Throwing Star LAN Tap
Summary
This description shows what the Throwing Star LAN Tap device is and how it can be used. Further information is given when the thorough explanation requires it.
Requirements
To use this device for traffic sniffing, the following things are needed:
- Throwing Star LAN Tap Kit (assembled) or Pro edition
- Wired LAN network, where the LAN sniffing device can be installed
- Device with RJ45 Ethernet port as monitoring device
- Wireshark running on the monitoring device for capturing the traffic
Description
LAN Taps are integrated in the existing network and are used to monitor the network, because all traffic/packets coming into and going out of the network can be inspected using sniffing programs such as WireShark. The Throwing Star LAN Tap is a passive Ethernet tap that needs no power for working.
Device - Editions
There are two editions: the Kit (Throwing Star LAN Tap Kit), which you must assemble yourself and solder to work, and the Pro Edition (Throwing Star LAN Tap Pro). The device itself is the same.
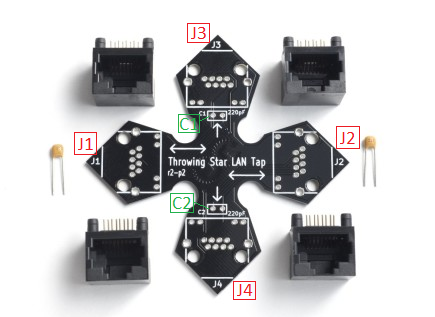
- The Kit is a circuit board printed as star shaped with four RJ-45 (Ethernet) connectors and two 220pF capacitors that must be placed on the board.
- The Pro Edition is the second option, where the electrical components are already soldered and prepared for easier usage and the device fully assembled.
Assembly of the Throwing Star LAN Tap Kit
To assemble the Throwing Star LAN Tap Kit, the following steps must be taken:
- The four modular RJ-45 connectors are inserted into the circuit board at J1 - J4.
- The two capacitors are inserted into the C1 and C2 slots at the J3 and J4 monitoring ports.
- If the assembly is done permanently, the eight leads of each connector and both leads of each capacitor must be soldered carefully.
- After the assembly is done, the Throwing Star LAN Tap is connected by Ethernet cables in line with the target network at J1 and J2.
- One or both of the monitoring ports J3 and J4 are connected with Ethernet cables to one or two monitoring devices.
- To capture the network traffic, a software such as WireShark or tcptump is used on the monitoring device.
In the following image you can see how the Throwing Star LAN Tap Kit has to be connected with Ethernet cables. The black cables seen in the picture are connected to the Internet and the target device. The yellow cable is connected to the monitoring device.
Step 1: Installation of the device in the LAN network
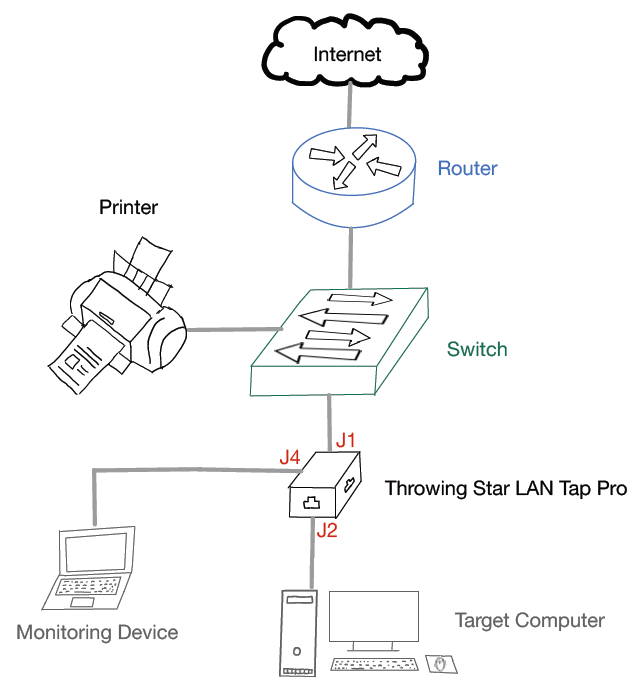
The following figure shows how the LAN traffic sniffing device can be implemented into the existing LAN network. From here on out, it does not matter whether the Kit or Pro edition is used - both work the same. The sniffing device, in this example, is placed between the switch and the target computer. The traffic runs through the device (ports J1 and J2). The monitoring notebook is connected to the monitoring port J4 of the Throwing Star LAN Tap Pro.
