USB Hacking
Zusammenfassung
Description what this documentation is about.
O.MG Kabel
- Operating system: Ubuntu 18.04 bionic amd64
- Packages: git emacs
In order to complete these steps, you must have followed Some Other Documentation before.
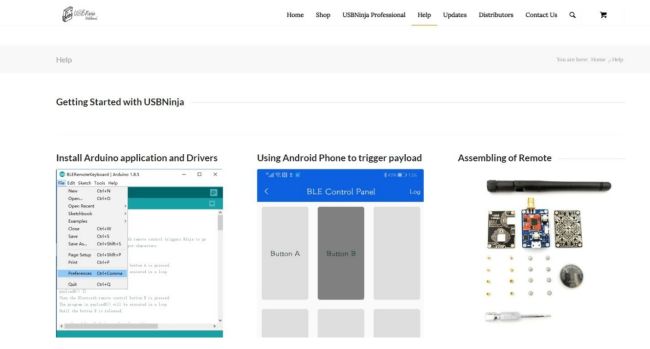
O.MG Kabel Setup
Step 1
Enter these commands in the shell
echo foo echo bar
Step 2
USBNinja Kabel
Das USBNinja Kabel ist ein Informationssicherheits- und Penetrationstest-Tool. Es ermöglicht das Ausführen von Payloads beim Anschließen des USB Kabels, indem es vortäuscht ein HID Gerät zu sein wie zum Beispiel eine Tastatur oder eine Maus. Die Programmierung des Kabels erfolgt über die Arduino IDE, was eine einfache und benutzerfreundliche Methode für die Verwendung von USB Ninja darstellt.
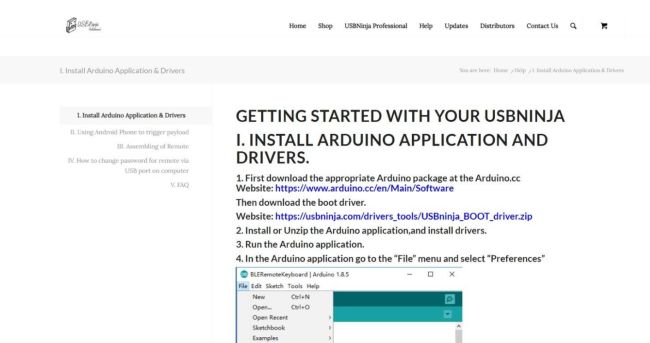
USBNinja Cable Setup
Step 1
To start with the USB NINJA cable, it is necessary to first access the official website at https://usbninja.com/help/
Step 2
Then, it is essential to strictly follow the steps described on the USBNinja website
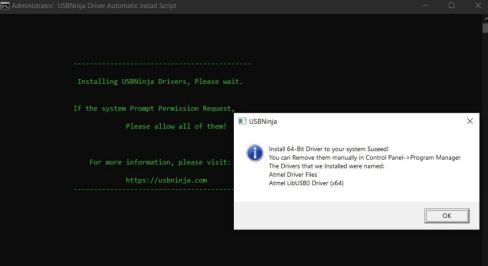
Step 3
After downloading the required boot driver and the Arduino IDE, it is imperative to run both as administrator to avoid future conflicts and then proceed with the installation
Step 4
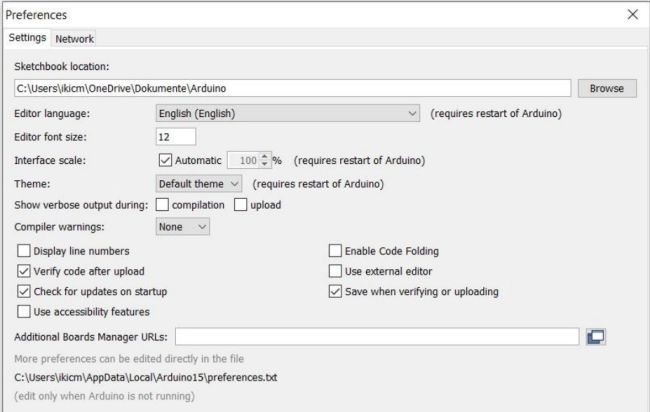
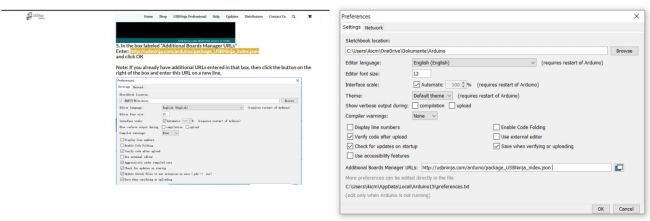
Next, in the Arduino IDE, go to "Preferences" and add the required link
Step 5
The URL for downloading the required JSON file can be easily found on the USB Ninja website. The link simply specifies the location for the download.
