Root Me

Root-Me is a website, which enable users to expand their pentesting and cyber security knowledge. As a matter of fact, the promotion of knowledge spread is also the main goal and philosophy of the non-profit penetration testing training platform, which was founded in 2010. They think that everybody should have the freedom to access every information for free on the internet, especially about ethical hacking and information security. The platform has grown its own indispensable community, which actively participate on the improvement of the website. There is no hierarchy between members and that is the reason behind the open-minded attitude.
Penetration Testing Training
The era of the Internet has started ongoing innovation in education and learning for students. Personalized and customized courses and training platforms are the basis for in-depth knowledge or practical application of various selected topics. As pentesting plays a significant role in the field of cyber security nowadays, these dedicated training resources offer unlimited opportunities to develop proficiency for this security assessment process. Penetration testing training can be approached by countless courses on platforms like Udemy, cyber security training platforms like Root Me or official certifications.
Penetration Testing
Penetration testing, short pentest, or ethical hacking is a common process in cyber security for analysing and assessing the security of a system. The main objective of a pentest is to uncover existing vulnerabilities of certain aspects of a system by a simulation of a hacker attack. To provide a reliable pentest the aspects of a system being tested must be precisely defined beforehand.
Pentesting consists of three methods called black-, white- and grey box. These methods define the amount of information available to the pentester about the target system.
- In black box testing there is no information revealed at all and the information gathering has to be done from the ground up.
- In a white box scenario, the tester has all the needed information, which is considered as an advantage.
- In grey box testing partial information is revealed to the pentester.
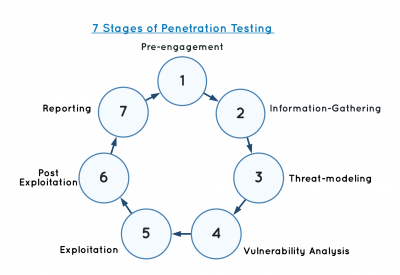
There are seven different stages in a penetration test, which should be fulfilled in this defined order:
Training Platforms
On penetration testing training platforms the grey box method, is commonly used. Specific vulnerability field and/or IP address of the the target system are given the individual, who is trying to solve the challenge.
Typically on all training platforms the key to solving a challenge is a so called ”flag”. This can be a combination of letters and numbers and can have a special meaning to the challenge itself. It can also be the password, which should be cracked or a word, which will be revealed after the exploit. Cyber security training platforms are promoting ethical hacking and the related technique as a powerful tool for justice in era of Internet and improvement of information technologies.
Root Me Overview
For both experts and beginners the platform Root Me delivers realistic and also easier challenges in different fields. To gather strong knowledge in cyber security a recommended learn- ing path is presented to beginners, which can help to progress step-by-step and master all the challenges.
Talking about challenges, there are nine different main types with subcategories:
- App
- Script - goal is to exploit environment weaknesses and misconfigurations. Also common vulnerabilities and their patterns in scripts/systems should be detected.
- System - Obtaining privilege rights by exploiting application vulnerabilities can get the user a flag to validate the challenge.
- Cracking - Cracking executables and reverse engineering binaries is the key to obtain the flag.
- Cryptanalysis - The challenges focus on reverting the encrypted or encoded messages to plain text and submitting it as the password.
- Forensic - Practicing analyzation skills are required to trace back digital assets. Memory dumps, log files or network captures are provided to acquire a flag.
- Network - Packet captures of network traffic with different protocols must be examined in network challenges and are key to solve them.
- Programming - Write code, often with Python, to automate tasks or assemble shellcodes to determine flags.
- Realist - In a near real-world environment with multiple system vulnerabilities the user is in a simulated hacker point of view, which is hired by companies to detect and exploit weaknesses.
- Steganography - In steganography challenges the solver is trying to acquire the hidden information in files. E.g. Images
- Web
- Client - Web scripting languages like JavaScript are used on the client-side and also directly implemented in the web browser, which can used for your advantage. By analyzing scripts and understanding their functionalities it is easy to obtain the flag for these challenges.
- Server - Server-side technologies used on the Internet can be abused to leak information or to manipulate the behaviour of the web browser to gain a password for the challenge. HTML and HTTP examples of server-side technologies used in those type of challenges.
Challenge Write-Up
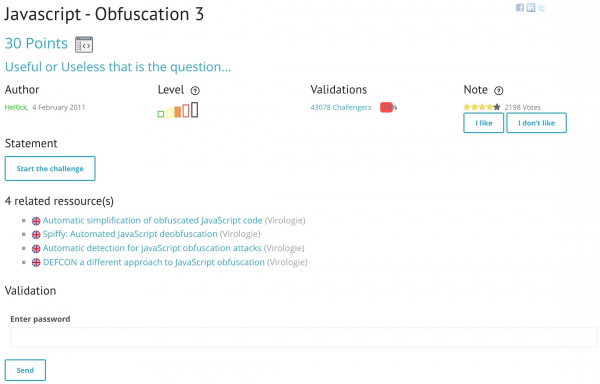
In this section, the solution to the ”Javascript - Obfuscation 3” challenge from the category Web-Client is presented. By the title of this challenge it is evident, that the prerequisite is intermediate knowledge and understanding of the scripting language Javascript. As Javascript is a client-side web technology, the idea is to use the integrated web browser console to manipulate the code and get the flag. Additionally the challenge contains resources, which might be helpful to understand the JavaScript obfuscation concept used in this challenge and how it is abused to make the code harder to understand and still keep its functionality.