Step 2: Performing different tasks on the target computer
For capturing various packets, several different kinds of programs and usages were performed on the target computer, which are listed in the following points:
- Browser Usage with HTTP-websites
- Browser Usage with HTTPS-websites
- VPN Connection
- Checking emails with Outlook in the browser
- Watching videos in the browser (https-websites)
- Printing PDFs on the connected printer in the network
- Listening to music with Spotify
- Identify potential security threats
- Monitor network traffic for performance analysis
- Analyze network traffic for security vulnerabilities
- Detect and investigate potential security incidents
- Identify and troubleshoot network issues
- Evaluate and ensure the quality of network service
- Analyze data to optimize network performance
- Monitor for suspicious or unauthorized activities on the network
Step 3: Analyse results in Wireshark on the monitoring device
Introduction
Nowadays, every secure website uses HTTPS for communication over a computer network. It is also called HTTP over TLS, because the communication protocol is encrypted using TLS (Transport Layer Security). The packets that are captured in Wireshark need to be inspected properly and in detail, because packet analysis is more complex since most internet traffic is encrypted and applications commonly use encryption based on TLS as well. Only if the HTTP-protocol is used, the information can be sniffed easier. As an example, data/information that is shown in the Wireshark captures for TCP communication with HTTPS on top. These are one of the most important protocols for the mentioned use-cases described in Step 2.
- Source IP and Destination IP
- Source Port and Destination Port
- Source MAC and Destination MAC
- Round Trip Time (RTT) between client and server
- Time to live (TTL) - which indicates the hops between client and server
- TCP windows and flags
- Sessions
- Packets, Data, Payload
- Retransmissions
Getting this basic metadata, which actually provides information about other data, with the Throwing Star LAN Tap is really powerful, because today, data is everything. Algorithms and systems can be used to extract insights and knowledge from this unstructured and structured data. Implementing the sniffing device (Throwing Star LAN Tap Kit or Pro edition) in corporate networks provides powerful information about companies, their whereabouts, knowledge, views and a lot more. Extracting useful information from the data is very important for data mining, which can give companies competitive advantages through statistics and predictions on basis of the given data.
Example Results
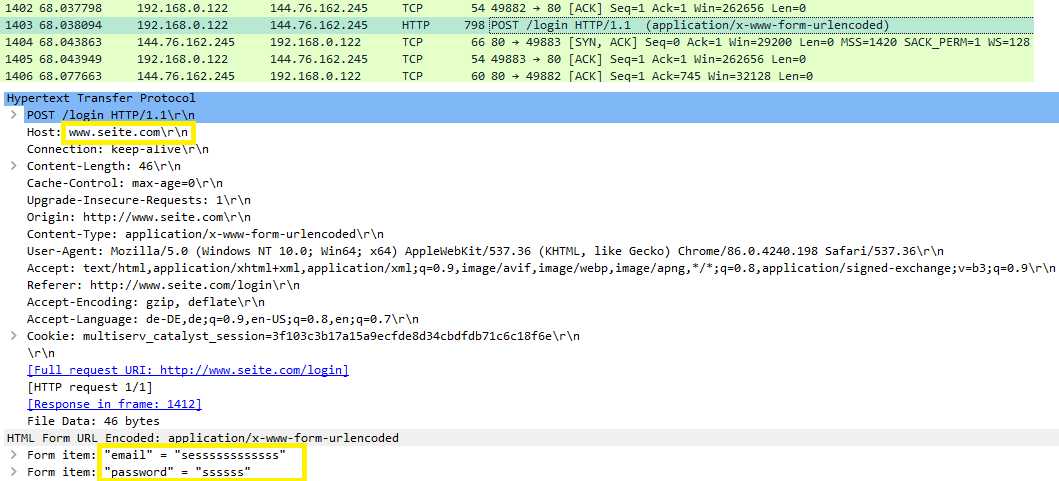
The following figures show examples of which kind of information can be sniffed with the Throwing Star LAN Tap. The target computer has the IP-address 192.168.0.122. The screenshots are taken from the Wireshark capture of the monitoring device. The first example shows what kind of things are possible to see, if the HTTP-protocol is used. The login data can be read in cleartext, which is marked together with the host with a yellow rectangle.
