Radio-Frequency Identification
Introduction
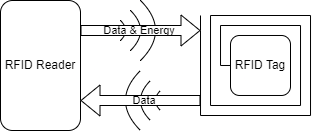
Radio-Frequency Identification (RFID) is a communication technology, that uses electromagnetic waves to identify and track tags. A RFID system consists out of a tag, which is attached to an object, an reader, which extracts the information of the tag and an application, that uses the gathered information.
RFID-System
It consists out of three parts [1]:
- Tag
- Reader
- Application
The focus will be set on the tag and the reader, not on the application.
Reader
A reader is responsible for initiating the communication with a tag, in case of a passive tag the reader also supplies the energy needed to operate the tag.
A reader consists out of to components:
- A control unit
- A high-frequency interface
Control Unit
The control unit is responsible for
- Communication with the application
- Communication with the tag
- Coding and decoding of the signal
- Anti-collision algorithm
- Encryption and decryption of data sent between reader and tag
- Authentication between reader and tag
High-frequency interface
The high-frequency interface is responsible for
- Generation of strong high-frequency signals to activate the tag and supply it with energy
- Modulating the transmission signal to send data to the tag
- Receiving the radio frequency signals transmitted by a tag and converting them back into original data
Tag
RFID tags are divided into six categories by EPC Global[2]. A tag in one category has all the capabilities of the subordinate categories. This means that tags are backward compatible
Passive tags, which have no built-in energy source and draw their energy from the reader's radio waves, are assigned to classes 0 to 3. Active tags, with their own energy source, are assigned to class 4. Class 5 is reserved for tag readers and active tags that can read other tags.
- Class 0: These tags are passive and work with UHF. These tags are pre-programmed in the manufacturer's factory and can no longer be reprogrammed, the information can no longer be changed.
- Class 1: Class 1 tags use HF radio waves. In contrast to class 0 tags, class 1 tags and higher can be programmed by the user. However, in class 1, tags can only be described once.
- Class 2: Unlike class 1, class 2 tags can be written to multiple times.
- Class 3: Read-write with integrated sensors that are able to detect parameters such as temperature, pressure and movement; can be semi-passive or active. Semi-passive means that they occupy an energy source but cannot initiate communication with other tags or readers.
- Class 4: Class 4 tags have their own energy source and can initiate communication with other tags or readers, so they are active tags.
- Class 5: Class 5 tags are the most advanced, they can transfer energy to passive tags and communicate with readers and tags of any class, so they can also be classified as readers.
Tag information
Four types of information can be stored on a transponder:
- Information to identify the tagged item: This category includes the identification data used to uniquely identify the tagged item. This includes user-defined fields such as bank accounts, product barcodes and prices, as well as predefined registers such as the Application Family Identifier (AFI) and the Data Storage Format Identifier (DSFID)
- Supplementary information on the object: Supplementary data includes further standard information such as Application Identifiers (AIs) and ANSI MH-10 Data Identifiers (DIs), which enable further differentiation and specific information on the tagged item
- Control data: Control data could include information about the configuration of the tag, such as the settings for the security controls, including mechanisms that restrict reads or writes to user memory blocks and special registers that contain the AFI and DSFID values
- Manufacturer data: The unique identifier (UID), transponder type, manufacturer and manufacturing data can be stored in this category. This information can be specific to each manufacturer and transponder type.
The first two categories, identification and supplementary information, are present on all tags as they provide essential information for identifying and supplementing the tagged item. Categories three and four, control data and manufacturer data, can vary depending on the manufacturer and contain specific information for configuring the tag and identifying the manufacturer.[3]
RFID Attacks
In contrast to attackers on the Internet, who can always attack a machine on the Internet, a server is always online and responds to requests from all over the world, an attacker of an RFID system does not have constant access. He must be physically close to the tag that is to be read. Or must be present during a transaction. Security models must be adapted to these facts. Further more, cheap RFID tags cannot perform standard encryption.
The challenge is therefore to create a realistic security model that reflects the threats and capabilities of reality as accurately as possible.
Attack methods
Cloning
There are two different types of cloning used to attack.[4]
- Simple RFID cloning: If an attacker gains physical access to an RFID tag, they can clone it. The advantage of cloning is that, unlike theft, the original tag does not have to be kept by the attacker. Since the owner can easily become aware that the original tag is missing in the event of theft, no changes are made to the tag during cloning. The cloned tag has the same access options as the original. This makes it much less likely that the victim will know that they have been victimized. Disadvantage, needs physical access to the card/tag, must copy it and then return it. There are various devices for copying the card.
- Distance RFID cloning: There are a large number of devices that can read and clone RFID tags at a distance. The range is limited to less than 1 meter, and the greater the range, the more expensive the devices become. There are devices that can store the read data on an SD card.
Man-in-the-middle attacks
For this attacks, the hacker positions himself between the RFID tag and the reader in order to influence or eavesdrop on the communication. We distinguish between the following attacks.
