Difference between revisions of "SQL Injection Examples on Known Vulnerable Web Applications"
VHorvathova (talk | contribs) |
VHorvathova (talk | contribs) |
||
| Line 38: | Line 38: | ||
== Acuart == | == Acuart == | ||
This is a web application (http://testphp.vulnweb.com/) created by Acunetix as a test and demonstration site for Acunetix Web Vulnerability Scanner <ref>Acuart test and demonstration site, 2022, accessed on: 05.01.2022. [Online]. Available: http://testphp.vulnweb.com/</ref><ref>Acunetix web vulnerability scanner, 2022, accessed on: 05.01.2022. [Online]. Available: https://www.acunetix.com/</ref>. Following are some examples | This is a web application (http://testphp.vulnweb.com/) created by Acunetix as a test and demonstration site for Acunetix Web Vulnerability Scanner <ref>Acuart test and demonstration site, 2022, accessed on: 05.01.2022. [Online]. Available: http://testphp.vulnweb.com/</ref><ref>Acunetix web vulnerability scanner, 2022, accessed on: 05.01.2022. [Online]. Available: https://www.acunetix.com/</ref>. Following are some examples categorized by the previously listed SQLi types on this vulnerable web application. | ||
* <b>Error-based SQLi</b> | * <b>Error-based SQLi</b> | ||
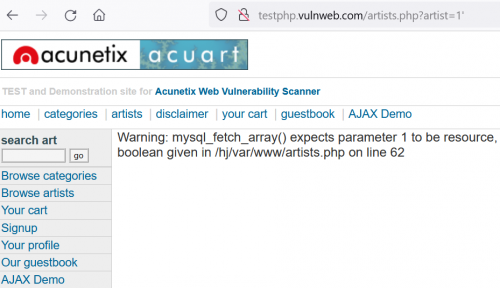
The URL we are targeting is http://testphp.vulnweb.com/artists.php?artist=1, which we want to manipulate. Somehow we want to pass a wrong SQL query to the backend database, to see if we receive an error message. A vulnerable web application will show one, while a secure server should never show error messages to regular website visitors. | The URL we are targeting is http://testphp.vulnweb.com/artists.php?artist=1, which we want to manipulate. Somehow we want to pass a wrong SQL query to the backend database, to see if we receive an error message. A vulnerable web application will show one, while a secure server should never show error messages to regular website visitors. <br> | ||
Now we try adding a single quote to the SQL query, which generates an error message as shown in the following screenshot. | |||
[[File:Error1.PNG|500px|center]]</br> | |||
== DVWA == | == DVWA == | ||
Revision as of 12:09, 5 January 2022
Summary
This is a documentation of various SQL Injection attacks performed on well-known and also not so popular vulnerable web applications. DRAFT
Requirements
- Operating system:
Methodology
Each example contains a link to the vulnerable web application or to a tutorial how to set it up, unless it is a vulnerable website that is just accessed online. Web applications used:
- Acuart
- BWAPP
- DVWA
- OWASP Juice Shop
- OWASP Mutillidae
- Badstore
- Zero Bank
- Hackxor
- ...
Each web application is listed below in separate chapters, providing some examples of the SQLi. This Wiki also offers a brief overview over the general types of SQL injection, another somewhat different overview can also be found here: SQL Injection.
Overview - Types of SQL injection [1]
In-band SQLi (Classic SQLi)
In-band SQL Injection is the most common and easy-to-exploit of SQL Injection attacks. In-band SQL Injection occurs when an attacker is able to use the same communication channel to both launch the attack and gather results [1]. There are two under categories of this SQLi type.
- Error-based SQLi
Error-based SQLi is an in-band SQL Injection technique that relies on error messages thrown by the database server to obtain information about the structure of the database. While errors are very useful during the development phase of a web application, they should be disabled on a live site, or logged to a file with restricted access instead, so that no attacker can see error information displayed directly on the website.
