using Burp Suite
Introduction
As the internet is used nowadays for fields like e-commerce, finance and healthcare, web applications need to become more and more secure to prevent attackers from exploiting any vulnerabilities so the user’s credentials can be kept safe. As some vulnerabilities are not as widely known as they should be, although they are rather common, this article deals with one of these vulnerabilities called Cross-Site Request Forgery(CSRF). This is an attack that tricks the end user to execute unwanted actions on a web application, like submitting a malicious request, in which they are authenticated at. In a browser request for most sites the user’s session cookie, IP address and Windows domain credentials, needs to be included. Because of that, it is impossible for the site to distinguish between a forged request of an attacker sent by the victim and a legitimate request of the victim. CSRF attacks target specifically state-changing requests, because the response to the forged request cannot be seen by the attacker. State-changing requests can be transferring funds, changing the e-mail address or password or purchasing items. This article shows how such an attack can be performed on an unsecure webpage by changing the e-mail address of a victim using Burpsuite.[1]
Step-by-Step Practical CSRF example using Burpsuite
Required Software:
Be careful to only start the OWASP Broken Web Application Project using VMNets with "host only" or "NAT" networks due to security reasons, as this application intentionally has a lot of vulnerabilities to explore.
Steps:
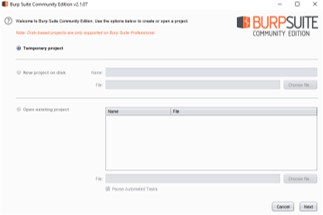
- Start Burp Suite and select "Temporary project"
- To configure the browser (in this case Firefox) to work with Burp Suite one has follow the steps below:
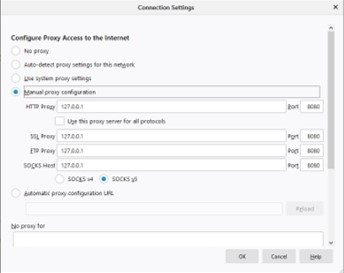
- Menu - Preferences - Options - General - Network Proxy - Settings.
- Select "Manual proxy configuration"
- Fill out the "HTTP Proxy" field with the Burp Proxy Listener address chosen when starting Burp Suite.(default(127.0.0.1))
- Fill out the "Port" field with the Burp Proxy Listener port also chosen before.(default(8080))
- Check the "Use this proxy server for all protocols" box
- Delete if necessary any information in the "No proxy for" field and click "OK"[3]
- To be able to open https-Websites while running Burp Suite, one has to install Burp’s CA Certificate. The steps of how to do that using Firefox can be seen in the following part of this article:
- Enter "http://burp" in your browser and click on the "CA Certificate" Button in the uppermost right corner of the browser to download the certificate
- Remember the download location
- Menu - Preferences - Options - Privacy and Security - Certificates - View Certificates - Authorities - Import
- Select the Burp CA certificate file, that you just downloaded and click "Open"
- Check the box "Trust this CA to identify web sites" when the dialog box pops up and save it by clicking on "OK"
- After restarting Firefox it should be possible to open https-Websites while running Burp Suite[4]
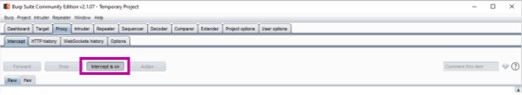
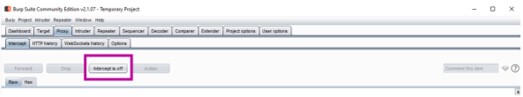
After this initial setup, one has to ensure that in the "Intercept" tab of the "Proxy" tab in Burp Suite "Intercept is off" is chosen.