- Eavesdropping: An attacker can use devices or apps to intercept the communication between the RFID tag and the reader in order to capture the transmitted data.
- Replay attacks: In this attack, the attacker is in the vicinity of a communication between the RFID/NFC tag and a reader. The communication is recorded and can be replayed at a later time to the reader.
- Relay attack: In a relay attack, the communication between the RFID tag and reader is recorded and sent to a third device.
Data manipulation
An attacker who has access to an RFID/NFC device manipulates it so that false data or requests are sent.
Skimming
Skimming is the use of unauthorized readers to retrieve data from RFID tags or to start a transaction, for example with a mobile wallet.
Spoofing
The attacker creates fake RFID tags or readers to fool the system and gain unauthorized access.
Denial of Service (DoS)
These attacks aim to overload RFID systems and disrupt their function in order to prevent authorized access.
Side channel attacks
This involves analyzing the physical properties of the RFID system, such as power consumption or electromagnetic emissions, in order to derive confidential information.
Cryptanalytical attacks
These attacks aim to break the cryptographic mechanisms used to protect the data in RFID systems.
Physical attacks
These include methods such as physically destroying RFID tags or changing their internal structures in order to disrupt their function or obtain information.
Phone malware
A vulnerability was found in Android devices in 2019. Using NFC, it was possible to download software that is not offered in the Google Play Store. Normally, the smartphone warns in such a case. The download triggered by this vulnerability did not trigger these warnings, but the user still had to confirm the download. This vulnerability has now been closed.[5]
Physical shielding of the tag
To circumvent Electronic Article Surveillance (EAS), thieves use multi-layered aluminium pockets, creating a Faraday cage, to shield the tag from the reader.
Social Engineering
Social engineering is not a direct attack, but social engineering can be used to gain access to NFC or RFID devices, which makes it possible to clone them or steal information.
Tools
There are a lot of different tools to attack RFID-Systems. Well known tools are:
- Flipper Zero is a powerful and multi-functional tool specifically created for pentesting and device hacking purposes. This is a little gadget that has the ability to communicate with many wireless systems, such as RFID, NFC, and radio frequencies. Flipper Zero is very proficient in analysing and evaluating the security of RFID systems. It may be used for various activities like as duplicating RFID tags, intercepting communications, and investigating weaknesses in wireless protocols.[6]
- ChameleonMini is a specialised device designed to emulate and clone RFID tags, with a particular focus on contactless card technology. It is often used in security research to assess the resilience of RFID systems against cloning and spoofing attacks. The ChameleonMini is a versatile tool that can imitate several kinds of RFID tags and store different RFID identities. This makes it an effective device for researchers and security experts to evaluate and showcase the security risks associated with RFID technology.[7]
- The Keysy RFID Duplicator is a small and easy-to-use hardware device designed to replicate Mifare cards, which are widely used for access control, public transit, and payment systems. Users are able to replicate and retain numerous sets of RFID tag data, so gaining the ability to reproduce the same functionality as these cards. This tool is very valuable for assessing and showcasing weaknesses in access control systems that are based on Mifare technology, hence emphasising possible security hazards in RFID implementations of such systems.[8]
- The Proxmark3 RDV4 is a refined and condensed iteration of the Proxmark3. It was created specifically for the community of professionals that do penetration tests. The frequencies 125kHz and 13.56MHz are the defining characteristics. The device is equipped with several antennas and may be expanded using diverse modules.[9]
Security experts and researchers often use these tools to assess and scrutinise the security of RFID systems.
Security controls for RFID
This section addresses security measures that are relevant to the majority of implementations. It fails to consider the security aspects of RFID-enabled smart cards and payment systems. Furthermore, it omits any mention of security measures pertaining to conventional IT systems, such as network infrastructure, databases, and web servers, since they are already addressed by existing security prerequisites and standards. To ensure the security of the data collected by the RFID system, it is important to protect EPCIS servers that can be accessed over the Internet by trading partners. This can be done by implementing similar controls that are used for any other system accessible over the Internet, such as encrypting sensitive communications and implementing access control measures to prevent unauthorised access to data and systems. Various sources, including NIST's Computer Security Resource Centre (CSRC), provide guidelines on areas such as IT server, application, database, and network security.
Management controls
Management control is crucial for assessing risks, designing and acquiring systems, as well as certifying and evaluating security. Further eplaination of the management controls for RFID systems is provided below.
-
RFID usage guideline:
- Description of authorized and unauthorized use of RFID technology
- Should be consistent with the organization's privacy policy
- Required for all organizations using RFID technology
- Provides the framework for further security controls
- Challenge is to ensure compliance with the policy
-
IT security guidelines:
- Define measures to achieve high-level security objectives
- Cover RFID subsystems such as network, database and application security
- Necessary for all RFID implementations, especially enterprise subsystems
- Provide guidance for the design and management of RFID systems
- Require consistent implementation and enforcement
-
Minimization of sensitive data on tags:
- Prefers to store sensitive data in secure enterprise systems.
