Root Me
Summary
Description what this documentation is about.
Penetration Testing Training
Penetration Testing
- Operating system: Ubuntu 18.04 bionic amd64
- Packages: git emacs
Training Platforms
Overview
Step 1
Enter these commands in the shell
echo foo echo bar
Step 2
Make sure to read
- War and Peace
- Lord of the Rings
- The Baroque Cycle
Challenge Write-Up
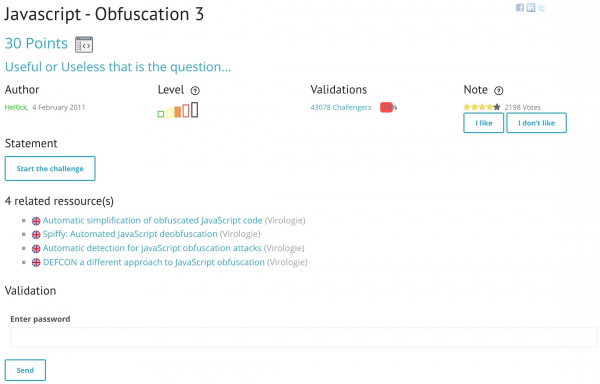
In this section, the solution to the ”Javascript - Obfuscation 3” challenge from the category Web-Client is presented. By the title of this challenge it is evident, that the prerequisite is intermediate knowledge and understanding of the scripting language Javascript. As Javascript is a client-side web technology, the idea is to use the integrated web browser console to manipulate the code and get the flag. Additionally the challenge contains resources, which might be helpful to understand the JavaScript obfuscation concept used in this challenge and how it is abused to make the code harder to understand and still keep its functionality.
After starting the challenge, a website opens up, which prompts the user to enter the password. At this point we can just try to intuitively enter a common password to see what the output/response is going to be. We are going to try ”admin” as our input and see, that an alert pops up with a ”FAUX PASSWORD HAHA” message, which is French and stands for false password haha. As far as we can see, the website is blank and displays no HTML elements, which does not necessarily mean that there is no hidden content or code on the website. This is why the first of an advanced penetration tester will be, trying to interact with the website via browser by inspecting the content of the page.
While analyzing the code and having the knowledge that this challenge is regarding JavaScript, we will be able to find an inline script in the HTML head element, which exposes the functionality of the password prompt. The inline script contains following content:
1 function dechiffre(pass_enc){
2 var pass = "70,65,85,88,32,80,65,83,83,87,79,82,68,32,72,65,72,65" var tab = pass_enc.split(’,’);
3 var tab2 = pass.split(’,’);var i,j,k,l=0,m,n,o,p = ""; i = 0;j = tab.length;
4 k = j + (l) + (n=0); n = tab2.length;
5 for(i = (o=0); i < (k = j = n); i++ ){
6 o = tab[i-l];
7 p += String.fromCharCode((o = tab2[i])); if(i == 5)break;
8 }
9 for(i = (o=0); i < (k = j = n); i++ ){ o = tab[i-l];
10 if(i > 5 && i < k-1)
11 p += String.fromCharCode((o = tab2[i]));
12 }
13 p += String.fromCharCode(tab2[17]);
14 pass = p;return pass;
15 } String["fromCharCode"](dechiffre("\x35\x35\x2c\x35\x36\x2c\x35\x34\x2c\x37\x39\x2c\x31\x31\x35\x2c\x36\x39\x2c\x31\x31\x34\x2c\x31 \x31\x36\x2c\x31\x30\x37\x2c\x34\x39\x2c\x35\x30"));
16 h = window.prompt(’Entrez le mot de passe / Enter password’);
17 alert( dechiffre(h) );
By observing the code we can detect a function dechiffre(pass enc), starting at line 1, which takes a pass enc parameter. By going through the function it is obvious, that it always returns the pass variable, defined on line 2. This means, that trying different promp/function inputs will make no difference, as the default ”FAUX PASSWORD HAHA” message will be displayed. The pass variable is Character Code and as a matter of fact can also be converted back to string format, by using the predefined JavaScript String.fromCharCode(value) function. We can try this by using the built-in web browser console and see the result.
At this point, we are familiar with the String.fromCharCode(value) function and therefore line 15 seems odd. It is a fact that the code has been obfuscated, ’uglified’ or in other words purposely harder to understand. Line 15 can be interpreted as a hint as the value passed to the dechiffre() function is in HEX. We already learned that the JavaScript console is a useful tool, which can also be used to perform the HEX to ASCII characters conversion. This can be done, by simply pasting the HEX string into the console as following:
The result of this operation is in a format, we might recognize, from our previous steps. Keyword: Character Code. Now the character code can be passed as an input to the String.fromCharCode(value) and it might return the flag to solve the challenge. The final outcome of the operation is shown below.
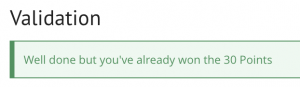
Last step was verifying our success on the Root Me platform by validating the challenge with the flag and we mastered the challenge!
Alternatives
✔️ The platform presents itself as a massive hacking playground with an enormous cyber security community of over 835k users. Its gamified unique learning and hacking approach can make it easy to quickly acquire an skillset for penetration testing. Everyone is welcome to the website, ranging from individual hacker, businesses to universities, which want to elevate their blue and red team cyber security skills.
✔️ If a beginner joins the TryHackMe community, he/she will be able to find write-ups and walkthroughs to challenges on the Internet, when help is needed, as TryHackMe is popular in the penetration testing learning platform field. On the platform there are so called Rooms, which a member can join and solve different tasks regarding a topic. They vary in difficulty and category and are part of learning paths, which are predefined to make the learning uncomplicated. Each room includes directly deployable virtual machines (VM), called AttackBox, that are hosted in the cloud of the platform. By trying to deliver a fun and gamified cyber security learning experience, the platform excels at its best.