Wireshark
Summary
Wireshark is one of the most famous network protocol analyzers. It is a powerful multi platform open source tool, that can analyze network traffic on all possible network interfaces, like Ethernet, Wi-Fi, Bluetooth, local Loopback and VMware Adapters and even USB. The Wireshark project was founded 1998 by Gerald Combs, under the name of 'Ethernal' and gets continuously further developed by volunteers, network professionals and enthusiasts around the globe. In 2006, Wireshark was created from a fork of the program Ethernal. Version 1.0 was released in 2008. Before that, only expensive and proprietary solutions were available. Today Wireshark provides a wide set of features including:
- Capturing network traffic
- Filter and visualise the traffic
- Safe and open captured traffic in files
- Import and export other capture file formats
Therefore Wireshark is used to troubleshoot network problems, examine network security, test network applications and for educational purposes. It runs on all popular computing platforms, including Unix, Linux, and Windows. It uses Qt, a graphical user interface library, and libpcap and npcap as packet capture and filtering libraries. You can use it also to analysis imported packet capture savings from other non-graphical packet capture programs like tcpdump or tshark.
The application is free to download from the Wireshark website and is published under the GNU General Public License. A wizard leads trough the installation process. Npcap has to be installed to capture network traffic, additionally USBpcap can be installed, to capture USB traffic. Npcap is a packet sniffing driver copyrighted by the Nmap Project. Linux users can find Wireshark in the package repositories.
Functionality
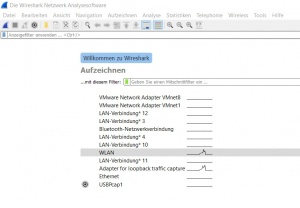
After starting the Wireshark application, it automatically scans for all available interfaces. In Figure 'Start screen' you can see the listed interfaces with a preview of the network traffic.
Wireshark can display packets sent and received over a network - connected to the computer. By clicking on 'Aufzeichnen' or 'Capture' above the interface list, the user interface menu opens.
Wireshark User Interface
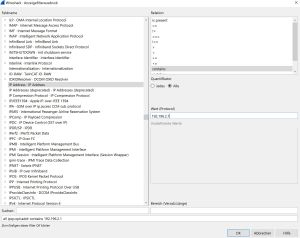
The user interface of Wireshark is divided into five parts:
- The first part contains a Menu Bar and the options displayed below it (red). This part is located at the top of the window. The File and Capture menu options are commonly used in Wireshark. The Record menu is used to start the recording process. And the File menu is used to open and save a capture file.
Among other things, you can define various rules with a few mouse clicks, which can be helpful, for example, the Packet Colorization.
- The second part is the Packet List Window (blue). It determines the packet flow or captured packets in the network. It contains the packet number, time, source, destination, protocol, length and information. Several other columns can be added as needed. The packet list can be sorted, by clicking on the column name.
- Next comes the Packet Header Detail Window (orange). It contains detailed information about the components of the packets. The log information can also be expanded or minimized as needed.
- The Bottom Window is the Package Contents window (black), which displays the contents in ASCII and hexadecimal format.
- Finally, there is the Filter Box (green) located at the top of the display. The captured packages on the screen can be filtered by any component that meets your requirements, as shown in the following chapter.
Capture and Display Filter
The capture process starts by double clicking a interface or select one and click on the blue fin icon in the menu bar.
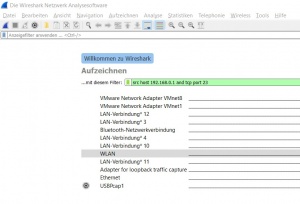
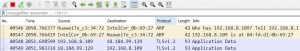
The Capture Filter is set before starting a packet capture and cannot be modified during the capture. It is more limited than the display filter and used to reduce the size of raw capture data. The filter can be entered in the text-field above the interfaces before the capturing is started. The Capture Filter has an own syntax described below. It only supports combinations of the listed primitives. An example is shown in figure 'Capture Filter'. The filter captures only packets which source IP address is 192.168.0.1 and the TCP port 23
Protocol selection [tcp|udp]
IP address [src|dst] [host]
Port number [port]
Operations [and|or] [less|greater] [not]
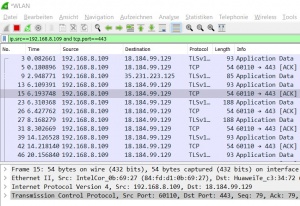
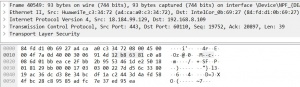
The Display Filter only filters the output on the screen. But can be modified during the capture process and also when analysing a saved capturing. So it's more flexible and can be adjusted to current needs. It's entered during a capturing in the above text field as shown in figure 'Display Filter'.
