Wormhole and Blackhole DoS Attack
Description
The two attacks pretend to have an efficient route between two distanced nodes, so that they get the mainly used rout and can compromise network traffic.
Wormhole
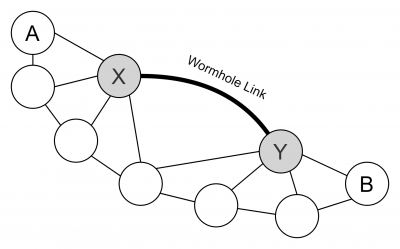
The Wormhole attack is dangerous even though the data stays confidential, encrypted and authenticated. The Wormhole is launched by planting two or more nodes in a network that are connected by a high-speed link called tunnel. Distanced nodes which need to use an multi hop route to communicate with each other get tricked in to using the wormhole link, because it seems like a one hop route between the two malicious nodes. The seemingly one hop route is achieved by encapsulating the transferred packets that the hop count does not get incremented. The attacker can now filter packets of a certain nodes or collect statistics about the network traffic, but he is still not able to read or alter the payload.
Blackhole
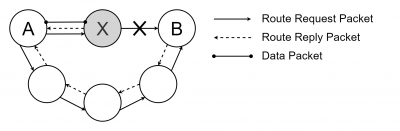
The Blackhole is based on the same principal to become a used link. The difference is that a black hole drops any traffic that it is meant to be delivered. Furthermore, the Blackhole sends reply packets to stay undetected. The Grayhole, an extension of the Blockhole, operates much more inconsiderable because it switches between two modes to raise less suspicion. Grayholes that operate in first mode drop packets of certain nodes and forward the data of the other as it is meant to be. In the second mode it works maliciously for some periods and the other time it operates normal.
References
- IEE 2012: DoS Attacks in Mobile Ad Hoc Networks: A Survey