WiFi Security
Summary
This documentation explores WiFi security, covering the progression from WEP to WPA3. It explains how each protocol, from WEP to WPA2 and WPA3, addresses security vulnerabilities with enhanced encryption and authentication methods. The focus is on the handshakes of WPA2 and WPA3, pivotal for securing network connections. Additionally, it touches on frame aggregation and fragmentation for optimizing data transmission, while acknowledging associated vulnerabilities. The article also mentions the potential exploitation of these weaknesses by tools like Aircrack-ng and Driftnet, emphasizing the importance of robust security measures in wireless networks.
Basics
WPA (sometimes referred to as the TKIP standard) became available in 2003. The Wi-Fi Alliance intended it as an intermediate measure in anticipation of the availability of the more secure and complex WPA2, which became available in 2004 and is a common shorthand for the full IEEE 802.11i (or IEEE 802.11i-2004) standard.
In January 2018, the Wi-Fi Alliance announced the release of WPA3, which has several security improvements over WPA2.[1]
As of 2023, most computers that connect to a wireless network have support for using WPA, WPA2, or WPA3.
Versions
WEP
WEP (Wired Equivalent Privacy) was an initial encryption standard implemented to provide security for wireless network connections, aiming to offer a level of privacy comparable to that of a wired network. Encryption keys of 60-bit and 128-bit lengths were utilized in WEP, comprising a mix of user-defined and pre-set bits by the manufacturer. The RC4 algorithm was employed to encrypt data, with each packet being secured by a key generated through the amalgamation of an Initialization Vector (IV) and a shared key. The decryption process entailed the inverse operation, where the IV and the shared key were used to create a key stream to decrypt the data payload. However, significant security flaws in WEP led to the eventual replacement of this protocol with more robust security standards. [2]
WPA
WPA was introduced as a temporary replacement for WEP until the IEEE 802.11i standard was ready, intended for firmware upgrade compatibility with wireless network interface cards dating back to 1999. However, most wireless access points (APs) before 2003 couldn't be upgraded to support WPA due to extensive required changes. WPA's major improvements included the Temporal Key Integrity Protocol (TKIP), which dynamically generated a unique key for each packet, and a Message Integrity Check to replace the less secure cyclic redundancy check (CRC) used by WEP. These enhancements addressed some of WEP's vulnerabilities, although WPA itself was later found to have flaws due to limitations in its message integrity check algorithm, making it less secure than its successor, WPA2. [3]
WPA2
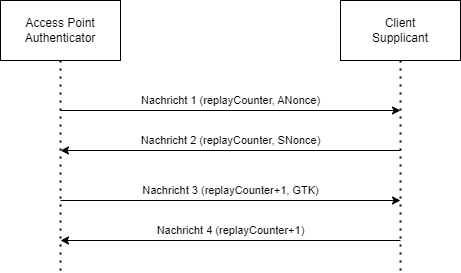
WPA2 (WiFi Protected Access 2) is specified in the IEEE 802.11i standard. It is the successor of WPA, which was based on an unfinished version of the IEEE 802.11i standard. This was done because the previously used WEP (Wired Equivalent Privacy) protocol was found to be insecure. WPA2 (and also WPA) uses the 4-Way-Handshake when a client connects to a network to create multiple keys, which are used to encrypt the communication between client (supplicant) and access point (authenticator). The handshake is based on a "Pairwise Master Key" (PMK), which is based on the Pre-Shared Key (PSK), the password you enter on a client to connect to a WiFi network. The 4-Way-Handshake consists of the following steps:
- The access point generates a random number (ANonce - Authenticator Nonce), and sends it to the client.
- The client also generates a random number (SNonce - Supplicant Nonce), and sends it to the access point, using the same value for the replay counter as the first message.
- The AP sends the group temporal key (GTK) to the client.
- The client confirms that the GTK was received.
After the 2. message, both, AP and client, have the needed information to calculate the Pairwise Transient Key (PTK), which is used to encrypt unicast messages between them. This PTK is based on the PMK, ANonce, SNonce and MAC adresses of both devices, and is therefore unique for each AP/client-combination. The GTK is used to encrypt multicast messages and therefore the same for every client in the network. This GTK is renewed regularly by sending the messages 3 and 4 again.
