Difference between revisions of "Wireshark"
| Line 30: | Line 30: | ||
Port number [port] | Port number [port] | ||
Operations [and|or] [less|greater] [not] | Operations [and|or] [less|greater] [not] | ||
[[File:Wireshark_Display.jpg|thumb|Display Filter]] | |||
The '''Display Filter''' only filters the output on the screen. But can be modified during the capture process and also when analysing a saved capturing. So it's more flexible and can be adjusted to current needs. | |||
It's entered during a capturing in the above text field as shown in figure 'Display Filter'. | |||
The Display Filter has a different syntax than the Capture Filter. Probably, because Wireshark is developed by many different developers, who add single features. The filter displays only packets which source IP address is 192.168.8.109 and the TCP port 443. As shown below, the Display Filter offers more possibilities to filter packets. | |||
MAC address [eth] | |||
L3 Protocol [ip|ipv6] | |||
L4 Protocol [tcp|udp] | |||
IP address [src|dst] [host] | |||
Port number [port] | |||
Operations [and|or|xor] []not|in] | |||
Comparison Operator [==|!=|<|<=|>=|>] | |||
Slices [x:y] | |||
Function [upper|lower|len|count|string] | |||
A more detailed list with possible filter expressions can be found in the Wireshark User Guide. | |||
== References == | == References == | ||
Revision as of 14:52, 15 January 2021
Summary
Wireshark is one of the most famous network protocol analyzers. It is a powerful multi platform open source tool, that can analyze network traffic on all possible network interfaces, like Ethernet, Wi-Fi, Bluetooth, local Loopback and VMware Adapters and even USB. The Wireshark project was founded 1998 by Gerald Combs, under the name of 'Ethernal' and gets continuously further developed by volunteers, network professionals and enthusiasts around the globe. Version 1.0 was released in 2008. Before, only expensive and proprietary solutions were available. Today Wireshark provides a wide set of features including:
- Capturing network traffic
- Filter and visualise the traffic
- Safe and open captured traffic in files
- Import and export other capture file formats
Therefore Wireshark is used to troubleshoot network problems, examine network security, test network applications and for educational purposes.
The application is free to download from the Wireshark website and is published under the GNU General Public License. A wizard leads trough the installation process. Npcap has to be installed to capture network traffic, additionally USBpcap can be installed, to capture USB traffic. Npcap is a packet sniffing driver copyrighted by the Nmap Project.
Functionality
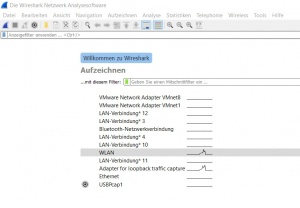
After starting the Wireshark application, it automatically scans for all available interfaces. In Figure 'Start screen' you can see the listed interfaces with a preview of the network traffic.
By clicking on 'Aufzeichnen' or 'Capture' above the interface list, the interface menu opens. The first tab shows the interfaces including their MAC Addresses, which helps identifying the right one. Also Pipes and remote interfaces can be configured. The second tab shows the output options. Here you can save the captures automatically in files, according to different rules. The third tab offers additional options for display and name resolution.
Capture and Display Filter
The capture process starts by double clicking a interface or select one and click on the blue fin icon in the menu bar.
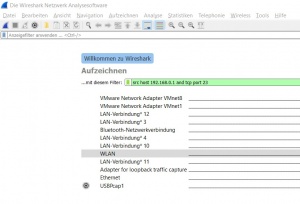
The Capture Filter is set before starting a packet capture and cannot be modified during the capture. It is more limited than the display filter and used to reduce the size of raw capture data. The filter can be entered in the text-field above the interfaces before the capturing is started. The Capture Filter has an own syntax described below. It only supports combinations of the listed primitives. An example is shown in figure 'Capture Filter'. The filter captures only packets which source IP address is 192.168.0.1 and the TCP port 23
Protocol selection [tcp|udp] IP address [src|dst] [host] Port number [port] Operations [and|or] [less|greater] [not]
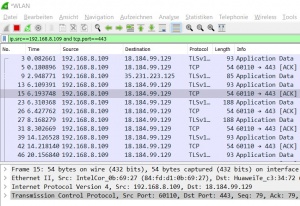
The Display Filter only filters the output on the screen. But can be modified during the capture process and also when analysing a saved capturing. So it's more flexible and can be adjusted to current needs. It's entered during a capturing in the above text field as shown in figure 'Display Filter'.
The Display Filter has a different syntax than the Capture Filter. Probably, because Wireshark is developed by many different developers, who add single features. The filter displays only packets which source IP address is 192.168.8.109 and the TCP port 443. As shown below, the Display Filter offers more possibilities to filter packets.
MAC address [eth] L3 Protocol [ip|ipv6] L4 Protocol [tcp|udp] IP address [src|dst] [host] Port number [port] Operations [and|or|xor] []not|in] Comparison Operator [==|!=|<|<=|>=|>] Slices [x:y] Function [upper|lower|len|count|string]
A more detailed list with possible filter expressions can be found in the Wireshark User Guide.
References
- https://www.wireshark.org/
- https://nmap.org/
- https://www.tcpdump.org/
- Comparative study of two most popular packet sniffing tools-Tcpdump and Wireshark - https://ieeexplore.ieee.org/document/8319360/
- Packet tracing and analysis of network cameras with Wireshark - https://ieeexplore.ieee.org/document/7916510/
- Network Traffic Monitoring and Analysis Using Packet Sniffer - https://ieeexplore.ieee.org/document/8742369/