Difference between revisions of "USB Armory"
| Line 10: | Line 10: | ||
* Full internal and third-party security audit for HABv4 and chain of trust. | * Full internal and third-party security audit for HABv4 and chain of trust. | ||
* Addition of built-in eMMC storage and external crypto authenticator. | * Addition of built-in eMMC storage and external crypto authenticator. | ||
* Bluetooth communication. | * Bluetooth communication <ref>Andrea Barisani, USB ARMORY RELOADED, https://www.nohat.it/2019/slides/nohat_barisani.pdf, 2019</ref>. | ||
=== Hardware === | === Hardware === | ||
* SoC: NXP i.MX6ULZ ARM® Cortex™-A7 900 MHz | * SoC: NXP i.MX6ULZ ARM® Cortex™-A7 900 MHz | ||
| Line 21: | Line 21: | ||
* External security elements: Microchip ATECC608A + NXP A71CH | * External security elements: Microchip ATECC608A + NXP A71CH | ||
* Physical size: 66 mm x 19 mm x 8 mm (without enclosure, including USB-C connector) | * Physical size: 66 mm x 19 mm x 8 mm (without enclosure, including USB-C connector) | ||
* Enclosure: included with all units for device protection | * Enclosure: included with all units for device protection <ref>Hacker Warehouse, USB Armory MK II, https://hackerwarehouse.com/product/usb-armory-mkii/, 2019</ref> | ||
===Software === | ===Software === | ||
* Boots from onboard eMMC or microSD (or via USB serial downloader) | * Boots from onboard eMMC or microSD (or via USB serial downloader) | ||
* Native Linux support – creating boot images is easy | * Native Linux support – creating boot images is easy | ||
* Precompiled images are available for Debian 9 (Stretch) and Arch Linux, with more on the way | * Precompiled images are available for Debian 9 (Stretch) and Arch Linux, with more on the way | ||
* USB device emulation (CDC Ethernet, mass storage, HID, etc.) | * USB device emulation (CDC Ethernet, mass storage, HID, etc.) <ref>Andrea Barisani, MK II Introduction, https://github.com/f-secure-foundry/usbarmory/wiki/Mk-II-Introduction#software</ref> | ||
=== How to connected === | === How to connected === | ||
* USB 2.0 over USB-C plug to host with full device emulation | * USB 2.0 over USB-C plug to host with full device emulation | ||
| Line 33: | Line 33: | ||
* Flash drive functionality via USB mass storage device emulation | * Flash drive functionality via USB mass storage device emulation | ||
* Serial communication over USB or physical UART using the Debug Board | * Serial communication over USB or physical UART using the Debug Board | ||
* Wireless connectivity over BLE | * Wireless connectivity over BLE <ref>Mouser Electronic, F-Secure USB Armory Mk II, https://www.mouser.at/new/f-secure/crowd-supply-usb-armorymkii/</ref> | ||
== Application examples == | == Application examples == | ||
Revision as of 21:34, 4 January 2022
Introduction
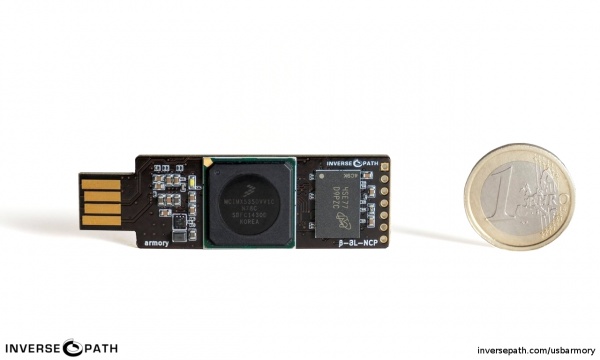
Launched in 2014, USB Armory is a small and portable USB-sized personal computer created by Andrea Barisani [1]. Originally intended to be produced as a secure data store, USB Armory managed to become a versatile device with the development of its Hardware and Software. With its hardware sufficient as a computer, it can be configured on an installed Linux system that boots and thus powers up when plugged into any computer, for example, so that data not only ends up on an encrypted partition, but is automatically re-encrypted when transferred [2] .