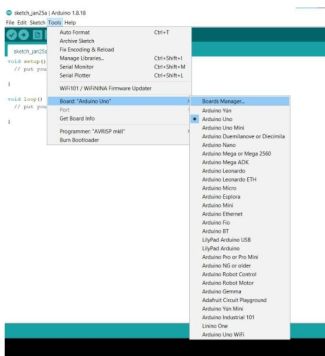
Step 6
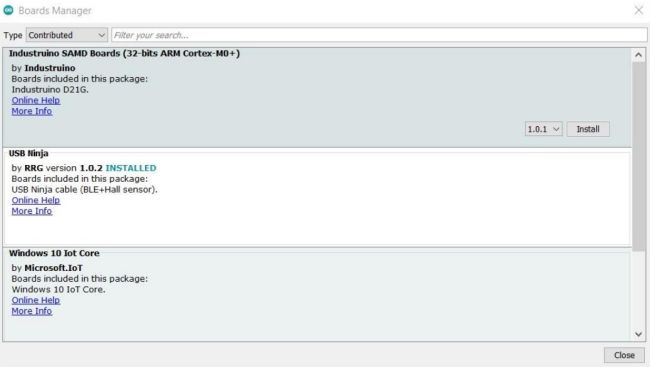
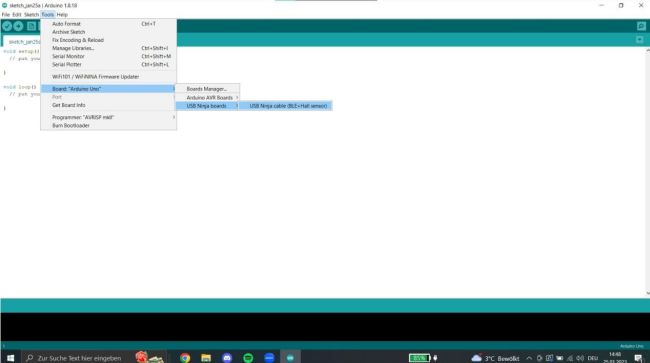
Next, we will open the Board Manager within the Arduino IDE and download the required board for the NINJA cable
Step 7
Finally, we simply select the previously downloaded board for the NINJA cable
Demonstration
Dein OMG Cable Angriff mit der Mail
Scenario
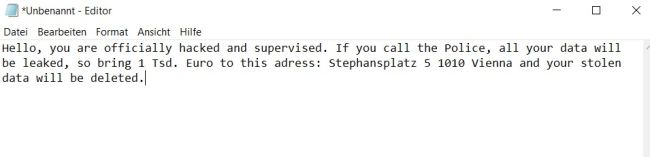
Imagine a hypothetical scenario: Our USB NINJA cable could pose potential dangers. Suppose someone is at an airport and wants to charge their laptop or smartphone. They find a public charging station with USB ports as well as accessible USB cables that can be connected to their laptop. Without thinking, the person connects the charging cable. As soon as the NINJA cable is connected, a threatening message appears on the screen, manipulating the user and causing them to follow the attacker's instructions. This is a typical attack through social engineering.
Präventive Maßnahmen
- Operating system: Ubuntu 18.04 bionic amd64
- Packages: git emacs
In order to complete these steps, you must have followed [[Some Other Doc