After sending message 4, the client installs the PTK and GTK, meaning they are being used now. The AP also installs the PTK (the GTK was already installed).
For the encryption WPA2 allows TKIP, CCMP (counter mode with CBC-MAC protocol) and GCMP (galois counter mode protocol). The support of CCMP is mandatory in the WPA2 standard. CCMP is based on AES and is secure, if no IV (initialization vector) is repeated. The IV contains the MAC-address of the sender, a Nonce, which is increased with every message, and some other information transmitted in the WiFi frame. GCMP, also based on AES, is also considered secure, if no IV is used again. Here the IV only contains the sender-MAC-address and the nonce. In both protocols, the nonce is also used as a replay counter and initialized with 0, when the PTK gets installed. [4]
WPA3
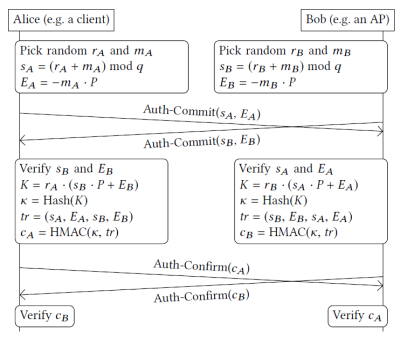
The publication of the KRACK attacks lead to the release of WPA3. This uses the Dragonfly Handshake to provide forward secrecy and prevent dictionary attacks. It is possible to use WPA2 and WPA3 simultaneously in a network, however WPA3 clients are required to use WPA3 when it's available. If the messages, that the network supports WPA3 are manipulated and the client wants to use WPA2 instead, this is recognized during the 4-Way-Handshake, therefore preventing downgrade attacks. The Dragonfly variant used in WPA3 is also called Simultaneous Authentication of Equals (SAE). It uses elliptic curve cryptography to generate a key based on a password. This key is then used for the 4-Way-Handshake. Due to it's much higher entropy (compared to a password), it prevents dictionary attacks. Before the handshake starts, the password is converted to a group element P, by generating hashes of the password, IDs of Client and AP, and an increasing value. This is repeated until the result is a group element (in elliptic curve cryptography a point on the curve), but at least 40 times.
The dragonfly handshake consists of two phases: Commit Phase and Confirm Phase. In the Commit Phase both (Client and AP) pick two random numbers r and m in the range [2, q[ with q being the order of the used group, and calculate s = (r+m) mod q and E = -m * P (P is the previously calculated group element). The next step is to send s and E to the communcation partner (Client->AP and AP->client) and to confirm that the received values are in a valid range, aborting the handshake otherwise. In the Confirm Phase a secret point K on the curve is calculated: K = r1 * (s2 * P + E2). r1 is the own chosen value r, while s2 and E2 are the received values s and E. The hash of this point K leads to the key k. Finally, an HMAC consisting of k, s1, E1, s2 and E2 is calculated and sent between the devices. If the value is correct, k is successfully chosen as key, which is then used for the 4-Way-Handshake.
Frame Aggregation and Fragmentation
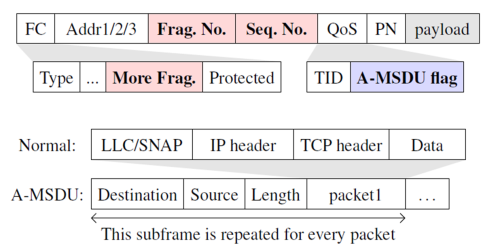
In WiFi the data is transmitted in so called Frames. To increase the efficiency of the transmission, it is possible to send multiple packets in one frame (aggreation), or to separate a (too) large packet into multiple frames (fragmentation). To to this, a frame contains a Frame Control Field, which specifies the type of the frame with multiple flags. The frame also contains MAC-adresses to specify the receiver and sender of the frame, as well as the source or destination. Furthermore, fields to specify the fragment- and sequence-number, and the QoS (Quality of Service) field are included. At the end, the actual transmitted data, called payload, is located. If the payload is small, multiple packets are aggregated into a large frame called A-MSDU (Aggregate MAC Service Data Units). This is marked by a flag in the QoS field, however this flag is not authenticated and can be changed by an attacker. The multiple payloads are called subframes, containing source- and destination-MAC-Address, packet-length and the actual data. The second possibility (fragmentation) is used, when the payload is too large for a single frame, but also in noisy environments. In the latter case this leads to an increased performance, because in the case of transmission errors, only a part of the data has to be transmitted again. It is possible to use up to 16 fragments, which have an incremental fragment-number and the same sequence-number.