The Display Filter has a different syntax than the Capture Filter. Probably, because Wireshark is developed by many different developers, who add single features. The filter displays only packets which source IP address is 192.168.8.109 and the TCP port 443. As shown below, the Display Filter offers more possibilities to filter packets.
MAC address [eth]
L3 Protocol [ip|ipv6]
L4 Protocol [tcp|udp]
IP address [src|dst] [host]
Port number [port]
Operations [and|or|xor] []not|in]
Comparison Operator [==|!=|<|<=|>=|>]
Slices [x:y]
Function [upper|lower|len|count|string]
A more detailed list with possible filter expressions can be found in the Wireshark User Guide or under "Analyse/Anzeigefilter" or "Analyse/Anzeigefilterausdruck".
Analyze
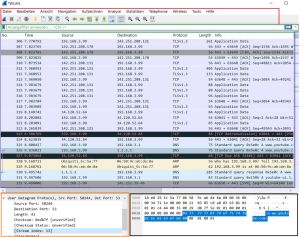
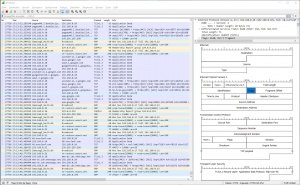
During the capture, a list of all incoming packets is displayed and you can start investigating traffic while it is in the process of capturing. In Figure 'Packet List', you see Wireshark in the middle of a capture. Three panes are worth looking at in the Wireshark window, thus are shown in figures 'Packet List' and 'Packet Details'. The top is for operation, such as starting/stoping capture process. The middle is the list of headers and the bottom pane shows the raw data, this includes a hexadecimal dump of each byte as well as an ASCII decode of those bytes on the right-hand side. Not all of the bytes can be decoded to a printable ASCII value, which is why you may see a lot of dots (.), that just indicates that there is a byte there but it can't be printed, see in Figure 'Packet Details'. The columns are described as follows:
- No. stands for the packet number, which Wireshark starts at zero, to make it more readable.
- Time shows the seconds since the capture started.
- Source is the packet source IP- or MAC-address.
- Destination is the packet destination IP- or MAC-address.
- Protocol stands for the used transport protocol.
- Length is the packet length in Bytes.
- Info shows the packet information, which Wireshark extracts automatically.
In the packet details, shown in figure 'Packet Details', you can see all headers from the different OSI Layers. In this example the TLS Application Data is encrypted and unreadable. From the TCP header you can read the source and destination port, sequence and ACK numbers, set flags, the size and the checksum. From the IP header you can read the version, length, flags, the TTL, the encapsulated protocol (TCP), checksum and source and destination IP address. From the Ethernet Header you can read the source and destination MAC address, the frame number and lengtha and the encapsualted protocols.
Below the packet details, is the packet shown in Bytes. Mostly not very human friendly to read. To change that, the configuration and other tips are shown in the next paragraph.
USBPcap
USBPcap is a product of Wireshark that allows sniffing USB traffic. It captures data from USB request blocks (URBs), which are transmitted in I/O request packets (IRP). These packets are then represented as frames.
Note: the packets and frames of USBPcap do not conform to the USB specifications and therefore differ.
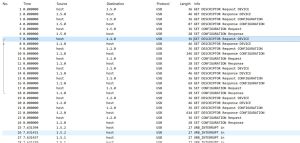
When sniffing USB traffic, ”raw data” - e.g. packets generated by a mouse/keyboard or any other USB device - is captured. Network interfaces that are connected to a host via a USB cable are handled specially. Here the operating system converts the raw USB packets into Ethernet packets and provides a network interface. In the figure above "USBPcap packet list window" is an example using a keyboard: Up to no. 25 it can be clearly seen that the timer is set to 0. In this phase, various packets are exchanged (request-response) to couple the keyboard to the computer. After the keyboard has been successfully coupled, a few letters are entered into the keyboard. These inputs can be seen under ”URB INTERRUPT in”- IN means from device to host, OUT means from host to device. Under the column Protocol, you can see that the used protocol is USB.