After starting the challenge, a website opens up, which prompts the user to enter the password. At this point we can just try to intuitively enter a common password to see what the output/response is going to be. We are going to try ”admin” as our input and see, that an alert pops up with a ”FAUX PASSWORD HAHA” message, which is French and stands for false password haha. As far as we can see, the website is blank and displays no HTML elements, which does not necessarily mean that there is no hidden content or code on the website. This is why the first of an advanced penetration tester will be, trying to interact with the website via browser by inspecting the content of the page.
While analyzing the code and having the knowledge that this challenge is regarding JavaScript, we will be able to find an inline script in the HTML head element, which exposes the functionality of the password prompt. The inline script contains following content:
1 function dechiffre(pass_enc){
2 var pass = "70,65,85,88,32,80,65,83,83,87,79,82,68,32,72,65,72,65" var tab = pass_enc.split(’,’);
3 var tab2 = pass.split(’,’);var i,j,k,l=0,m,n,o,p = ""; i = 0;j = tab.length;
4 k = j + (l) + (n=0); n = tab2.length;
5 for(i = (o=0); i < (k = j = n); i++ ){
6 o = tab[i-l];
7 p += String.fromCharCode((o = tab2[i])); if(i == 5)break;
8 }
9 for(i = (o=0); i < (k = j = n); i++ ){ o = tab[i-l];
10 if(i > 5 && i < k-1)
11 p += String.fromCharCode((o = tab2[i]));
12 }
13 p += String.fromCharCode(tab2[17]);
14 pass = p;return pass;
15 } String["fromCharCode"](dechiffre("\x35\x35\x2c\x35\x36\x2c\x35\x34\x2c\x37\x39\x2c\x31\x31\x35\x2c\x36\x39\x2c\x31\x31\x34\x2c\x31 \x31\x36\x2c\x31\x30\x37\x2c\x34\x39\x2c\x35\x30"));
16 h = window.prompt(’Entrez le mot de passe / Enter password’);
17 alert( dechiffre(h) );
By observing the code we can detect a function dechiffre(pass enc), starting at line 1, which takes a pass enc parameter. By going through the function it is obvious, that it always returns the pass variable, defined on line 2. This means, that trying different promp/function inputs will make no difference, as the default ”FAUX PASSWORD HAHA” message will be displayed. The pass variable is Character Code and as a matter of fact can also be converted back to string format, by using the predefined JavaScript String.fromCharCode(value) function. We can try this by using the built-in web browser console and see the result.
At this point, we are familiar with the String.fromCharCode(value) function and therefore line 15 seems odd. It is a fact that the code has been obfuscated, ’uglified’ or in other words purposely harder to understand. Line 15 can be interpreted as a hint as the value passed to the dechiffre() function is in HEX. We already learned that the JavaScript console is a useful tool, which can also be used to perform the HEX to ASCII characters conversion. This can be done, by simply pasting the HEX string into the console as following:
The result of this operation is in a format, we might recognize, from our previous steps. Keyword: Character Code. Now the character code can be passed as an input to the String.fromCharCode(value) and it might return the flag to solve the challenge. The final outcome of the operation is shown below.
Last step was verifying our success on the Root Me platform by validating the challenge with the flag and we mastered the challenge!
Alternatives
✔️ The platform presents itself as a massive hacking playground with an enormous cyber security community of over 835k users. Its gamified unique learning and hacking approach can make it easy to quickly acquire an skillset for penetration testing. Everyone is welcome to the website, ranging from individual hacker, businesses to universities, which want to elevate their blue and red team cyber security skills.
✔️ If a beginner joins the TryHackMe community, he/she will be able to find write-ups and walkthroughs to challenges on the Internet, when help is needed, as TryHackMe is popular in the penetration testing learning platform field. On the platform there are so called Rooms, which a member can join and solve different tasks regarding a topic. They vary in difficulty and category and are part of learning paths, which are predefined to make the learning uncomplicated. Each room includes directly deployable virtual machines (VM), called AttackBox, that are hosted in the cloud of the platform. By trying to deliver a fun and gamified cyber security learning experience, the platform excels at its best.
Summary
In this Wiki entry the penetration testing learning platform Root Me and the relevancy of such platforms in the field of cyber security was presented and discussed. In conclusion, it is a matter of fact that all penetration testing learning platforms are an effective approach to gain cyber security knowledge and skills by practice. They are therefore in exceptional need these days to educate individuals to become seasoned penetration testers.
Root Me and its alternatives, which have been presented are both beginner and advanced hacker friendly. It is evident, that they provide useful resources to everyone. The fact that each user can tackle specific challenges and tasks in various categories, makes it possible to test their own limits of pentesting. This self reflection can be used to determine lack of knowledge in different areas of cyber security and consequently adapt the learning path accordingly. Suitable resources and community forums allow users to further understand cyber security concepts and discuss theoretical and practical questions for given tasks.
References
- https://openrepository.aut.ac.nz/handle/10292/7801
- https://ieeexplore.ieee.org/document/8378035
- https://ieeexplore.ieee.org/document/9418926
- https://www.researchgate.net/publication/220209928_Ethical_hackers_Putting_on_the_white_hat
- https://www.researchgate.net/publication/267245065_Automatic_Simplification_of_Obfuscated_JavaScript_Code_Extended_Abstract
- https://repo.zenk-security.com/Magazine%20E-book/Penetration%20Testing%20-%20A%20hands-on%20introduction%20to%20Hacking.pdf
- https://www.udemy.com/topic/penetration-testing/
- https://tryhackme.com/
- https://www.hackthebox.com/