Difference between revisions of "Bluetooth Pentesting Tools (HW/SW)"
| Line 49: | Line 49: | ||
btmon --write ~/Documents/bttraffic.snoop | btmon --write ~/Documents/bttraffic.snoop | ||
These files can be viewed and analysed with 'Wireshark' which is also preinstalled on kali linux. Alternatively you can capture bluetooth traffic directly with Wireshark: | |||
[[File:Wiresharkhciscan.PNG]] | |||
Enter these commands in the shell | Enter these commands in the shell | ||
| Line 63: | Line 67: | ||
* The Baroque Cycle | * The Baroque Cycle | ||
== | == Bluetooth Pentesting Hardware == | ||
For hardware pentesting devices like the Ubertooth one please see following documentations: | |||
[[ | * [[Bluetooth_Hacking_Ubertooth]] | ||
[[ | * [[Bluetooth_Sniffing_with_Ubertooth:_A_Step-by-step_guide]] | ||
== Courses == | == Courses == | ||
Revision as of 17:23, 17 February 2020
Summary
This article describes various tools for bluetooth penetration testing and aims to provide an overview to choose the right tool for a use case.
Requirements
- Operating system: Kali Linux amd64 2019.2
- Packages: Individual shown for each tool
In order to use hardware pentesting devices a dedicated installation of kali linux is recommended but it is also possible to use hypervisors which are capable of passing USB devices from the host- to the guestsystem e.g. VMWare Workstation or the free hypervisor VirtualBox.
Information gathering
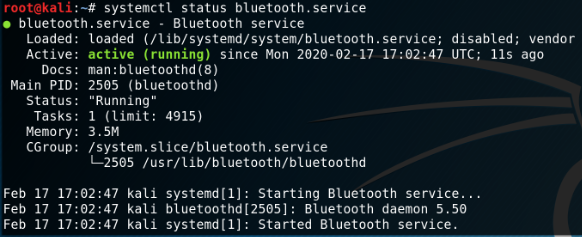
The offical linux bluetooth protocol stack BlueZ is already installed on kali linux but can be installed on other linux maschines with:
apt install -y bluez bluez-utils systemctl start bluetooth.service systemctl status bluetooth.service
Scanning for bluetooth devices
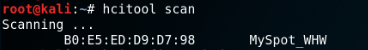
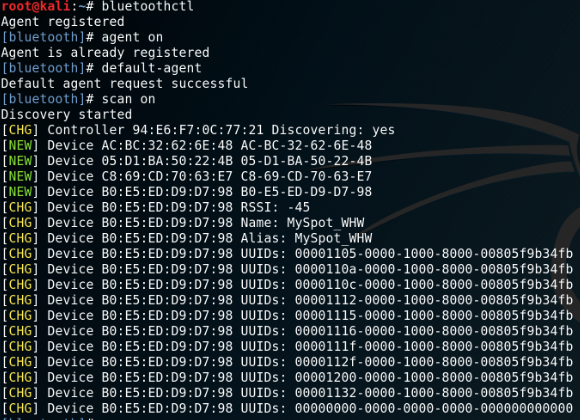
To start with penetration testing we need to gather information about our environment, for this purpose scan for available bluetooth devices with the included packages 'hcitool' or 'bluetoothctl'.
First check if your bluetooth device is available:
hciconfig
Scan for BR/EDR Bluetooth devices with hcitool:
hcitool scan
Alternatively you can use bluetoothctl:
In order to scan for BLE devices use:
hcitool lescan
Capturing bluetooth traffic
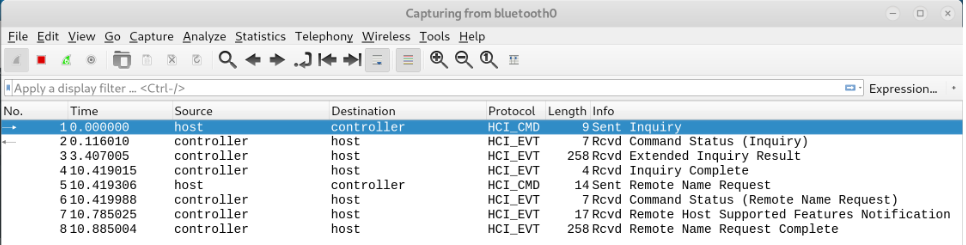
With the preinstalled package 'btmon' it is possible to capture traffic between the HCI and the controller:
btmon --write ~/Documents/bttraffic.snoop
These files can be viewed and analysed with 'Wireshark' which is also preinstalled on kali linux. Alternatively you can capture bluetooth traffic directly with Wireshark:
Enter these commands in the shell
echo foo echo bar
Step 2
Make sure to read
- War and Peace
- Lord of the Rings
- The Baroque Cycle
Bluetooth Pentesting Hardware
For hardware pentesting devices like the Ubertooth one please see following documentations:
Courses
- A course where this documentation was used (2017, 2018)
- Another one (2018)