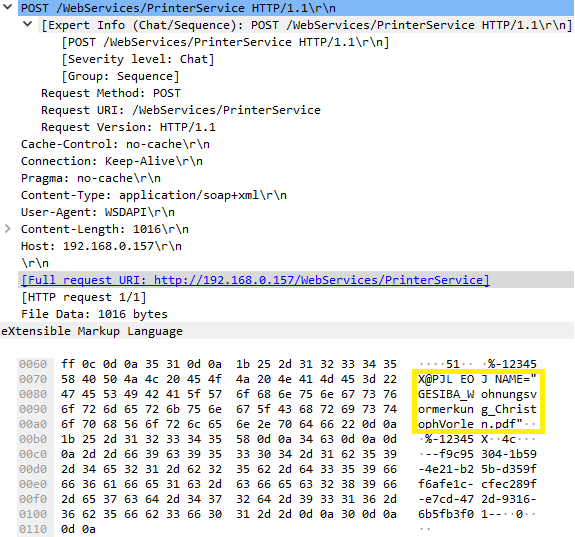
The second packet capture example of Wireshark in the following figure shows that a document was printed on the printer, which is available in the Local Area Network (LAN). The document name can be seen in cleartext in the Wireshark packet capture, highlighted with a yellow rectangle.
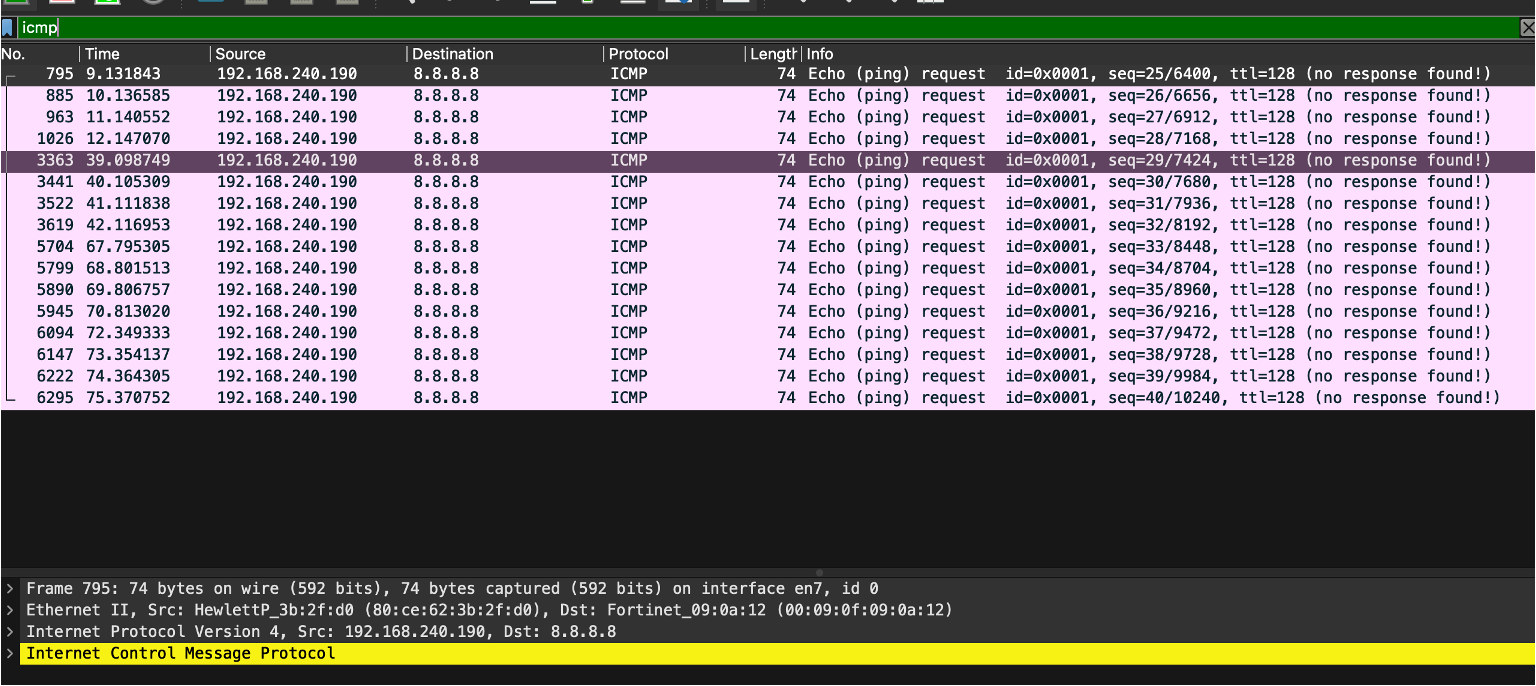
The third packet capture example of Wireshark in the following figure shows that a ping command was executed on the target computer with the IP adddress 192.168.240.190. ICMP echo requests are sent, which can be captured in Wireshark on the monitoring device, as seen in the following image.
Summary of the important aspects
All captured packets in Wireshark provide data like the listed points given in step 2 above for TCP with HTTPS on top. It is important to mention that the most data can be seen during connection/3-way-handshake or at the beginning of a session or transaction. After the initiation process and data starts flowing, only the payload can be seen, which does not provide more than encrypted payload packets with source and destination, length/size and the used protocol. As an example, for a network administrator it is possible to use data such as Source/Destination IP, Source/Destination MAC and the protocols to easily comprehend what the devices or users in the target network are up to and with whom they are communicating. It is important to remember that nowadays several protocols in use ensure security for the packets sent over a network. Therefore, traffic sniffing by using a device such as the Throwing Star LAN Tap becomes more difficult with Wireshark, but it is still possible to see loads of information and metadata. These can be used to inspect and learn a lot about the target network and are really powerful to a network administrator or for illegally obtained access to the network from a hacker. With a high number of IoT devices connected to a Local Area Network via Ethernet, the Throwing Star LAN Tap can be used very successfully by