Design Goals
- The microSD hinge replacement with a push/pull slot.
- Real USB plugs, plug + socket for integrated host adapter.
- Enclosure design right from the beginning.
- Full internal and third-party security audit for HABv4 and chain of trust.
- Addition of built-in eMMC storage and external crypto authenticator.
- Bluetooth communication [3].
Hardware
- SoC: NXP i.MX6ULZ ARM® Cortex™-A7 900 MHz
- RAM: 512 MB DDR3
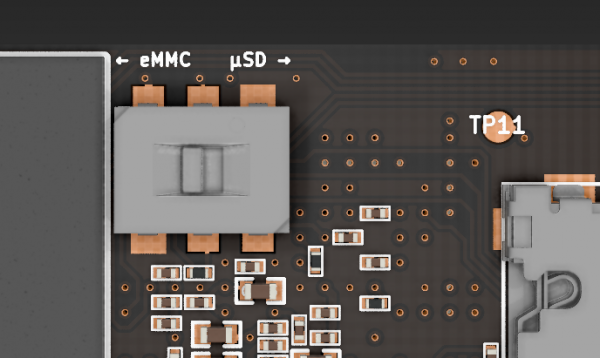
- Storage: internal 16 GB eMMC + external microSD
- Bluetooth module: u-blox ANNA-B112 BLE
- USB-C ports: DRP (Dual Role Power) receptacle + UFP (Upstream Facing Port) plug, USB 2.0 only (no * video support)
- LEDs: two
- Slide switch: for boot mode selection between eMMC and microSD
- External security elements: Microchip ATECC608A + NXP A71CH
- Physical size: 66 mm x 19 mm x 8 mm (without enclosure, including USB-C connector)
- Enclosure: included with all units for device protection [4]
Software
- Boots from onboard eMMC or microSD (or via USB serial downloader)
- Native Linux support – creating boot images is easy
- Precompiled images are available for Debian 9 (Stretch) and Arch Linux, with more on the way
- USB device emulation (CDC Ethernet, mass storage, HID, etc.) [5]
How to connected
- USB 2.0 over USB-C plug to host with full device emulation
- USB 2.0 over USB-C receptacle for the additional devices or as a connection to the host
- Full TCP/IP connection to/from USB armory via USB CDC Ethernet emulation
- Flash drive functionality via USB mass storage device emulation
- Serial communication over USB or physical UART using the Debug Board
- Wireless connectivity over BLE [6]
Application examples
- mass storage device with advanced features such as automatic
- encryption, virus scanning, host authentication, and data self-destruct
- OpenSSH client and agent for untrusted hosts (kiosk)
- router for end-to-end VPN tunneling, Tor
- password manager with integrated webserver
- electronic wallet (e.g. pocket Bitcoin wallet)
- authentication token
- portable penetration testing platform
- low-level USB security testing
Getting Started
Boot Mechanisms
In order for USB Armory to work in a certain operating system, either the microSD card inserted in the device or the MMc (16 GB) in it must be booted. Mk II supports 3 boot mechanisms:
- internal 16GB eMMC
- external microSD
- USB Serial Download Protocol (SDP)
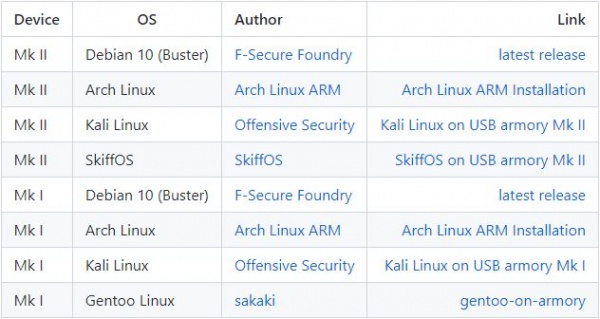
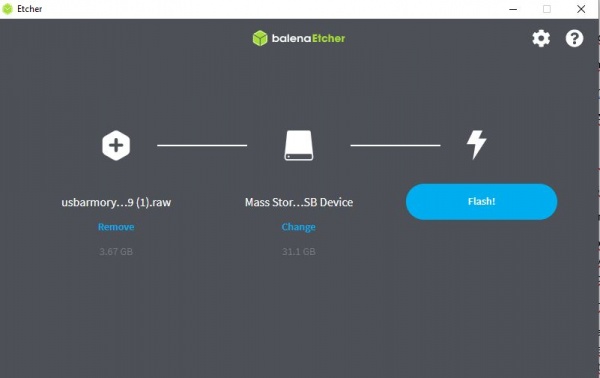
if we want to boot the MMC we have to drag the inverter to the left, and if we want to boot the SD micro card we have to drag the inverter to the right. If we want to put it in SDP mode we have to leave it in the middle. How to boot a microSD card? USB Armory has a valid Pre-Image file for each operating system on its own page. Optionally, booting can be done either manually or by downloading the appropriate file and flashing the microSD card (before it is inserted into the USB Armory) with balenaEtcher software.