- Union-based SQLi
Union-based SQLi is an in-band SQL injection technique that uses the UNION SQL operator to combine the results of two or more SELECT statements into a single result which is then returned as part of the HTTP response.
Inferential SQLi (Blind SQLi)
Inferential SQL Injection, unlike in-band SQLi, may take longer for an attacker to exploit, however, it is just as dangerous as any other form of SQL Injection. In an inferential SQLi attack, no data is actually transferred via the web application and the attacker would not be able to see the result of an attack in-band (which is why such attacks are commonly referred to as “blind SQL Injection attacks”). Instead, an attacker is able to reconstruct the database structure by sending payloads, observing the web application’s response and the resulting behavior of the database server.
- Boolean-based (content-based) Blind SQLi
This technique functions via sending an SQL query to the database which forces the application to return a different result depending on whether the query returns a TRUE or FALSE result. Depending on the result, the content within the HTTP response will change, or remain the same. This allows an attacker to infer if the payload used returned true or false, even though no data from the database is returned. This way, the attacker can ask "true" and "false" questions and in this way GUESS a lot of essential information about the database, such as table/column/attribute names, users, passwords and much more.
- Time-based Blind SQLi
Sends an SQL query to the database which forces the database to wait for a specified amount of time (in seconds) before responding. The response time will indicate to the attacker whether the result of the query is TRUE or FALSE. Depending on the result, an HTTP response will be returned with a delay, or returned immediately. This allows an attacker to infer if the payload used returned true or false, even though no data from the database is returned. The reason why the previous category is called content-based compared to this, is that here the true/false questions are based on returning the same result with a delay, whilst the content-based returns a different result.
Out-of-band SQLi
Out-of-band SQL Injection is not very common, mostly because it depends on features being enabled on the database server being used by the web application. Out-of-band SQL Injection occurs when an attacker is unable to use the same channel to launch the attack and gather results. Out-of-band SQLi techniques would rely on the database server’s ability to make DNS or HTTP requests to deliver data to an attacker. Such is the case with Microsoft SQL Server’s xp_dirtree command, which can be used to make DNS requests to a server an attacker controls; as well as Oracle Database’s UTL_HTTP package, which can be used to send HTTP requests from SQL and PL/SQL to a server an attacker controls.
Acuart
This is a web application (http://testphp.vulnweb.com/) created by Acunetix as a test and demonstration site for Acunetix Web Vulnerability Scanner [2][3]. Following are some examples categorized by the previously listed SQLi types on this vulnerable web application.
- Error-based SQLi
The URL we are targeting is http://testphp.vulnweb.com/artists.php?artist=1, which we want to manipulate. Somehow we want to pass a wrong SQL query to the backend database, to see if we receive an error message. A vulnerable web application will show one, while a secure server should never show error messages to regular website visitors.
Now we try adding a single quote to the SQL query, which generates an error message as shown in the following screenshot.
DVWA
The so-called damn vulnerable web app (DVWA) is a vulnerable PHP / MySQL web service [4][5]. For a related article with a tutorial on how to set up the DVWA, please refer to DVWA wiki.
Used Hardware
Device to be used with this documentation Maybe another device to be used with this documentation
References
- ↑ Acunetix, Types of SQL Injection (SQLi), 2022, accessed on: 05.01.2022. [Online]. Available: https://www.acunetix.com/websitesecurity/sql-injection2/
- ↑ Acuart test and demonstration site, 2022, accessed on: 05.01.2022. [Online]. Available: http://testphp.vulnweb.com/
- ↑ Acunetix web vulnerability scanner, 2022, accessed on: 05.01.2022. [Online]. Available: https://www.acunetix.com/
- ↑ DVWA, 2022, accessed on: 05.01.2022. [Online]. Available: https://dvwa.co.uk//
- ↑ DVWA Github, 2022, accessed on: 05.01.2022. [Online]. Available: https://github.com/digininja/DVWA