Attacks
KRACK
Key Reinstallation Attacks are based on repeated installation of keys (see explanation of the 4-Way-Handshake), which leads to the Nonce resetting to 0, and therefore reusing an IV.
When the messages 2 and 4 of the 4-Way-Handhake are not received, the messages 1 and 3 are sent again. The IEEE 802.11i standard also states, that client should immediately install the keys after receiving message 3. In KRACK, the message 4 is intercepted, so the AP doesn't receive it. The client doesn't know about this and starts sending encrypted messages. When the access point sends the message 3 again, the client reinstalls the keys, resets the Nonce, and starts sending encrypted messages again. Since the IVs are reused now, the encryption is no longer considered secure.
FragAttacks
Fragmentation and Aggregation Attacks affect the above mentioned possibilites of fragmenting and aggregating frames.
To attack the aggregation, the frame has to be intercepted and the A-MSDU flag modified, to make normal frames look like aggregated frames. The payload has to contain specific values, so the subframe contains the desired values. This is done by making the client perform a POST-request with specific data (e.g. on a malicious website of the attacker). If chosen correctly, the data will be interpreted as correct subframe, leading to it being forwarded like an authentic frame. With this attack it's possible to e.g. perform portscans, or to get clients to use specific (malicious) DNS servers.
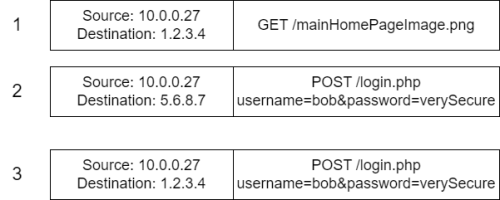
The other type of FragAttacks targets the fragmentation. One variant of this is the Mixed Key Attack, which exploits flaws in the 802.11 standard, since it's not required, that multiple fragments of a frame are encrypted using the same key. This attack requires, that the keys are renewed regularly, be performing a full 4-Way-Handshake. The victim has to access data on the server of an attacker (e.g. through social engineering), which is hosted on a long URL. This leads to the frame being fragmented. The attacker intercepts these fragments and only forwards the first (with packet number n) to the access point, which encrypts it, recognizes it needs to wait for the other fragments, and stores it. At a later time, the keys are renewed and the package number is reset. When the client then sends a fragment with the packet number n+1, the attacker forwards this fragment to the AP, which then combines the previous stored fragment with the new fragment, and forwards it. This could lead to sending login data (meant for a normal website) to the server of the attacker. See the picture on the right for a simplified example.
Dragonblood
Dragonblood is a set of attacks targeting the Dragonfly Handshake of WPA3. All of them require that the attacker is in close range of the Client or the Access Point. Depending on which of these devices is attacked, the attacker has to pretend to be the other.
As mentioned above, downgrade attacks to force WPA2 instead of WPA3 are recognized during the 4-Way-Handshake. However, at this point the client has already sent enough encrypted data, to allow an attacker to perform a dictionary attack based on this data. This leads to one of the advantages of WPA3 being bypassed. To do this, a fake WPA2-network with the same SSID as the original network has to be created. Depending on the specific implementation, clients even try to connect to the fake network, although the original network doesn't support WPA2.