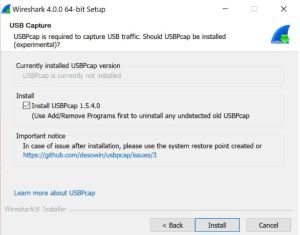
Side Note: If you already have Wireshark installed but you are missing USBPcap and you are ready now, you can easily install it afterwards as shown in the following Figure (USBPcap_installation).
Limits of USBPcap: With USBPcap you only see the USB control transmission sent to the device after the device has been assigned its address. This means exactly, that only URBs passed between functional device object (FDO) and physical device object (PDO) can be captured.
Bus states (Suspended, Power ON, Power OFF, Reset, High Speed Detection Handshake), Packet ID (PID), duration of bus state and time used to transfer packet over the wire and Transfer speed (Low Speed, Full Speed, High Speed) are information you can only get when using hardware USB sniffer.
Not so well known Features
Here are some configurations listed to make Wireshark easier and clearer to read.
- Wide Screen - The default view of Wireshark is not adjusted for wide screen. To make a better use of the whole screen change the following. In the menu Edit/Preferences/Appearance/Layout use the fourth Pane order. For the third pane choose Packet Diagram, instead of Packet Bytes. The result is shown in figure 'Full Screen'. In the Packet Diagram, you can click on any field and the corresponding value is shown in the Packet Details.
- Time - By default the Time in the Packet List is set to seconds since the capture started. To make it easier to find specific packages, under View/Display Time Format, you can change it to Time of Day.
- Name Resolution - Also by default, DNS is not activated. Under View/Name Resoultion you can activate name resolution for phyiscal, network and transport addresses. The name resolution is the only active action, which is performed by Wireshark in an observed network.
- Open Connections - In the Statistics menu, under Conversations, you can see all open connections at once. Separated in the different Layers: Data Link (Ethernet), Network (IP) and Transport (TCP/UDP).
- ACL Rule Creation - In the Tools menu, under Firewall ACL Rules, you can create different ACL Rules. Dependent of the selected packet in the Packet List, it shows a combination of outbound/inbound allow/deny rules. And also for different systems like Cisco IOS, IP Filter, IP Tables and Windows Firewall.
- Credentials - Also in the Tools menu, under Credentials, Wireshark shows all credentials, which could be read automatically, and in which packet they were sent. This only works with unencrypted traffic, like Open Authentication.
- Follow traffic stream - The traffic you are interested in will often be spread across a number of incoming and outgoing packets. This can be quite frustrating when trying to view sensitive HTTP Request/Response pairs and most application level data in general. Fortunately Wireshark allows you to select a packet and view the entire TCP stream it belongs to. Inbound and outbound traffic will be highlighted in red and blue to show the application layer communication without packet headers.
- Statistics - This menu contains items to display various statistics windows, including a summary of recorded packets, a display of protocol hierarchy statistics and more. For example, the tab "Protocol hierarchy" displays a tree of all logs listed in the acquisition process. This is useful for determining the types, amounts, and relative proportions of protocols within a trace.
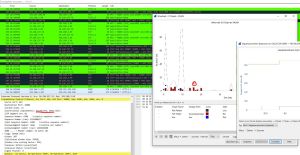
The tab Conversations generates for each line of the list the statistical value of a particular "dialog". And most importanly the tab "Flow Graph". The Flow Graph Generates a sequence graph for the selected traffic. This is useful for understanding seq. and ack. calculations. The tab "Packet lengths" displays the properties of the different packet lengths determined in the network. A very interesting tab, is the I/O Graph. It presents a graphical representation of the captured packets. During the process you can also apply filters.
.
Limits
Even tough, Wireshark is a powerful network analyzer, it also has its limits, which are listed below.
- No Attack Software - Wireshark can capture and analyze the traffic of specific interfaces. But it cannot manipulate any packets or send own packets to temper with legit connections. So it's no tool for Man-In-The-Middle or any other attacks. As already stated, the only actions taken by Wireshark is name resolution (DNS).
- No IDS - Wireshark only runs if you start it and shows the incoming and outgoing traffic in the user interface. But the analysis is left to the user. Wireshark has no built in scan engine or alert system. So it cannot be seen as Intrusion Detection System.
- No Decryption - Wireshark can not decrypt any captured traffic. Encrypted traffic like TLS is shown as unreadable characters. Also if you hold any public or private keys, they can not be applied in the Wireshark application to decrypt the traffic. So Wireshark can analyse unencrypted traffic only.