For anyone using a different browser than Firefox, the following to links will be helpful:
1783055-Installing ConfiguringyourBrowser.html Browser Configuration
1783075-Installing InstallingCACertificate.html Certificate Installation
To test the “GETBOO” website of the OWASP Broken Web Application Project for CSRF vulnerabilities one then has to follow the steps below:
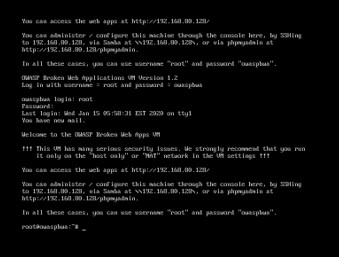
- Start the VM Ware containing the OWASP Broken Web Application Project and log in using the credentials provided.
- Open the Website using the address provided in the VM Ware
- Choose GetBoo
- Authenticate into the website with the credentials user:user
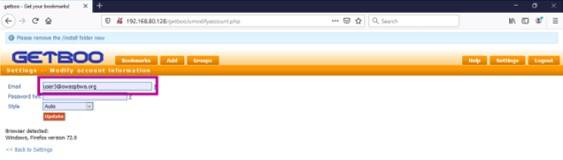
- Modify in the tab "Settings - - Modify account information" the value of the field "Email"
- Chose in Burp Suite in the "Intercept" tab of the "Proxy" tab "Intercept is on".
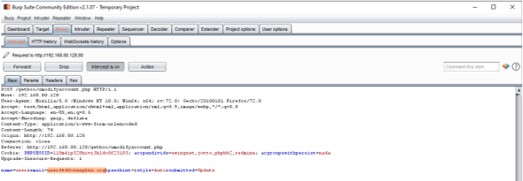
- Submit the request so Burp Suite is able to capture the data
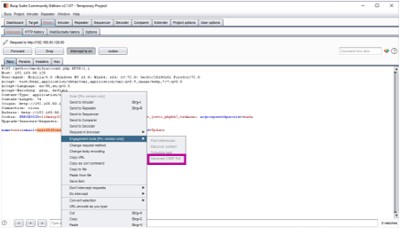
- In the "Proxy" tab right click on the raw request - Engagement tools - Generate CSRF PoC
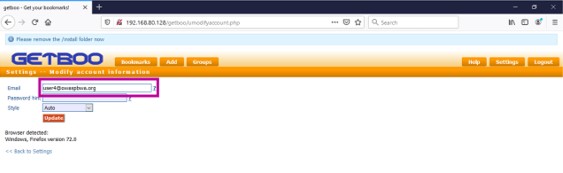
- In the "CSRF PoC generator" it can be seen that the value of email is changed to "user4@owaspbwa.org"
- Click "Copy HTML" in the same window
- Copy this HTML into a text editor and save it as a HTML file
- select in the "Intercept" tab of the "Proxy" tab in Burp Suite "Intercept is off" again
- Open the HTML file saved before using the same browser as before
If the data is successfully changed, the attack has been successful and the website is vulnerable to CSRF Attacks.[2]
Additional Information: The steps after the last picture are only possible if one has a Burp Suite Version higher than Community.
Conclusion
Although CSRF is a rather common web application vulnerability, it is not as widely known, as one would think. Therefore, this article offered a step-by-step guide on how to find a CSRF vulnerability using Burp Suite. For anyone interested in CSRF my seminar paper File:Thesis.pdf offers insight into the vulnerabilities of CSRF, the different attack modes and some defensive techniques are explained as well. As CSRF is not the only common web application vulnerability not so widely known, the paper mentioned before also contains an overview of Cross-Site Scripting (XSS) and its attack modes as well as some defensive techniques.
References
[1] https://www.owasp.org/index.php/Cross-Site Request Forgery
[2] https://support.portswigger.net/customer/portal/articles/ 1965674-using-burp-to-test-for-cross-site-request-forgery-csrf-
[3] https://support.portswigger.net/customer/portal/articles/ 1783066-Installing ConfiguringyourBrowser-FF.html
[4] https://support.portswigger.net/customer/portal/articles/ 1783087-Installing InstallingCACertificate-FF.htm