Difference between revisions of "Wireshark: Traffic analysis of a smart alarm system"
Jostrowski (talk | contribs) |
Jostrowski (talk | contribs) |
||
| Line 13: | Line 13: | ||
This analysis looks at the network traffic of the smart alarm system and later in step "Smartphone communication" at the traffic between the Alarm system and Smartphone App. | This analysis looks at the network traffic of the smart alarm system and later in step "Smartphone communication" at the traffic between the Alarm system and Smartphone App. | ||
With the help of the [[Princeton IoT Inspector]] we | With the help of the [[Princeton IoT Inspector]] we are able to get a brief overview of the communications between the device and the outside world. | ||
<div><ul> | <div><ul> | ||
| Line 33: | Line 33: | ||
The password looks like a base64 string -> decode it: hex representation: aeb20fe3ead5942602831840a5c7292f9d548c7e (=bit length: 140 ... probably sha-1 or sha-128) | The password looks like a base64 string -> decode it: hex representation: aeb20fe3ead5942602831840a5c7292f9d548c7e (=bit length: 140 ... probably sha-1 or sha-128) | ||
https://en.wikipedia.org/wiki/Digest_access_authentication | |||
==== HTTP Traffic ==== | ==== HTTP Traffic ==== | ||
Revision as of 19:58, 3 October 2019
Summary
This is a traffic analysis of the Technaxx WiFi smart alarm system starter kit TX-84 using Wireshark.
Requirements
- Router running tcpdump (see: OpenWRT: Installation)
- Technaxx WiFi smart alarm system starter kit TX-84 with connected Smartphone app
- Wireshark
Analysis
This analysis looks at the network traffic of the smart alarm system and later in step "Smartphone communication" at the traffic between the Alarm system and Smartphone App.
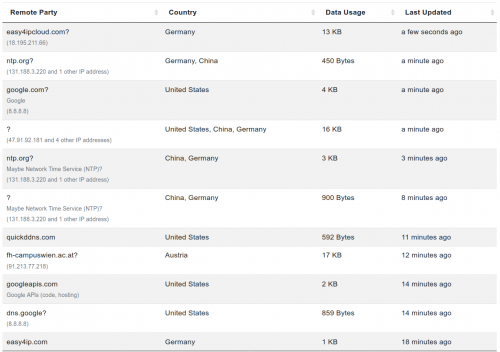
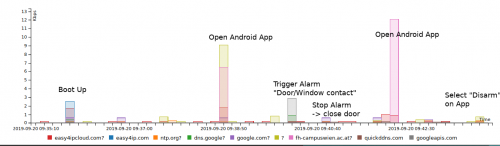
With the help of the Princeton IoT Inspector we are able to get a brief overview of the communications between the device and the outside world.
What is not covered by the Princeton IoT-Inspector is the internal traffic. We will later find out that is quite interesting.
Boot up
There are two main communications to the outside world: 1. Heartbeat and 2. HTTP Traffic
Heartbeat / "Hello" to Chinese server
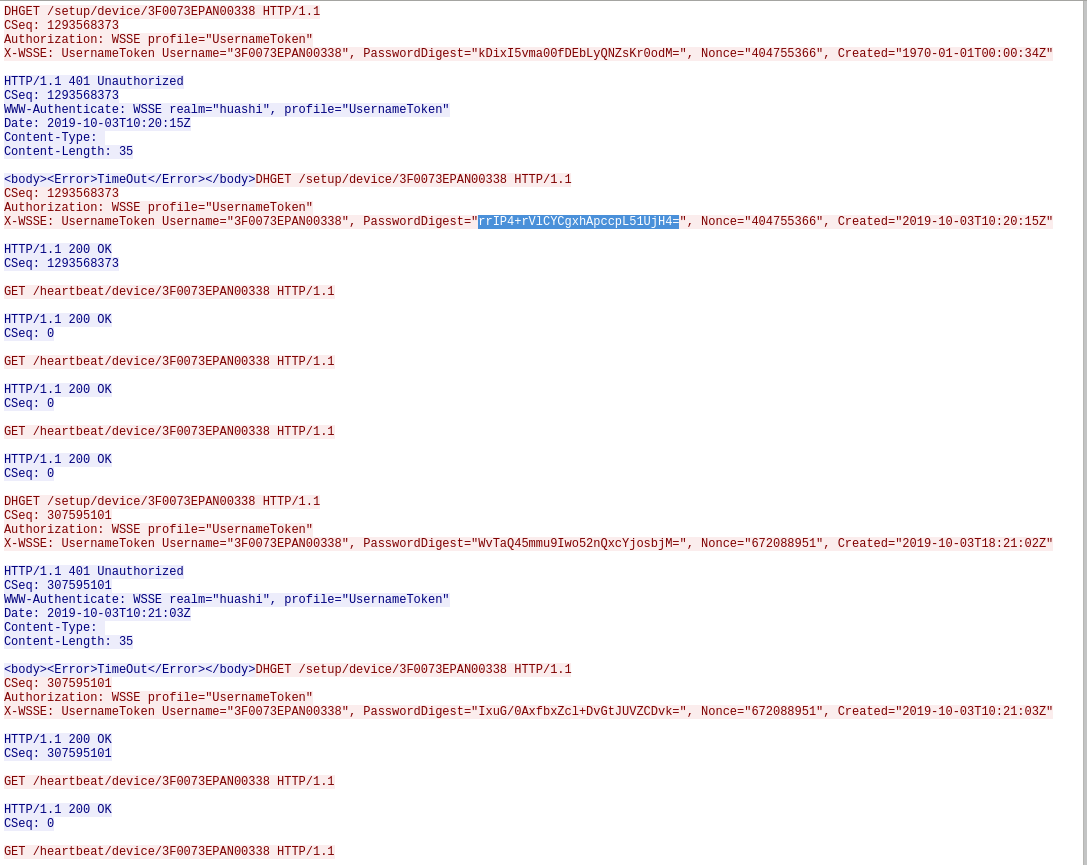
While the device is turned on it will send a notification to a Chinese server that it is turned on and active.
The password looks like a base64 string -> decode it: hex representation: aeb20fe3ead5942602831840a5c7292f9d548c7e (=bit length: 140 ... probably sha-1 or sha-128)
https://en.wikipedia.org/wiki/Digest_access_authentication
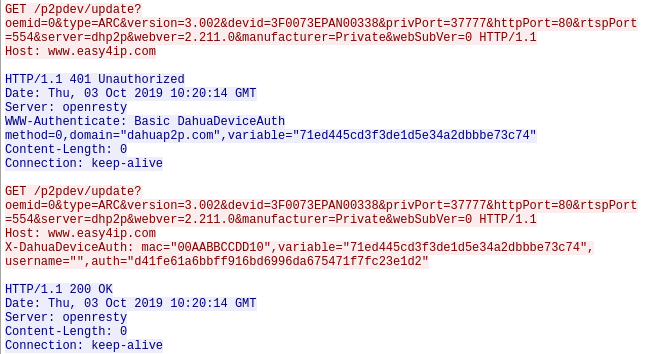
HTTP Traffic
Used Hardware
- Router: Zyxel Armor Z2 AC 2600 MU-MIMO dualband wireless router
- Technaxx WiFi smart alarm system starter kit TX-84
References
- I found a interesting presentation very similar to my findings
- https://site.ieee.org/neworleans/files/2016/12/12052016-Presentation-IoT-security-website-copy.pdf