Throwing Star LAN Tap
Summary
This description shows what the Throwing Star LAN Tap device is and how it can be used.
Requirements
- Throwing Star LAN Tap Kit or Pro edition
- Device with RJ45 Ethernet port as monitoring device
- Wired LAN network, where the LAN sniffing device is installed
Description
LAN Taps are integrated in the existing network and are used to monitor the network, because all traffic/packets coming into and going out of the network can be inspected using sniffing programs such as WireShark. The Throwing Star LAN Tap is a passive Ethernet tap that needs no power for working.
Versions
There are two editions: the Kit (Throwing Star LAN Tap Kit), which you must assemble yourself and solder to work. And the Pro Edition (Throwing Star LAN Tap Pro), where the electrical components are already soldered and prepared for easier usage and fully assembled in a plastic box. The device itself is the same.
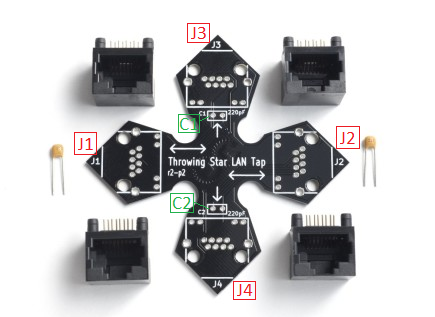
- The Kit is a circuit board printed as star shaped with four RJ-45(Ethernet) connectors and two 200pF capacitors that must be placed on the board.
- The Pro Edition is the second option, where the electrical components are already soldered and prepared for easier usage and the device fully assembled.
Assembly of the Throwing Star LAN Tap Kit
To assemble the Throwing Star LAN Tap Kit, the following steps must be taken:
- The four modular RJ-45 connectors are inserted into the circuit board at J1 - J4.
- The two capacitors are inserted into the C1 and C2 slots at the J3 and J4 monitoring ports.
- If the assembly is done permanently, the eight leads of each connector and both leads of each capacitor must be soldered carefully.
- After the assembly is done, the Throwing Star LAN Tap is connected by Ethernet cables in line with the target network at J1 and J2.
- One or both of the monitoring ports J3 and J4 are connected with Ethernet cables to one or two monitoring devices.
- To capture the network traffic, a software such as WireShark or tcptump is used on the monitoring device.
Step 1: Installation of the device in the LAN network
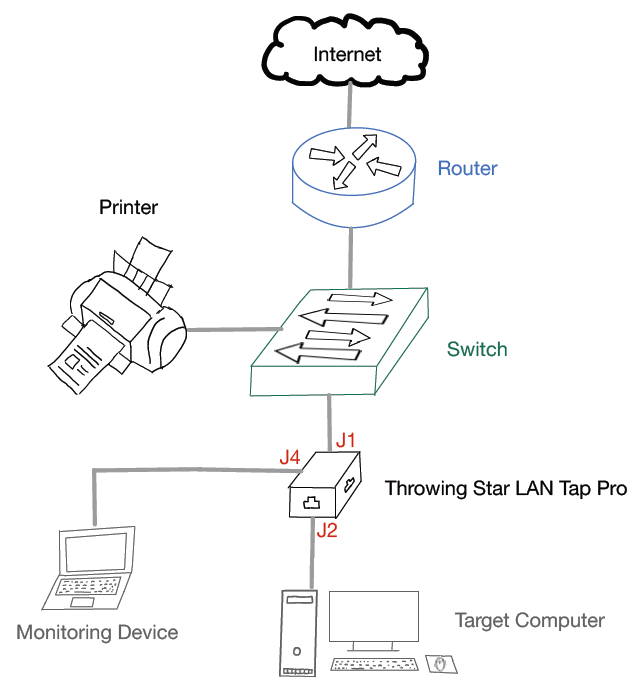
The following figure shows how the LAN traffic sniffing device can be implemented into the existing LAN network. From here on out, it does not matter whether the Kit or Pro edition is used - both work the same. The sniffing device was placed between the switch and the target computer. The traffic runs through the device (ports J1 and J2). The monitoring notebook is connected to the monitoring port J4 of the Throwing Star LAN Tap Pro.
Step 2: Performing different tasks on the target computer
For testing purposes, several different kinds of programs and usages were performed on the target computer, which are listed in the following points:
- Browser Usage with HTTP-websites
- Browser Usage with HTTPS-websites
- VPN Connection
- Checking emails with Outlook in the browser
- Watching videos in the browser (https-websites)
- Printing PDFs on the connected printer in the network
- Listening music with Spotify
Step 3: Results in Wireshark
Nowadays, every secure website uses HTTPS for communication over a computer network. It is also called HTTP over TLS, because the communication protocol is encrypted using TLS (Transport Layer Security). The packets that are captured in Wireshark need to be inspected properly and in detail, because packet analysis is more complex since most internet traffic is encrypted and applications commonly use encryption based on TLS as well. Only if the HTTP-protocol is used, the information can be sniffed easier. As an example, data/information that is shown in the Wireshark captures for TCP communication with HTTPS on top. These are one of the most important protocols for the mentioned use-cases described in Step 2.
- Source IP and Destination IP
- Source Port and Destination Port
- Source MAC and Destination MAC
- Round Trip Time (RTT) between client and server
- Time to live (TTL) - which indicates the hops between client and server
- TCP windows and flags
- Sessions
- Packets, Data, Payload
- Retransmissions
Getting this basic metadata, which actually provides information about other data, with the Throwing Star LAN Tap Pro is really powerful, because today, data is everything. Algorithms and systems can be used to extract insights and knowledge from this unstructured and structured data.