Another type of a Dragonblood attack targets the possibility, that Client and AP negotiate which elliptic curve is used for the handshake. The client sends the access point their desired curve. If the AP doesn't support this curve, it responds with a message stating so, leading to the client select another curve from it's list. This is repeated until a curve supported by both devices is found. The message that the AP doesn't support a curve is not verified, therefore it can be forged to force them to use a weaker curve (downgrade attack). This can also be used to perform an upgrade attack, leading to a denial of service on devices with low computational power.[5]
Tools
Aircrack-ng and Driftnet are two significant tools in the cybersecurity context, each with specific functions and impacts on the digital security landscape.
Aircrack-ng
is an open-source suite designed for assessing Wi-Fi network security. It's capable of monitoring and capturing wireless network traffic to evaluate network security. Tools within the Aircrack-ng suite, such as Aireplay-ng, can inject packets into Wi-Fi networks, facilitating potential attacks. Commonly, Aircrack-ng is used to crack Wi-Fi networks secured with WEP or WPA-PSK protocols through dictionary and brute-force attacks. Dictionary attacks employ predefined wordlists, while brute-force attacks attempt all possible password combinations. To protect against Aircrack-ng attacks, strong passwords, regular updates of security protocols, router firmware, and network monitoring for suspicious activities are recommended.[6]
for more description of how aircrack-ng (a popular program suite for WiFi network security) can be used to crack the Pre Shared Key after capturing the 4-Way-Handshake can be found in the article: WiFi Sniffing
Driftnet
leverages the technique of sniffing WLAN traffic to gather information. It specializes in intercepting and analyzing unencrypted packets, benefiting from the vulnerability of unsecured WLAN connections, especially those lacking WPA2 or WPA3 encryption. Driftnet's capability to decrypt and reveal sensitive information underscores the vulnerability of unsecured WLAN networks. It is used in training scenarios to demonstrate technical vulnerabilities of WLAN security and to raise awareness about the risks associated with unencrypted WLAN communication. The detection of activities by tools like Driftnet highlights the urgency of implementing advanced encryption protocols such as WPA3 and integrating Intrusion Detection Systems (IDS) to identify and block suspicious activities, including packet sniffing. [7]
References
- https://www.krackattacks.com/
- https://www.fragattacks.com/
- https://wpa3.mathyvanhoef.com/
- https://ieeexplore.ieee.org/document/523485
- https://github.com/deiv/driftnet
- ↑ https://www.wi-fi.org/news-events/newsroom/wi-fi-alliance-introduces-security-enhancements%7Ctitle=Wi-Fi Alliance® introduces security enhancements | Wi-Fi Alliance|website=www.wi-fi.org|language=en|access-date=2018-01-09
- ↑ Arash Habibi Lashkari, Mir Mohammad Seyed Danesh, and Behrang Samadi. A survey on wireless security protocols (wep, wpa and wpa2/802.11i). In 2009 2nd IEEE International Conference on Com- puter Science and Information Technology, pages 48–52, 200
- ↑ Kashish Monga, Vishal Arora, and Ashish Kumar. Analyzing the be- havior of wpa with modification. In 2015 International Conference on Communication Networks (ICCN), pages 53–56, 2015.
- ↑ Tamara Radivilova and Hassan Ali Hassan. Test for Penetration in Wi-Fi Network: Attacks on WPA2-PSK and WPA2-Enterprise. In 2017 International Conference on Information and Telecommunication Technologies and Radio Electronics (UkrMiCo), pages 1–4, 2017.
- ↑ Mathy Vanhoef and Eyal Ronen. Dragonblood: Analyzing the Dragonfly Handshake of WPA3 and EAP-pwd. In 2020 IEEE Symposium on Security and Privacy (SP), pages 517–533, 2020.
- ↑ Elyas Baray and Nitish Kumar Ojha. ‘wlan security protocols and wpa3 security approach measurement through aircrack-ng technique’. In 2021 5th International Conference on Computing Methodologies and Commu- nication (ICCMC), pages 23–30, 2021
- ↑ deiv (2023). Driftnet. GitHub repository. Verfügbar unter: https://github.com/deiv/driftnet. Zuletzt besucht am 11. Dezember 2023.