- Administrative privileges - Like tcpdump, Wireshark will put the network interface into promiscuous mode to capture all of the packets that pass by the interface. Putting the interface into promiscuous mode, as it is a hardware-related function, requires administrative access. Therefor there are issues running Wireshark to perform captures because it can require administrative privileges. This can lead to the potential to exploit vulnerabilities in Wireshark and provide administrative-level access to the attacker. Therefore, it's better to do it with limited permissions rather than allowing the attacker to have complete run of the system.
Comparison to Tcpdump and Tshark
Beside Wireshark with its graphical user interface, Tcpdump is a well known command line tool for netowrk traffic analysis. In this chapter, Tcpdump will be presented and compared to Wireshark, based on its performance and features. The focus of this list are the differences of these two tools. The similarities in traffic capturing are well known.
Tcpdump is a lightweight network traffic capturing tool working on the command line. It's available for free on most UNIX and Windows systems under the BSD license. It also uses the libcap library to capture packets and creates dumps of the packet data in raw format. The analysis is left to the user, which may be challenging for beginners. To control the output and help analyzing it, Tcpdump provides a wide set of parameters. A full list is available at the Tcpdump manual.
It offers a command line interface, which makes it more lightweight. An important feature is, that Tcpdump can decrypt IPsec packets, if the needed secrets are provided. Wireshark can't decrypt any traffic. Tcpdump shows packets directly in the terminal window, without buffering them and by default. Wireshark always buffers packets, which can show them delayed. In terms of needed resources, Tcpdump is much more undemanding compared to Wireshark. Wireshark needs ten times more memory and hundreds of times more energy than Tcpdump. However, it should be noted that Wireshark accesses the processor much more often, has more wakeups, which leads to more accurate and up-to-date data, but requires more resources
Wireshark offers a graphical user interface and colouring of different protocols with different color schemes (Packet Colorization). Tcpdump, on the other hand, does not distinguish between different packet types, i.e. the user must classify the individual packets himself. It's also very easy to apply different filters to captured traffic. Wireshark can save dumps in different files, like ring buffer, while Tcpdump can write one file only. As stated before, it can show current traffic statistics, which Tcpdump can't. Also Wireshark is 2-3% faster at capturing traffic. This can make a difference at high data rates. The biggest advantage of Wireshark is the flexibility in terms on analyzing and saving dumps. This can be changed in Wireshark after the capturing (= in real time), while in Tcpdump everything has to be specified before you start capturing and can't be changed afterwards. Another significant advantage of Wireshark over Tcpdump is, that Tcpdump- in monitoring mode, discards a large number of packets starting from 1000 packets per minute. This is actually a problem when scanning the network thoroughly, because when detecting malicious packets, it makes a difference whether all packets are scanned or not. Wireshark, on the other hand, manages to capture more packets in the same amount of time.
Tshark compared to Wireshark; we see that Wireshark also differs here on the topic of graphical interfaces. While tshark only presents you with a summary and the most important information, mostly from the packet headers, Wireshark contains a set of modules called dissectors. These dissectors are what make Wireshark so valuable.
This comparison shows that both tools have advantages and disadvantages. Wireshark is the more flexible and clearer tool. The GUI makes it easier to understand and very suitable for academic purposes. Tcpdump is more suitable for professional usage, as the dump needs to be clearly specified and it needs less resources. By the features it cannot be said, which tool is the better one. It depends on the use case and the environment to analyze. And also of the knowledge of the user, since Wireshark is more user friendly for academic purposes.
References
- https://www.wireshark.org/
- https://nmap.org/
- https://www.tcpdump.org/
- Comparative study of two most popular packet sniffing tools-Tcpdump and Wireshark - https://ieeexplore.ieee.org/document/8319360/
- Packet tracing and analysis of network cameras with Wireshark - https://ieeexplore.ieee.org/document/7916510/
- Network Traffic Monitoring and Analysis Using Packet Sniffer -
https://ieeexplore.ieee.org/document/8742369/
- Piyush Goyal and Anurag Goyal. Comparative study of two most popular packet sniffing tools-tcpdump and wireshark. in: IEEExplore-1ieee.org, 2017.- https://ieeexplore-1ieee-1org-1tn53mdiy09fc.han.fh-campuswien.ac.at/document/8319360, Accessed: 2022-09-14.
- OWASP. Wireshark basics. in: OWASP.org, 2019.- https://owasp.org/www-pdf-archive//Owaspwireshark.pdf, Accessed: 2022-09-14.