USB Armory
Summary
This documentation describes basic information about USB Armory. General functionalities / hardfacts about the system and a set up example, where a Linux OS with a Lynx Browser application is installed via ssh on the USB Armory (Mk I).
Requirements
- Operating system: Ubuntu 18.04 bionic amd64
- Packages: -
Basic information
- F-Secure's or Inverse Path's USB-Armory (Mk I) is an open-source hardware design that implements a flash-drive sized computer.
- The device is conventionally connected to an end device or any power source via the installed USB Type-A port, and due to the compactness of the overall system, provides an efficient and mobile way to develop and run a variety of applications and even full operating systems.
- The USB Armory is implemented as a System on a Chip (SoC), which, with the help of the board's open-source architecture and the software integrations provided, offers a fully customizable and secure USB device for innovative and personal security applications.
- The hardware design features the NXP i.MX53 processor, which supports advanced security features such as Secure Boot and ARM - TrustZone. It is supported by standard software environments and requires very little customization. In fact, vanilla Linux kernels and standard distributions run seamlessly USB Armory board, despite its small format.
- The Secure Boot feature allows users to combine verification keys that guarantee only trusted firmware can run on the USB-Armory.
- ARM - TrustZone support also enables developers to create custom trusted platform modules (TPMs), unlike traditional trusted platform modules (TPMs), by enforcing domain separation between the "secure" and "normal" worlds, which spreads across all SoC components and is therefore not limited to the CPU core.
Application examples
1. File storage with advanced features such as automatic encryption, virus scanning, host authentication and self-destruction of data.
2. OpenSSH client and agent for using public or insecure hosts.
3. Router for end-to-end VPN tunneling, Tor
4. Password manager with integrated web server
5. Electronic wallet (e.g. Bitcoin wallet)
6. Mobile platform for penetration-testing
7. Almost full-fledged end device via host adapter
How to set up the USB Armory
This is an introduction on how to set up the USB Armory with a Linux OS fully working on the device. A full-featured (precompiled image is used to facilitate the process) Linux image can be flashed to an micro-SD card, which can then be inserted into the USB Armory and booted by plugging the USB Armory into an end-device, for example.
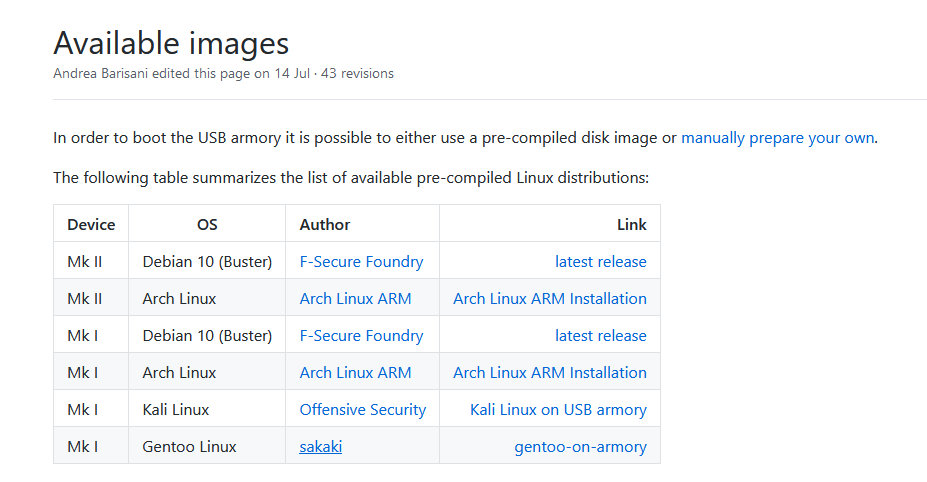
Download a Linux Distribution image from the list
- List of precompiled-images: https://github.com/f-secure-foundry/usbarmory/wiki/Available-images
- Download and unzip the image to get a ".raw" file
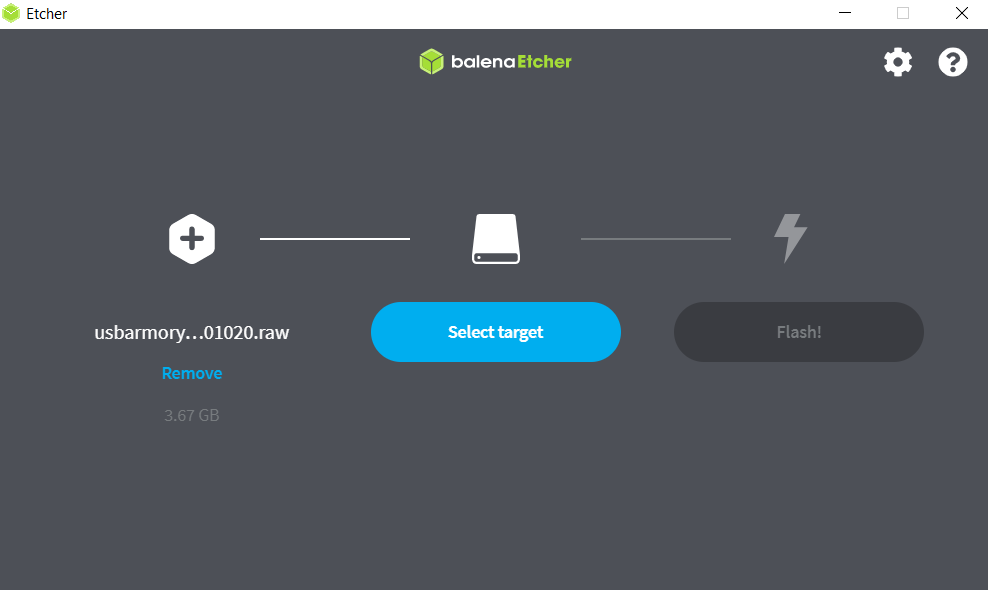
Flash image to any Mirco-SD card (min. 4GB) with the Etcher tool
- Download and install the tool for the appropriate OS, link: https://www.balena.io/etcher/
- Start tool, insert Micro-SD into host device
- Select Micro-SD, select .raw file from 1. and start the process
Once the process is finished, the Micro-SD card can be inserted into the USB-Armory and the USB-Armory can be plugged into a USB port of your laptop and will boot directly! A blinking LED indicates that the device is up and running.
Connect to the USB Armory via ssh and install/run Lynx Browser
Once the USB Armory is set up and ready to use, plug it into the computer and open a terminal on the host machine. Type in the following commands:
# look up the name of the USB virtual Ethernet interface which was created by the USB Armory ifconfig
# bring the USB virtual Ethernet interface up sudo /sbin/ip link set <name of virtual interface> up
# set the host IP address sudo /sbin/ip addr add 10.0.0.2/24 dev <name of virtual interface>
# enable masquerading for outgoing connections towards wireless interface sudo /sbin/iptables -t nat -A POSTROUTING -s 10.0.0.1/32 -o <actual interface on host machine> -j MASQUERADE
# enable IP forwarding sudo sysctl -w net.ipv4.ip_forward=1
#connect to USB Armory via ssh - password: usbarmory ssh usbarmory@10.0.0.1
#install Lynx Web browser on USB Armory sudo apt-get install Lynx
#run Lynx sudo Lynx
References
- https://genode.org/documentation/articles/trustzone
- https://www.f-secure.com/en/consulting/foundry/usb-armory
- https://inversepath.com/usbarmory_mark-one.html
- https://github.com/f-secure-foundry/usbarmory/wiki
- https://github.com/f-secure-foundry/usbarmory/wiki/Host-communication
- https://trac.torproject.org/projects/tor/wiki/doc/TransparentProxy