- Suitable for applications with tags that process sensitive or interpretable data.
- Prevents adversaries from obtaining information through scanning or eavesdropping.
- Challenge is the dependency on network availability.
Operational controls
Operational controls include various measures that are used in RFID systems. They range from access restrictions to operator training. The following points provide a detailed overview of these controls.
-
Physical access control:
- Enclosing critical areas with fences, doors and surveillance cameras.
- The aim is to prevent unauthorized access to RFID components.
- Limits the possibility for adversaries to compromise RFID data.
- Not applicable in publicly accessible areas.
-
Appropriate placement of tags and readers:
- Avoidance of unnecessary electromagnetic radiation
- Placement away from sources of interference and sensitive products
- Reduces the risk of interference and data breaches
-
Safe disposal of tags:
- Physical or electronic destruction of tags after use.
- Prevents adversaries from gaining access to data.
- Important for applications with data protection risks.
-
Training of operators and administrators:
- Providing skills and knowledge for compliance
- Important for all RFID implementations
- Training supports the correct use and maintenance of the system
-
Information label and notes:
- Provides basic information about the RFID system
- Important for applications where privacy is a concern
- Communicates risks and risk mitigation measures
-
Separation of duties:
- Distribution of system tasks to different roles
- Reduces the risk of fraud and malicious damage
- Important for applications with high value or internal security risks
-
Non-revealing identifier formats:
- Use of identifier formats that do not reveal any information
- Prevents opponents from obtaining information from the identifier format alone
- Important for applications where tag identification is a business risk
-
Fallback identification system:
- Provision of alternative identification methods in the event of system failure
- Applicable to all RFID applications
- Provides redundancy and security in case of emergency or system failure
Technical controls
Technical controls are essential for the security of RFID systems. These include measures for authentication and data integrity, for protecting the RF interface and for securing the data stored on the tags. \cite{NISTSP800-98}
- Authentication and data integrity
- Password authentication: Use of passwords to control access to tags. Complex password management and risks associated with wireless transmission are challenges.
- HMAC (Keyed-Hash Message Authentication Code): Use of HMAC for stronger authentication and data integrity. However, requires efficient key management and computing power on the tag.
- Digital signatures: Use of digital signatures to authenticate transactions. Requires a public key infrastructure (PKI) and is more memory-intensive than other methods.
- RF interface protection
- cover coding:Encryption of communication between reader and tag to prevent eavesdropping.
- encryption of transmitted data: Protection of data during transmission through encryption.
- Electromagnetic shielding: Use of shielding to control the propagation of RF signals and prevent unauthorized reading.
- Frequency selection: Selection of the appropriate frequency to avoid interference and provide optimum radio coverage.
- Adjustment of transmission characteristics: Control over transmission power and antenna alignment to minimize interference and radiation risks.v
- Temporary deactivation of tags: Option to temporarily disable tags to prevent unauthorized access.
- Tag activation switch:User control over the activation of tags to prevent unauthorized communication.
- tag query (polling):Periodic polling of tags to check their presence and state.
- Privacy on tags
- Tag memory access control: Password-protected locking functions to control read and write access.
- encryption of data at rest: Protection of the data stored on the tag by encryption.
- Kill function: Ability to permanently disable tags to protect them from unauthorized use.
- Tamper protection: Properties of tags that make tampering more difficult or visible.
References
- ↑ Xiaolin Jia, Quanyuan Feng, Taihua Fan, and Quanshui Lei, "RFID Technology and Its Applications in Internet of Things (IoT)," in Proceedings of the 2012 2nd International Conference on Consumer Electronics, Communications and Networks (CECNet), 2012, pp. 1282-1285, doi: 10.1109/CECNet.2012.6201508.
- ↑ EPC-RFID, "RFID Tags," Accessed: 2023. [Online]. Available: https://www.epc-rfid.info/rfid-tags. Note: RFID tags are classified as Class 0 through Class 5, depending on their functionality.
- ↑ Fotios Chantzis, Ioannis Stais, Paulino Calderon, Evangelos Deirmentzoglou, and Beau Woods, "Practical IoT Hacking: The Definitive Guide to Attacking the Internet of Things," No Starch Press, 2021, ISBN 978-1-7185-0091-4.
- ↑ Kolin Nielson and Sayeed Sajal, "The Art of RFID Hacking," in Proceedings of the 2023 Intermountain Engineering, Technology and Computing (IETC), 2023, pp. 328-333, doi: 10.1109/IETC57902.2023.10152251.
- ↑ https://nvd.nist.gov/vuln/detail/CVE-2019-2114
- ↑ https://flipperzero.one/
- ↑ https://github.com/emsec/ChameleonMini
- ↑ https://tinylabs.io/keysy/
- ↑ https://proxmark.com/proxmark-3-hardware/proxmark-3-rdv4