installing it in the right place in the network, for example between the switch and router. If all IoT devices are directly connected to the switch, all traffic that is sent to the router can be sniffed on the monitoring port, without any of the IoT devices knowing about this. For network administrators this can be a very powerful tool to find flaws and problems or inspect the network in detail.
Important Take-Aways
- The Throwing Star LAN Tap is a device for passive LAN traffic sniffing and is a really powerful tool for network administrators.
- Nowadays, several protocols in use ensure security for the packets sent over a network. Traffic sniffing therefore becomes more difficult with Wireshark, but it is still possible to see loads of information and metadata. Stealing confidential data is not the primary goal nowadays.
- Algorithms and systems can be used to extract insights and knowledge from these unstructured and structured data. Extracting useful information from this data is very important for data mining, which can give companies competitive advantages through statistics and predictions on basis of the given data.
- The device is transparent to the network, so it doesn't alter the flow of data or introduce laten
Used Hardware
References
- Hessel Schut, Mark Scanlon, Jason Farina, and Nhien-An Le-Khac. Towards the Forensic Identification and Investigation of Cloud Hosted Servers through Non-Invasive Wiretaps. 08/2015
- V. Ribeiro, A. Rocha, R. Peixoto, F. Portela, and M. F. Santos. Importance of statistics for data mining and data science. In 2017. 5th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), pages 156-163, 2017.
- T. Scheible, Hardware & Security Werkzeuge, Pentesting, Prävention. Bonn: Rheinwerk, pages 470-474 2022.
- Michael Kofler, Klaus Gebeshuber, Peter Kloep, Frank Neugebauer, Andr´e Zingsheim, Thomas Hackner, Markus Widl, Roland Aigner, Stefan Kania, Tobias Scheible, and Matthias W¨ubbeling. Hacking and security: The comprehensive guide to penetration testing and cybersecurity. SAP Press, 2023