Defend The Web

Defend The Web is a Capture the Flag Website that teaches topic about Cyber Security and offers users on-hand-training for their theoretical skills. A free account is needed to access every section of the website. This can be either done by registering a new one from scratch or by using one of the available Single Sign On Providers (SSO Providers) Twitter (aka X), Google or GitHub. After logging in, the user gets redirected to a dashboard that offers information about new content in the articles and community sections as well as the progress in solving CTFs and the user's current level. Every user can earn medals by finishing challenges, participating in the community, writing articles and other actions on the website. [2]
Overview
The landing page after logging in is the dashboard which consists of three main parts A) Articles, B) Playground and C) Community.
Articles
The article section consists of nine topics. Each article has a read time that depends on the length of the text as well as a counter of how many people have read it. The following list contains the topics and the number of articles within each topic at the time of writing. Topics in bold are directly accessible through the sidebar navigation within the dashboard.
- Coding (11)
- Hacking (21)
- Privacy (2)
- Encryption and Steganography (9)
- Lock Picking (2)
- Network security (7)
- Phreaking (1)
- Talks / videos (11)
- Miscellaneous (13)
Playground
When navigating to the playground, the user is greeted with a list of all levels as well as a recommendation of the next level that may suit the current experience level. The challenges can be filtered using 12 categories. Every challenge has a level which is one of bronze, silver or gold, to show the complexity of the challenge. Statistics on how many users have attempted a challenge and how many of them completed it are available after clicking on one of them. Information about who and when the challenge was solved first is available as well as who and when it was completed lastly. All challenges, except those in the category realistic, are kept in the same style, requiring the user to enter data into one or more text fields and clicking a button to send the solution. From a usability perspective it is simple to use and easy to understand, focusing only on the objectives that need to be solved. Below the challenge itself, a notes field is available that gives the user the option to write down things that didn't work or ideas on how to solve the challenge to find those information at the next attempt. This notes are only visible to the user who wrote them and cannot be shared.
Community
A forum and Chat function can be found in the community section as well as a function to exchange private messages between users. At the time of writing, the chat function was not working, but a workaround was mentioned in the forum. [3]
Challenge Write-Up
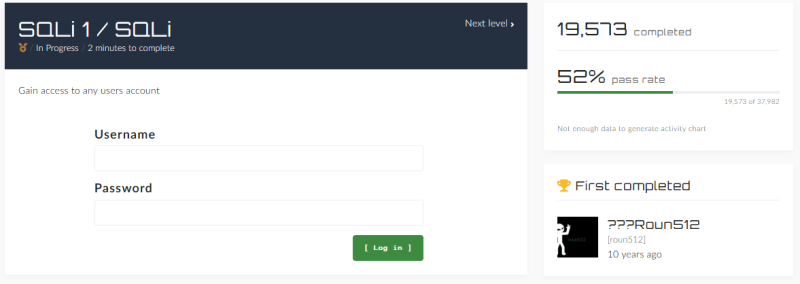
To show how the website works we will play one challenge from start to end. For this demonstration, we chose the challenge 'SQLi 1 / SQLi', which is a SQL injection CTF. As most challenges, we are facing a login screen with a short description of the objective. In this case we have to 'Gain access to any users account' by providing an username and a password or by exploiting the site. We can also observe that more than 19,000 users have completed this challenge and that only 52\% of the users that attempted this challenge have actually completed it.
To solve this challenge we need some knowledge about SQL injections in general. Before frameworks made it easier and safer to write SQL statements, they were mostly written as strings and the variables were replaced by the script engine. This way an attacker could insert malicious symbols that change the way the query works. The following PHP code snippet uses unchecked user input and inserts it in a SQL query string.
$username = $_POST['username'];
$password = $_POST['password'];
$q = "SELECT * FROM users WHERE user='$username' and pass='$password'";
$result = mysqli_query($connection, $q);
$count = mysqli_num_rows($result);
if($count == 1) {
// User successfully logged in
}
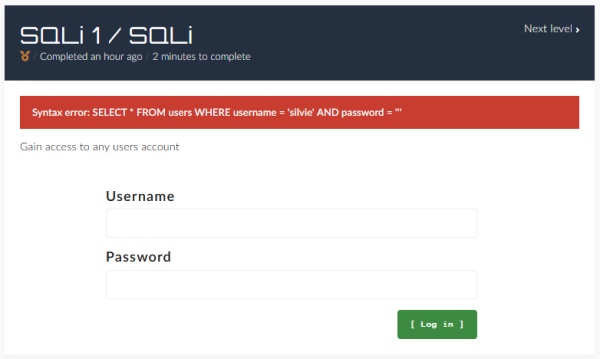
As we suspect a similar query to be used in the background of the challenge, we use ambiguous characters to get more information. Using the username "silvie" and the password ' (a single quote), we get back the error message "Syntax error: SELECT * FROM users WHERE username = 'user' AND password = '''". We can now see the used query and that the single quote invalidated it.
For the exploit itself we can now use any username, as the script will not check this anyway after our changes, and the password "' OR 1=1;". The query will be rendered in the background to "SELECT * FROM users WHERE username = 'silvie' AND password = OR 1=1;'". The query now evaluates two parts, the one before the OR and the other after. The first one will probably fail because the user may not exist or even if it does, the password will probably not be empty. The second part will always be true, because 1 equals 1. The single quote at the end will be ignored, because we added a semicolon at the end that finishes the query.
Alternatives
Root Me
The CTF platform Root Me has established only two years after Defend The Web in 2010, but offers already more than 540 challenges. [4]
Hack The Box
Another alternative is Hack The Box, which offers over 500 challenges [5] but also attracts by doing community events all over the world. [6]