1. Step
You can find the following Pre-Image files at this link: https://github.com/f-secure-foundry/usbarmory/wiki/Available-images
2. Step
You can download the following software here: https://www.balena.io/etcher/
Host communication
Since the booted microSD card is ready in the operating system, Host communication can be started. For other operating systems, click here: https://github.com/f-secure-foundry/usbarmory/wiki/Host-communication
# look up the name of the USB virtual Ethernet interface which was created by the USB Armory ifconfig
# bring the USB virtual Ethernet interface up /sbin/ip link set usb0 up
# set the host IP address /sbin/ip addr add 10.0.0.2/24 dev usb0
# enable masquerading for outgoing connections towards wireless interface sudo /sbin/iptables -t nat -A POSTROUTING -s 10.0.0.1/32 -o <actual interface on host machine> -j MASQUERADE
# enable masquerading for outgoing connections towards wireless interface /sbin/iptables -t nat -A POSTROUTING -s 10.0.0.1/32 -o wlan0 -j MASQUERADE
# enable IP forwarding sudo sysctl -w net.ipv4.ip_forward=1
#connect to USB Armory via ssh - password: USB armory ssh usbarmory@10.0.0.1
#install Lynx Web browser on USB Armory sudo apt-get install Lynx
#launch Lynx Web browser on USB Armory lynx google.com
References
- https://hackerwarehouse.com/product/usb-armory-mkii/
- https://github.com/f-secure-foundry/usbarmory/wiki
- https://genode.org/documentation/articles/trustzone
- https://www.f-secure.com/en/consulting/foundry/usb-armory
- https://inversepath.com/usbarmory_mark-one.html
- https://www.golem.de/news/usb-armory-linux-stick-fuer-sichere-daten-1412-111374.html
- https://github.com/f-secure-foundry/usbarmory/wiki/Boot-Modes-(Mk-II)
- https://github.com/f-secure-foundry/usbarmory/wiki/Available-images
- https://www.balena.io/etcher/
- https://github.com/f-secure-foundry/usbarmory/wiki/Host-communication
- ↑ Andrea Barisani. Forging the USB armory, https://www.nohat.it/2019/slides/nohat_barisani.pdf ,2014.
- ↑ NXP Communitiy, Introducing USB armory, an Open Source Hardware Freescale i.MX53 Dongle , https://community.nxp.com/t5/i-MX-Solutions-Knowledge-Base/Introducing-USB-armory-an-Open-Source-Hardware-Freescale-i-MX53/ta-p/1126823, 2014
- ↑ Andrea Barisani, USB ARMORY RELOADED, https://www.nohat.it/2019/slides/nohat_barisani.pdf, 2019
- ↑ Hacker Warehouse, USB Armory MK II, https://hackerwarehouse.com/product/usb-armory-mkii/, 2019
- ↑ Andrea Barisani, MK II Introduction, https://github.com/f-secure-foundry/usbarmory/wiki/Mk-II-Introduction#software
- ↑ Mouser Electronic, F-Secure USB Armory Mk II, https://www.mouser.at/new/f-secure/crowd-supply-usb-armorymkii/